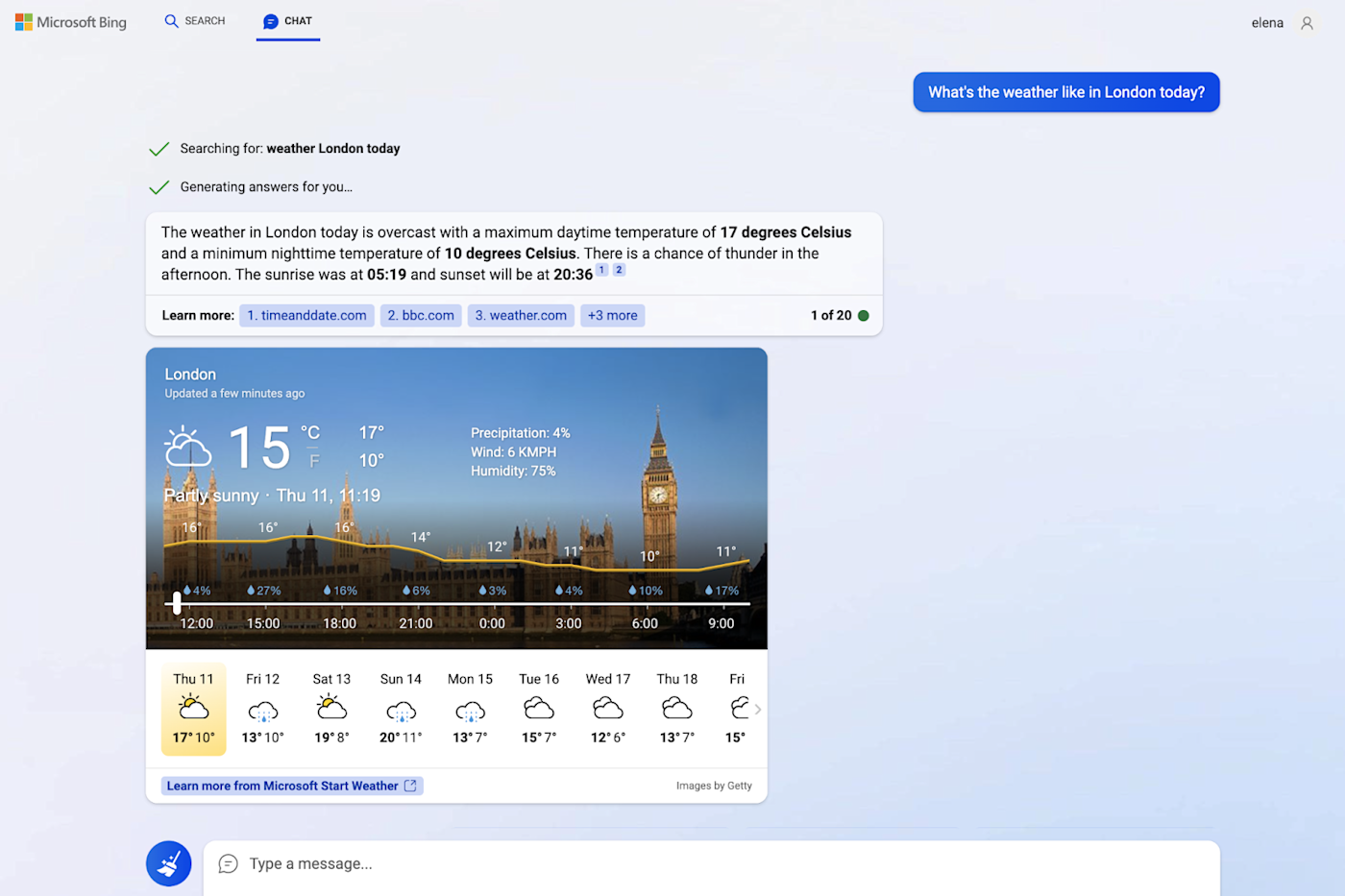
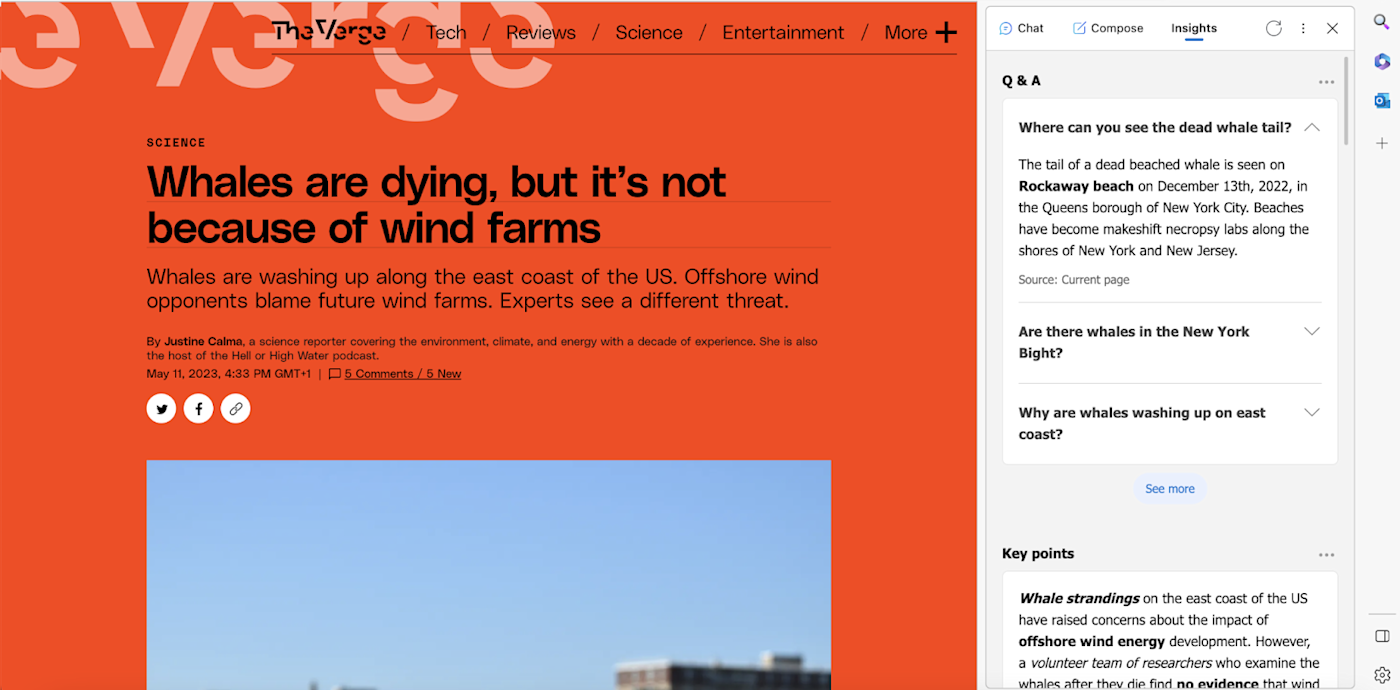
BY COLLINS AYUYA MAY 23, 2023
In the fast-paced realm of cyberspace where threats continue to multiply, firewall software represents a critical line of defense for businesses of all sizes.
Such programs function as digital gatekeepers, regulating the flow of inbound and outbound network traffic according to a set of rules defined by the user.
With the continued rise of data breaches, investing in the best firewall software isn’t a mere consideration; it’s a necessity.
That’s why we researched, analyzed, and selected the best firewall software solutions for 2023:
- Norton: Best for a comprehensive security suite (Read more)
- Fortinet: Best for scalability (Read more)
- GlassWire: Best for user-friendly interface (Read more)
- Cisco Secure Firewall Management Center: Best for centralized management and control (Read more)
- pfSense: Best open source solution (Read more)
- Sophos Firewall: Best for cloud-based management (Read more)
- ZoneAlarm: Best for personal use (Read more)
Best firewall software comparison
Before delving into each firewall software’s in-depth review, let’s take a quick overview of what each product offers via a comparison chart:
| Comprehensive security suite | Scalability | User-friendly interface | Robust features | Cloud-based management | Open-source | Starting price | |
|---|---|---|---|---|---|---|---|
| Norton | ✔ | ✘ | ✔ | ✔ | ✔ | ✘ | $49.99 for 5 devices for the first year |
| FortiGate | ✔ | ✔ | ✘ | ✔ | ✔ | ✘ | $250/year for home office |
| GlassWire | ✘ | ✔ | ✔ | ✔ | ✘ | ✘ | Free, or $2.99/month/license |
| Cisco Secure Firewall Management Center | ✔ | ✔ | ✔ | ✔ | ✔ | ✘ | Contact Cisco |
| pfSense | ✔ | ✔ | ✘ | ✔ | ✘ | ✔ | Free |
| Sophos Firewall | ✔ | ✔ | ✔ | ✔ | ✔ | ✘ | Contact Sophos |
| ZoneAlarm | ✔ | ✘ | ✔ | ✘ | ✔ | ✘ | Free, or $22.95/year for 1 PC |
Jump to:
- Key features of firewall software
- Benefits of working with firewall software
- How to choose the best firewall software for your business
- Frequently Asked Questions (FAQ)
- Methodology

Norton
Best for a comprehensive security suite
Norton is a household name in cybersecurity that has long been delivering top-tier firewall software that signifies its wealth of experience in the sector.
The standout attribute of Norton is its comprehensive security suite, going beyond basic firewall protection to incorporate a smart firewall and intrusion prevention system (IPS), antivirus capabilities, identity theft protection, and even a VPN offering.
All that adds up to a holistic solution for businesses desiring a single-stop security software.
Pricing
Norton’s Smart Firewall is included in Norton 360, whose pricing plans at the time of writing are:
- Deluxe: $49.99 for the first year for 5 PCs, Macs, tablets, or phones.
- Select + LifeLock: $99.99 for the first year for 10 PCs, Macs, tablets, or phones.
- Advantage + LifeLock: $191.88 for the first year for 10 PCs, Macs, tablets, or phones.
- Ultimate Plus + LifeLock: $299.88 for the first year for unlimited PCs, Macs, tablets, or phones.
Features
- Advanced smart firewall with customizable rules, allowing businesses to modify access based on their specific needs, thus providing a higher level of personalized security.
- Integrated VPN for safe browsing ensures users can access the internet securely without worrying about potential threats or privacy breaches.
- Identity theft protection is another vital feature, which helps safeguard sensitive personal and business data from potential hackers.
- SafeCam feature prevents unauthorized access to your webcam, thwarting any potential spying or privacy intrusions.
- Automatic updates ensure that your protection is always up-to-date, reinforcing defenses against new and evolving threats.
Pros
- Norton offers a comprehensive security suite, providing a broad spectrum of protective measures beyond the typical firewall, creating a fortified line of defense against a myriad of cyber threats.
- The interface is easy to navigate, making the process of setting up and managing the firewall less complex and more user-friendly, even for those with limited technical knowledge.
- It provides 24/7 customer support, ensuring that you’ll have access to assistance whenever you need it, regardless of the hour or day.
Cons
- While perfect for small to mid-sized businesses, Norton might not be as scalable for larger businesses with a vast network of devices, potentially limiting its effectiveness in such an environment.
- Depending on your requirements, the subscription can become expensive with add-ons, which might be a drawback for businesses on a tight budget.

Fortinet
Best for scalability
Fortinet is a well-regarded player in the cybersecurity arena and its firewall software exemplifies its commitment to delivering high-quality solutions. FortiGate, Fortinet’s firewall offering, is recognized for its advanced firewall solutions that are scalable and robust.
Particularly useful for growing businesses, FortiGate brings forward top-notch features that can effortlessly adapt to the needs of expanding network infrastructures.
Pricing
Fortinet offers a variety of solutions priced broadly to accommodate all business sizes—from $250 for home office to $300,000 for large enterprises. Contact Fortinet for accurate pricing information.
Features
- FortiGate offers an advanced firewall with extensive protection against incoming threats, thus maintaining the security of your network.
- With scalability at its core, FortiGate can adapt and grow along with your business, addressing increasing security demands seamlessly.
- Smooth integration with other Fortinet security solutions, enabling a comprehensive security ecosystem for your business.
- FortiGate Cloud-Native Firewall offers high resiliency to ease security delivery across cloud networks and availability zones at scale.
- Automatic updates keep the firewall current and equipped to deal with the latest threats, ensuring your network’s protection remains robust.
Pros
- Fortinet’s robust firewall features deliver comprehensive security for your network, providing the necessary defenses to ward off potential threats.
- With a strong focus on scalability, Fortinet is an ideal choice for rapidly growing businesses that need a security solution to match their expanding network.
- The software’s high-performance nature means that it delivers robust security without hampering your network’s speed or efficiency.
Cons
- Despite (or because of) offering a wealth of features, Fortinet’s interface may not be as user-friendly as some other options, potentially causing difficulties for those without substantial technical knowledge.
- While Fortinet offers a range of pricing options, the cost can quickly escalate for larger networks or when additional features are included, which may not suit budget-conscious businesses.
- Pricing information is not transparent and requires negotiation. Your mileage may vary.

GlassWire
Best for user-friendly interface
GlassWire is an elegant and visually appealing firewall software that provides comprehensive network monitoring capabilities.
It uniquely combines a network monitor and firewall, offering users a clear visual representation of their network activity. This functionality helps users to understand their online behavior and potential threats in a way that’s easy to interpret.
Pricing
GlassWire offers a tiered pricing model:
- Free: provides limited features, perfect for individual users or small businesses.
- Premium: Starts at $2.99 per month per license, paid annually. Its premium tier plans suitable for business range between 10 and 200 licenses.
Features
- Real-time and detailed visualization of your current and past network activity, offering an intuitive and easy-to-understand representation of what’s happening on your network.
- Built-in firewall that allows users to easily monitor applications using the network and block any suspicious activity, providing a comprehensive network security solution.
- A unique “Incognito” mode for users who do not want certain network activities to appear on the network graph, ensuring user privacy.
- Firewall profiles to instantly switch between different environments, such as public and private networks.
- The network time machine feature allows users to go back in time up to 30 days to see what their computer or server was doing in the past.
Pros
- GlassWire offers a beautifully designed, user-friendly interface that presents complex network security information in a visually appealing and understandable way.
- Its comprehensive network monitoring capability allows users to understand their online behavior, identify patterns and detect anomalies.
- The software’s built-in firewall offers users the flexibility to control which applications can access the network, enhancing the overall security of their systems.
Cons
- The software requires a moderate amount of system resources to run efficiently, which might be an issue for systems with limited resources.
- Although GlassWire’s visualizations are beautiful and informative, some users may find them overwhelming and would prefer a more traditional interface.

Cisco Secure Firewall Management Center
Best for centralized management and control
The Cisco Secure Firewall Management Center provides a comprehensive solution for centralized control and management of security policies. It enhances the overall efficiency of network administration by offering a unified platform to manage multiple Cisco security appliances.
Businesses that use a variety of Cisco security tools will find this a valuable addition to streamline operations and enhance control.
Pricing
Cisco Secure Firewall Management Center’s pricing depends on the scale of operations and the specific needs of a business. For detailed and customized pricing information, you can directly contact Cisco or its partners.
Features
- A unified management console that can control a wide range of Cisco security appliances, reducing the complexity associated with managing multiple devices.
- Advanced threat detection and analysis capabilities, enabling administrators to swiftly identify and respond to security incidents.
- Flexible deployment options, including on-premises, virtual and cloud-based solutions, catering to various operational needs and preferences.
- Comprehensive policy management, allowing administrators to efficiently establish and enforce security policies across their Cisco security infrastructure.
- Integration with other Cisco security tools, such as Cisco Threat Response, provides a cohesive and powerful security solution.
Pros
- The ability to manage multiple Cisco security appliances from a single platform is a significant advantage, especially for larger enterprises managing complex security infrastructures.
- Cisco Secure Firewall Management Center offers advanced threat detection and analysis capabilities, aiding in swift and efficient incident response.
- Its flexible deployment options cater to diverse operational needs, providing convenience and ease of setup to businesses of all sizes.
Cons
- Although powerful, the platform may require a steep learning curve, particularly for those who are new to Cisco’s ecosystem.
- Some users have reported a desire for more customization options within the management interface to meet their specific operational needs.
- Pricing information is not transparent and requires negotiation. Your mileage may vary.

pfSense: Best open source solution
pfSense is an open-source firewall software solution that is highly customizable, suitable for tech-savvy businesses that prefer having the flexibility to tailor their firewall to specific needs. It’s built on the FreeBSD operating system, offering a comprehensive range of features for network management and security.
Pricing
As an open-source platform, pfSense is free to download and use. However, Netgate, the company behind pfSense, offers paid support and services, including hardware solutions integrated with pfSense software.
Features
- A wide array of networking functionalities, including firewall, VPN, and routing services, ensuring comprehensive network protection.
- Being open-source, it offers extensive customization options, allowing businesses to tailor the software to their specific needs.
- Supports a large selection of third-party packages for additional features, granting more flexibility in expanding its capabilities.
- Detailed network monitoring and reporting tools, allowing for granular insight into network traffic and potential security threats.
- It has a community-backed development model, ensuring continuous improvements and updates to its features.
Pros
- pfSense’s open-source nature allows for extensive customization, giving businesses control over how they want to configure their firewall.
- The software provides a comprehensive set of features, ensuring thorough network protection and management.
- Its support for third-party packages allows for the addition of further functionalities, enhancing its overall capabilities.
Cons
- The configuration of pfSense can be quite complex, particularly for users without a strong technical background, which could pose a challenge for some businesses.
- The user interface, while functional, may not be as polished or intuitive as some commercial firewall solutions.
- As with many open-source projects, while there’s a supportive community, professional customer service might not be as accessible as with commercial solutions.

Sophos Firewall
Best for cloud-based management
Sophos Firewall brings a fresh approach to the way you manage your firewall and how you can detect and respond to threats on your network.
Offering a user-friendly interface and robust features, this product provides businesses with an effective and efficient solution for their network security needs. It’s a versatile solution that not only offers traditional firewall capabilities but also integrates innovative technologies to ensure all-round security.
Pricing
Sophos does not publicize pricing information, because their solutions are provided by resellers and can vary depending on the business’s size, needs, and location. You can contact them directly for accurate pricing information.
Features
- All-in-one solution by integrating advanced threat protection, IPS, VPN, and web filtering in a single comprehensive platform, thereby providing robust security for your network.
- Deep learning technology and threat intelligence, both of which work in synergy to identify and respond to threats before they can cause damage, offering advanced protection against malware, exploits, and ransomware.
- User-friendly interface that simplifies configuration and management tasks, making it easier for users to set up security policies and monitor network activities.
- Synchronized Security technology that facilitates communication between your endpoint protection and your firewall, creating a coordinated defense against cyber threats.
- The Sophos Firewall comes with an effective cloud management platform, allowing administrators to remotely manage the system, configure settings, and monitor network activity.
Pros
- A user-friendly interface that simplifies the process of setting up and managing network security policies, making it suitable for businesses with limited technical expertise.
- It integrates advanced protection capabilities, such as threat intelligence and deep learning technology, to provide robust defense against sophisticated cyber threats.
- This firewall software’s unique Synchronized Security feature offers a coordinated and automated response against threats, enhancing the overall effectiveness of your network security.
Cons
- Some users have reported that while the user interface is intuitive, it might take some time to navigate due to the depth of features available.
- The initial setup and configuration might require technical expertise, although Sophos provides comprehensive resources and customer support to guide users.
- Although Sophos’ site advertises “Simple Pricing,” their costs are not in fact transparent and will require negotiating a quote. Your mileage may vary.

ZoneAlarm
Best for personal use
ZoneAlarm is an excellent choice for personal use and small businesses due to its simplicity and effectiveness.
With a robust set of features and an intuitive interface, it provides robust protection without requiring extensive technical knowledge. Its reputation as a reliable firewall solution makes it an attractive choice for users seeking to safeguard their systems from various threats.
Pricing
ZoneAlarm offers both free and premium versions of their firewall software. The free version provides basic protection, while the Pro Firewall version, which comes at a yearly subscription fee starting from $22.95 for 1 PC, offers advanced features such as zero-day attack protection and full technical support.
Features
- Robust two-way firewall protection, preventing unauthorized access to your network while also stopping malicious applications from sending out your data.
- Advanced privacy protection feature that protects your personal information from phishing attacks.
- Unique ID Lock feature that keeps your personal information safe.
- ZoneAlarm boasts an Anti-Phishing Chrome Extension that detects and blocks phishing sites, protecting your information online.
- The premium version offers advanced real-time antivirus protection, ensuring that your system is continuously protected from threats.
Pros
- ZoneAlarm offers a straightforward interface and setup process, making it an ideal choice for users who lack advanced technical skills.
- The software provides a comprehensive suite of features, including robust firewall protection, advanced privacy tools and real-time antivirus capabilities.
- ZoneAlarm’s ID Lock feature is a standout, helping to ensure the security of personal data.
Cons
- While ZoneAlarm offers robust features, its protection level may not be adequate for large enterprises or businesses with complex network architectures.
- Some users have reported that the software can be resource-intensive, potentially slowing down system performance.
Key features of firewall software
When choosing the best firewall software for your business, there are key features you should consider. These range from the extent of the security suite to scalability and cloud-based management, all of which play a significant role in how effectively the software will serve your needs.
Comprehensive security suite
A comprehensive security suite is more than just a basic firewall. It includes additional layers of security like antivirus capabilities, identity theft protection, and a VPN.
The best firewall software solutions should deliver this kind of comprehensive coverage, protecting against a wide variety of threats and helping you maintain the security of your entire network. Norton, Cisco, and Sophos firewalls excel in this area.
Scalability
Scalability is particularly important for businesses that are growing or plan to grow. As the size of your network increases, your security needs will change and become more complex.
Firewall software like FortiGate and pfSense are designed with scalability in mind, allowing them to adapt to the increasing security demands of your expanding network.
User-friendly interface
A user-friendly interface is crucial, especially for those who may not have a lot of technical expertise. Firewall software should be easy to navigate and manage, making the process of setting up and adjusting the firewall less daunting.
Norton excels in this area, with an intuitive interface that is straightforward to use. GlassWire, while not as intuitive, also offers an attractive and convenient interface.
Robust features
Having robust features in firewall software is key to ensuring comprehensive protection. This includes an advanced firewall with extensive customizable rules, IPS, and threat detection capabilities.
The most robust firewall solutions include Norton, FortiGate, Cisco, and Sophos, as well as pfSense, although you’ll have to do some legwork to program the latter in particular.
Cloud-based management
Cloud-based management is a significant advantage in today’s digital landscape. It allows for the remote configuration and monitoring of your firewall, making it easier to manage and adjust as needed. This feature is particularly beneficial for businesses with remote workers or multiple locations.
Norton, FortiGate, Cisco, Sophos, and ZoneAlarm all provide this capability.
Advanced firewall protection
Advanced firewall protection includes capabilities like deep packet inspection, which examines data packets to detect malware that could otherwise bypass standard firewalls. This kind of advanced protection is vital to secure your network from sophisticated threats. Most of the firewalls in this list offer advanced, next-generation capabilities.
Integration
Integration capabilities are crucial as they allow your firewall software to work in harmony with other security solutions you might have in place. Cisco firewalls, as you might expect, integrate seamlessly with other Cisco solutions, but can falter when trying to integrate with third-party solutions. On the other hand, thanks to its open-source nature, pfSense can be configured to integrate very broadly.
By considering these features when choosing your firewall software, you can ensure that you select a solution that meets the specific needs of your business, provides comprehensive protection and offers room for growth and adaptation as your business evolves.
Benefits of working with firewall software
Employing robust firewall software within your network infrastructure brings along a myriad of benefits that contribute to the overall security and efficiency of your business operations, from enhanced network security and data protection to reduced downtime and regulatory compliance.
Enhanced network security
Perhaps the most fundamental advantage of using firewall software is the enhanced network security it provides. Firewall software acts as the first line of defense against potential threats, including hackers, viruses, and other cyberattacks.
By monitoring and controlling incoming and outgoing network traffic based on predetermined security rules, firewall software ensures that only safe connections are established, thus protecting your network.
Data protection
With the increasing incidence of data breaches and cyber theft, data protection is more crucial than ever. Firewall software plays a pivotal role in safeguarding sensitive data from being accessed or stolen by unauthorized users.
By blocking unauthorized access, it ensures the safety of important information and reduces the risk of data breaches.
Traffic management
Firewall software is not only about protection but also about managing and optimizing the network traffic. Features like bandwidth management can be leveraged to allocate network resources effectively and ensure the smooth functioning of your online operations.
Real-time security updates
With the constantly evolving threat landscape, maintaining up-to-date security measures is vital. Firewall software frequently receives real-time security updates, which help to protect your network against the latest threats. This ensures that your network remains secure against even the most recent forms of cyberattacks.
Reduced downtime
Downtime can be a significant issue for any business, leading to financial losses and damage to reputation. By proactively identifying and preventing potential threats, firewall software can significantly reduce the risk of system outages, leading to increased uptime and reliability.
Scalability
As your business grows, so does the complexity and the scope of your network. Scalable firewall software grows with your business, adjusting to the increased demands and providing consistent protection despite the expanding network size. This makes it a cost-effective solution that can support your business in the long term.
Regulatory compliance
Many industries have regulations in place requiring businesses to protect sensitive data. Firewall software helps meet these regulatory requirements by providing robust security measures that prevent data breaches and protect client and customer information.
Incorporating firewall software into your network infrastructure is a critical step towards securing your business in an increasingly digital world. The benefits it offers are invaluable, providing not just enhanced protection, but also efficiency and adaptability that can significantly contribute to your business’s success.
How to choose the best firewall software for your business
Choosing the best firewall software for your business involves a careful examination of your specific needs and security requirements.
- Size and security level: The size and nature of your business, the sensitivity of your data, and the extent of your network operations are crucial factors that determine what kind of firewall software will be the most beneficial.
- Comprehensive features: Moreover, you should consider firewall solutions that offer a comprehensive suite of security features, such as VPN services, antivirus protection, and advanced threat detection capabilities.
- Scalability: The scalability of a firewall software solution is important, particularly for growing businesses. Opt for software that can seamlessly adapt to the expanding needs of your network, providing reliable protection irrespective of your business size.
- Interface: Unless you have a robust, well-trained IT department, the interface of your chosen software will need to be user-friendly and easily manageable, even for those with minimal technical expertise.
- Cloud-based management: Features that allow for remote configuration and monitoring are highly beneficial in the current era of remote work. These features offer the flexibility of managing your network’s security from any location, improving overall efficiency.
- Integration: Your chosen software should integrate smoothly with your existing security infrastructure to create a comprehensive, effective security system.
- Support: Solid customer support from the vendor is also crucial to navigating any issues that may arise during setup or throughout the software’s lifespan.
Choosing firewall software is an investment in your business’s security, so take the time to evaluate each option thoroughly.
Frequently Asked Questions (FAQs)
Who should use firewall software?
Any individual, business, or organization that uses a network or the internet should consider using firewall software. Whether you’re a small business owner, a large corporation, or a home user, a firewall can provide essential protection against unauthorized access and various cyber threats.
Where are firewalls located on a network?
Firewalls are typically located at the edge of a network, serving as a barrier between a trusted internal network and an untrusted external network, such as the internet. They can also be positioned between different parts of an organization’s networks to control access.
Are there any downsides to using a firewall?
While firewalls are essential for network security, they can occasionally block legitimate traffic if the security settings are too restrictive. Additionally, managing and maintaining a firewall can require technical expertise. However, the benefits of using a firewall far outweigh these potential challenges.
How often should a firewall be updated?
Firewall software should be updated regularly to ensure it can protect against the latest threats. Many firewall providers release updates regularly and many firewalls are set to update automatically. However, it’s a good idea to check for updates manually periodically to ensure your firewall is up-to-date.
What is firewall software’s role in regulatory compliance?
For many businesses, especially those in regulated industries like healthcare or finance, firewall software plays a critical role in meeting compliance requirements. Regulations like the Health Insurance Portability and Accountability Act (HIPAA) or the General Data Protection Regulation (GDPR) require robust data protection measures, which includes network security provided by a firewall.
Can firewall software protect against all cyber threats?
While firewall software provides a strong layer of protection, it’s not a panacea for all cyber threats. Some sophisticated threats, like targeted phishing attacks or insider threats, require additional security measures. It’s essential to have a comprehensive security strategy in place that includes firewall software, antivirus software, strong access controls, and user education about safe online practices.
Methodology
To deliver this list, we based our selection on an examination of firewall software features and overall reputation in addition to their ease of use, quality of customer support, and value for money.
This information is available in user reviews as well as official product pages and documentation. Nonetheless, we encourage you to conduct your own research and consider your unique requirements when choosing a firewall software solution.
Bottom line: Choosing the best firewall software for your business
The evolving threat landscape necessitates a robust and reliable firewall solution for both personal use and businesses of all sizes. Based on the products listed, it’s evident that several excellent options exist in the market, each with its own unique strengths and capabilities.
Choosing the best firewall software ultimately depends on your requirements, the nature of the network environment, and the budget at hand. It’s essential to consider each product’s features, pros, and cons, and align them with your individual or business needs.
The chosen solution should provide comprehensive protection, be user-friendly, and ideally offer scalability for future growth. Whether it’s for personal use or to protect a multilayered enterprise network, there’s a firewall solution out there that fits the bill.
Also see
Firewalls come in all shapes and sizes. Here’s a look at eight different types of firewalls.
We also did a review of the best firewalls for small and medium-sized businesses.
And once you’ve selected your firewall, make sure you define and implement a clear, strong firewall policy to back it up—as well as setting robust firewall rules to govern the software.
Source :
https://www.enterprisenetworkingplanet.com/guides/best-firewall-software/