It’s only been 4 months since the previous major release but we’re already excited to welcome WordPress 6.0. Of course, as with every other major release, you can expect loads of loads of improvements and exciting new features. This new version is no different. WordPress 6.0 continues to refine and iterate on the tools and features introduced in earlier releases. Let’s dive deeper into what WordPress 6.0 brings to your table!
For starters, this release will include all the great new features, enhancements and gains from Gutenberg 12.0 and 13.0. At the same time, developers and contributors continue to work on bug fixes and improvements that significantly impact the overall user experience on WordPress. This translates to over 400 updates, 500 bug fixes, and 91 new features in just one release, which is huge!
We’re getting an improved list view experience, style theme variations, additional templates, new blocks, new enhancements to the block editors and many more. Since there are many new things coming in this release, we’d like to bring your attention to some of the features and improvements that will likely have an impact on the way you use WordPress.
Full site editing enhancements and new features
Full site editing was the talk of the town when this major feature was introduced in previous releases. WordPress 6.0 continues to build upon the groundwork laid in 5.9 and further improves on what you can do with full site editing. You will need to use a block-based theme such as WordPress’s Twenty-Twenty-Two to take advantage of full site editing.
Style variations and global style switcher
Many people in the WordPress community are excited about this feature in the Site editor. You’ll be able to use theme variations derived from one single theme using various color and font combinations. It’s kind of like having several child themes but integrated into one single theme. And it’s incredibly easy to apply a new style variation across your entire site. From now on, you’ll be able to change the look and feel of your website with just a click.
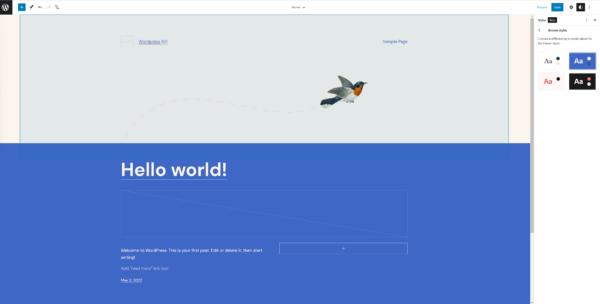
Theme export capability
Another huge improvement to full site editing specifically and the WordPress platform as a whole is the ability to export block themes. Any templates, layouts and style changes you made can be saved and exported to a .zip file. This feature is huge because it’s paving the way for visual theme building. You can create a WordPress theme just by purely using Gutenberg blocks. And of course, no coding knowledge is required!
To export your theme, go to your Site editor and click on the 3 dots icon in your top right corner. There should appear a menu with the option to download your theme.
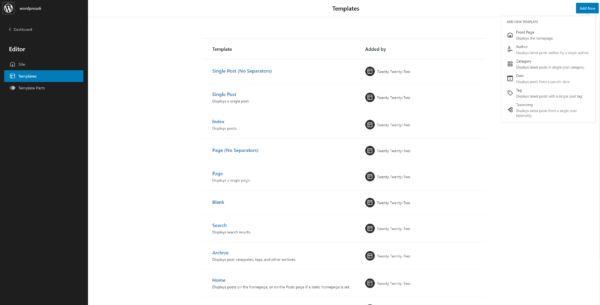
New templates
Being able to use and customize templates to build your website content is great because it helps you to save time. We had templates to work with in previous WordPress versions, but the options were limited. WordPress 6.0 expands on this and introduces several new templates for specific functions. These include templates for displaying posts from a specific author, category, date, tag, or taxonomy.
List view enhancements
When you access the list view in WordPress 6.0, you will see that your blocks are grouped together and collapsed instead of showing everything like in previous versions. This will make navigating the list view much easier. Next to this, when you’re working on a page with the list view open and you click anywhere on the page, it will highlight precisely where you are in the list view. Anyone who regularly works on complex pages should appreciate this enhancement.
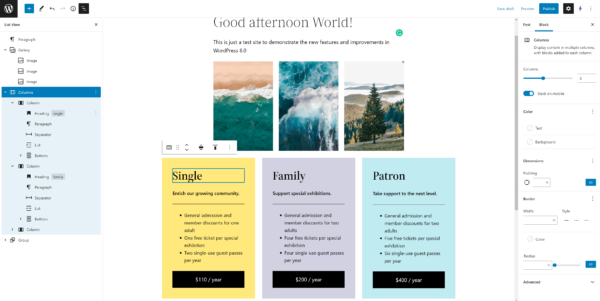
Block editor enhancements
New core blocks
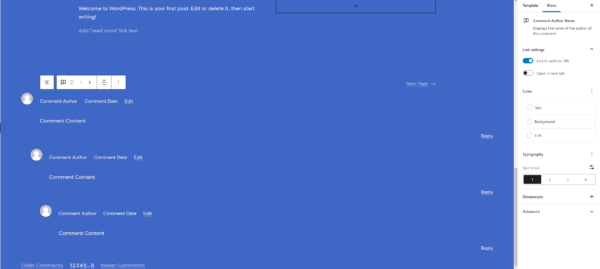
WordPress 6.0 will ship with several new blocks including post author biography, avatar, no result in query loop and read more. We want to point you to the new comment query loop block because it further ‘blockifies’ the comment section of your post. With this new block, you’ll get plenty of customization options to design the comment section the way you want to.
More features and enhancements
There are quite a lot of improvements and enhancements to the block editor that we can’t cover everything in this post. Instead, we will mention a few that we think will be the most beneficial for you.
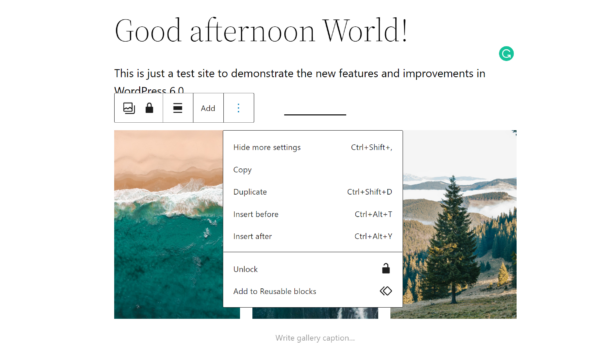
The first new enhancement in the block editor we want to introduce is block locking. Moving forward, you’ll be able to lock a block so it can’t be moved and/or edited. A locked block will display a padlock when you click on it. And when you open the list view, you’ll also see the padlock indicating a locked block. This feature is especially useful if you work a lot with reusable blocks and don’t want anyone messing around with those blocks. It’s also beneficial for preserving design layouts when you’re creating templates or working with clients.
Next to that, in WordPress 6.0, when you customize a button and then add a new button using the plus button, it will have the same style as the one you’ve just customized. Before, you would need to redo all the customization if you want to add several buttons with the same style.
Another cool feature in this new version is style retention. It’s now possible to keep a block’s style when transforming certain blocks from one type to another and vice versa. It works with quite a few blocks, ranging from quote, list, code, heading, pullquote, verse, etcetera.
Lastly, the cover block can now dynamically grab your featured image and set it as the background for the cover block. All you have to do is select the ‘use featured image‘ setting and WordPress will do the rest.
Writing improvements
You can expect several notable writing improvements in this new version of WordPress. They are not major changes by any means, but you’ll definitely notice and appreciate the refinement in your overall writing experience.
Have you ever tried selecting text from 2 separate blocks and got annoyed because it automatically selected all the text from both blocks? Well, you won’t be bothered by that anymore. From WordPress 6.0 onwards, you can easily select text across blocks and edit it to your liking. This is definitely a quality of life improvement.
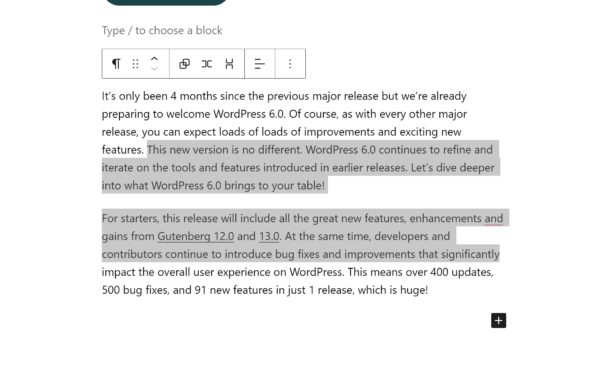
Also coming your way is a new link completer shortcut. You can access this shortcut anytime by typing “[[” and it will show you a list of links on your site. This feature can be handy when you’re doing internal linkings, for instance.
Lastly, WordPress will remind you to add tags and categories as the last step before you can publish a post. When you publish a lot of posts, it can be easy to forget this step so this is quite a neat feature for forgetful folks.
Design and layout tools
We won’t be diving too much into the improvements in design and layout tools, but we do think the following two features deserve a mention.
The first one is transparency control for background, which is very useful when you want to use a background with columns. You’ll surely elevate your post design if you can make use of this feature. The next fun addition to WordPress 6.0 is gap support for the gallery block. This just means you have more control over the spacing of your images, giving you a bit more freedom on how you want to display your image gallery. Anyone can take advantage of these 2 new features, but photography and fashion website runners can probably appreciate them the most.
Source :
https://yoast.com/wordpress-6-0/