By: Jon Clay
January 11, 2024
Read time: 4 min (970 words)
Trend Micro collaborates with INTERPOL to defend FIFA World Cup by preventing attacks & mitigating risks to fight against the rising threat of cybercrime.
The prominent sporting event, FIFA World Cup, concluded in December 2022, and it generated a lot of online engagements from millions of fans around the world. The remarkable penalty-shootout in the finals was hailed the champion of the event and it was a trending topic in social media and headline news. Before and during this event, the online users were rejoicing and betting their favorite teams at the same time cybercriminals were taking advantage of the event to deploy spam and scams. With this, law enforcement, and in particular, INTERPOL, had to step up and tapped its gateway partners to be on the lookout and report to them the cyberthreats surrounding the 2022 FIFA World Cup. Trend Micro helped by proactively monitoring our global threat intelligence that revealed many malicious websites and scams before and during the event. For example, we saw websites disguised as ticketing systems of the 2022 FIFA World Cup and many survey scams. We shared this information to INTERPOL, helping in their goal of preventing attacks and mitigating the risk posed by the fraudsters of this event. Furthermore, through our global threat intelligence, we monitored the detections of malicious websites and files from the country of Qatar as INTERPOL worked closely with them to prevent cybercriminals and malicious actors in disrupting the sporting event.
Let’s look a bit deeper into the different cyber threats we discovered and shared with INTERPOL, besides blocking them for our customers.
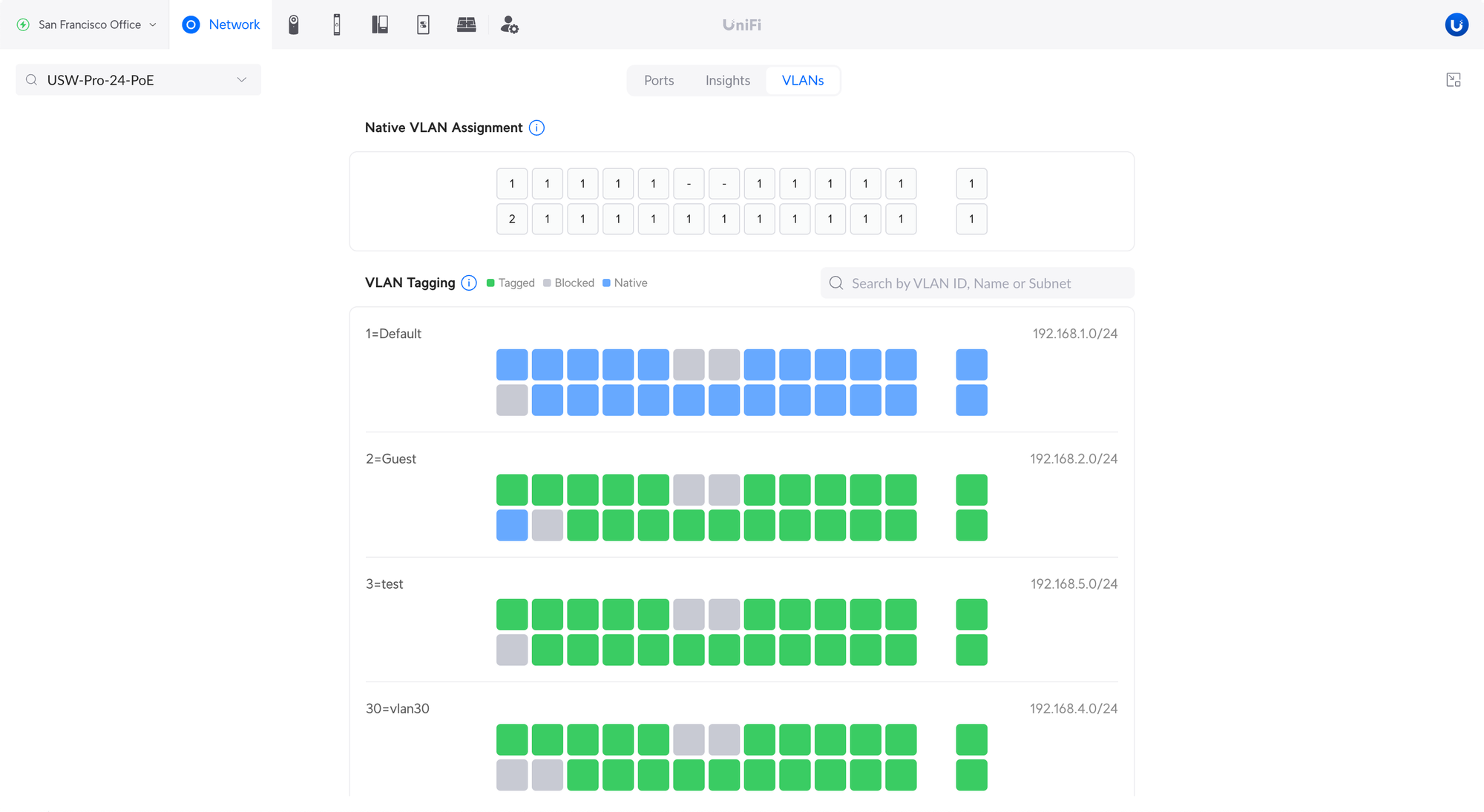
Malicious Websites found throughout 2022
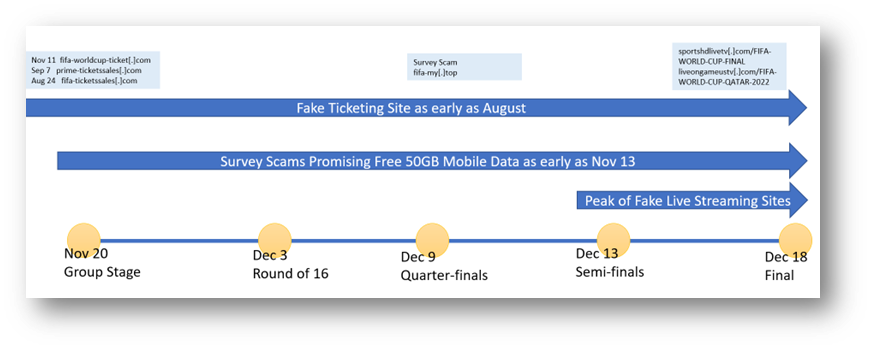
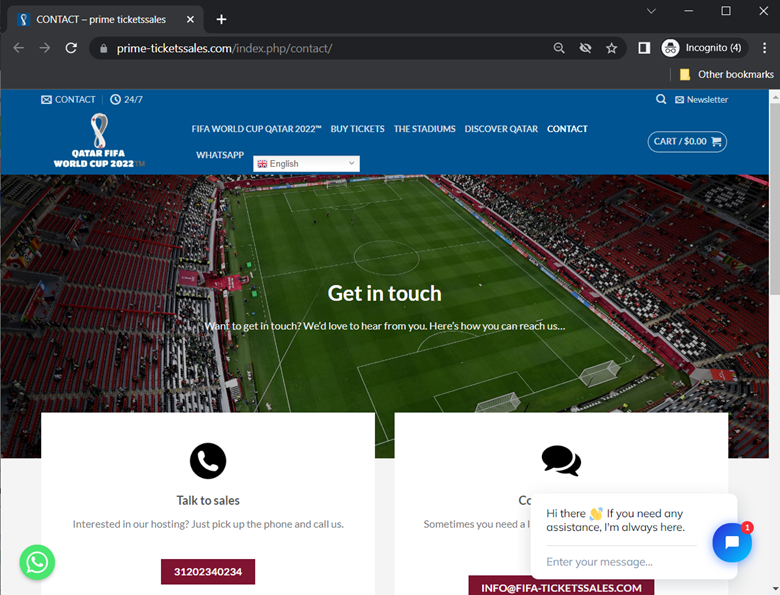
Fake Ticketing System
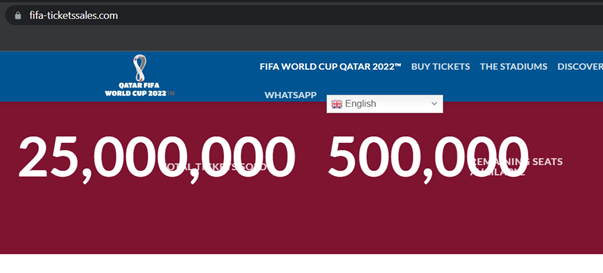
It is no wonder due to the millions of potential victims that cybercriminals created dubious sites for selling tickets to the 2022 FIFA World Cup and trick users into inputting their personal information and credit card details in phishing attempts. We observed a few sites such as fifa-ticketssales[.]com and prime-ticketssales[.]com, both imitating the FIFA World Cup ticketing page and one showing an unbelievable number of sold tickets and remaining number of seats. We also identified contact details of scammers such as phone numbers and email addresses, some of these phone numbers were linked to other scam sites which is typical for scammers to reuse phone numbers.
Fake Live Streaming
Cybercriminals created several fake streaming sites to lure victims to click on it. We identified around 40 unique domains that hosted fake streaming of FIFA World Cup. Example sites are watchvsportstv[.]com/2022-FIFA-WORLD-CUP-FINAL, sportshdlivetv[.]com/FIFA-WORLD-CUP-FINAL and istream2watch[.]stream/video/fifa-world-cup. From our analysis of these fake live streaming pages, the user will be redirected to websites with subscription forms or premium access requests and lure these users to subscribe and pay. Among the top countries detected were Brazil, Philippines, and Malaysia.
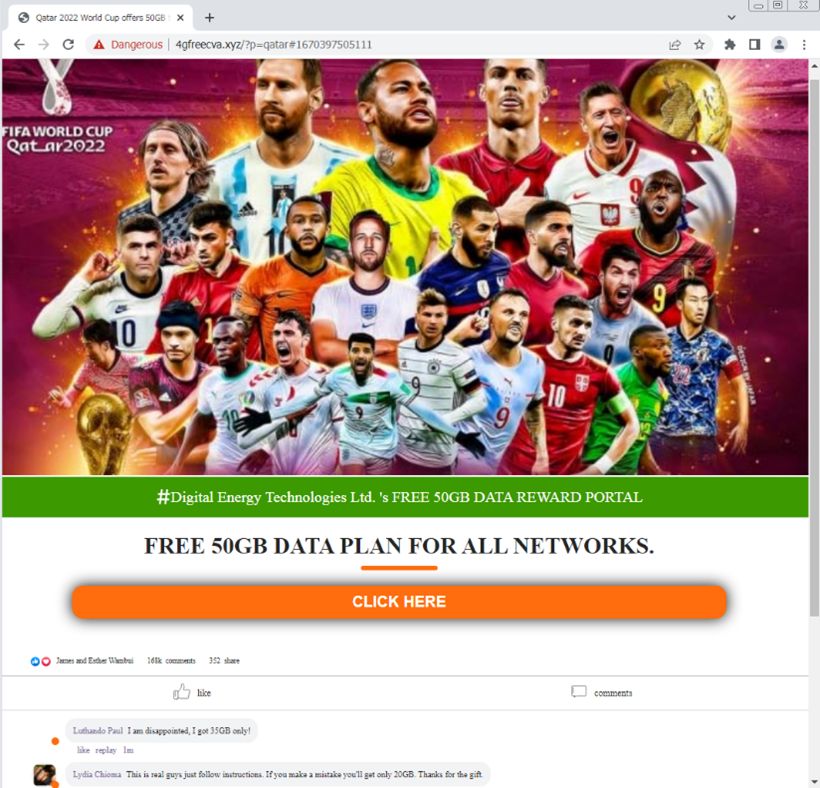
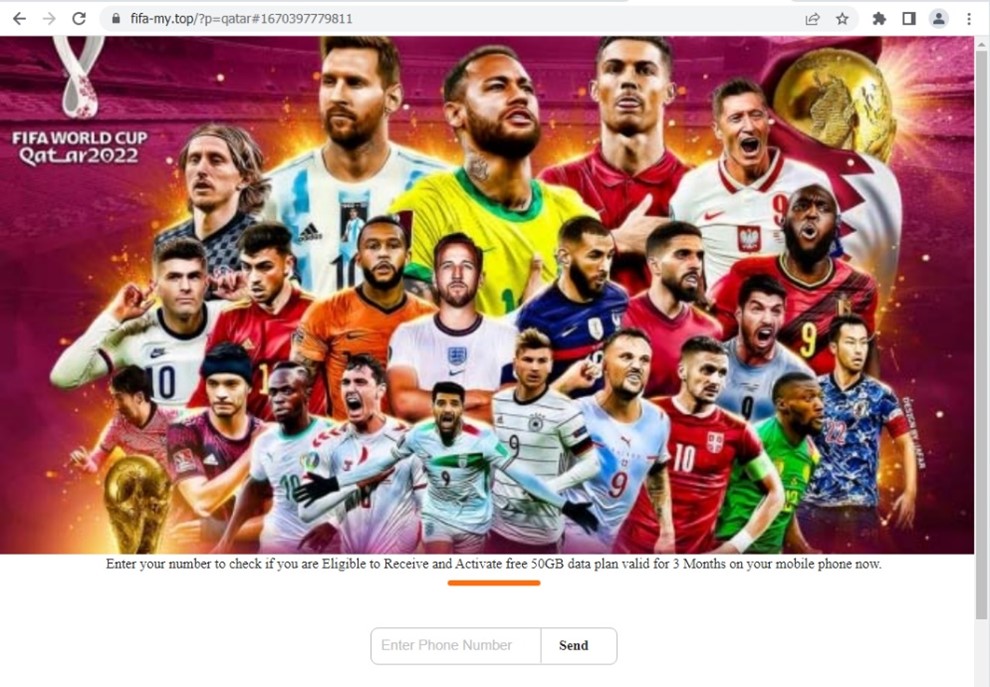
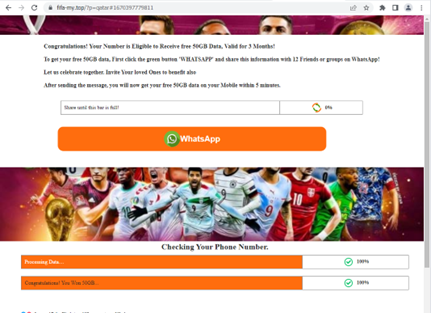
Survey Scams
Survey scams are relentless and scammers have been using them for a long time now. One we reported for example was https://www.theregister.com/2012/03/23/pinterest_attracts_scammers/. While the FIFA World Cup 2022 was ongoing, especially as we approached the semi-finals and final game, we observed malicious sites hosting survey scams that offered free 50GB mobile data. We identified more than 40 IP addresses or servers hosting the scam sites. Mostly were registered by Chinese names and hosted under Google LLC. Survey scams aim to trick users into obtaining free mobile data 50GB for a faster streaming of video or a free mobile network. It tricks users into inputting phone number and personal information thus in the end it will incur charges to the victims not knowing that it is a scam and may use their personal information for future spam or scams. Additionally, mostly it will redirect to fake dating sites and would require and harvest email address which can allow spammers to include them in their next wave of spam.
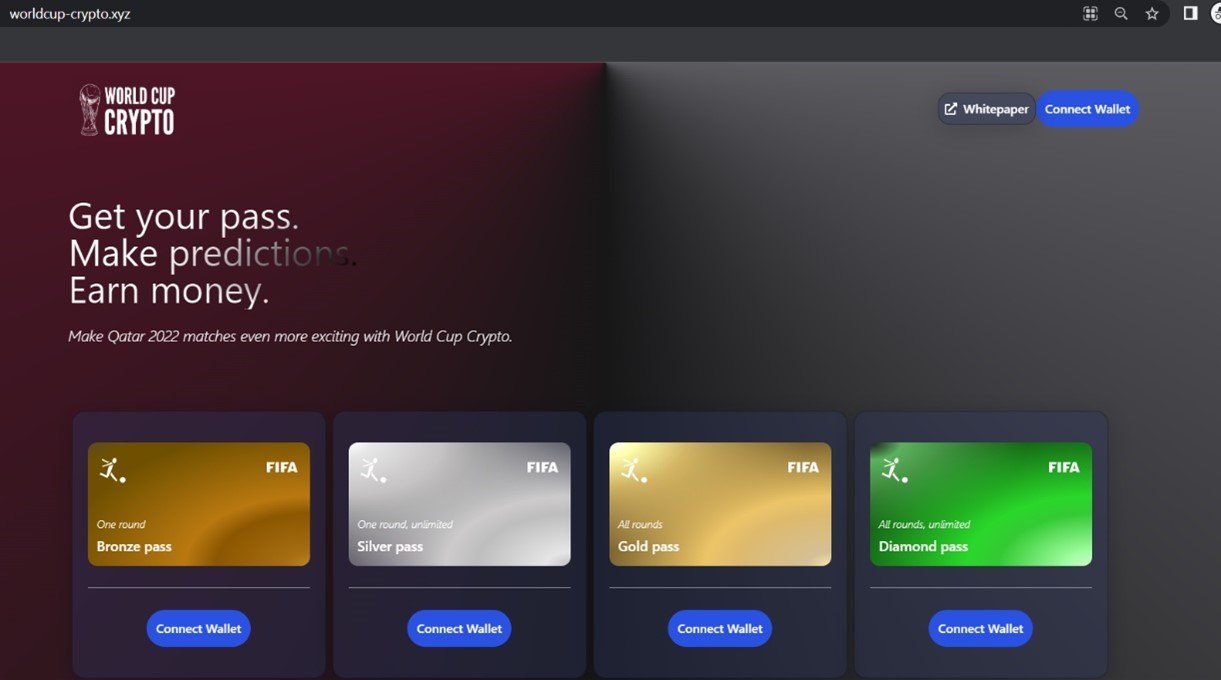
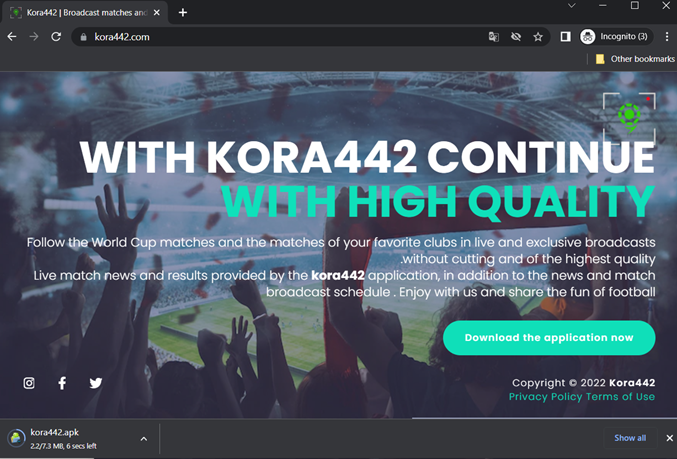
Crypto scamming and malicious app
Based on external reports there were crypto scammers that leveraged the sporting event. We observed some scam sites such as cristiano-binance[.]xyz, binance[.]supply, football-blnance[.]com, football-binance[.]com, birance[.]online and birance[.]site that lure users to click on the button “Connect wallet” and will compromise the account. We also observed malicious app or Android RAT which was reported from https://twitter.com/ESETresearch/status/1596222440996311040 https://blog.cyble.com/2022/12/09/threat-actors-targeting-fans-amid-fifa-world-cup-fever/ and it was called “ Kora 442” with malicious site kora442[.]com. It lured users to download the app “kora442.apk” and promised live and exclusive broadcasts of the 2022 FIFA World Cup. Example of hashes are 2299d4e4ba3e9c2643ee876bb45d6a976362ce3c, c66564b7f66f22ac9dd2e7a874c6874a5bb43a26, 9c904c821edaff095e833ee342aedfcaac337e04 and 60b1da6905857073c4c46e7e964699d9c7a74ec7. The package name is com.app.projectappkora and we detect it as AndroidOS_DummyColl.HRX. It steals information from the infected device and sends it to the Command &Control (C&C) server.
Trend Micro’s mission has always been making the world safe for exchanging digital information and our support of INTERPOL and the 2022 FIFA World Cup gave us an opportunity to do exactly this. We’re proud of our continued support of INTERPOL, whether it is helping them with investigations of cybercriminals, or helping with a major worldwide sporting event. Our 34 years of experience in proactively identifying new threats and attacks and protecting users against them will continue in the future and we look forward to more engagements with law enforcement and organizations managing these events.