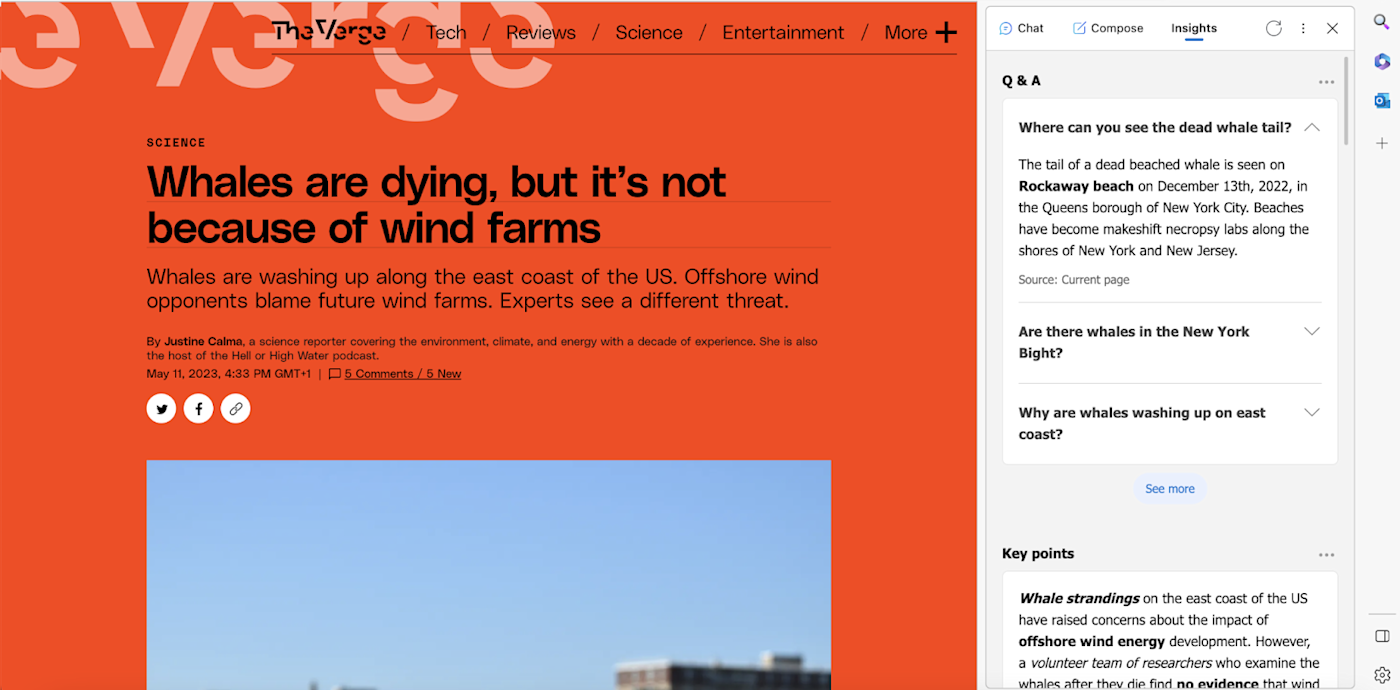
BY KIHARA KIMACHIA
MAY 30, 2023
Network scanning tools are a critical investment for businesses in this era of increasing cyber threats. These tools perform an active examination of networks to identify potential security risks and help IT administrators maintain the health and security of their networks.
As businesses become more digital and interconnected, the demand for such tools has significantly increased. To help businesses sort through the plethora of these solutions available on the market, we’ve narrowed down the list to eight top products and their ideal use cases.
Here are our picks for the top network scanning software:
- Burp Suite: Best for comprehensive web vulnerability scanning (Read more)
- Detectify: Best for ease of use and automation (Read more)
- Intruder: Best for cloud-based network security (Read more)
- ManageEngine OpManager: Best for real-time network monitoring (Read more)
- Tenable Nessus: Best for vulnerability analysis (Read more)
- Pentest Tools: Best for penetration testing (Read more)
- Qualys VMDR: Best for cloud security compliance (Read more)
- SolarWinds ipMonitor: Best for large-scale enterprise networks (Read more)
Top network scanning tools and software comparison
| Vulnerability Scanning | Real-time Network Monitoring | Penetration Testing | Compliance Assurance | Integration with Other Tools | Ease of Use | Range of Vulnerabilities Detected | Scalability | Pricing (Starting) | |
|---|---|---|---|---|---|---|---|---|---|
| Burp Suite | ✔ | ✘ | ✔ | ✔ | ✔ | Moderate | High | High | $1,999/yr |
| Detectify | ✔ | ✔ | ✘ | ✔ | ✔ | High | Moderate | High | $89/mo. |
| Intruder | ✔ | ✔ | ✔ | ✔ | ✔ | High | High | High | $160/mo. |
| Manage Engine OpManager | ✔ | ✔ | ✘ | ✔ | ✔ | Moderate | Moderate | High | $245 |
| Tenable Nessus | ✔ | ✘ | ✔ | ✔ | ✔ | High | High | High | $4,990/yr |
| Pentest Tools | ✔ | ✔ | ✔ | ✔ | ✔ | Moderate | High | Moderate | $72/mo. |
| Qualys VMDR | ✔ | ✔ | ✘ | ✔ | ✔ | Moderate | High | High | $6,368/yr |
| SolarWinds ipMonitor | ✔ | ✔ | ✘ | ✔ | ✔ | High | Moderate | High | $1,570/yr |
Jump to:
- Key features of network scanning tools and software
- How to choose the best network scanning software for your business
- Frequently Asked Questions (FAQ)
- Methodology
Burp Suite
Best for comprehensive web vulnerability scanning

Burp Suite is a trusted tool among IT professionals for its robust web vulnerability scanning capabilities. It identifies security holes in web applications and is particularly well-suited for testing complex applications.
Pricing
The vendor has three enterprise pricing options as follows:
- Pay as you scan: This tier starts at $1,999 per year plus $9 per hour scanned. It includes unlimited applications and users.
- Classic: This tier is priced at $17,380 per year and includes 20 concurrent scans, unlimited applications and unlimited users.
- Unlimited: This is the superior plan and is priced at $49,999 per year. It includes unlimited concurrent scans, applications, and users.
Features
- Out-of-band Application Security Testing (OAST) added to dynamic scans for accurate identification of vulnerabilities.
- Easy setup with point-and-click scanning or trigger via CI/CD.
- Recurring scanning options for daily, weekly, or monthly scans.
- Out-of-the-box configurations for fast crawl or critical vulnerability audits.
- API security testing for increased coverage of microservices.
- JavaScript scanning to uncover more attack surfaces in Single Page Applications (SPAs).
- Scalable scanning with the ability to adjust the number of concurrent scans.
- Custom configurations available, including crawl maximum link depth and reported vulnerabilities.
- Burp Scanner, a trusted dynamic web vulnerability scanner used by over 16,000 organizations.
- Integration with major CI/CD platforms such as Jenkins and TeamCity.
- API-driven workflow for initiating scans and obtaining results via the REST API.
- Integration with vulnerability management platforms for seamless scanning and security reporting.
- Burp extensions allow customization of Burp Scanner to meet specific requirements.
- Multiple deployment options including interactive installer and Kubernetes deployment.
- Integration with bug tracking systems like Jira with auto ticket generation and severity triggers.
- GraphQL API for initiating, scheduling, canceling, and updating scans.
- Role-based access control for multi-user functionality and control.
- Compatible configurations from Burp Suite Pro can be manually integrated into the Enterprise environment.
- Reporting features include graphical dashboards, customizable HTML reports, scan history metrics, intuitive UI, rich email reporting, security posture graphing, aggregated issue reporting, and compliance reporting for PCI DSS and OWASP Top 10.
Pros
- Extensive vulnerability detection.
- Can handle complex web applications.
- Integration with popular CI/CD tools.
Cons
- Steep learning curve for beginners.
- Relatively higher pricing.
Detectify
Best for ease of use and automation

Detectify is a fully automated External Attack Surface Management (EASM) solution powered by a world-leading ethical hacker community. It can help map out a company’s security landscape and find vulnerabilities that other scanners may miss.
Pricing
The vendor has several pricing options as follows:
- The full EASM package comes with a 2-week free trial. Pricing is custom and based on the number of domains, sub-domains, and web applications of the attack surface.
- For organizations with a small attack surface, the vendor offers two pricing tiers that also come with a free 2-week trial:
- Surface Monitoring: Pricing starts from $289 per month (billed annually). This package includes up to 25 subdomains.
- Application Scanning: Pricing starts from $89 per month per scan profile (billed annually).
Features
The features of the full EASM solution are:
- Continuous 24/7 coverage for discovering and monitoring your modern tech stack.
- Crawling and fuzzing engine that surpasses traditional DAST scanners.
- Ability to monitor large enterprise products and protect sensitive organizational data.
- Accurate results with 99.7% accuracy in vulnerability assessments through payload-based testing.
- SSO, API access, automatic domain verification, custom modules, and attack surface custom policies.
- Identify risks before they are exploited by enriching assets with critical information like open ports, DNS record types, and technologies.
- Integrates with popular tools such as Slack, Jira, and Splunk, and comes with an API that allows users to export results in the manner that best suits their workflows.
Pros
- Simple and clean interface, easy to use.
- Continuous automatic updates and scans.
- Customizable reports and notifications.
Cons
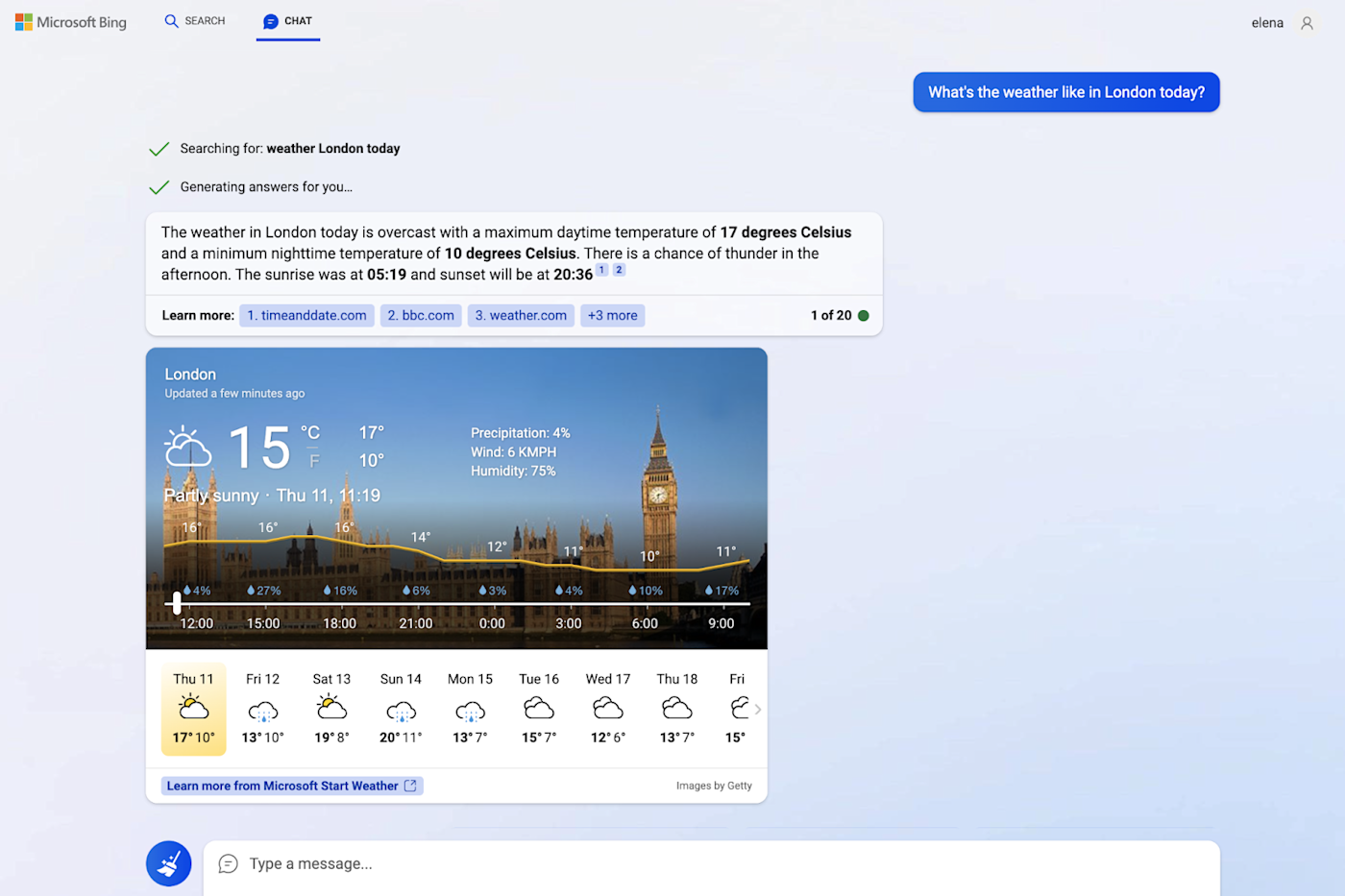
- Limited manual testing capabilities.
- May generate false positives.
Intruder
Best for cloud-based network security

Intruder is a powerful cloud-based network security tool that helps businesses prevent security breaches by automating routine security checks. Each threat found is classified according to severity and a remediation plan proposed.
Pricing
- Pricing is based on the number of applications and infrastructure targets with three pricing tiers: Essential, Pro and Premium. The Pro plan comes with a 14-day free trial.
- Example pricing for 1 application and 1 infrastructure target is as follows:
- Essential: $160 per month, billed annually.
- Pro: $227 per month, billed annually.
- Premium: From $3,737 per year.
Features
- Easy-to-use yet powerful online vulnerability tool.
- Comprehensive risk monitoring across your stack, including publicly and privately accessible servers, cloud systems, websites, and endpoint devices.
- Detection of vulnerabilities such as misconfigurations, missing patches, encryption weaknesses, and application bugs, including SQL injection, Cross-Site Scripting, and OWASP Top 10.
- Ongoing attack surface monitoring with automatic scanning for new threats and alerts for changes in exposed ports and services.
- Intelligent results that prioritize actionable findings based on context, allowing you to focus on critical issues like exposed databases.
- Compliance and reporting with high-quality reports to facilitate customer security questionnaires and compliance audits such as SOC2, ISO27001, and Cyber Essentials.
- Continuous penetration testing by security professionals to enhance coverage, reduce the time from vulnerability discovery to remediation, and benefit from vulnerability triage by certified penetration testers.
- Seamless integration with your technical environment, with no lengthy installations or complex configurations required.
Pros
- Cloud-based, eliminating the need for on-site servers.
- Comprehensive vulnerability coverage.
- Automated, regular security checks.
Cons
- Dependency on automated scanning engines may result in occasional false positives or false negatives.
ManageEngine OpManager
Best for real-time network monitoring

ManageEngine OpManager is a comprehensive network monitoring application, capable of providing intricate insights into the functionality of various devices such as routers, switches, firewalls, load balancers, wireless LAN controllers, servers, virtual machines, printers, and storage systems. This software facilitates in-depth problem analysis to identify and address the core source of network-related issues.
Pricing
The vendor offers three editions with starting prices as follows:
- Standard: $245 for up to 10 devices.
- Professional: $345 for up to 10 devices.
- Enterprise: $11,545 for 250 up to 250 devices.
Features
- Capable of monitoring networks using over 2,000 performance metrics, equipped with user-friendly dashboards, immediate alert systems, and intelligent reporting features.
- Provides crucial router performance data including error and discard rates, voltage, temperature, and buffer statistics.
- Enables port-specific traffic control and switch port mapping for device identification.
- Continuous monitoring of WAN link performance, latency, and availability, leveraging Cisco IP SLA technology.
- Active monitoring of VoIP call quality across WAN infrastructure, facilitating the troubleshooting of subpar VoIP performance.
- Automatic generation of L1/L2 network mapping, aiding in the visualization and identification of network outages and performance issues.
- Provides monitoring for both physical and virtual servers across various operating systems such as Windows, Linux, Solaris, Unix, and VMware.
- Detailed, agentless monitoring of VMware-virtualized servers with over 70 VMware performance monitors.
- Utilizes WMI credentials to monitor Microsoft Hyper-V hosts and guest performance with over 40 in-depth metrics.
- Enables monitoring and management of Host, VMs, and Storage Repositories of Citrix Hypervisor, providing the necessary visibility into their performance.
- Allows for monitoring and management of processes running on discovered devices through SNMP/WMI/CLI.
- Uses protocols like SNMP, WMI, or CLI for monitoring system resources and gathering performance data.
- Provides immediate notifications on network issues via email and SMS alerts.
- Facilitates the orchestration and automation of initial network fault troubleshooting steps and maintenance tasks.
- Provides a centralized platform for identifying network faults, allowing for visualization, analysis, and correlation of multiple monitor performances at any instant.
- Enables network availability, usage trend, and performance analysis with over 100 ready-made and customizable reports.
- Employs a rule-based approach for syslog monitoring to read incoming syslogs and assign alerts.
- Includes a suite of OpManager’s network monitoring tools to assist in first and second-level troubleshooting tasks.
Pros
- In-depth network monitoring.
- Easy-to-understand performance dashboards.
- Supports both physical and virtual servers.
Cons
- May be complex for beginners.
- Cost can quickly escalate based on number of devices.
Tenable Nessus
Best for vulnerability analysis

Tenable Nessus is a vulnerability assessment tool that enables organizations to actively detect and rectify vulnerabilities throughout their ever-evolving attack surface. It is formulated to evaluate contemporary attack surfaces, expanding beyond conventional IT assets to ensure the security of cloud infrastructure and provide insights into internet-connected attack surfaces.
Pricing
- Nessus offers a free 7-day trial. Customers can scan up to 32 IPs per scanner during the trial period.
- After the trial, the product is available at a starting fee of $4,990 per year for an unlimited number of IPs per scanner.
- Nessus Enterprise pricing is dependent on business requirements.
Features
- Evaluates contemporary attack surfaces, extends beyond conventional IT assets, and provides insights into internet-connected environments.
- Built with an understanding of security practitioners’ work, aiming to make vulnerability assessment simple, intuitive, and efficient.
- Provides a reporting feature that prioritizes the top ten significant issues.
- Nessus is deployable on a range of platforms, including Raspberry Pi, emphasizing portability and adaptability.
- Ensures precise and efficient vulnerability assessment.
- Offers visibility into your internet-connected attack environments.
- Ensures the security of cloud infrastructure before deployment.
- Focuses on the most significant threats to enhance security efficiency.
- Provides ready-to-use policies and templates to streamline vulnerability assessment.
- Allows for customization of reports and troubleshooting procedures.
- Provides real-time results for immediate response and rectification.
- Designed for straightforward and user-friendly operation.
- Provides an organized view of vulnerability assessment findings for easy interpretation and analysis.
Pros
- Broad vulnerability coverage.
- Easy integration with existing security systems.
- User-friendly interface.
Cons
- Relatively higher pricing.
Pentest Tools
Best for penetration testing

Pentest Tools is a suite of software designed to assist with penetration testing. Pentest Tools provides the necessary capabilities to effectively carry out penetration tests, offering insights into potential weak points that may be exploited by malicious actors.
Pricing
The vendor offers four pricing plans as follows:
- Basic: $72 per month, billed annually, for up to 5 assets and up to 2 parallel scans.
- Advanced: $162 per month, billed annually, for up to 50 assets and up to 5 parallel scans.
- Teams: $336 per month, billed annually, for up to 500 assets and up to 10 parallel scans.
- Enterprise: For more than 500 assets and more than 10 parallel scans, plan pricing varies.
Features
- Initially built on OpenVAS, now includes proprietary technology to assess network perimeter and evaluate a company’s external security posture.
- Uses proprietary modules, like Sniper: Auto Exploiter, for a comprehensive security scan.
- Provides a simplified and intuitive interface for immediate scanning.
- Conducts in-depth network vulnerability scans using over 57,000 OpenVAS plugins and custom modules for critical CVEs.
- Includes a summarized report of vulnerabilities found, their risk rating, and CVSS score.
- Each report offers recommendations for mitigating detected security flaws.
- Prioritizes vulnerabilities based on risk rating to optimize manual work and time.
- Generates customizable reports with ready-to-use or custom templates.
- Provides a complete view of “low hanging fruit” vulnerabilities, enabling focus on more advanced tests.
- Allows testing of internal networks through a ready-to-use VPN, eliminating the need for time-consuming scripts and configurations.
- Identifies high-risk vulnerabilities such as Log4Shell, ProxyShell, ProxyLogon, and others.
- Assists in running vulnerability assessments necessary to comply with various standards like PCI DSS, SOC II, HIPAA, GDPR, ISO, the NIS Directive, and others.
- Facilitates thorough infrastructure tests, detecting vulnerabilities ranging from weak passwords to missing security patches and misconfigured web servers.
- Third-party infrastructure audit that’s useful for IT services or IT security companies, providing reports for client assurance on implemented security measures.
Pros
- Broad coverage of penetration testing scenarios.
- Easy to use, with detailed reports.
- Regular updates and enhancements.
Cons
- Proprietary technology can also limit interoperability with other tools or platforms.
- New users may experience a steep learning curve.
Qualys VMDR
Best for cloud security compliance

Qualys VMDR is a top choice for businesses looking for cloud-based network security software. It provides automated cloud security and compliance solutions, allowing businesses to identify and fix vulnerabilities.
Pricing
- Prospective customers can try out the tool for free for 30 days.
- Pricing starts at $199 per asset with a minimum quantity of 32 (i.e., $6,368 total starting cost).
- Flexible pricing for larger packages based on business needs.
Features
- Qualys is a strong solution for businesses seeking cloud-based network security software, providing automated cloud security and compliance solutions.
- Utilizes TruRisk™ to quantify risk across vulnerabilities, assets, and asset groups, enabling proactive mitigation and risk reduction tracking.
- Automates operational tasks for vulnerability management and patching with Qualys Flow, saving valuable time.
- Leverages insights from over 180,000 vulnerabilities and 25+ threat sources to provide preemptive alerts on potential attacks with the Qualys Threat DB.
- Detects all IT, OT, and IoT assets for a comprehensive, categorized inventory with detailed information such as vendor lifecycle.
- Automatically identifies vulnerabilities and critical misconfigurations per Center for Internet Security (CIS) benchmarks, by asset.
- Integrates with ITSM tools like ServiceNow and Jira to automatically assign tickets and enable orchestration of remediation, reducing Mean Time To Resolution (MTTR).
Pros
- Cloud-based, reducing on-premise hardware needs.
- Comprehensive vulnerability and compliance coverage.
- Powerful data analytics capabilities.
Cons
- Can be complex for small businesses.
- Pricing is high and can be prohibitive for smaller organizations.
SolarWinds ipMonitor
Best for large-scale enterprise networks

SolarWinds ipMonitor is an established network monitoring solution ideal for monitoring servers, VMware hosts, and applications on large-scale enterprise networks. It offers deep performance insights and customizable reports.
Pricing
SolarWinds ipMonitor has three pricing editions, each with a 14-day free trial:
- 500 monitors for $1,570
- 1000 monitors for $2,620
- 2500 monitors for $5,770
Features
- The monitoring tool provides over a dozen notification types including alerts via email, text message, or directly to Windows Event Log files.
- Facilitates the monitoring of common ports with key protocols.
- Ensures IT environment functionality by continuously monitoring database availability.
- Enhances end user network experience monitoring capabilities.
- Offers monitoring of network equipment health in tandem with network infrastructure.
- Confirms the ability of a web server to accept incoming sessions.
- Provides critical insights into the overall IT environment.
- Offers an affordable tool for network monitoring.
- Utilizes VM ESXi host monitors to track the health and performance of your virtual environment.
- Enables monitoring of Windows services and applications..
Pros
- Extensive scalability for large networks.
- Deep insights and comprehensive reporting.
- Wide range of integrated applications.
Cons
- Can be overly complex for smaller networks.
- The pricing model may not suit smaller businesses.
Key features of network scanning tools and software
Vulnerability scanning is central to all network scanning tools, but other features, such as real-time monitoring, penetration testing, and integrability, should not be overlooked.
Vulnerability scanning
This is the most critical feature buyers typically look for in network scanning tools. Vulnerability scanning helps identify potential security threats and weak spots within the network.
The tools do this by scanning the network’s devices, servers, and systems for known vulnerabilities such as outdated software, open ports, or incorrect configurations.
This feature matters because it provides an overview of the network’s security posture, enabling users to take corrective measures promptly.
Real-time network monitoring
Real-time network monitoring allows for continuous observation of the network’s performance, detecting any issues or anomalies as they occur.
This feature is vital because it can significantly reduce downtime and address performance issues before they impact business operations.
Penetration testing
Penetration testing (or pentesting) simulates cyberattacks on your network to test the effectiveness of your security measures and identify potential vulnerabilities that may not be detectable through standard vulnerability scanning.
Penetration testing is essential for businesses as it offers a more proactive approach to cybersecurity than standard vulnerability scans.
Compliance assurance
Compliance assurance ensures that the organization’s network aligns with various regulatory standards, such as HIPAA for healthcare or PCI DSS for businesses that handle credit card information.
Compliance assurance is critical because non-compliance can result in hefty fines and damage to the company’s reputation.
Integration with other tools
Integration capabilities are an often overlooked but essential feature of network scanning tools. The ability to integrate with other IT management and security tools allows for a more streamlined and efficient workflow.
For example, integrating a network scanning tool with a ticketing system could automatically create a ticket when a vulnerability is detected.
This feature is vital as it enables businesses to enhance their overall IT infrastructure management and improve response times to potential threats.
How to choose the best network scanning software for your business
Selecting the best network scanning tool for your business involves several key considerations:
- Identify your needs: The first step is to understand what you need from a network scanning tool. Do you require real-time network monitoring, pentesting, compliance assurance, or more? The type of network you’re operating and the size of your business can heavily influence your needs.
- Consider the ease of use: The usability of the software is an important factor depending on the size and expertise of your IT team. If it’s too complex, it may be challenging for your team to use effectively. Look for software that has a user-friendly interface and offers good customer support.
- Examine the features: Look for software that offers the features that match your specific requirements. If you’re unsure what features you might need, consulting with an IT professional can be beneficial.
- Evaluate scalability: Your business is likely to grow, and so will your network. The network scanning tool you choose should be able to scale along with your business without losing efficiency.
- Check for regular support and updates: Good network scanning software should provide reliable support and regular updates to address emerging security threats. Check whether the software is frequently updated and if technical support is readily available.
- Review pricing: Lastly, consider the pricing and your budget. Keep in mind that while some software might be more expensive, it could offer more features or better support, leading to better value for your business in the long run.
Frequently Asked Questions (FAQs)
What are the benefits of network scanning tools?
Network scanning tools offer a multitude of benefits, including:
- Security enhancement: Network scanning tools identify vulnerabilities and security risks within a network, allowing businesses to address these issues proactively and bolster their security posture.
- Compliance assurance: Many of these tools help ensure that your network aligns with various regulatory and industry standards, reducing the risk of non-compliance penalties.
- Real-time monitoring: By providing real-time network monitoring, these tools allow for immediate detection and mitigation of issues, thereby reducing network downtime and improving performance.
- Resource optimization: Network scanning can identify underutilized resources, aiding in more efficient resource allocation and cost savings.
- Improved network management: With a thorough understanding of the network infrastructure, administrators can make more informed decisions regarding network planning and expansion.
Who should use network scanning software?
Network scanning software is beneficial for a variety of roles and industries, including:
- Network administrators: These professionals can use network scanning tools to monitor and manage the health of the network, consistently optimizing its performance.
- IT security professionals: These tools are crucial for IT security staff in identifying potential vulnerabilities and mitigating security risks.
- Managed Service Providers (MSPs): MSPs can utilize network scanning tools to manage and monitor their clients’ networks, ensuring they are secure and comply with relevant regulations.
- Regulated industries: Businesses within industries that must adhere to strict data security standards, such as healthcare, finance, and e-commerce, can benefit significantly from these tools to ensure compliance and protect sensitive data.
What are the types of network scanning?
Network scanning can be categorized into several types based on their function:
- Port scanning: This type identifies open ports and services available on a network host. It can help detect potential security vulnerabilities.
- Vulnerability scanning: This process involves identifying known vulnerabilities in the network, such as outdated software or misconfigurations, that could be exploited.
- Network mapping: This type of scanning identifies the various devices on a network, their interconnections, and topology.
- Performance scanning: This form of scanning monitors network performance, identifying potential issues that could affect the speed or reliability of the network.
- Compliance scanning: This type checks the network’s compliance with certain regulatory or industry standards, helping avoid potential legal issues.
Methodology
The selection, review, and ranking of the network scanning tools in this list was carried out through a comprehensive and structured methodology, which involved several key steps: namely, requirement identification, market research, feature evaluation, user reviews and feedback, ease of use, pricing, and scalability.
By combining these steps, we have aimed to provide a balanced and comprehensive overview of the top network scanning tools of 2023, thereby enabling potential buyers to make an informed decision that best suits their specific needs and circumstances.
Bottom line: Managing vulnerabilities with network scanning tools
Network scanning tools are essential for any organization striving to maintain a secure and efficient IT environment. From identifying vulnerabilities to ensuring compliance and enhancing overall network performance, these tools play a pivotal role in successful network management.
The eight tools discussed in this article offer a variety of features and capabilities, catering to different needs and business sizes. However, choosing the right tool should be guided by an organization’s unique requirements, budget, and the tool’s ability to scale alongside the growth of the business.
By doing so, businesses can foster a more secure, compliant, and reliable IT network, boosting operational efficiency and business resilience.
Knowing your network’s vulnerabilities is just the beginning. Here are the best vulnerability management tools to keep your data locked up safe.
Source :
https://www.enterprisenetworkingplanet.com/security/network-scanning-tools/