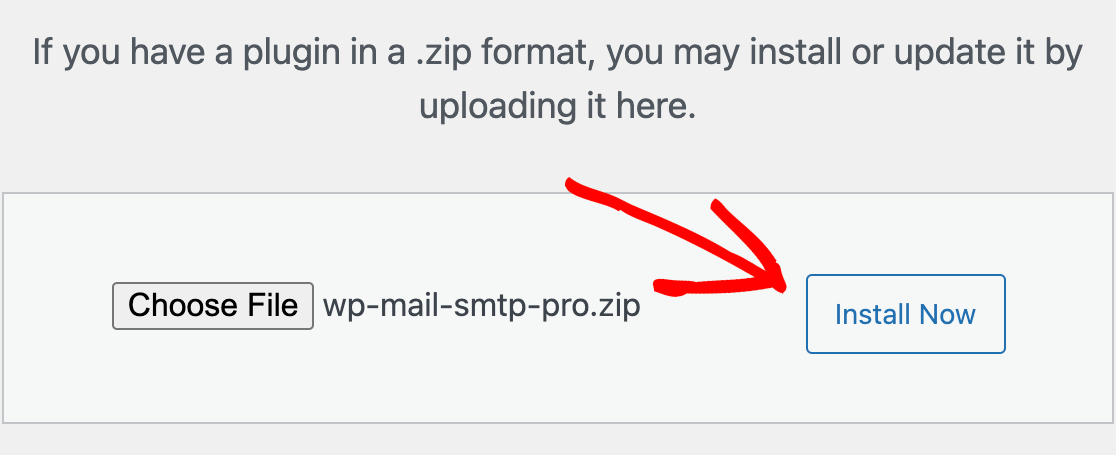
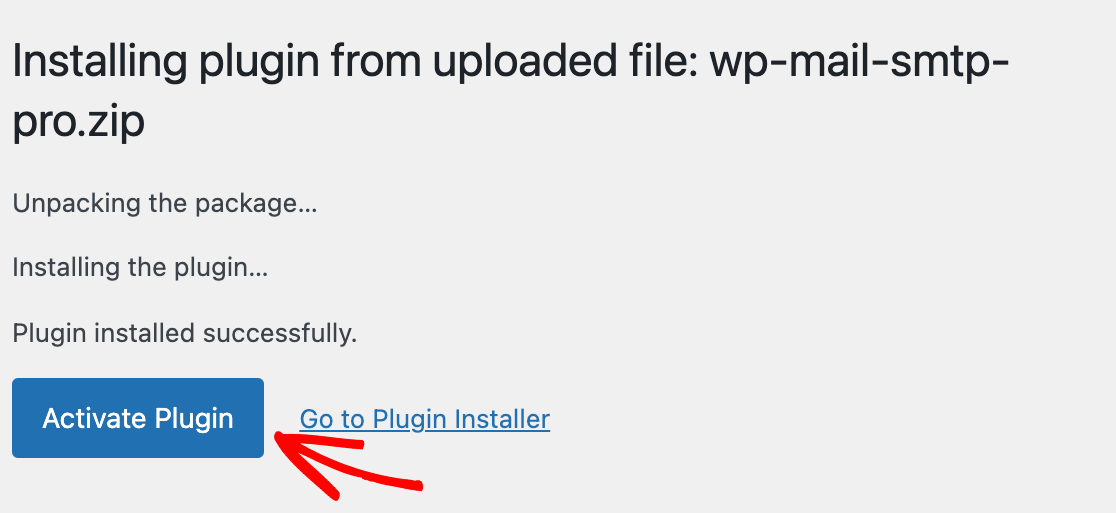
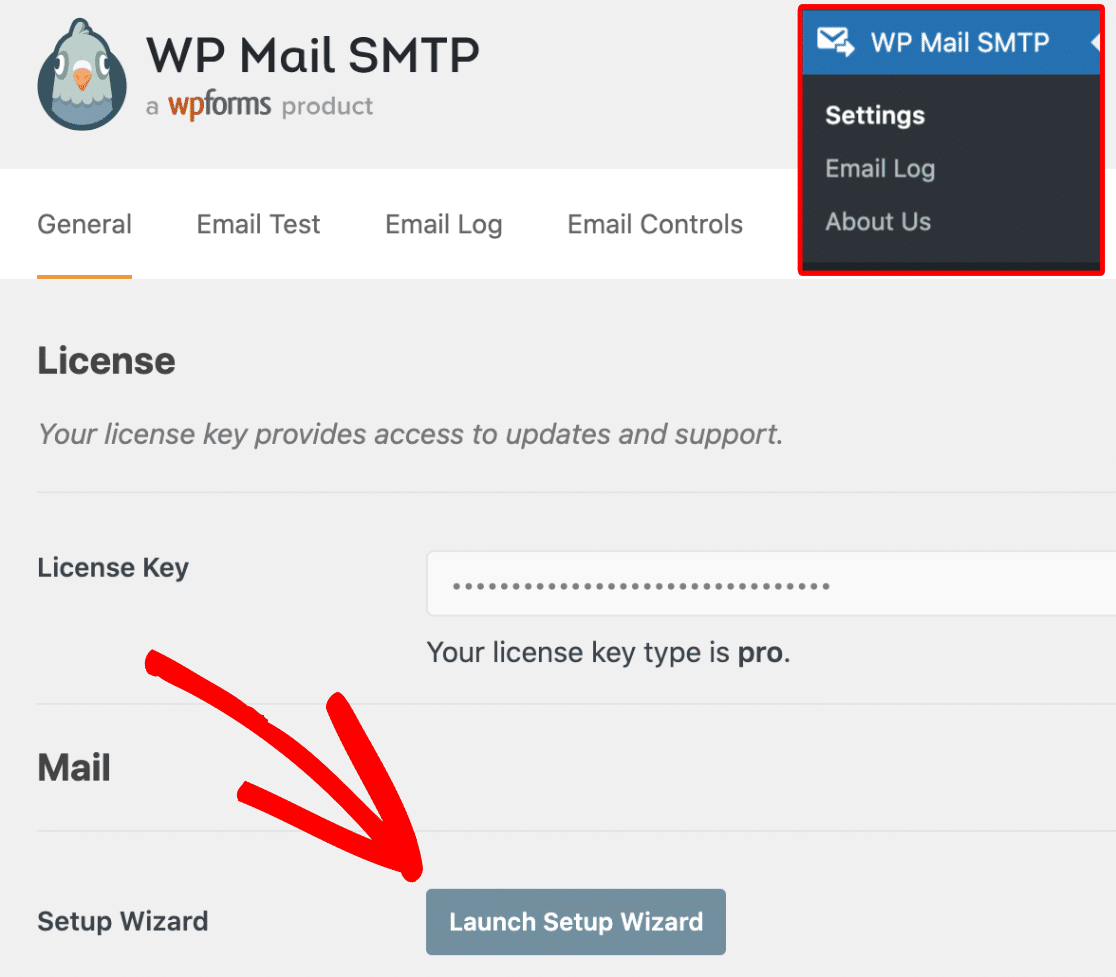
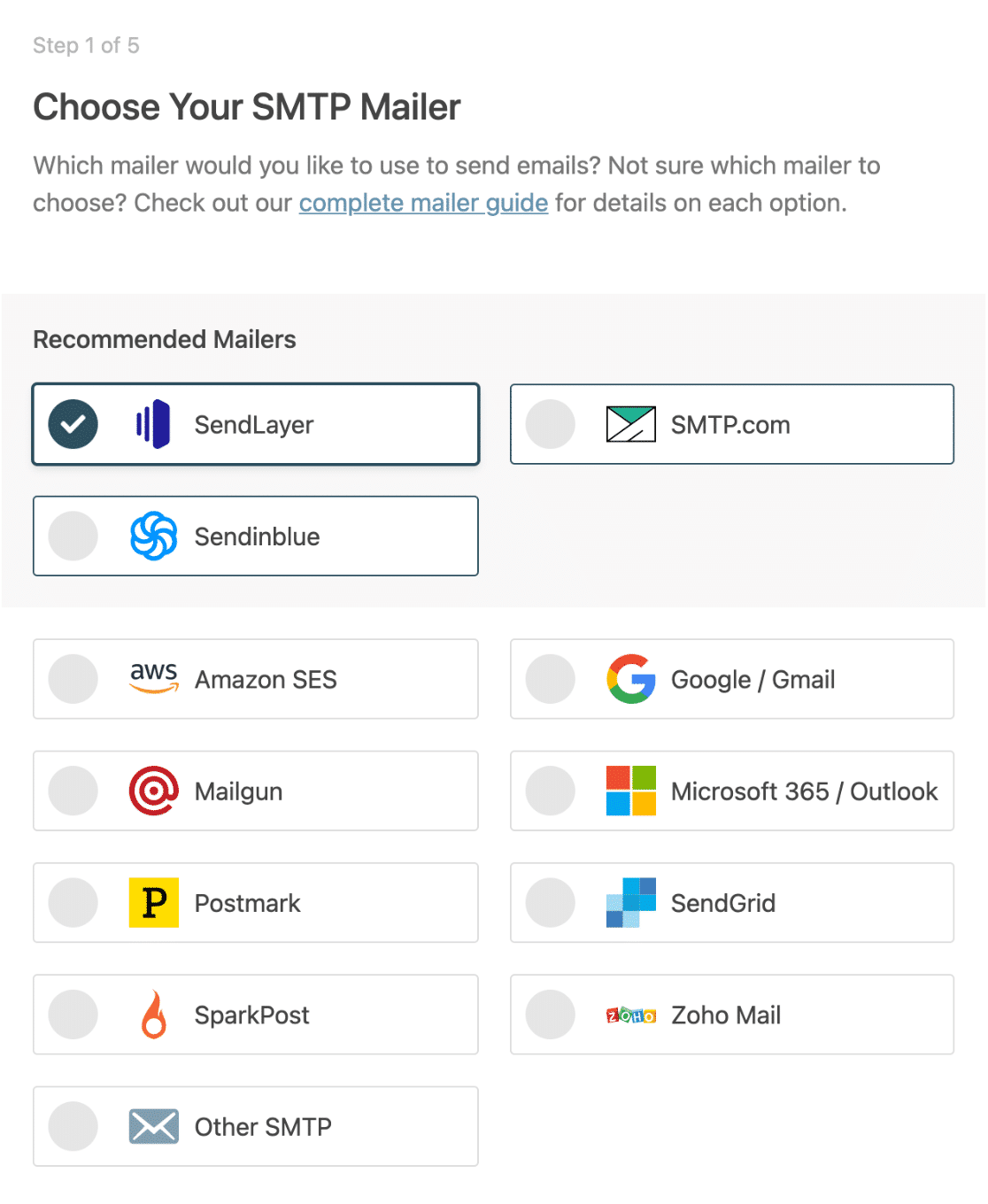
“Luck favors the prepared,” as the saying goes. The maxim is true in cyber security, too. We all know about data breaches. We know they’re alarmingly common; more common than ever, if you can believe it. We know they can be costly, time-consuming, and disruptive. And yet, what do we know of mentally and emotionally preparing for an attack to happen to us?
A cyber attack can have a tremendous negative psychological impact, the effects of which victims can feel for weeks and months. Understanding the emotions you might feel during and after an attack can help you better prepare for and handle a cyber attack if/when it happens to you. Here’s what you need to know about the potential psychological impact of cyber attacks and what to do in advance so you can deal with one calmly and rationally.
During a cyber attack
Cyber attacks can happen suddenly. For example, you might get a random text or email about new account activity or a changed password. A service might inform you of a money transfer you didn’t approve, a purchase you didn’t make, or an account change you weren’t expecting. Or the next time you try to log in to an account, you find yourself locked out. Or your data is suddenly gone and held hostage by a cyber-criminal demanding a ransom. Or you just hung up the phone with someone who claimed to be tech support, and now you’re watching someone else control your computer without your consent.
No matter how it happens, panic often sets in once you find yourself suffering a cyber attack. It’s common to feel intense fear; fear for what will happen to your money and your personal information and the unknown impact the attack will have on your life. You might panic about what to do, how to regain control, and how to get help. You might feel violated, like someone has invaded your personal space and upended your sense of safety. In some ways, a cyber attack can feel like the digital equivalent of being robbed, with a corresponding wave of anxiety and dread.
Anxiety, panic, fear, and frustration – even intense anger – are common emotional responses when experiencing a cyber attack. While expected, these emotions can paralyze you and prolong or worsen a cyber attack. The combination of not knowing what to do and being paralyzed with fear can keep you from taking quick, effective action against a cyber attack. Preparing in advance can help you move through these intense emotions and respond productively.
During an attack, your focus should be on regaining control of the situation. Do you still have access to the account/device under attack? Immediately change passwords, remove unauthorized locations, notify customer service, check all security settings and do everything you can to lock out access to any third parties while beefing up security (including enabling two-factor authentication). On a trusted device (e.g., not a compromised device), change passwords for other high-value accounts like email, banking/financial, and social media. A password manager can help you change passwords quickly to new, random ones. You need to act fast while staying focused on the actions most likely to stop or at least slow down an attack.
Immediately after an attack
At some point, the attack will be over. Either you shut down the attack or the attackers “win,” and you find yourself dealing with the aftermath. Regardless, the emotional and mental impact may continue. A cyber attack can leave you with tough questions despite the initial relief when the immediate threat is over.
Self-pity and rumination are typical responses in the immediate wake of an attack. Why me? Did I draw their attention? Did I make a mistake? Why was my data/money/account/device worth stealing? Could I have done something different to prevent it? What if I had done x or y? Are they going to strike again? And on and on. You might find yourself overthinking and overanalyzing everything leading up to the attack. You might obsess over your actions during the attack and criticize yourself excessively for what you did or didn’t do.
Again, all of the above are understandable responses to a cyber attack. But these negative emotions can drag you down. If you’re mentally stuck, you’ll struggle to clean up after the attack and prepare for future incidents.
After an attack, your focus should be on analyzing how the attack happened and closing those “gaps” in your cyber security. Scan your devices for malware and change passwords. Turn on two-factor authentication, remove unknown and unused apps/browser extensions/software/files, and review the security settings for important accounts like email and financials. If the cybercriminals stole money, you’d need to follow any options for recourse against theft. You might also need to cancel a card, close an account, or freeze your credit to prevent further abuse. In sum, your goal immediately after an attack is over should be to identify weaknesses in your online security and eliminate or minimize them to prevent further problems.
Long-term impact
Unfortunately, negative emotions can persist weeks and months after a cyber attack, especially when the attack results in the theft of data, money, or other personal property. You’ll likely feel embarrassed about what happened, maybe even ashamed. You may worry about what others think if they find out the details. Sometimes, workplace security mistakes can lead to loss of employment, which can devastate one’s mental and physical wellbeing.
Avoidance is common, too; if you feel uncomfortable thinking about the cyber attack, you might use your discomfort as an excuse to avoid improving your cyber security. Ignoring your feelings, though, can keep you from processing what happened and doing what you must to ensure it doesn’t happen again.
Will it happen again? Apprehension is understandable in the wake of a cyber attack. You’ve been through a roller coaster of emotions, and the attack has forever shattered your sense of digital safety. Anxiety and worry about future attacks are normal but use those feelings as motivation to improve your cyber security strategy. There is never a “done” when it comes to cyber security. Hackers are constantly evolving their methods, and your cyber security strategy needs to keep up.
How to minimize psychological distress
Whether or not you’ve been the victim of a cyber attack, there are things you can do to stop or minimize future attacks. Building a solid foundation of cyber security requires doing the basics well. It’s not hard, but it takes a little time and commitment to improving your digital practices. The good news is that once you make these changes, you’ll find they can improve your online experience and help you feel better prepared for cyber attacks.
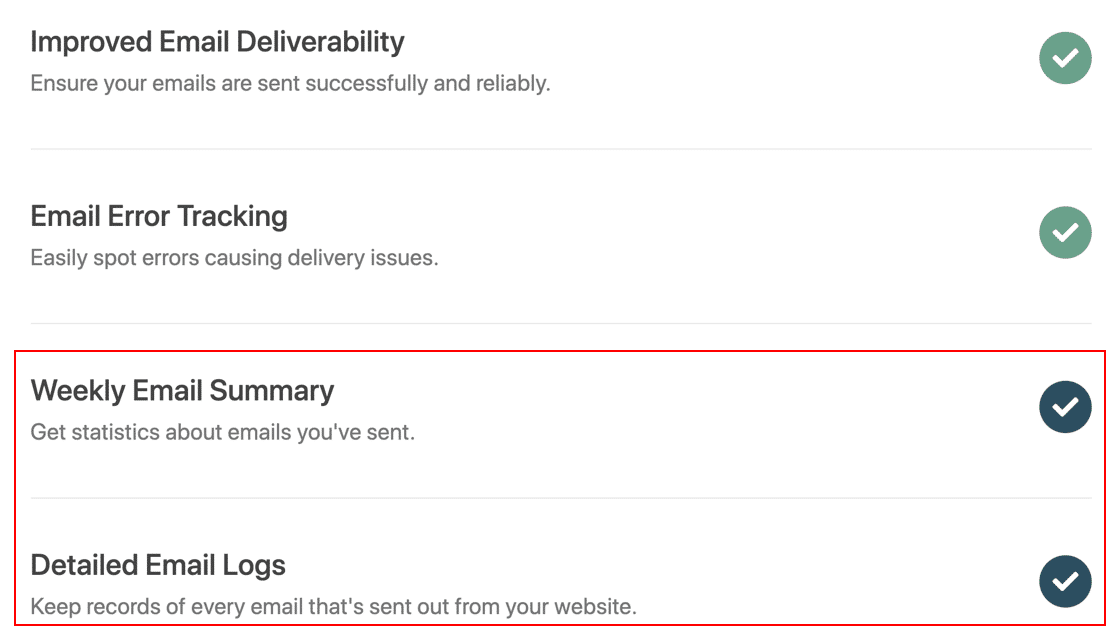
Prioritize good password hygiene. Weak, reused, guessable passwords contribute to account takeovers and online theft. Replace passwords with generated ones that are genuinely random and strong enough to withstand cracking. Enable two-factor authentication wherever it’s available; some two-factor apps make it easier to log in to an account.
Safeguard accounts with a password manager. A password manager stores credentials for your online accounts, enters your info when you need to log in, and ensures every password is unique and random. It simplifies strong password security and takes the hassle out of logging in.
Keep a clean machine. Don’t click random links. Don’t download strange attachments. Don’t install unverified apps and extensions. Don’t give strangers your login information, SSN, or other data. Don’t answer the phone for “tech support” – no tech support or police department or bank will ever call you to deal with a “security issue” or “software problem.”
Stay cyber aware. Watch for suspicious online account activity and take action at the first sign of something strange. Turn on account alerts to your phone or email. Enable dark web monitoring and follow up immediately on publicized data breaches. Know the signs of phishing and social engineering attacks, and scrutinize every text/email/phone call/social media message for signs of fraud.
Seek support and professional advice. You don’t have to suffer alone. Like other traumatic life events, a therapist or other qualified mental health professional can help you process after you’re the victim of cybercrime. When necessary, digital forensics and information security professionals can also help investigate and resolve a digital crime. Don’t hesitate to seek personal and professional support when needed.
Cybercriminals like to go after easy targets. Building a solid foundation with cyber security basics can prevent cyber attacks by making it too difficult or costly for criminals to go after your accounts. It can also buy you time to react immediately when an attack starts.
Cyber attacks can cause intense, paralyzing emotions. The more you educate yourself and prepare in advance, the more likely you are to work around those emotions during and after an attack. Don’t just assume you’ll deal with it and figure everything out in the moment. Do the work now to prepare so you’re not overwhelmed mentally by a cyber attack. Getting started with a password manager will help you build stronger, more effective online security habits. When you feel confident handling a cybersecurity incident, you’ll minimize the psychological impact of these scary events and more effectively navigate the challenges they can bring.
Source :
https://blog.lastpass.com/2022/08/the-psychological-impact-of-cyber-attacks/
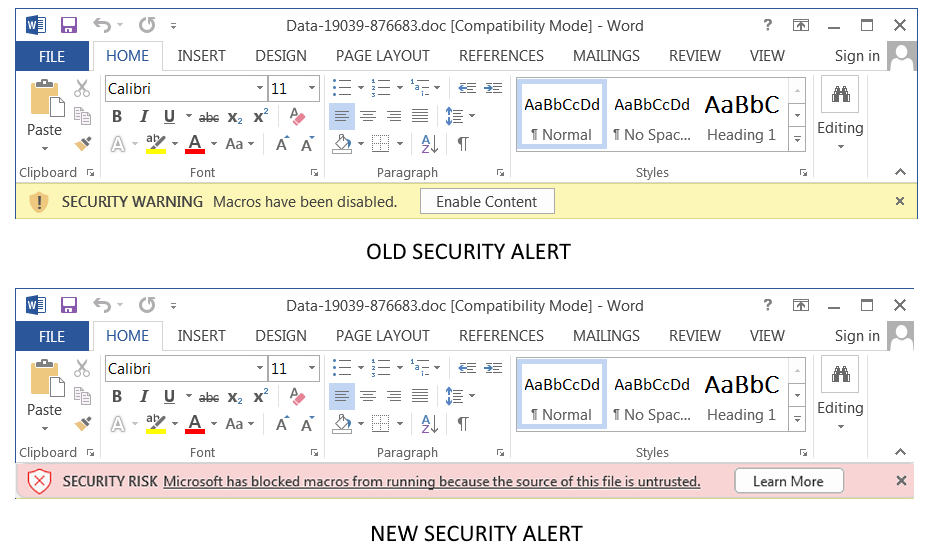
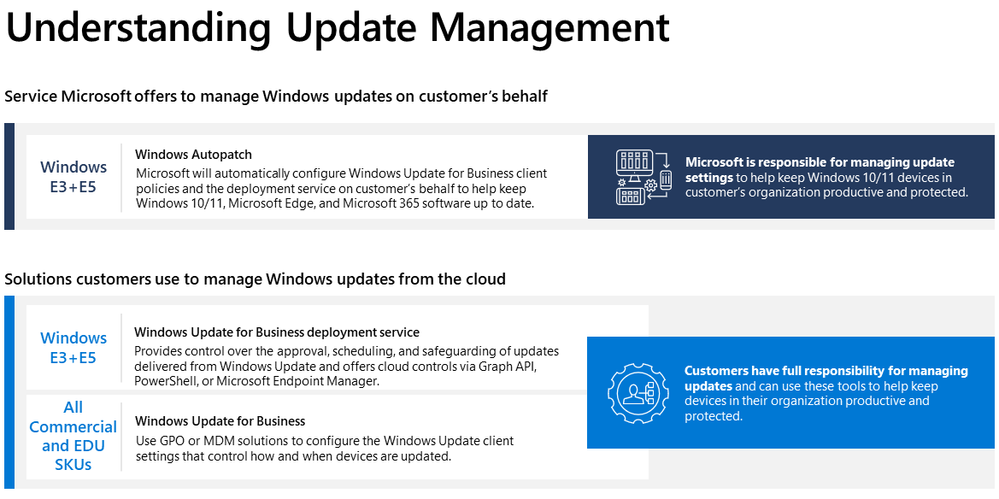 Windows Autopatch is a service that uses the Windows Update for Business solutions on your behalf.
Windows Autopatch is a service that uses the Windows Update for Business solutions on your behalf.
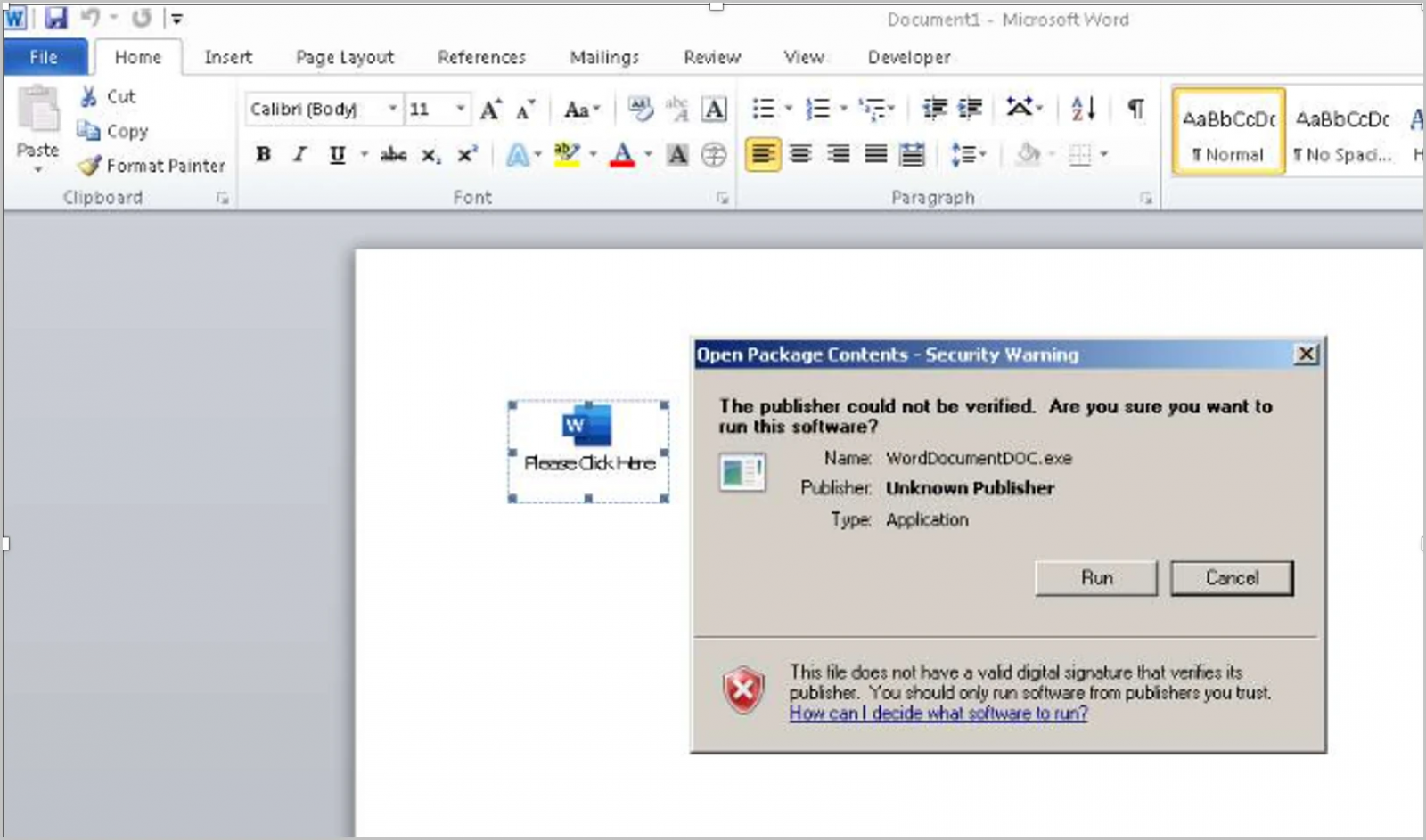
.png)