An update was added to the end of the article explaining that any Authenticode-signed file, including executables, can be modified to bypass warnings.
A new Windows zero-day allows threat actors to use malicious stand-alone JavaScript files to bypass Mark-of-the-Web security warnings. Threat actors are already seen using the zero-day bug in ransomware attacks.
Windows includes a security feature called Mark-of-the-Web (MoTW) that flags a file as having been downloaded from the Internet and, therefore, should be treated with caution as it could be malicious.
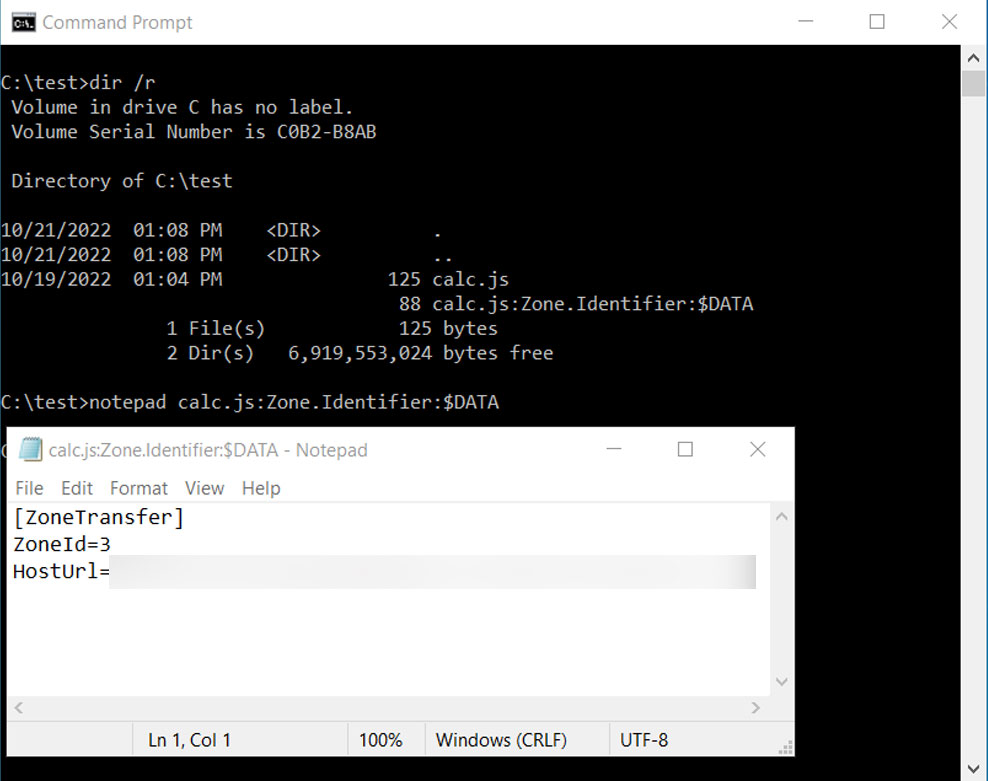
The MoTW flag is added to a downloaded file or email attachment as a special Alternate Data Stream called ‘Zone.Identifier,’ which can be viewed using the ‘dir /R’ command and opened directly in Notepad, as shown below.
Source: BleepingComputer
This ‘Zone.Identifier’ alternate data stream includes what URL security zone the file is from (three equals the Internet), the referrer, and the URL to the file.
When a user attempts to open a file with the Mark-of-the-Web flag, Windows will display a warning that the file should be treated with caution.
“While files from the Internet can be useful, this file type can potentially harm your computer. If you do not trust the source, do not open this software,” reads the warning from Windows.
.jpg)
Source: BleepingComputer
Microsoft Office also utilizes the MoTW flag to determine if the file should be opened in Protected View, causing macros to be disabled.
Windows MoTW bypass zero-day flaw
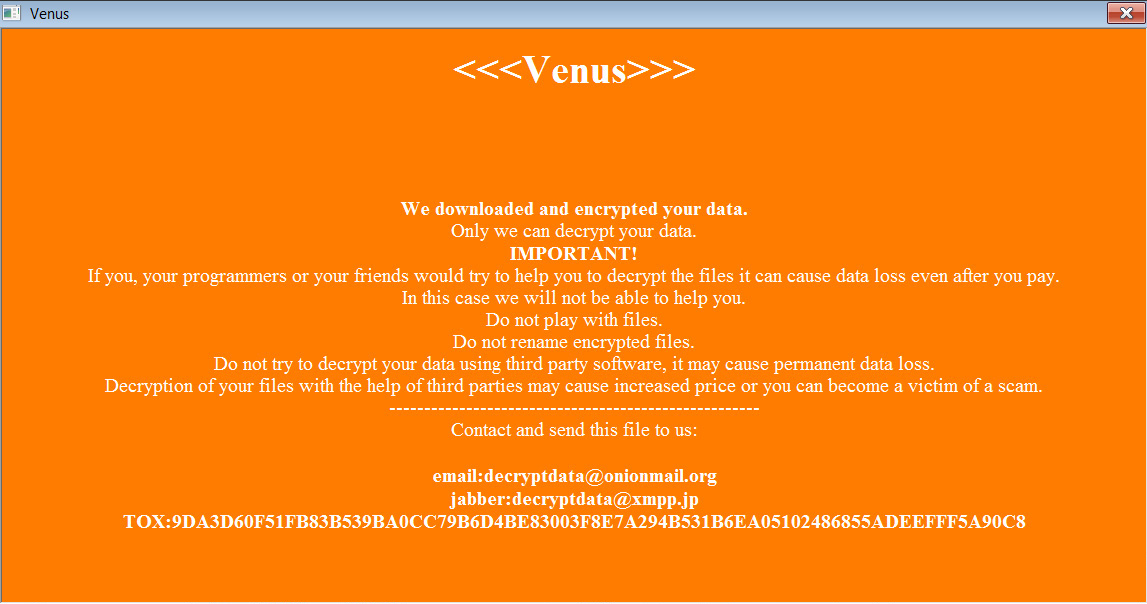
The HP threat intelligence team recently reported that threat actors are infecting devices with Magniber ransomware using JavaScript files.
To be clear, we are not talking about JavaScript files commonly used on almost all websites, but .JS files distributed by threat actors as attachments or downloads that can run outside of a web browser.
The JavaScript files seen distributed by the Magniber threat actors are digitally signed using an embedded base64 encoded signature block as described in this Microsoft support article.
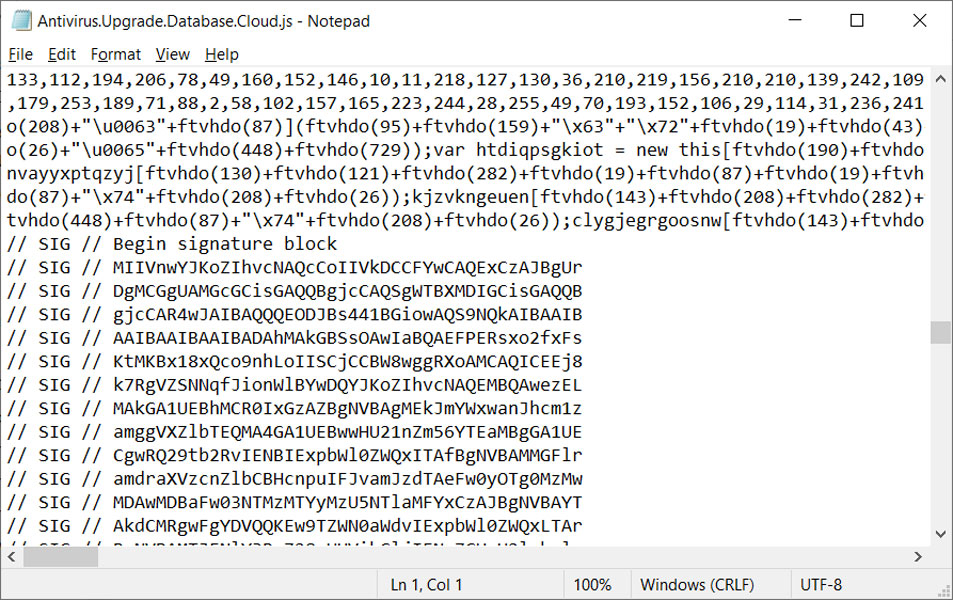
Source: BleepingComputer
AD
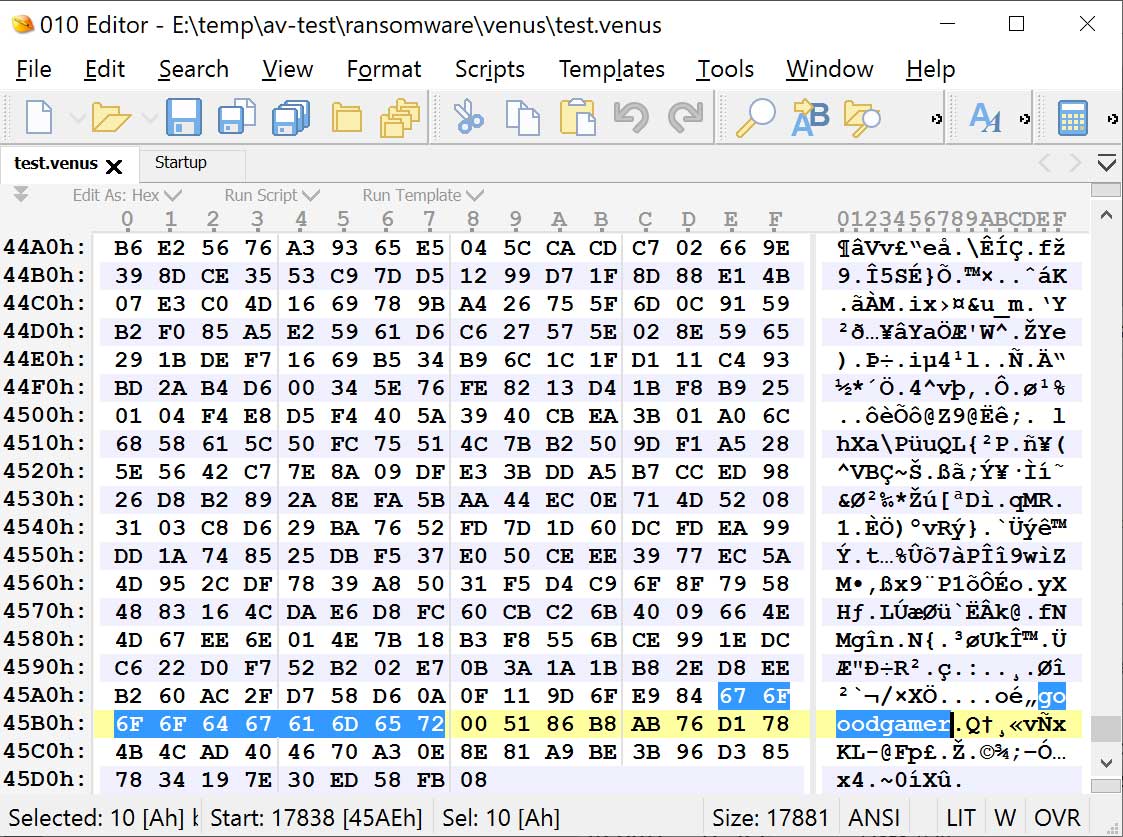
After being analyzed by Will Dormann, a senior vulnerability analyst at ANALYGENCE, he discovered that the attackers signed these files with a malformed key.
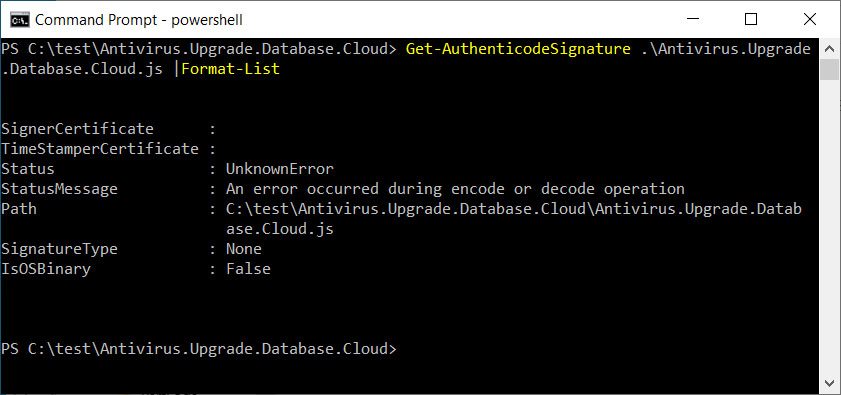
Source: BleepingComputer
When signed in this manner, even though the JS file was downloaded from the Internet and received a MoTW flag, Microsoft would not display the security warning, and the script would automatically execute to install the Magniber ransomware.
Dormann further tested the use of this malformed signature in JavaScript files and was able to create proof-of-concept JavaScript files that would bypass the MoTW warning.
Both of these JavaScript (.JS) files were shared with BleepingComputer, and as you can see below, they both received a Mark-of-the-Web, as indicated by the red boxes, when downloaded from a website.
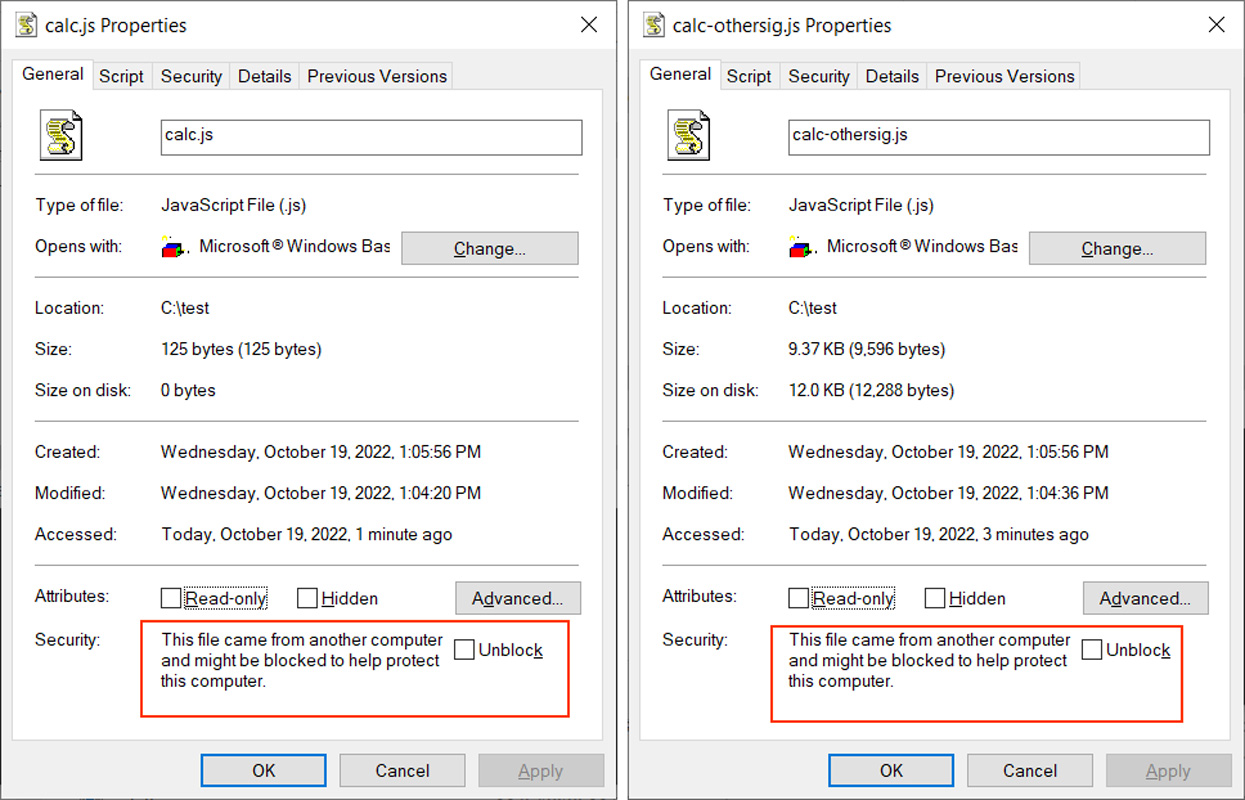
Source: BleepingComputer
The difference between the two files is that one is signed using the same malformed key from the Magniber files, and the other contains no signature at all.
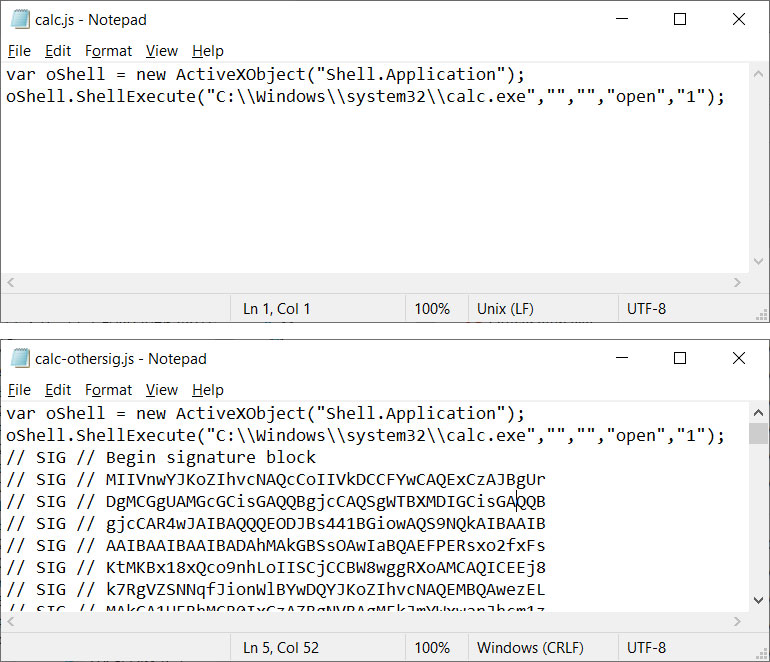
Source: BleepingComputer
When the unsigned file is opened in Windows 10, a MoTW security warning is properly displayed.
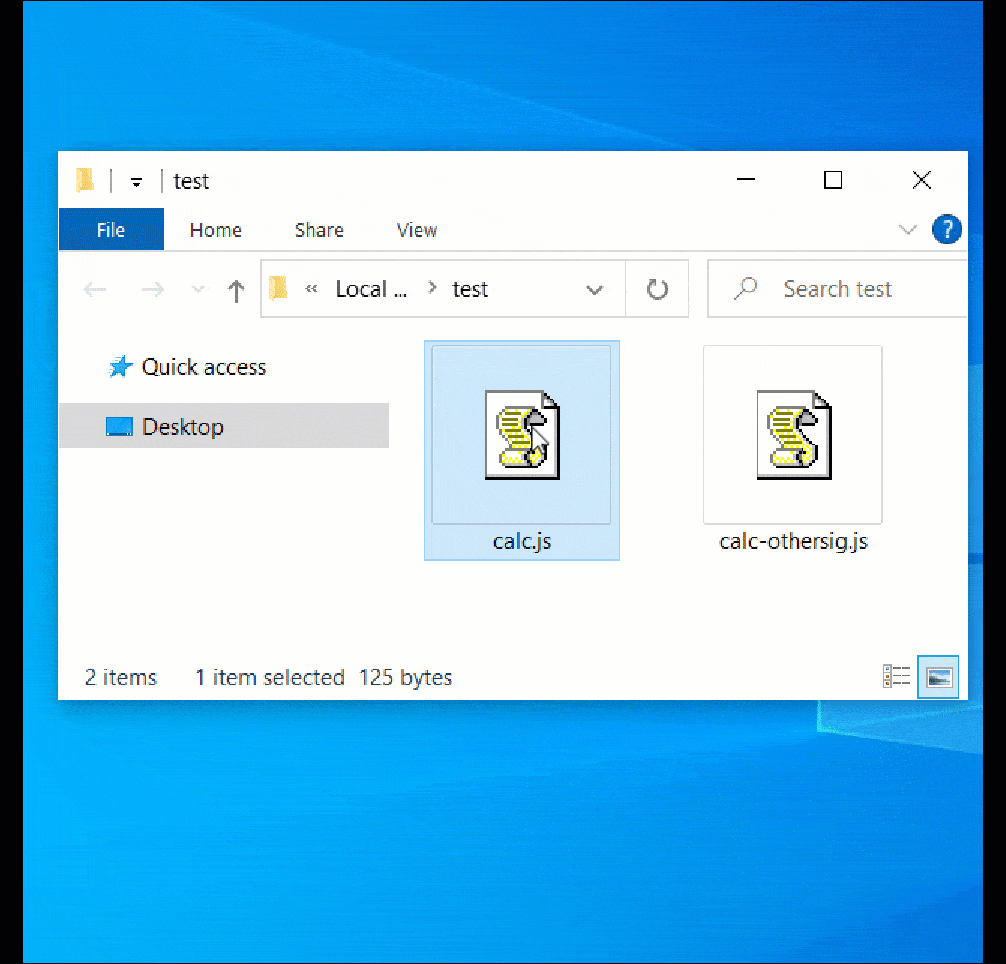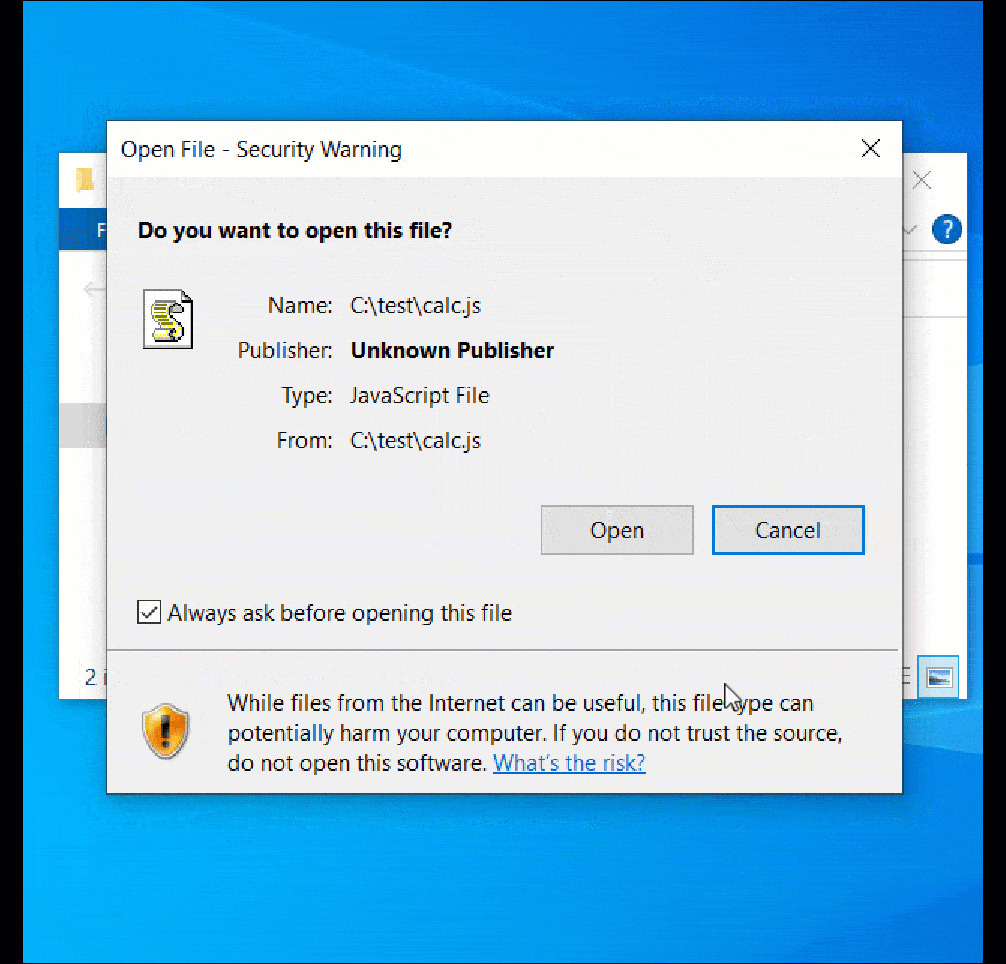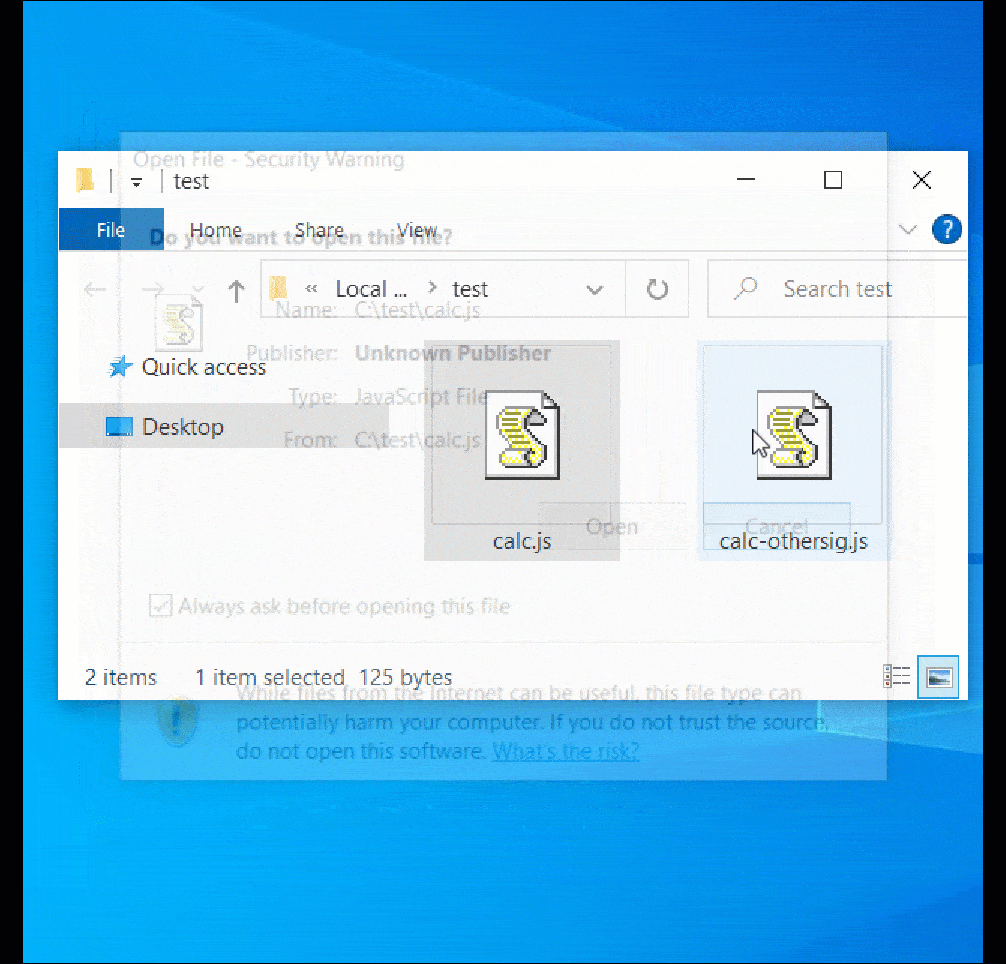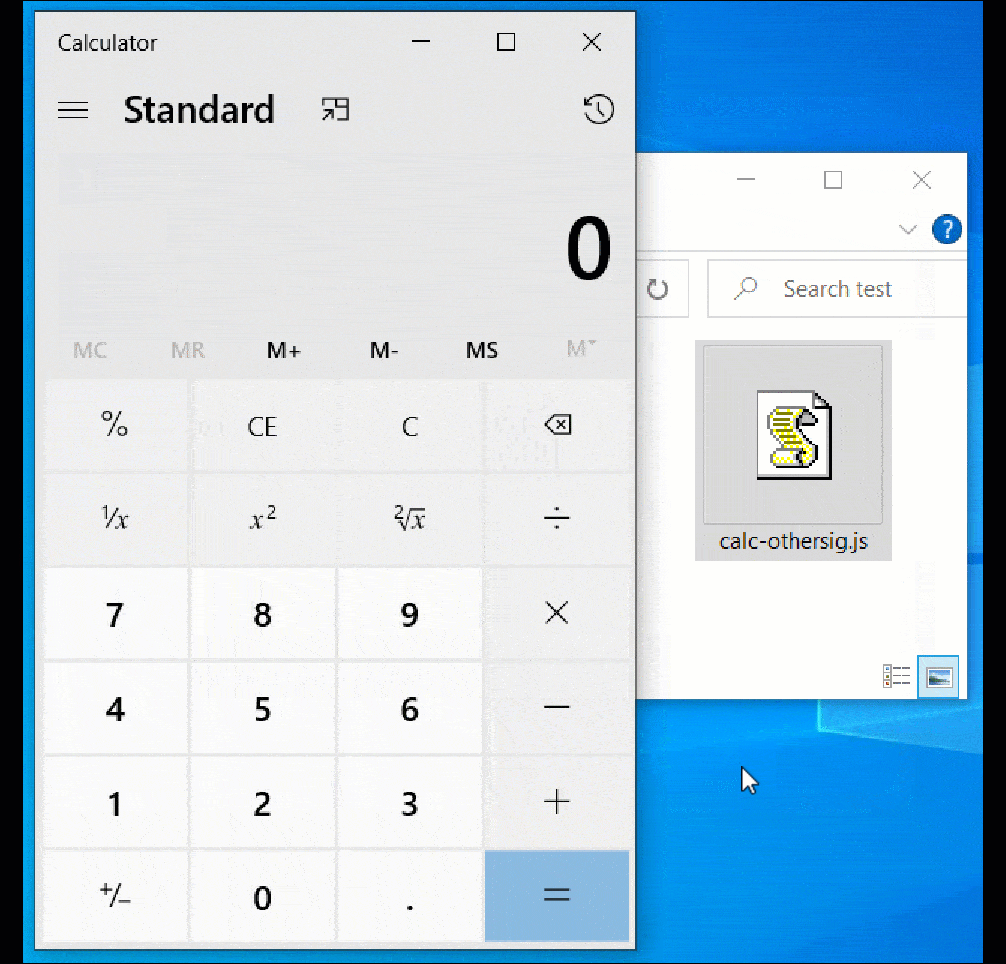
However, when double-clicking the ‘calc-othersig.js,’ which is signed with a malformed key, Windows does not display a security warning and simply executes the JavaSript code, as demonstrated below.
Source: BleepingComputer
Using this technique, threat actors can bypass the normal security warnings shown when opening downloaded JS files and automatically execute the script.
BleepingComputer was able to reproduce the bug in Windows 10. However, for Windows 11, the bug would only trigger when running the JS file directly from an archive.
Dormann told BleepingComputer that he believes this bug was first introduced with the release of Windows 10, as a fully patched Windows 8.1 device displays the MoTW security warning as expected.
https://platform.twitter.com/embed/Tweet.html?creatorScreenName=BleepinComputer&dnt=false&embedId=twitter-widget-0&features=eyJ0ZndfdGltZWxpbmVfbGlzdCI6eyJidWNrZXQiOlsibGlua3RyLmVlIiwidHIuZWUiLCJ0ZXJyYS5jb20uYnIiLCJ3d3cubGlua3RyLmVlIiwid3d3LnRyLmVlIiwid3d3LnRlcnJhLmNvbS5iciJdLCJ2ZXJzaW9uIjpudWxsfSwidGZ3X2hvcml6b25fdGltZWxpbmVfMTIwMzQiOnsiYnVja2V0IjoidHJlYXRtZW50IiwidmVyc2lvbiI6bnVsbH0sInRmd190d2VldF9lZGl0X2JhY2tlbmQiOnsiYnVja2V0Ijoib24iLCJ2ZXJzaW9uIjpudWxsfSwidGZ3X3JlZnNyY19zZXNzaW9uIjp7ImJ1Y2tldCI6Im9uIiwidmVyc2lvbiI6bnVsbH0sInRmd19jaGluX3BpbGxzXzE0NzQxIjp7ImJ1Y2tldCI6ImNvbG9yX2ljb25zIiwidmVyc2lvbiI6bnVsbH0sInRmd190d2VldF9yZXN1bHRfbWlncmF0aW9uXzEzOTc5Ijp7ImJ1Y2tldCI6InR3ZWV0X3Jlc3VsdCIsInZlcnNpb24iOm51bGx9LCJ0Zndfc2Vuc2l0aXZlX21lZGlhX2ludGVyc3RpdGlhbF8xMzk2MyI6eyJidWNrZXQiOiJpbnRlcnN0aXRpYWwiLCJ2ZXJzaW9uIjpudWxsfSwidGZ3X2V4cGVyaW1lbnRzX2Nvb2tpZV9leHBpcmF0aW9uIjp7ImJ1Y2tldCI6MTIwOTYwMCwidmVyc2lvbiI6bnVsbH0sInRmd19kdXBsaWNhdGVfc2NyaWJlc190b19zZXR0aW5ncyI6eyJidWNrZXQiOiJvbiIsInZlcnNpb24iOm51bGx9LCJ0ZndfdmlkZW9faGxzX2R5bmFtaWNfbWFuaWZlc3RzXzE1MDgyIjp7ImJ1Y2tldCI6InRydWVfYml0cmF0ZSIsInZlcnNpb24iOm51bGx9LCJ0ZndfdHdlZXRfZWRpdF9mcm9udGVuZCI6eyJidWNrZXQiOiJvbiIsInZlcnNpb24iOm51bGx9fQ%3D%3D&frame=false&hideCard=false&hideThread=false&id=1583055972280324097&lang=en&origin=https%3A%2F%2Fwww.bleepingcomputer.com%2Fnews%2Fsecurity%2Fexploited-windows-zero-day-lets-javascript-files-bypass-security-warnings%2F&sessionId=ad0d187be79e9f0d5b7b04498fef77964be23c7f&siteScreenName=BleepinComputer&theme=light&widgetsVersion=1c23387b1f70c%3A1664388199485&width=550px
According to Dormann, the bug stems from Windows 10’s new ‘Check apps and files’ SmartScreen feature under Windows Security > App & Browser Control > Reputation-based protection settings.
“This issue is in the new-as-of-Win10 SmartScreen feature. And disabling “Check apps and files” reverts Windows to the legacy behavior, where MotW prompts are unrelated to Authenticode signatures,” Dormann told BleepingComputer.
AD
“So that whole setting is unfortunately currently a tradeoff. On one hand, it does scan for baddies that are downloaded.”
“On the other, baddies that take advantage of this bug can get a LESS-SECURE behavior from Windows compared to when the feature is disabled.”
The zero-day vulnerability is particularly concerning as we know threat actors are actively exploiting it in ransomware attacks.
Dormann shared the proof-of-concept with Microsoft, who said they could not reproduce the MoTW security warning bypass.
However, Microsoft told BleepingComputer that they are aware of the reported issue and are investigating it.
Update 10/22/22
After the publication of this article, Dormann told BleepingComputer that threat actors could modify any Authenticode-signed file, including executables (.EXE), to bypass the MoTW security warnings.
To do this, Dormann says that a signed executable can be modified using a hex editor to change some of the bytes in the signature portion of the file and thus corrupt the signature.
https://platform.twitter.com/embed/Tweet.html?creatorScreenName=BleepinComputer&dnt=false&embedId=twitter-widget-1&features=eyJ0ZndfdGltZWxpbmVfbGlzdCI6eyJidWNrZXQiOlsibGlua3RyLmVlIiwidHIuZWUiLCJ0ZXJyYS5jb20uYnIiLCJ3d3cubGlua3RyLmVlIiwid3d3LnRyLmVlIiwid3d3LnRlcnJhLmNvbS5iciJdLCJ2ZXJzaW9uIjpudWxsfSwidGZ3X2hvcml6b25fdGltZWxpbmVfMTIwMzQiOnsiYnVja2V0IjoidHJlYXRtZW50IiwidmVyc2lvbiI6bnVsbH0sInRmd190d2VldF9lZGl0X2JhY2tlbmQiOnsiYnVja2V0Ijoib24iLCJ2ZXJzaW9uIjpudWxsfSwidGZ3X3JlZnNyY19zZXNzaW9uIjp7ImJ1Y2tldCI6Im9uIiwidmVyc2lvbiI6bnVsbH0sInRmd19jaGluX3BpbGxzXzE0NzQxIjp7ImJ1Y2tldCI6ImNvbG9yX2ljb25zIiwidmVyc2lvbiI6bnVsbH0sInRmd190d2VldF9yZXN1bHRfbWlncmF0aW9uXzEzOTc5Ijp7ImJ1Y2tldCI6InR3ZWV0X3Jlc3VsdCIsInZlcnNpb24iOm51bGx9LCJ0Zndfc2Vuc2l0aXZlX21lZGlhX2ludGVyc3RpdGlhbF8xMzk2MyI6eyJidWNrZXQiOiJpbnRlcnN0aXRpYWwiLCJ2ZXJzaW9uIjpudWxsfSwidGZ3X2V4cGVyaW1lbnRzX2Nvb2tpZV9leHBpcmF0aW9uIjp7ImJ1Y2tldCI6MTIwOTYwMCwidmVyc2lvbiI6bnVsbH0sInRmd19kdXBsaWNhdGVfc2NyaWJlc190b19zZXR0aW5ncyI6eyJidWNrZXQiOiJvbiIsInZlcnNpb24iOm51bGx9LCJ0ZndfdmlkZW9faGxzX2R5bmFtaWNfbWFuaWZlc3RzXzE1MDgyIjp7ImJ1Y2tldCI6InRydWVfYml0cmF0ZSIsInZlcnNpb24iOm51bGx9LCJ0ZndfdHdlZXRfZWRpdF9mcm9udGVuZCI6eyJidWNrZXQiOiJvbiIsInZlcnNpb24iOm51bGx9fQ%3D%3D&frame=false&hideCard=false&hideThread=true&id=1582493426494636032&lang=en&origin=https%3A%2F%2Fwww.bleepingcomputer.com%2Fnews%2Fsecurity%2Fexploited-windows-zero-day-lets-javascript-files-bypass-security-warnings%2F&sessionId=ad0d187be79e9f0d5b7b04498fef77964be23c7f&siteScreenName=BleepinComputer&theme=light&widgetsVersion=1c23387b1f70c%3A1664388199485&width=550px
Once the signature is corrupted, Windows will not check the file using SmartScreen, as if a MoTW flag was not present, and allow it to run.
“Files that have a MotW are treated as if there were no MotW if the signature is corrupt. What real-world difference that makes depends on what type of file it is,” explained Dormann.
Related Articles:
Magniber ransomware now infects Windows users via JavaScript files
Microsoft finally releases tabbed File Explorer for Windows 11
Windows Mark of the Web bypass zero-day gets unofficial patch
Microsoft: New Prestige ransomware targets orgs in Ukraine, Poland
Microsoft Exchange servers hacked to deploy LockBit ransomware
Source :
https://www.bleepingcomputer.com/news/security/exploited-windows-zero-day-lets-javascript-files-bypass-security-warnings/


.png)



 A confirmation message appears.
A confirmation message appears. If you cannot find the PSID, contact the disk manufacturer.
If you cannot find the PSID, contact the disk manufacturer.