The Wordfence Threat Intelligence team has been tracking a large-scale attack against a Remote Code Execution vulnerability in Tatsu Builder, which is tracked by CVE-2021-25094 and was publicly disclosed on March 24, 2022 by an independent security researcher. The issue is present in vulnerable versions of both the free and premium Tatsu Builder plugin. Tatsu Builder is a proprietary plugin that is not listed on the WordPress.org repository, so reliable installation counts are not available, but we estimate that the plugin has between 20,000 and 50,000 installations. Tatsu sent an urgent email notification to all of their customers on April 7th advising them to update, but we estimate that at least a quarter of remaining installations are still vulnerable.
All Wordfence users with the Wordfence Web Application Firewall active, including Wordfence free customers, are protected against attackers trying to exploit this vulnerability.
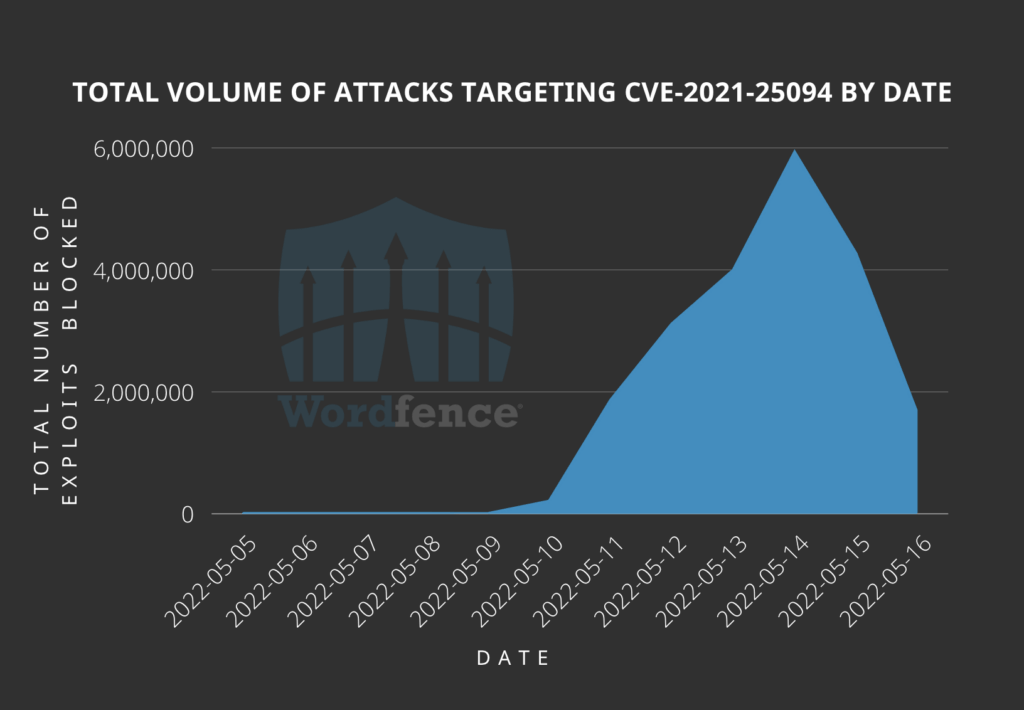
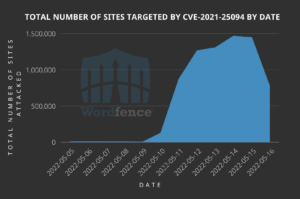
We began seeing attacks on May 10, 2022. The attacks are ongoing with the volume ramping up to a peak of 5.9 million attacks against 1.4 million sites on May 14, 2022. The attack volume has declined but the attacks are still ongoing at the time of publication.
The following is a graph showing the total volume of attacks targeting the vulnerability in Tatsu Builder.
While the following is a graph showing the total number of sites being targeted by attackers trying to exploit the vulnerability in Tatsu Builder.
Description: Unauthenticated Remote Code Execution
Affected Plugin: Tatsu Builder
Plugin Slug: tatsu
Plugin Developer: BrandExponents
Affected Versions: < 3.3.13
CVE ID:CVE-2021-25094
CVSS Score: 8.1 (High)
CVSS Vector:CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H
Researcher/s: Vincent Michel (darkpills)
Fully Patched Version: 3.3.13
Indicators of Attack
Most of the attacks we have seen are probing attacks to determine the presence of a vulnerable plugin. These may appear in your logs with the following query string:
/wp-admin/admin-ajax.php?action=add_custom_font
The vast majority of attacks are the work of just a few IP addresses.
The top 3 attacking IPs have each attacked over 1 million sites:
148.251.183.254176.9.117.218217.160.145.62
An additional 15 IPs have each attacked over 100,000 sites:
65.108.104.1962.197.136.10251.38.41.1531.210.20.17031.210.20.10185.202.169.17585.202.169.7185.202.169.8685.202.169.3685.202.169.8385.202.169.92194.233.87.72.56.56.20385.202.169.129135.181.0.188
Indicators of Compromise
The most common payload we’ve seen is a dropper used to place additional malware located in a randomly-named subfolder of wp-content/uploads/typehub/custom/ such as wp-content/uploads/typehub/custom/vjxfvzcd.
The dropper is typically named .sp3ctra_XO.php and has an MD5 hash of 3708363c5b7bf582f8477b1c82c8cbf8.
Note the dot at the beginning as this indicates a hidden file, which is necessary to exploit the vulnerability as it takes advantage of a race condition.
This file is detected by the Wordfence scanner.
What Should I Do?
All Wordfence users with the Wordfence Web Application Firewall active, including Wordfence free customers, are protected against this vulnerability. Nonetheless, if you use the Tatsu Builder plugin, we strongly recommend updating to the latest version available, which is 3.3.13 at the time of this writing. Please note that version 3.3.12 contained a partial patch but did not fully address all issues.
If you know anyone using the Tatsu Builder plugin on their site, we urge you to forward this article to them as this is a large-scale attack and any vulnerable sites that are not updated and not using some form of a Web Application Firewall are at risk of complete site takeover.
If you believe your site has been compromised as a result of this vulnerability or any other vulnerability, we offer Incident Response services via Wordfence Care. If you need your site cleaned immediately, Wordfence Response offers the same service with 24/7/365 availability and a 1-hour response time. Both these products include hands-on support in case you need further assistance.
Source :
https://www.wordfence.com/blog/2022/05/millions-of-attacks-target-tatsu-builder-plugin/