Excel for Microsoft 365 Word for Microsoft 365 Outlook for Microsoft 365 More…
Note: This feature requires a Microsoft 365 subscription and is available for users and organizations whose administrators have set up sensitivity labels. If you’re an administrator looking to get started with sensitivity labels see Get started with sensitivity labels.
You can apply sensitivity labels to your files and emails to keep them compliant with your organization’s information protection policies.
The names of these labels, the descriptions you see when you hover over them, and when to use each label will be customized for you by your organization. If you need additional information about which label to apply, and when, contact your organization’s IT department.
How are sensitivity labels applied?
Sensitivity labels are applied either manually or automatically.
Note: Even if your administrator has not configured automatic labeling, they may have configured your system to require a label on all Office files and emails, and may also have selected a default label as the starting point. If labels are required you won’t be able to save a Word, Excel, or PowerPoint file, or send an email in Outlook, without selecting a sensitivity label.
To apply, change, or remove a label manually follow these steps:
Office 365Office 365 for MacOffice for AndroidOffice for iOSWeb
Outlook
- When composing an email, select Sensitivity.
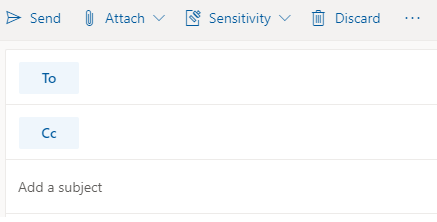 Important: Sensitivity is not available if your Office account isn’t a work account, and if your administrator hasn’t configured any sensitivity labels and enabled the feature for you.
Important: Sensitivity is not available if your Office account isn’t a work account, and if your administrator hasn’t configured any sensitivity labels and enabled the feature for you. - Choose the sensitivity label that applies to your email.
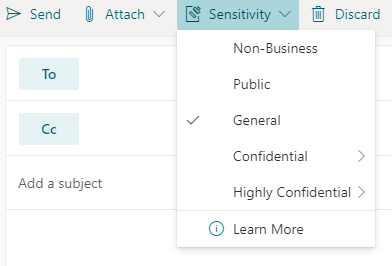 Note: If your organization has configured a website to learn more about their sensitivity labels, you will also see a Learn More option.
Note: If your organization has configured a website to learn more about their sensitivity labels, you will also see a Learn More option.
To remove a sensitivity label that has already been applied to an email, unselect it from the Sensitivity menu. Naturally if your organization requires labels on all files you won’t be able to remove it.
Word, Excel, PowerPoint
- On the Home tab, select Sensitivity.
 Important: Sensitivity is not available if your Office account isn’t a work account with a Office 365 Enterprise E3 or Office 365 Enterprise E5 license assigned, or if your administrator hasn’t configured any sensitivity labels and enabled the feature for you .
Important: Sensitivity is not available if your Office account isn’t a work account with a Office 365 Enterprise E3 or Office 365 Enterprise E5 license assigned, or if your administrator hasn’t configured any sensitivity labels and enabled the feature for you . - Choose the sensitivity label that applies to your file.
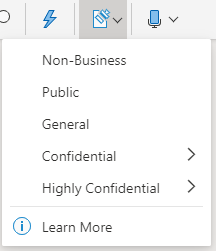 Note: If your organization has configured a website to learn more about their sensitivity labels, you will also see a Learn More option.
Note: If your organization has configured a website to learn more about their sensitivity labels, you will also see a Learn More option.
To remove a sensitivity label that has already been applied to a file, unselect it from the Sensitivity menu. Naturally if your organization requires labels on all files you won’t be able to remove it.
Automatically applied (or recommended) labels
If your administrator has set up automatic labeling then files or emails that contain certain kinds of information – such as social security numbers, credit card numbers, or other sensitive information – can have a specified label either recommended for, or applied, automatically.
If a label has been applied automatically you’ll see a notification below the Office ribbon that looks like this.
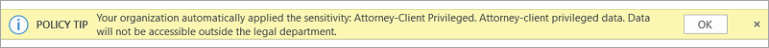
The notice for when a label has been recommended, but not automatically applied, looks similar.
For more information see Automatically apply or recommend sensitivity labels to your files and emails in Office
How do I know what label is currently applied?
The way to see the currently applied label, if any, varies slightly depending upon whether you’re on desktop or mobile.
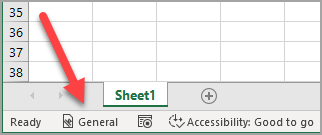
On desktop apps (including Office for the web) look at the status bar at the bottom of the window.
On the Office mobile apps, select the ![]() menu.
menu.
Outlook is a bit different
In Outlook nothing appears if no label has been selected or if you’re composing an email and only the default label is applied.
If a label has been selected, however, you’ll see it on the InfoBar just above the To field.
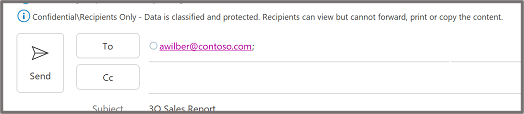
What happens when I apply a sensitivity label?
When you apply a sensitivity label, the label information will persist with your file or email, even as it is shared between devices, applications, and cloud services. Applying a sensitivity label may also result in changes to your file or email according to your organization’s configuration, such as:
- Encryption with Information Rights Management may be applied to your file or email
- A header or footer may appear in your file or email
- A watermark may appear in your file
Note: If you don’t have permission to change or remove a sensitivity label, you’ll be prevented from doing so with an error message in most apps. In some apps, like Outlook mobile, the sensitivity labels will simply be disabled.
Not all apps on all platforms support the same behavior, so the exact results of applying a sensitivity label may vary slightly. For more information about what capabilities are supported on each platform see Support for sensitivity label capabilities in apps.
Justify changes to sensitivity label
Your administrator can have a policy that requires you to provide justification before changing a sensitivity label from a higher sensitivity to a lower sensitivity. In this configuration, you may be asked to choose a justification reason or provide your own when selecting a less sensitive label.
Note: You will only be asked to justify changes one time after opening a document or replying to forwarding an email message. After justifying once, subsequent changes will not require justification until that document or email message is closed and opened again.