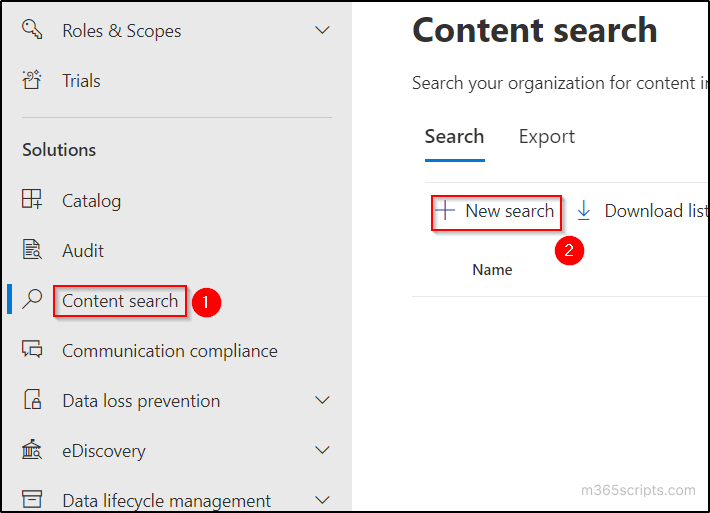
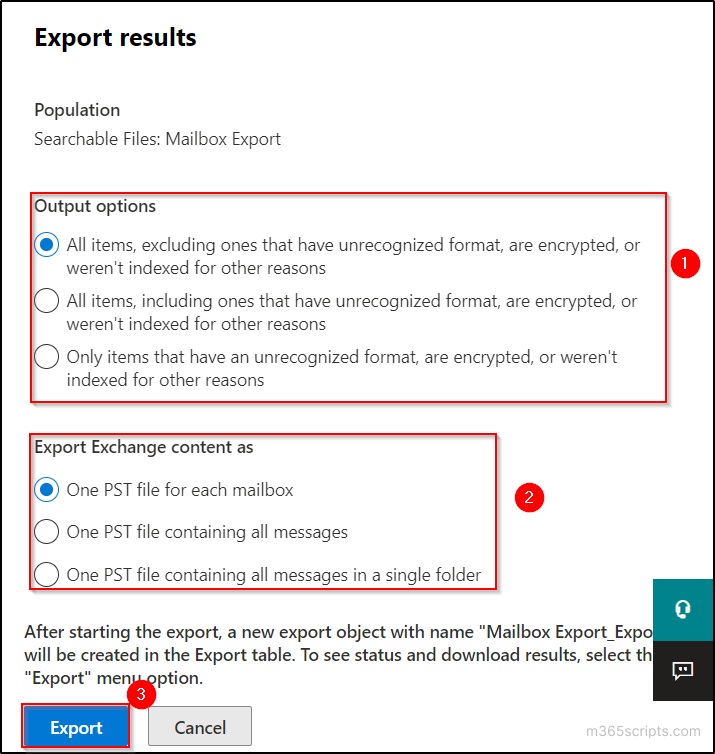
BY AMINU ABDULLAHI MAY 26, 2023
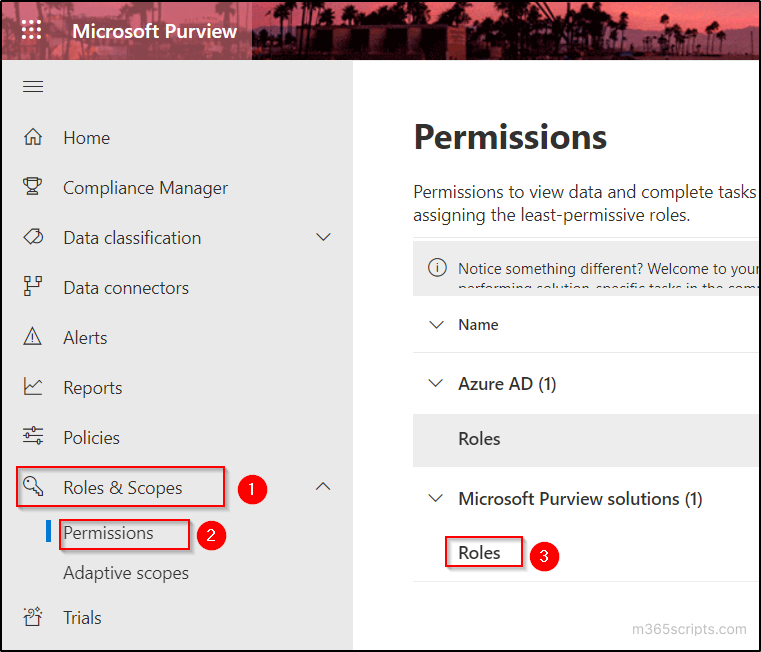
Enterprise firewall software is an essential component of network security infrastructure for organizations. These firewalls are designed to provide high availability and scalability to meet the needs of large and complex networks because they can handle high traffic volumes and accommodate the growth of network infrastructure.
By exploring the following top firewall solutions, enterprises can make an informed decision to fortify their network defenses and safeguard critical assets from ever-evolving cyber threats.
- Palo Alto Networks: Best all-in-one enterprise firewall solution (Read more)
- Check Point Quantum: Best for connected devices (Read more)
- Fortinet FortiGate: Best for flexibility and scalability (Read more)
- Juniper Networks: Best for logging and reporting (Read more)
- Cisco Secure Firewall: Best for centralized management (Read more)
- Zscaler: Best for businesses with cloud network infrastructure (Read more)
- pfSense: Best open source firewall (Read more)
Best firewall solutions for enterprises: Comparison chart
| Best for | DLP capability | URL filtering | Reporting | Integration with third party solution | DNS filtering | Starting price | |
|---|---|---|---|---|---|---|---|
| Palo Alto Networks | Overall | ✔ | ✔ | ✔ | ✔ | ✔ | Available on request |
| Check Point Quantum | Connected devices | ✔ | ✔ | ✔ | ✔ | ✔ | Available on request |
| Fortinet FortiGate | Flexibility and scalability | ✔ | ✔ | ✔ | ✔ | ✔ | Available on request |
| Juniper Networks | Logging and reporting capability | ✔ | ✔ | ✔ | ✔ | ✔ | Available on request |
| Cisco Secure Firewall | Centralized management | ✔ | ✔ | ✔ | ✔ | ✔ | Available on request |
| Zscaler | Businesses with cloud network infrastructure | ✔ | ✔ | ✔ | ✔ | ✔ | $72 per user per year |
| pfSense | Open source | ✔ | ✔ | ✔ | ✔ | ✔ | $0.01 per hour |
Jump to:
- Key features of enterprise firewall software
- Benefits of working with enterprise firewalls
- How do I choose the best enterprise firewall solution for my business?
- Frequently Asked Questions (FAQ)
- Methodology

Palo Alto Networks
Best overall enterprise firewall
Palo Alto is a leading network security provider of advanced firewall solutions and a wide range of network security services.
The company offers various firewall solutions for various enterprise use cases, including cloud next generation firewalls, virtual machine series for public and private clouds, container series for Kubernetes and container engines like Docker, and its PA-series appliances designed for data centers, network edge, service providers, remote branches and retail locations, and harsh industrial sites.
These firewalls provide enhanced visibility, control, and threat prevention capabilities to protect networks from various cyber threats, including malware, viruses, intrusions, and advanced persistent threats (APTs).
Pricing
Palo Alto doesn’t advertise its product pricing on its website. Our research found that the Palo Alto PA-series price range from $2,900 to $200,000 (more or less). To get the actual rates for your enterprise, contact the company’s sales team for custom quotes.
Standout features
- Advanced threat prevention.
- Advanced URL filtering.
- Domain name service (DNS) security.
- Medical IoT security.
- Enterprise data loss prevention (DLP).
- Up to 245 million IPv4 OR IPv6 sessions.
Pros
- Provides visibility across IoT and other connected devices.
- Provides visibility across physical, virtualized, containerized and cloud environments.
- Offers a variety of products for different business sizes, from small businesses to large enterprises.
- Easy-to-navigate dashboard and management console.
Cons
- Complex initial setup.
- Some users reported that the Palo Alto license is pricey.

Check Point Quantum
Best for connected devices
Check Point is an Israeli multinational company that develops and sells software and hardware products related to network, endpoint, cloud, and data security.
Check Point Quantum is designed to protect against advanced cyber threats, targeting Gen V cyber attacks. This solution encompasses various components to safeguard networks, cloud environments, data centers, IoT devices, and remote users.
Check Point’s SandBlast technology employs advanced threat intelligence, sandboxing, and real-time threat emulation to detect and prevent sophisticated attacks, including zero-day exploits, ransomware, and advanced persistent threats.
Pricing
Check Point does not publicly post pricing information on its website. Data from resellers shows that Check Point products can range from around $62 for a basic solution to over $50,000 for an enterprise-level solution. Contact the Check Point sales team for your actual quotes.
Standout features
- URL filtering.
- DLP.
- Full active-active redundancy.
- Zero-trust protection for IoT devices.
- Check Point Quantum protects against GenV attacks.
- Advanced threat protection.
Pros
- 24/7 customer service and support.
- Easy to setup and use.
- Management platform with automation features.
- Sandblast protection for testing malware.
Cons
- Users reported that the Check Point firewall is expensive.
- Documentation can be improved.

Fortinet FortiGate
Best for flexibility and scalability
Fortinet offers various firewall products for different organization sizes, from home offices to large enterprises.
The FortiGate 7000 series (FG-7121F, FG-7081F, FG-7081F-2, FIM-7921F, FIM-7941F, and FPM-7620F) is an enterprise firewall product that provides high-performance network security. It is designed for organizations with high network traffic volumes and that have to manage large network infrastructures.
This firewall series is powered by a Security Processing Unit (SPU) of up to 520Gbps and also includes the latest NP7 (Network Processor 7) and CP9 (Content Processor 9).
Pricing
Fortinet’s FortiGate firewall tool pricing is available upon request. Pricing will depend on various factors, including the size of the network, the number of users, and the types of security features needed. Contact a Fortinet representative for pricing and product information.
Standout features
- Protects IT, IIoT, and OT devices against vulnerability and device-based attack tactics.
- FortiGate 7000F series provides NGFW, segmentation, secure SD-WAN, and mobile security for 4G, 5G, and IoT.
- Offers various types of firewalls, including container firewalls, virtual firewalls and hardware firewall appliances.
- Zero Touch Integration with Fortinet’s Security Fabric Single Pane of Glass Management.
Pros
- Integrations with over 500 third-party services.
- AI-powered capabilities.
- Users reported that the tool is user-friendly.
Cons
- Support can be improved.
- Its reporting feature can be improved.

Juniper Networks
Best for logging and reporting capability
Juniper Networks’ firewall helps enterprises protect their network edge, data center, and cloud applications.
The company is also known for its Junos operating system (OS), a scalable network OS that powers Juniper Networks devices. Junos provides advanced routing, switching, and security capabilities and allows for seamless integration with third-party software and applications.
Juniper Networks vSRX virtual firewall provides enhanced security for Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform, IBM Cloud, and Oracle Cloud environments, while its cSRX Container Firewall offers advanced security services to secure applications running in containers and microservices. The company’s SRX firewalls series is designed for various organization sizes, from small to large enterprises.
Pricing
Juniper Network pricing is available on request. However, they offer different license methods, including Pay-As-You-Go (PAYG) and Bring-Your-Own-License (BYOL) options for public clouds. Contact the company’s sales team for custom quotes.
Standout features
- Juniper Network has various types of firewalls, including container firewalls, virtual firewalls and hardware firewall appliances.
- Public cloud workload protection, including AWS, Microsoft Azure, and Google Cloud Platform.
- Logging and reporting capability.
- Supports VMware ESXi, NSX, and KVM (Centos, Ubuntu).
Pros
- Advanced threat prevention capability.
- Deployable on-premises and cloud environments.
Cons
- Support can be improved.
- Users report that some Juniper Networks firewall products are expensive.

Cisco Secure Firewall
Best for centralized management
Cisco Secure Firewall combines firewall capabilities with advanced security features to protect networks from various threats, including unauthorized access, malware, and data breaches.
Cisco Secure Firewall integrates with Cisco Talos, a threat intelligence research team. This collaboration enables the firewall to receive real-time threat intelligence updates, enhancing its ability to identify and block emerging threats.
Cisco Secure Firewall can be centrally managed through Cisco Firepower Management Center (FMC). This management console provides a unified interface for configuration, monitoring, and reporting, simplifying the administration of multiple firewalls across the network.
Pricing
Contact Cisco’s sales team for custom quotes.
Standout features
- IPS to protect against known threats.
- Web filtering.
- Network segmentation.
- Centralized management.
Pros
- Provides comprehensive visibility and control.
- Efficient support team.
- Highly scalable tool.
Cons
- Support can be improved.
- Complex initial setup.

Zscaler
Best for businesses with cloud network infrastructure
The Zscaler firewall provides cloud-based security for web and non-web traffic for all users and devices. Zscaler inspects all user traffic, including SSL encrypted traffic, with elastically scaling services to handle high volumes of long-lived connections.
One of the key advantages of Zscaler’s cloud-based approach is that it eliminates the need for on-premises hardware or software installations. Instead, organizations can leverage Zscaler’s infrastructure and services by redirecting their internet traffic to the Zscaler cloud. This makes scaling and managing security easier across distributed networks and remote users.
Pricing
Zscaler doesn’t advertise its rates on its website. However, data from resellers shows that its pricing starts from about $72 per user per year. For your actual rate, contact the Zscaler sales team for quotes.
Standout features
- Centralized policy management.
- Fully-integrated security services.
- Real-time granular control, logging, and visibility.
- User-aware and app-aware threat protection.
- Adaptive IPS security and control.
- File transfer protocol (FTP) control and network address translation (NAT) support.
Pros
- Easy to use and manage.
- AI-powered cyberthreat and data protection services.
- Always-on cloud intrusion prevention system (IPS).
- AI-powered phishing and C2 detection.
Cons
- Complex initial setup.
- Documentation can be improved.

pfSense
Best open-source firewall
pfSense is an open-source firewall and routing platform based on FreeBSD, an open-source Unix-like OS. It is designed to provide advanced networking and security features for small and large networks.
pfSense can be deployed as a physical appliance or as a virtual machine. pfSense offers many capabilities, including firewalling, VPN connectivity, traffic shaping, load balancing, DNS and DHCP services, and more.
Pricing
For pfSense cloud:
- pfSense on AWS: Pricing starts from $0.01 per hour to $0.40 per hour.
- pfSense on Azure: Pricing starts from $0.08 per hour to $0.24 per hour.
For pfSense software:
- pfSense CE: Open source version available to download for free.
- pfSense+ Home or Lab: Available at no cost for evaluation purposes only.
- pfSense+ W/TAC LITE: Currently available at no charge, but the vendor may increase the rate to $129 per year in the future.
- pfSense+ W/TAC PRO: $399 per year.
- pfSense+ W/TAC ENT: $799 per year.
pfSense offers three hardware appliances tailored to the needs of large enterprises.
- Netgate 8200: Cost $1,395. It has 18.55 Gbps IPERF3 and 5.1 Gbps IMIX traffic speed.
- Netgate 1537: Cost $2,199. It has 18.62 Gbps(10k ACLs) IPERF3 and 10.24 Gbps (10k ACLs) IMIX traffic speed.
- Netgate 1541: Cost $2,899. It has 18.64 Gbps(10k ACLs) IPERF3 and 12.30 Gbps(10k ACLs) IMIX traffic speed.
Standout features
- NAT mapping (inbound/outbound).
- Captive portal guest network.
- Stateful packet inspection (SPI).
Pros
- Free open-source version.
- Community support.
- Anti-spoofing capability.
Cons
- Steep learning curve for administrators with limited experience.
- GUI is old-fashioned and could be simplified.
Key features of enterprise firewall software
There’s a wide variety of capabilities that enterprise firewall software can provide, but some of the key features to look for include packet filtering, stateful inspection, application awareness, logging and reporting capabilities, and integration with your existing security ecosystem.
Packet filtering
Firewall software examines incoming and outgoing network packets based on predefined rules and policies. It filters packets based on criteria such as source/destination IP addresses, ports, protocols, and packet attributes. This feature enables the firewall to block or allow network traffic based on the configured rules.
Stateful inspection
Enterprise firewalls employ stateful inspection to monitor network connections’ state and analyze traffic flow context. By maintaining information about the state of each connection, the firewall can make more informed decisions about which packets to allow or block.
Application awareness
Modern firewall software often includes application awareness capabilities. It can identify specific applications or protocols within network traffic, allowing organizations to enforce granular policies based on the application or service used. This feature is handy for managing and securing web applications and controlling the use of specific services or applications.
Logging and reporting
Firewall software logs network events, including connection attempts, rule matches, and other security-related activities. Detailed logging enables organizations to analyze and investigate security incidents, track network usage, and ensure compliance with regulatory requirements. Reporting capabilities help generate comprehensive reports for auditing, security analysis, and compliance purposes.
Integration with the security ecosystem
Firewall software is typically part of a broader security ecosystem within an organization. Integration with other security tools and technologies, such as antivirus software, threat intelligence platforms, Security Information and Event Management (SIEM) systems, and network access control (NAC) solutions, allows for a more comprehensive and coordinated approach to network security.
Benefits of working with enterprise firewalls
Key advantages of enterprise firewall solutions include enhanced network security, threat mitigation, and access control, as well as traffic analytics data.
- Network security: Firewalls act as a protective barrier against external threats such as unauthorized access attempts, malware, and other malicious activity. Enforcing access control policies and modifying network traffic helps prevent unauthorized access and protect critical data.
- Threat mitigation: By combining intrusion prevention techniques, deep packet monitoring, and threat intelligence, a firewall can detect and block suspicious traffic, reducing the risk there that the network will be corrupted and damaged so
- Access control: Firewall software allows administrators to restrict or allow access to network resources, applications, and services based on specific user roles, departments, or needs. This ensures that only authorized people or systems can access the screen and its accessories.
- Traffic data and analytics: In addition to protecting your network, firewalls can also provide granular information about traffic and activity passing through your network, as well as its overall performance.
How do I choose the best enterprise firewall solution for my business?
When choosing the best enterprise firewall software for your business, consider the following factors.
- Security: Assess your organization’s specific security needs and requirements.
- Features: Evaluate the features and capabilities of firewall solutions, such as packet filtering, application awareness, intrusion prevention, VPN support, centralized management, and scalability. Consider the vendor’s reputation, expertise, and support services.
- Compatibility: Ensure compatibility with your existing network infrastructure and other security tools.
- Hands-on tests: Conduct a thorough evaluation of different firewall solutions through demos, trials, or proofs of concept to assess their performance, ease of use, and effectiveness in meeting your organization’s security goals.
- Total cost of ownership (TCO): Consider the cost, licensing models, and ongoing support and maintenance requirements.
By considering these factors, you can make an informed decision and select the best enterprise firewall software that aligns with your business needs and provides robust network security.
Frequently Asked Questions (FAQ)
Is an enterprise firewall different from a normal firewall?
Although they share many characteristics, an enterprise firewall is not the same as a consumer-grade firewall. Enterprise firewalls are designed to meet large organizations’ security needs and network infrastructure challenges. They are robust, scalable, and can handle high network traffic volumes and sophisticated threats, compared to generic firewalls for home or small office environments.
What is the strongest type of firewall?
A firewall’s strength depends on various factors, and no universally dependable firewall exists. A firewall’s effectiveness depends on its materials, configuration, and how well it fits into the organization’s security needs.
That said, next-generation firewalls (NGFWs) provide improved security capabilities and are often considered the ideal firewall solution in today’s enterprise. NGFWs combine traditional firewall features with additional functionality such as application awareness, intrusion prevention, deep packet monitoring, and user-based policies. They provide advanced protection against modern threats with greater visibility and control over network traffic.
How do you set up an enterprise firewall?
Setting up an enterprise firewall involves several steps:
- Determine your network topology.
- Define security policies.
- Plan firewall placement.
- Configure firewall rules.
- Implement VPN and remote access.
- Test and monitor firewall performance.
- Perform regular updates and maintenance.
We recommend engaging network security experts or reviewing vendor documentation and support materials for specific guidance in installing and configuring your enterprise firewall.
Methodology
The firewall solutions mentioned in this guide were selected based on extensive research and industry analysis. Factors such as industry reputation, customer reviews, infrastructure, and customer support were considered.
We also assessed the features and capabilities of the firewall solutions, including packet filtering, application awareness, intrusion prevention, DLP, centralized management, scalability, and integration with other security tools.
Also see
If you’re not sure one of the firewalls included here is right for your business, we also determined the best firewalls for SMBs, as well as the best software-based firewalls.
And once your firewall is in place, don’t neglect its maintenance. Here are the best firewall audit tools to keep an eye on its performance.
Source :
https://www.enterprisenetworkingplanet.com/security/enterprise-firewalls/