June 30, 2023
Remote users can connect to their Windows 10 and 11 computers through the Remote Desktop Services (RDP). All you need to do is enable Remote Desktop, grant the user RDP access permissions, and connect to the computer using any remote desktop client. However, the number of concurrent RDP sessions is limited in desktop versions of Windows. Only one active Remote Desktop user session is allowed.
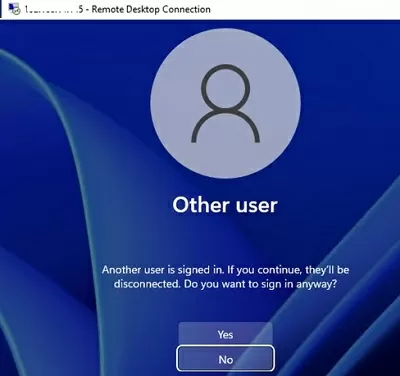
A warning will appear asking you to disconnect the first user’s session if you try to establish a second RDP connection.
Another user is signed in. If you continue, they’ll be disconnected. Do you want to sign in anyway?
Contents:
- Number of Concurrent RDP Connections on Windows
- RDP Wrapper: Enable Multiple RDP Sessions on Windows
- RDP Wrapper Not Working on Windows
- Patch the Termsrv.dll to Enable Multiple Remote Desktop Sessions
- Multiple Concurrent RDP Connections in Windows 10 Enterprise Multi-session
Number of Concurrent RDP Connections on Windows
There are a number of restrictions on the use of Remote Desktop Services in all desktop versions of Windows 10 and 11:
- Only Windows Professional and Enterprise editions can accept remote desktop connections. RDP access is not allowed to Home/Single Language Windows editions;
- Only one simultaneous RDP connection is available. Attempting to start a second RDP session will prompt the user to end the active session;
- If the user is working at the computer console (locally), their local session is disconnected (locked) when they make a remote RDP connection. The remote RDP session will also be terminated if the user logs into Windows from the computer’s console.
The number of concurrent RDP connections on Windows is actually a license limitation. Microsoft prohibits the creation of a workstation-based Terminal RDP server for multiple users to work simultaneously.
If your tasks require the deployment of a terminal server, Microsoft suggests purchasing Windows Server (allows two simultaneous RDP connections by default). If you need more concurrent user sessions, you will need to purchase RDS CALs, install, and configure the Remote Desktop Session Host (RDSH) role or deploy an RDS farm.
Technically, any version of Windows with sufficient RAM and CPU resources can support dozens of remote user sessions simultaneously. On average, an RDP user session requires 150-200MB of memory (excluding running apps). This means that the maximum number of concurrent RDP sessions is limited only by the available resources of the computer.
In this article, we are going to show you three ways to remove the limit on the number of concurrent RDP connections in Windows 10 and 11:
- RDP Wrapper
- Modifying the termsrv.dll file
- Upgrading Windows 10/11 edition to Enterprise for virtual desktops (multi-session)
Note. Any modifications to the operating system that are described in this article are considered a violation of the Windows License Agreement and may be used at your own risk.
Before you proceed, make sure that the Remote Desktop protocol is enabled in Windows.
- Go to Settings -> System —> Remote Desktop -> Enable Remote Desktop;
- Or use the classic Control Panel: run the command
SystemPropertiesRemoteand check the option Allow remote connection to this computer.
Find out how to enable and configure Remote Desktop on Windows.
RDP Wrapper: Enable Multiple RDP Sessions on Windows
The RDP Wrapper Library OpenSource project allows you to enable multiple RDP sessions on Windows 10/11 without replacing the termsrv.dll file. This tool acts as a layer between SCM (Service Control Manager) and the Remote Desktop Services. The RDP wrapper doesn’t make any changes to the termsrv.dll file, it simply loads the termsrv with the modified settings.
Thus, the RDPWrap will work even in the case of termsrv.dll file update. It allows you not to be afraid of Windows updates.
Important. Before installing the RDP Wrapper, it is important to make that you are using the original (unpatched) version of the termsrv.dll file. Otherwise, RDP Wrapper may become unstable or not start at all.
You can download the RDP Wrapper from the GitHub repository https://github.com/binarymaster/rdpwrap/releases (the latest available version of the RDP Wrapper Library is v1.6.2). The project hasn’t been updated since 2017, but it can be used in all new builds of Windows 10 and 11. To use the wrapper on modern versions of Windows, simply update the rdpwrap.ini configuration file.
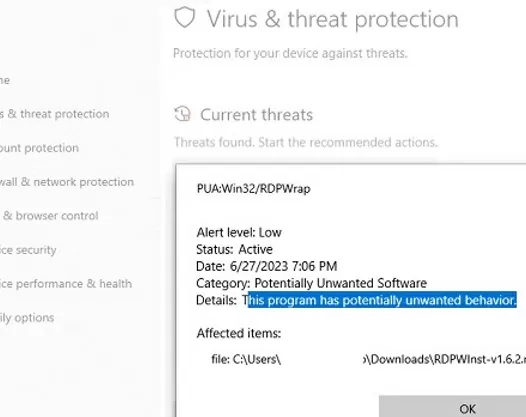
RDP Wrapper is detected as a potentially dangerous program by most antivirus scanners. For example, it is classified as PUA:Win32/RDPWrap (Potentially Unwanted Software) with a low threat level by the built-in Microsoft Defender antivirus. If your antivirus settings are blocking the RDP Wrapper from starting, you will need to add it to the exceptions.
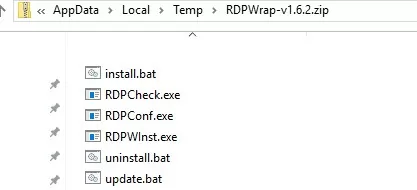
The RDPWrap-v1.6.2.zip archive contains some files:
- RDPWinst.exe — used to install/uninstall an RDP wrapper library;
- RDPConf.exe — RDP Wrapper configuration tool;
- RDPCheck.exe —an RDP check tool (Local RDP Checker);
- install.bat, uninstall.bat, update.bat — batch files to install, uninstall, and update RDP Wrapper.
To install RDPWrap, run the install.bat file as an administrator. The program is installed in the C:\Program Files\RDP Wrapper directory.
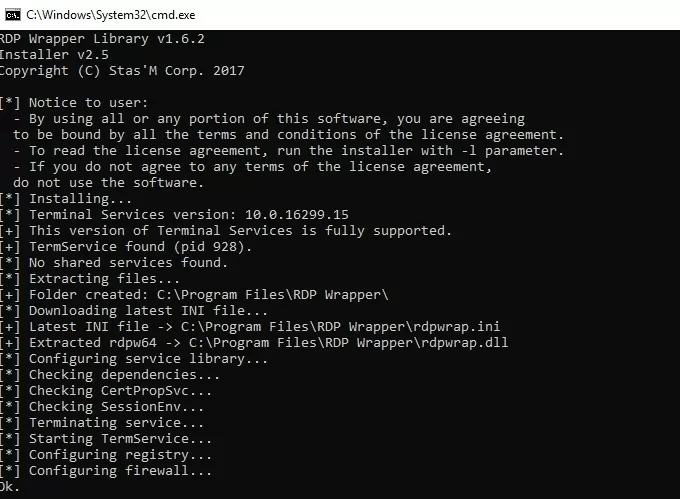
Run RDPConfig.exe when the installation is complete.
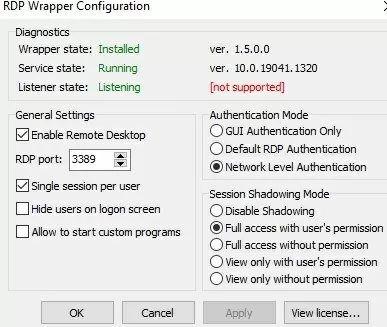
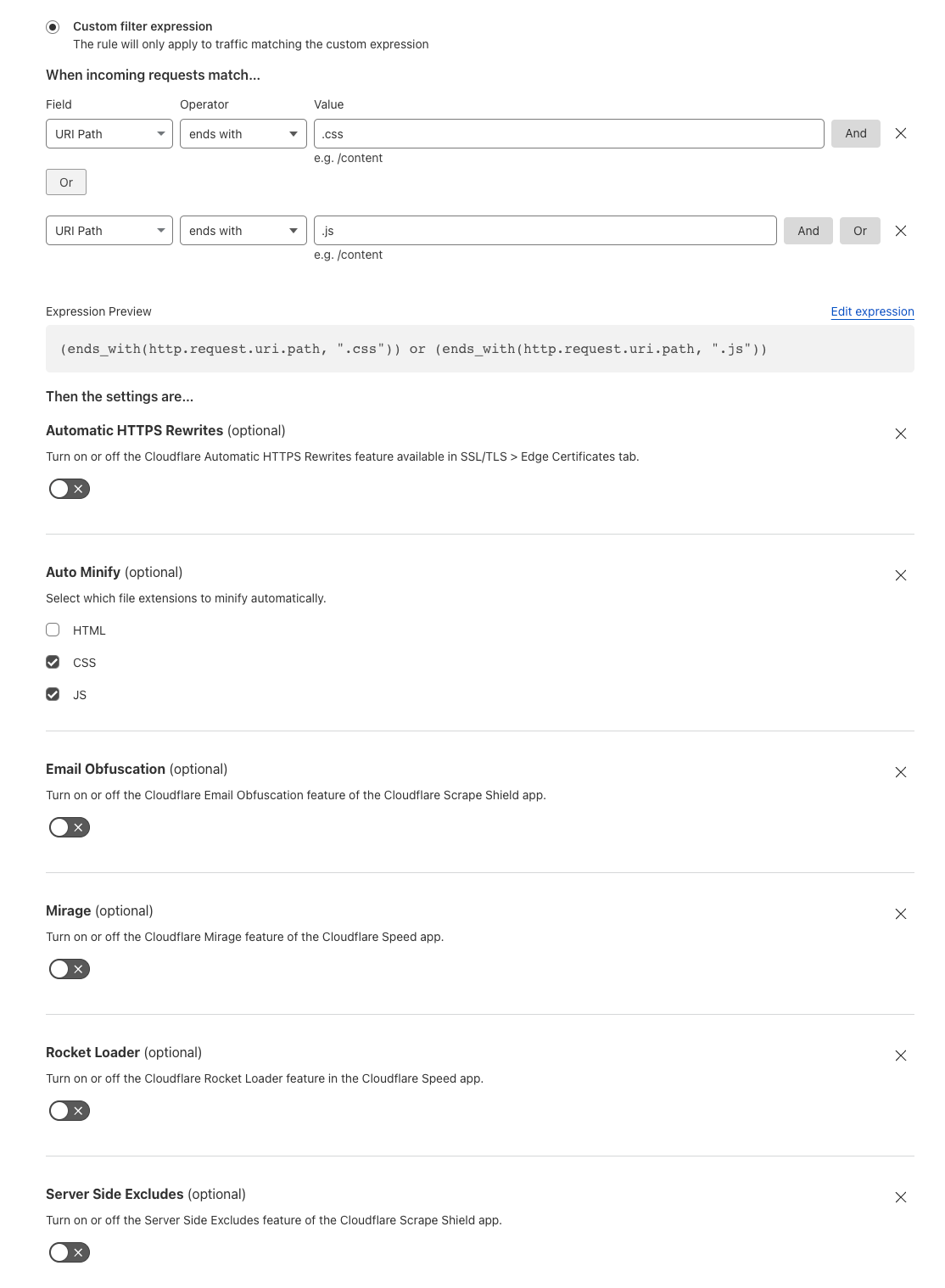
Most likely, immediately after installation, the tool will show that the RDP wrapper is running (Installed, Running, Listening), but not working. Note the red [not supported] warning. It reports that this version of Windows 10 22H2 (ver. 10.0.19041.1949) is not supported by the RDPWrapper.
This is because the rdpwrap.ini configuration file does not contain settings for your Windows version (build). +
✅ Download the latest version of rdpwrap.ini here https://raw.githubusercontent.com/sebaxakerhtc/rdpwrap.ini/master/rdpwrap.ini
Manually copy the contents of this page into the C:\Program Files\RDP Wrapper\rdpwrap.ini file. Or download the INI file using the PowerShell cmdlet Invoke-WebRequest (you must first stop the Remote Desktop service):
Stop-Service termservice -Force
Invoke-WebRequest https://raw.githubusercontent.com/sebaxakerhtc/rdpwrap.ini/master/rdpwrap.ini -outfile "C:\Program Files\RDP Wrapper\rdpwrap.ini"
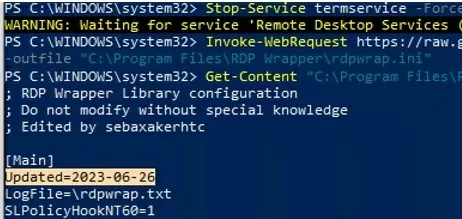
You can create a scheduled task to check for changes to rdpwrap.ini and update it automatically.
This screenshot shows that the latest version of the rdpwrap.ini file (Updated=2023-06-26) is used on the computer.
Restart your computer and run the RDPConfig.exe tool. Check that all items in the Diagnostics section are green and that the [Fully supported] message is displayed. The RDP wrapper started successfully on Windows 11 22H2 in my case.
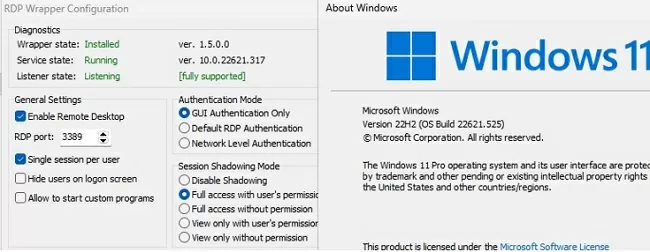
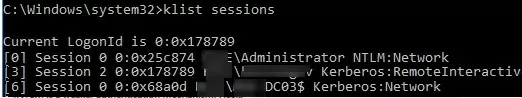
Now try to establish several concurrent RDP sessions with this computer under different user accounts (use your favorite RDP client: mstsc.exe, RDCMan, mRemoteNG, etc).
You can use saved RDP credentials to connect to a remote computer.
You can check that two (or more) RDP sessions are active on the computer at the same time by using the command:
qwinsta
rdp-tcp#0 user1 1 Active rdp-tcp#1 user2 2 Active

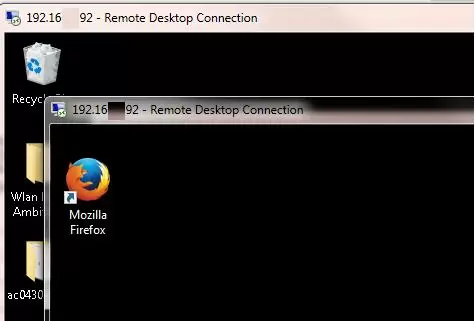
The RDPWrap tool is supported in all Windows editions, so you can build your own terminal (RDS) server on any Windows device. So you can turn any version of Windows client into a full-featured terminal server.
The following options are available in the RDP Wrapper:
- Enable Remote Desktop
- RDP Port —change the default remote desktop port number (TCP 3389)
- Hide users on logon screen – allow hide the list of users from the Windows Logon Screen;
- Single session per user — allow several concurrent RDP sessions under the same user account. This option sets the fSingleSessionPerUser registry value to 0 (
HKLM\SYSTEM\ CurrentControlSet\Control\Terminal Server\fSingleSessionPerUser). This parameter is also configured through the GPO option Restrict Remote Desktop Services to a single Remote Desktop Services session under Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Connections; - The Session Shadowing Mode allows you to configure the remote control (shadow) connection mode to the RDP users’ desktops
You can set limits on the duration of RDP user sessions using the Group Policy. This allows idle user sessions to be automatically disconnected.
RDP Wrapper Not Working on Windows
In some cases, the RDP Wrapper may not work as you expect it to and you may not be able to use more than one RDP connection on Windows.
The termsrv.dll file version can be updated during Windows Updates installation. If the description for your version of Windows is missing from the rdpwrap.ini file, then the RDP Wrapper will not be able to apply the necessary settings. In this case, the status [not supported]. will be displayed in the RDP Wrapper Configuration window.
✅ In this case, you must update the rdpwrap.ini file as described above.
If RDP Wrapper does not work after updating the rdpwrap.ini file, try to open the rdpwrap.ini file and look for the section for your version of Windows.
How to understand if your Windows version is supported in rdpwrapper config?
The screenshot below shows that for my version of Windows 11 (10.0.22621.317) there are two sections of settings:
[10.0.22621.317] ... [10.0.22621.317-SLInit] ...
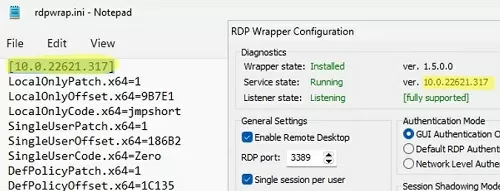
If there is no section in the rdpwrap configuration file for your version of Windows, try searching the web for the rdpwrap.ini file. Add the configuration settings you found to the end of the file.
If RDP Wrapper does not work after you install security updates or upgrade the Windows build, check that there is no Listener state: Not listening warning in the RDPWrap Diagnostics section.
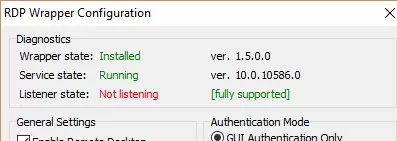
Try updating the rdpwrap.ini file, and then reinstalling the rdpwrapper service:
rdpwinst.exe -u
rdpwinst.exe -i
It can happen that when you try to make a second RDP connection as a different user, you will get an error message:
The number of connections to this computer is limited and all connections are in use right now. Try connecting later or contact your system administrator.
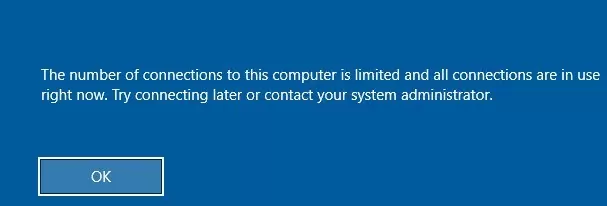
In this case, you can use the local Group Policy Editor (gpedit.msc) to enable the “Limit number of connections” option under Computer Configuration -> Administrative Templates -> Windows Components -> Remote Desktop Services -> Remote Desktop Session Host -> Connections section. Increase the ‘RD maximum connection allowed’ value to 999999.
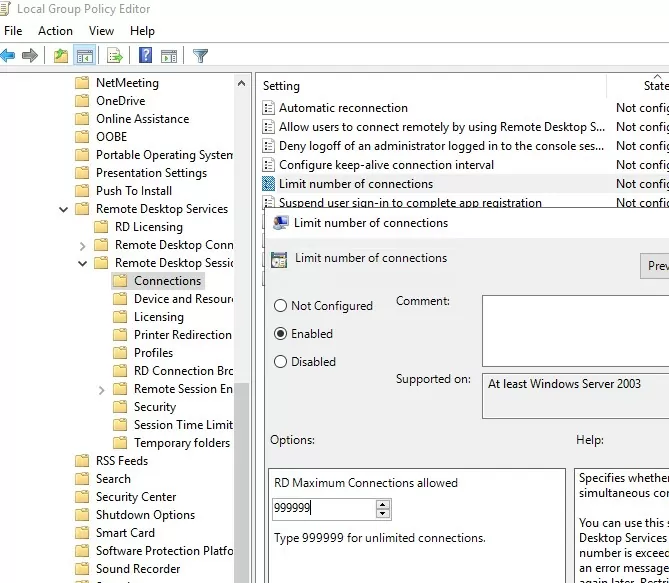
Restart your computer to update the local Group Policy and apply the settings.
Patch the Termsrv.dll to Enable Multiple Remote Desktop Sessions
To remove the limit on the number of concurrent RDP user connections in Windows without using rdpwrapper, you can replace the original termsrv.dll file. This is the main library file used by the Remote Desktop Service. The file is located in the C:\Windows\System32 directory.
It is advisable to make a backup copy of the termsrv.dll file before editing or replacing it. This will help you to revert to the original version of the file if necessary. Open an elevated command prompt and run the command:
copy c:\Windows\System32\termsrv.dll termsrv.dll_backup
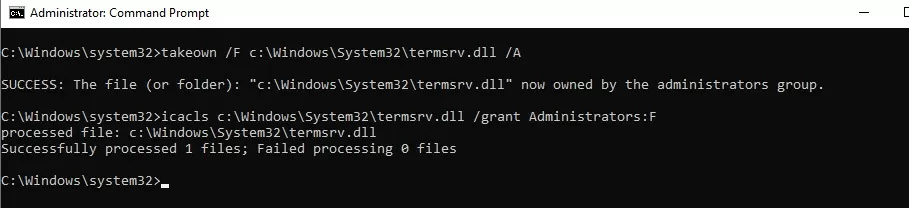
Then you need to take ownership of the termsrv.dll file. To change a file’s owner from TrustedInstaller to the local Administrators group, use the command:
takeown /F c:\Windows\System32\termsrv.dll /A
SUCCESS: The file (or folder): c:\Windows\System32\termsrv.dll now owned by the administrators group
Now use the icacls.exe tool to grant Full Control permissions to the termsrv.dll file for the local Administrators group:
icacls c:\Windows\System32\termsrv.dll /grant Administrators:F
processed file: c:\Windows\System32\termsrv.dll Successfully processed 1 files; Failed processing 0 files.
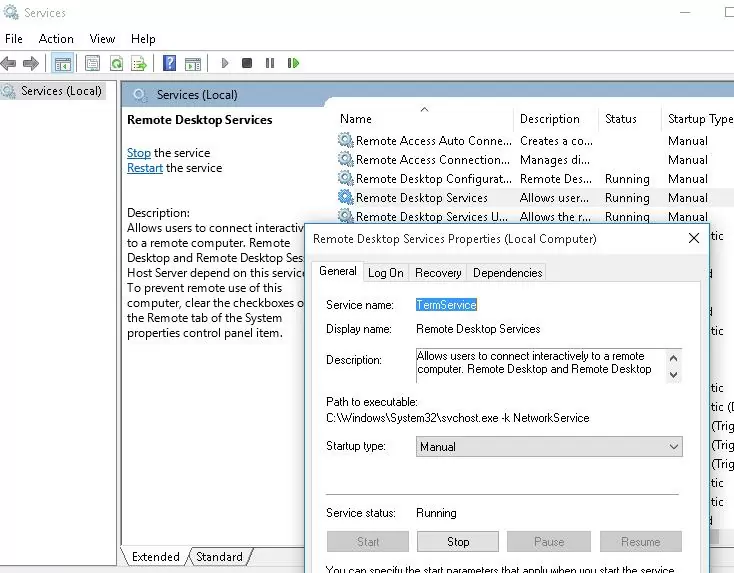
Now you need to stop the Remote Desktop service (TermService) using the services.msc console or with the command:
net stop TermService
It also stops the Remote Desktop Services UserMode Port Redirector service.
Run the winver command or the following PowerShell command to find your Windows build number:
Get-ComputerInfo | select WindowsProductName, WindowsVersion
In my case, Windows 10 build 22H2 is installed.
Then open the termsrv.dll file using any HEX editor (for example, Tiny Hexer). Depending on the build of Windows you are using, you will need to find and replace the string according to the table below:
| Windows build | Find the string | Replace with |
| Windows 11 22H2 | 39 81 3C 06 00 00 0F 84 75 7A 01 00 | B8 00 01 00 00 89 81 38 06 00 00 90 |
| Windows 10 22H2 | 39 81 3C 06 00 00 0F 84 85 45 01 00 | |
| Windows 11 21H2 (RTM) | 39 81 3C 06 00 00 0F 84 4F 68 01 00 | |
| Windows 10 x64 21H2 | 39 81 3C 06 00 00 0F 84 DB 61 01 00 | |
| Windows 10 x64 21H1 | 39 81 3C 06 00 00 0F 84 2B 5F 01 00 | |
| Windows 10 x64 20H2 | 39 81 3C 06 00 00 0F 84 21 68 01 00 | |
| Windows 10 x64 2004 | 39 81 3C 06 00 00 0F 84 D9 51 01 00 | |
| Windows 10 x64 1909 | 39 81 3C 06 00 00 0F 84 5D 61 01 00 | |
| Windows 10 x64 1903 | 39 81 3C 06 00 00 0F 84 5D 61 01 00 | |
| Windows 10 x64 1809 | 39 81 3C 06 00 00 0F 84 3B 2B 01 00 | |
| Windows 10 x64 1803 | 8B 99 3C 06 00 00 8B B9 38 06 00 00 | |
| Windows 10 x64 1709 | 39 81 3C 06 00 00 0F 84 B1 7D 02 00 |
Tiny Hexer cannot edit termsvr.dll file directly from the system32 folder. Copy it to your desktop and replace the original file after modifying it.
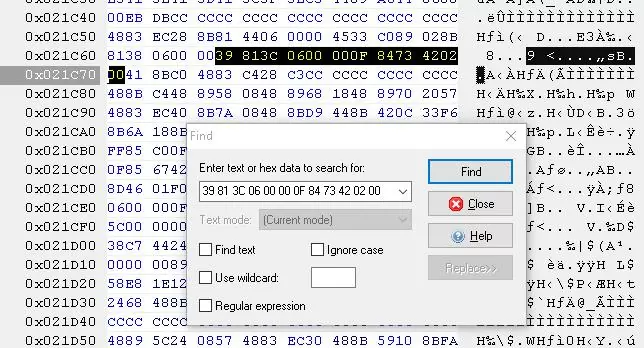
For example, my build of Windows 10 x64 is 22H2 19045.2006 (termsrv.dll file version is 10.0.19041.1949). Open the termsrv.dll file in Tiny Hexer, then find the text:
39 81 3C 06 00 00 0F 84 75 7A 01 00
and replace it with:
B8 00 01 00 00 89 81 38 06 00 00 90
Save the file and start the TermService.
If something goes wrong and you experience some problems with the Remote Desktop service, stop the service and replace the modified termsrv.dll file with the original version:
copy termsrv.dll_backup c:\Windows\System32\termsrv.dll
To avoid manually editing the termsrv.dll file with a HEX editor, you can use the following PowerShell script to automatically patch the termsrv.dll file. The PowerShell script code is available in my GitHub repository at the following link:
This script was written for the Windows PowerShell version and does not work in modern PowerShell Core.
👍 The advantage of the method of enabling multiple RDP sessions in Windows 10 or 11 by replacing the termsrv.dll file is that antivirus software will not react to it (unlike RDPWrap, which is detected by many antivirus products as a malware/hack tool/trojan).
👎The disadvantage of this is that you will have to manually edit the file each time you update the Windows build (or if the monthly cumulative patches update the version of termsrv.dll).
Multiple Concurrent RDP Connections in Windows 10 Enterprise Multi-session
Microsoft has recently released a special edition of the operating system called Windows Enterprise Multi-Session (Previously known as Windows 10 Enterprise for Remote Sessions and Windows 10 Enterprise for Virtual Desktops)
The key feature of this edition is that it supports multiple concurrent RDP user sessions out of the box. Although the Windows multi-session edition is only allowed to be run in Azure VMs, you can install this edition on an on-premises network and use that computer as a terminal server (even though this would be against Microsoft’s licensing policies).
The Enterprise Multi-Session edition is available for both Windows 10 and Windows 11.
Next up, we’re going to show you how to upgrade a Windows 10 Pro edition to Windows 10 Enterprise for Virtual Desktop and use it for multiple RDP users simultaneously.
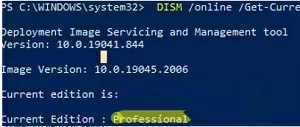
Open a command prompt and check your current edition of Windows (Professional in this example):
DISM /online /Get-CurrentEdition
Upgrade your edition of Windows 10 from Pro to Enterprise with the command:
changepk.exe /ProductKey NPPR9-FWDCX-D2C8J-H872K-2YT43
Now install the GVLK key for Windows 10 Enterprise for Remote Sessions:
slmgr.vbs /ipk CPWHC-NT2C7-VYW78-DHDB2-PG3GK
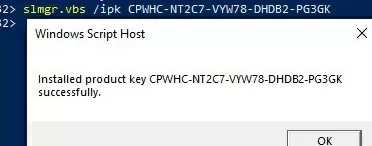
Check that your edition of Windows 10 has now changed to ServerRdsh (Windows 10 Enterprise for Virtual Desktops).

Activate your copy of Windows 10 Enterprise Multi-Session edition on your KMS server:
slmgr /skms kms-srv.woshub.local:1688
slmgr /ato
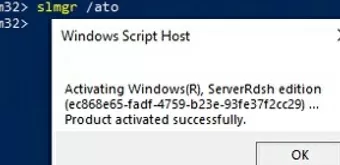
See the Key Management Service (KMS) Activation FAQ.
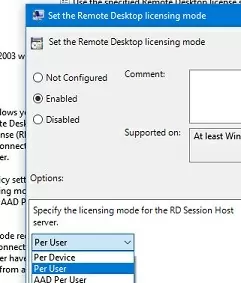
Open the Local GPO Editor (gpedit.msc) and enable Per-User licensing mode in the Set the Remote Desktop licensing mode (Computer Configuration -> Policies -> Administrative Templates -> Windows Components -> Remote Desktop Services -> Remote Desktop Session Host -> Licensing).
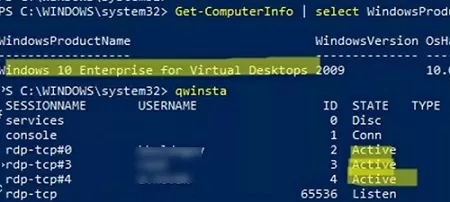
You must restart Windows after activation. Now try connecting to the computer using RDP with different user accounts. As you can see, Windows 10 Enterprise multi-session supports simultaneous RDP connections right out of the box.
Get-ComputerInfo | select WindowsProductName, WindowsVersion, OsHardwareAbstractionLayer
Windows 10 Enterprise for Virtual Desktops 2009 10.0.19041.2728
qwinsta
In this article, we have looked at a number of ways to get rid of the limit on the number of concurrent RDP user connections and run a free terminal server on desktop versions of Windows 10/11. Each method has its own advantages and disadvantages. Which one you choose is up to you.
Source :
https://woshub.com/how-to-allow-multiple-rdp-sessions-in-windows-10/