MSRC / By MSRC Team / March 16, 2021
This guidance will help customers address threats taking advantage of the recently disclosed Microsoft Exchange Server on-premises vulnerabilities CVE-2021-26855, CVE-2021-26858, CVE-2021-26857, and CVE-2021-27065, which are being exploited. We strongly urge customers to immediately update systems. Failing to address these vulnerabilities can result in compromise of your on-premises Exchange Server and, potentially, other parts of your internal network.
Mitigating these vulnerabilities and investigating whether an adversary has compromised your environment should be done in parallel. Applying the March 2021 Exchange Server Security Updates is critical to prevent (re)infection, but it will not evict an adversary who has already compromised your server. Based on your investigation, remediation may be required. This guide will help you answer these questions:
- How does the attack work?
- Am I vulnerable to this threat?
- How do I mitigate the threat?
- Have I been compromised?
- What remediation steps should I take?
- How can I better protect myself and monitor for suspicious activity?
Microsoft will continue to monitor these threats and provide updated tools and investigation guidance to help organizations defend against, identify, and remediate associated attacks. We will update this guidance with new details and recommendations as we continue to expand our knowledge of these threats and the threat actors behind them, so come back to this page for updates.
How does the attack work?
Microsoft released security updates for four different on premises Microsoft Exchange Server zero-day vulnerabilities (CVE-2021-26855, CVE-2021-26858, CVE-2021-26857, and CVE-2021-27065). These vulnerabilities can be used in combination to allow unauthenticated remote code execution on devices running Exchange Server. Microsoft has also observed subsequent web shell implantation, code execution, and data exfiltration activities during attacks. This threat may be exacerbated by the fact that numerous organizations publish Exchange Server deployments to the internet to support mobile and work-from-home scenarios.
In many of the observed attacks, one of the first steps attackers took following successful exploitation of CVE-2021-26855, which allows unauthenticated remote code execution, was to establish persistent access to the compromised environment via a web shell. A web shell is a piece of malicious code, often written in typical web development programming languages (e.g., ASP, PHP, JSP), that attackers implant on web servers to provide remote access and code execution to server functions. Web shells allow adversaries to execute commands and to steal data from a web server or use the server as launch pad for further attacks against the affected organization. Therefore, it is critical to not only immediately mitigate the vulnerabilities, but also remove any additional backdoors, such as web shells that attackers may have created.
Am I vulnerable to this threat?
If you are running Exchange Server 2010, 2013, 2016, or 2019 you must apply the March 2021 Security Update to protect yourself against these threats.
To determine if your Exchange Servers are vulnerable to this attack, the following methods can be used:
- Using Microsoft Defender for Endpoint
- Scanning your Exchange servers using Nmap
Microsoft Defender for Endpoint
Microsoft Defender for Endpoint customers can use the threat analytics article in Microsoft 365 security center to understand their risk. This requires your Exchange Servers to be onboarded to Microsoft Defender for Endpoint. See instructions for onboarding servers that are not currently monitored.

Scanning using Nmap script
For servers not onboarded to Microsoft Defender for Endpoint, use this Nmap script to scan a URL/IP to determine vulnerability: http-vuln-cve2021-26855.nse.
How do I mitigate the threat?
The best and only complete mitigation for these threats is to update to a supported version of Exchange Server and ensure it is fully updated. If it’s not possible to immediately move to the current Exchange Server Cumulative Update and apply security updates, additional strategies for mitigation are provided below. These lesser mitigation strategies are only a temporary measure while you install the latest Cumulative Update and Security Updates.
Immediate temporary mitigations
The following mitigation options can help protect your Exchange Server until the necessary Security Updates can be installed. These solutions should be considered temporary, but can help enhance safety while additional mitigation and investigation steps are being completed.
- Run EOMT.ps1 (Recommended) – The Exchange On-premises Mitigation Tool (EOMT.ps1) mitigates CVE-2021-26855 and attempts to discover and remediate malicious files. When run, it will first check if the system is vulnerable to CVE-2021-26855 and, if so, installs a mitigation for it. It then automatically downloads and runs Microsoft Safety Scanner (MSERT). This is the preferred approach when your Exchange Server has internet access.
- Run ExchangeMitigations.ps1 – The ExchangeMitigations.ps1 script applies mitigations but doesn’t perform additional scanning. This is an option for Exchange Servers without internet access or for customers who do not want Microsoft Safety Scanner to attempt removing malicious activity it finds.
Applying the current Exchange Server Cumulative Update
The best, most complete mitigation is to get to a current Cumulative Update and apply all Security Updates. This is the recommended solution providing the strongest protection against compromise.
- See installation instructions at Released: March 2021 Exchange Server Security Updates.
Apply security hotfixes to older Cumulative Updates
To assist organizations that may require additional time and planning to get to a supported Cumulative Update, security hotfixes have been made available. It’s important to note that applying these security hotfixes to older Cumulative Updates will mitigate against these specific Exchange vulnerabilities, but it will not address other potential security risks your Exchange Server may be vulnerable to. This approach is only recommended as a temporary solution while you move to a supported Cumulative Update.
- See installation instructions at March 2021 Exchange Server Security Updates for older Cumulative Updates of Exchange Server.
Isolation of your Exchange Server
To reduce the risk of exploitation of the vulnerabilities, the Exchange Server can be isolated from the public internet by blocking inbound connections over port 443.
- Blocking port 443 from receiving inbound internet traffic provides temporary protection until Security Updates can be applied, but it reduces functionality as it could inhibit work-from-home or other non-VPN remote work scenarios and does not protect against adversaries who may already be present in your internal network.
- The most comprehensive way to complete this is to use your perimeter firewalls that are currently routing inbound 443 traffic to block this traffic. You can use Windows Firewall to accomplish this, but you will have to remove all inbound 443 traffic rules prior to blocking the traffic.
Have I been compromised?
To determine if your Exchange Servers have been compromised due to these vulnerabilities, multiple options have been made available:
- Microsoft Defender for Endpoint
- Publicly available tools published by Microsoft
If Microsoft Defender for Endpoint is not running, skip directly to the publicly available tools section. If it is running, we recommend that you follow both methods.
Microsoft Defender for Endpoint
- Check the threat analytics article in Microsoft 365 security center to determine if any indications of exploitation are observed. The Analyst report tab in the Microsoft 365 Security Center threat analytics article contains a continuously updated detailed description of the threat, actor, exploits, and TTPs. On the Overview page, the Impacted assets section lists all impacted devices. The Related incidents section shows any alerts for detected exploitation or post-exploitation activity.

- If you have devices that are flagged as impacted (see Impacted assets section) and have active alerts and incidents, click the incidents to further understand the extent of the attack.

- Microsoft Defender for Endpoint blocks multiple components of this threat and has additional detections for associated malicious behaviors. These are raised as alerts in the Microsoft Defender Security Center. Additionally, Microsoft Defender for Endpoint prevents some critical behaviors observed in attacks, such as attempts to exploit the CVE-2021-27065 post-authentication file-write vulnerability that can be combined with CVE-2021-26855 to elevate privileges.

- Microsoft Defender for Endpoint also detects post-exploitation activity, including some techniques that attackers use to maintain persistence on the machine. Note that alerts marked “Blocked” indicate that the detected threat is also remediated. Alerts marked “Detected” require security analyst review and manual remediation.

- You can use advanced hunting to search for unexpected files dropped or executing in Exchange folders, which could be web shells or other attacker artifacts. See more advanced hunting queries relevant to this threat in the Analyst report in Threat Analytics and in our GitHub queries repository.

Publicly available tools published by Microsoft
The following tools have been made available by Microsoft to aid customers in investigating whether their Microsoft Exchange Servers have been compromised. We recommend customers to run both tools as part of their investigation:
Exchange On-Premises Mitigation Tool
Download and run EOMT.ps1 as an administrator on your Exchange Server to automatically run the latest version of Microsoft Safety Scanner (MSERT). MSERT discovers and remediates web shells, which are backdoors that adversaries use to maintain persistence on your server.

- After completing the scan, EOMT.ps1 reports any malicious files it discovers and removes. If malicious files are discovered and removed by the tool, follow the web shell remediation workflow. If no malicious files are found, it will report “No known threats detected.”
- If this initial scan does not find evidence of malicious files, a full scan can be run via “.\EOMT.ps1 -RunFullScan”. This may take a few hours or days, depending on your environment and the number of files on the Exchange Server.
- If the script is unable to download Microsoft Safety Scanner (MSERT), you can download and copy MSERT manually to your Exchange Server. Run this executable directly as an administrator. Follow the on-screen instructions to run a Quick or Full scan. A new version of MSERT should be downloaded each time it is run to ensure it contains the latest protections
Test-ProxyLogon.ps1
Run the Test-ProxyLogon.ps1 script as administrator to analyze Exchange and IIS logs and discover potential attacker activity.
IMPORTANT: We recommend re-downloading this tool at a minimum of once per day if your investigation efforts span multiple days, as we continue to make updates to improve its usage and output.
Step 1 – Review script output to determine risk:
- If the script does not find attacker activity, it outputs the message Nothing suspicious detected
- Continue to the scan remediation workflow.
- If attacker activity was found, the script reports the vulnerabilities for which it found evidence of use and collects logs that it stores in the specified output path in the Test-ProxyLogonLogs directory. Continue following these steps for remediation. Below is an example of the output:

Step 2 – Investigate CVE-2021-27065:
- If CVE-2021-27065 is detected, then investigate the logs specified for lines containing Set-OabVirtualDirectory. This indicates that a file was written to the server.
- Investigate web server directories for new or recently modified .aspx files or other file types that may contain unusual <script> blocks.
- This indicates an adversary may have dropped a web shell file. Below is an example of such a <script> block.
- If yes, continue to continue to the web shell remediation workflow.

Step 3 – Investigate CVE-2021-26857:
- If CVE-2021-26857 is detected, then investigate the collected logs labeled <servername>Cve-2021-26857.csv.
- This indicates an adversary may have run arbitrary code as SYSTEM.
- If yes, continue to continue to the web shell remediation workflow.
Step 4 – Investigate CVE-2021-26858:
- If CVE-2021-26858 is detected, then investigate the collected logs labeled <servername>Cve-2021-26858.log.
- Does the tool output any path other than *\Microsoft\ExchangeServer\V15\ClientAccess\OAB\Temp\*?
- This indicates an attacker may have written an arbitrary file.
- If yes, continue to continue to the web shell remediation workflow.
Step 5 – Investigate CVE-2021-26855:
- If CVE-2021-26855 is detected, then investigate the collected logs labeled <servername>Cve-2021-26855.csv.
- Does the tool output for AnchorMailbox contain Autodiscover.xml ONLY?
- This indicates an attacker is scanning your infrastructure as a precursor to additional compromise.
- If yes, continue to the scan remediation workflow.
- Does the tool output for AnchorMailbox contain /ews/exchange.asmx?
- This indicates an attacker may be exfiltrating your email.
- If yes, inspect the Exchange web services (EWS) logs in \V15\Logging\EWS to verify if the adversary accessed a mailbox, and then proceed to the corresponding remediation workflow.
What remediation steps should I take?
- The steps in Have I been compromised? section help establish the scope of possible exploitation: scanning, unauthorized email access, establishment of persistence via web shells, or post-exploitation activity.
- Follow applicable remediation workflows:
- Was post-compromise activity related to credential harvesting or lateral movement detected by Microsoft Defender for Endpoint or during manual investigation?
- Engage your incident response plan. Share the investigation details to your incident response team.
- If you are engaging with CSS Security or Microsoft Detection and Response Team (DART), and you are a Microsoft Defender for Endpoint customer, see instructions for onboarding Windows Server to Microsoft Defender for Endpoint.
- Were web shells detected?
- Clean and restore your Exchange Server:
- Preserve forensic evidence if your organization requires evidence preservation.
- Disconnect the Exchange Server from the network, either physically or virtually via firewall rules.
- Restart Exchange Server.
- Stop W3WP services.
- Remove any malicious ASPX files identified via the investigation steps above.
- Delete all temporary ASP.NET files on the system using the following script:
- Clean and restore your Exchange Server:
- Was post-compromise activity related to credential harvesting or lateral movement detected by Microsoft Defender for Endpoint or during manual investigation?
iisreset /stop
$tempAspDir = "$env:Windir\Microsoft.NET\Framework64\$([System.Runtime.InteropServices.RuntimeEnvironment]::GetSystemVersion())\Temporary ASP.NET Files"
mkdir 'C:\forensicbackup'
Copy-Item -Recurse -Path $tempAspDir -Destination 'C:\forensicbackup'
rm -r -Force $tempAspDir
iisreset /start
- Run a full EOMT.ps1 scan via “.\EOMT.ps1 -RunFullScan”. See Have I been compromised? for additional instructions for running EOMT.ps1.
- Apply Security Updates. See How do I mitigate the threat?
- Reset administrator credentials.
- Consider submitting suspected malicious files to Microsoft for analysis following this guidance: Submit files for analysis by Microsoft and include the string “ExchangeMarchCVE” in the Additional Information text box of the submission form.
- Was mailbox access and exfiltration detected?
- Disconnect Exchange Server from the network.
- Apply Security Updates.
- Run a full EOMT.ps1 scan via “.\EOMT.ps1 -RunFullScan”. Have I been compromised? for additional instructions for running EOMT.ps1.
- Resume operation.
- Was scan-only adversary behavior detected?
- Disconnect Exchange Server from the network.
- Apply Security Updates.
- Resume operation.
How can I better protect myself and monitor for suspicious activity?
- Additional protection and investigation capabilities are available if Microsoft Defender Antivirus and Microsoft Defender for Endpoint are running on the Exchange Server. If neither are yet installed, installing both now can provide additional protection moving forward and is strongly advised.
- If you are an existing Microsoft Defender for Endpoint customer but have Exchange servers that are not onboarded, see instructions for onboarding Windows Server to Microsoft Defender for Endpoint.
- If you are not an existing Microsoft Defender for Endpoint customer, Microsoft is making publicly available a 90-day Microsoft Defender for Endpoint trial offer exclusively to support commercial on-premises Exchange Server customers that require continuous investigation and additional post-compromise security event detection beyond what MSERT offers. Next, follow the steps for setting up Microsoft Defender for Endpoint and onboarding your Exchange Server.
Microsoft’s Detection and Response Team (DART)
Microsoft 365 Defender Team
CSS Security Incident Response
This blog and its contents are subject to the Microsoft Terms of Use. All code and scripts are subject to the applicable terms on Microsoft’s GitHub Repository (e.g., the MIT License).
Source :
https://msrc-blog.microsoft.com/2021/03/16/guidance-for-responders-investigating-and-remediating-on-premises-exchange-server-vulnerabilities/





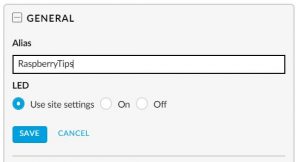
 (it’s available on Amazon if you don’t have one with your access point:
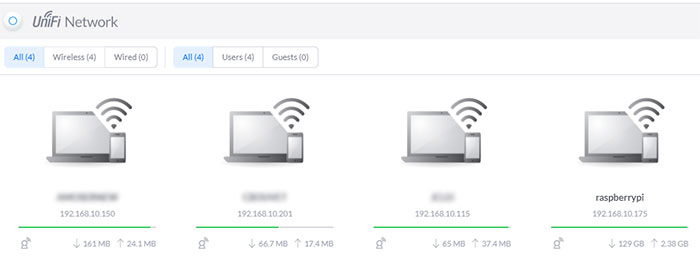
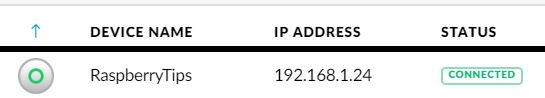
(it’s available on Amazon if you don’t have one with your access point: 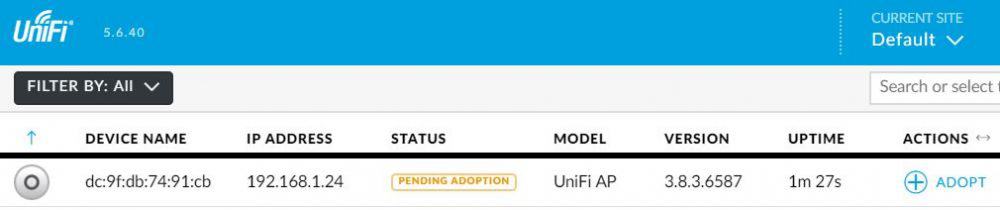 The controller is seeing it, but we need to tell that it’s an access point for this controller.
The controller is seeing it, but we need to tell that it’s an access point for this controller.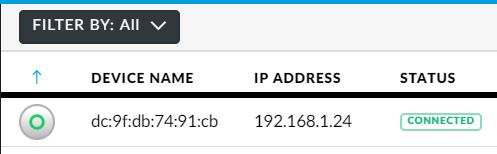
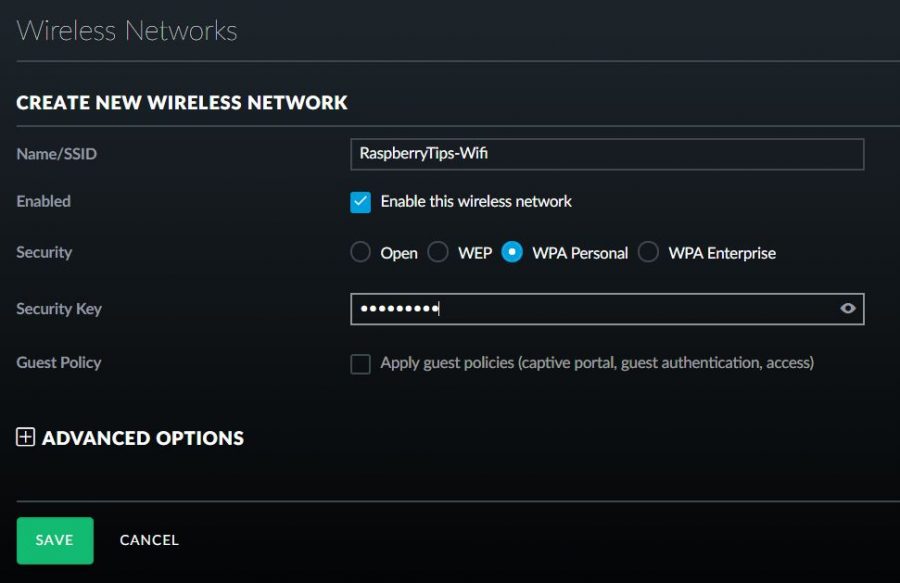 Choose WPA-Personal for security, WEP is not secure.
Choose WPA-Personal for security, WEP is not secure.