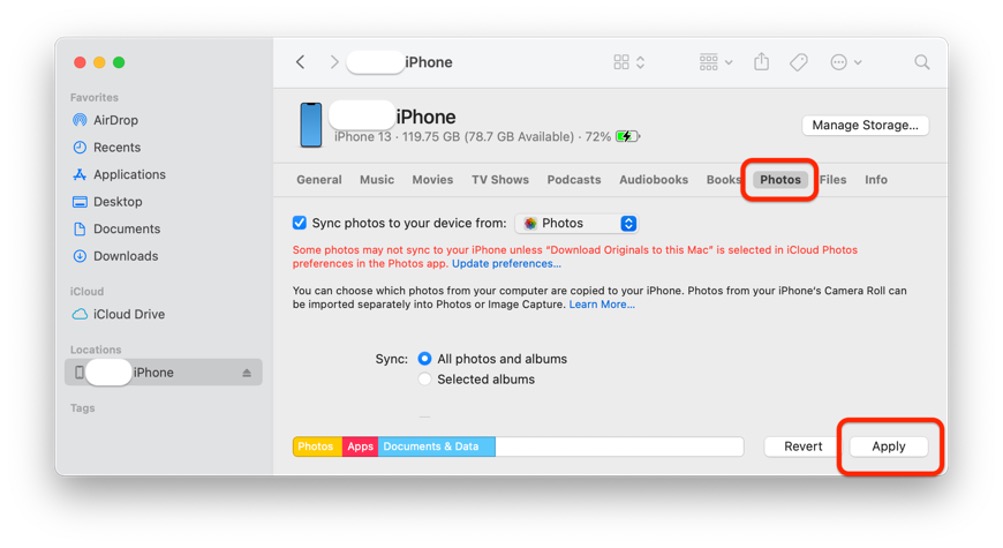
In the modern world, searching for information is simple. There’s no need to go from one library to another, flipping through numerous pages, or checking the table of contents before you get to what you’re looking for. Simply typing words on the internet will give you limitless results — all you need to do is narrow them down.
What is a Search Engine?
If you need to find something, like a website or page that contains your needed information, you’ll need to go and visit a search engine page to query keywords.
A search engine is a program or application that checks, hunts, and searches the web for sites based on keywords. It uses these keywords and returns pages that are connected to what you have typed.
Search engines use web crawlers or web spiders to catalog the World Wide Web. These crawling bots are used for indexing contents. They will scan, check, assess and inspect site pages and their information across the web.
Notable Search Engines and Their Brief Histories
Archie — During the 1990s, the very first search engine arrived, named Archie. Its purpose was to search FTP sites to create indexes of files that are downloadable.
Veronica and Jughead — Created around 1992/93, they both searched file names and titles in Gopher index systems.
Infoseek — In 1994, Webmasters would submit and provide a page in real-time with this program.
Yahoo Search — Also created in 1994, it created a collection of favorable web pages with description of each website.
Looksmart, Excite and AltaVista — These search engines were created in 1995 and tried to compete with Yahoo.
Backrub — Created around 1996, Google’s initial project, Backrub, was a search engine that utilized backlinks for searches. It ranked pages depending on citations from other sites.
Ask Jeeves — Started in 1996, this search engine used human editors that tried to match search queries.
Google — Officially launched in 1998.
MSN Search — Relied on three different search engines: Looksmart, Overture and Inktomi.
Snap — A somewhat complex search engine, released in 2005, that shows search volumes, revenues and advertisers.
Bing — Rebranded name for MSN/Live Search.
Schema.Org — In 2011, Microsoft, Google and Yahoo collaborated to create Schema.org to create structured internet data.
Top 10 Most Used Search Engines
The following list contains the top ten from across the world:
1. Google:“Just google it” is a ubiquitous expression nowadays. Google is the most popular across all search engines — even more than all others combined. According to statistics, around 78% of desktops and laptops uses Google.
2. Yahoo: In the past, Yahoo had competed with Google. But as the years went on, Yahoo users had declined significantly. Now it is mostly used as a backup search engine in case the dominant one is down.
3. Bing: Microsoft Bing (or just Bing) is owned by Microsoft. Its origin came from MSN Search and Windows Live Search. This search engine is proud of its ‘decision’ engine which provides suggestions on the sides.
4. AOL Search: Known before as American Online Search. This search engine is used mostly by older people accustomed to AOL.
5. Duck Duck Go: Some say that Duck Duck Go is for and by Hipsters. But the main reason users choose this search engine is that it does not track search history and avoids spammy websites.
6. Baidu: This search engine is the 3rd largest out there. Baidu dominates the Chinese market and is the first choice in China. This engine has a sophisticated online censorship system since there’s many restrictions in its operating region.
7. Yandex: If Baidu has China as its market, then Yandex has the Russian market.
8. Ask: Its origin is the older “Ask Jeeves”. Since it could not compete with Google, it’s now powered by Google — if you can’t beat ‘em, join ‘em!
9. Naver: South Korea is another huge tech and communications market with its own search engine, Naver.
10.Seznam: The search engine popular in the Czech Republic and C. Europe.
And some honorable mentions:
- Ecosia — Donates surplus income to organizations that plant trees.
- Dogpile — Shows results from the top 3 search engines (Google, Bing and Baidu).
- Gigablast — An open-source search engine.
- Qwant — A popular, EU-based search engine.
Tips For Using Search Engines
Search engines are brilliant tools to immediately get the information we want. However, since search engines generally do not have much security capability, you should invest in a security product to provide and efficient browsing.
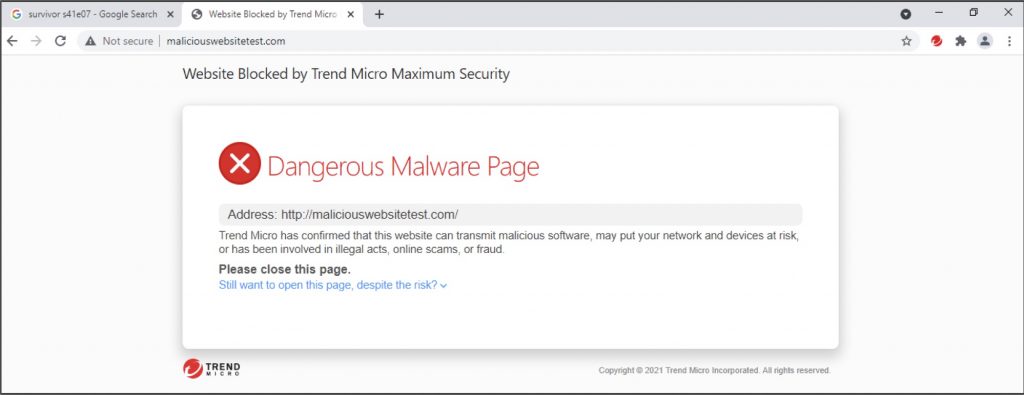
1. Install the Maximum Security tool bar to prevent you from visiting malicious websites.
You can install the Trend Micro Maximum Security toolbar service, which warns you of security risks relevant to the websites you visit.
When you search online, it monitors and rates websites in search engines such as Google, Bing, Baidu, and Yahoo. The Trend Micro Toolbar provides Page Ratings that show if the page is safe, suspicious, dangerous, trusted or untested.
- A Mac User? No problem. Trend Micro Antivirus for Mac has the same toolbar feature to protect your online activity.
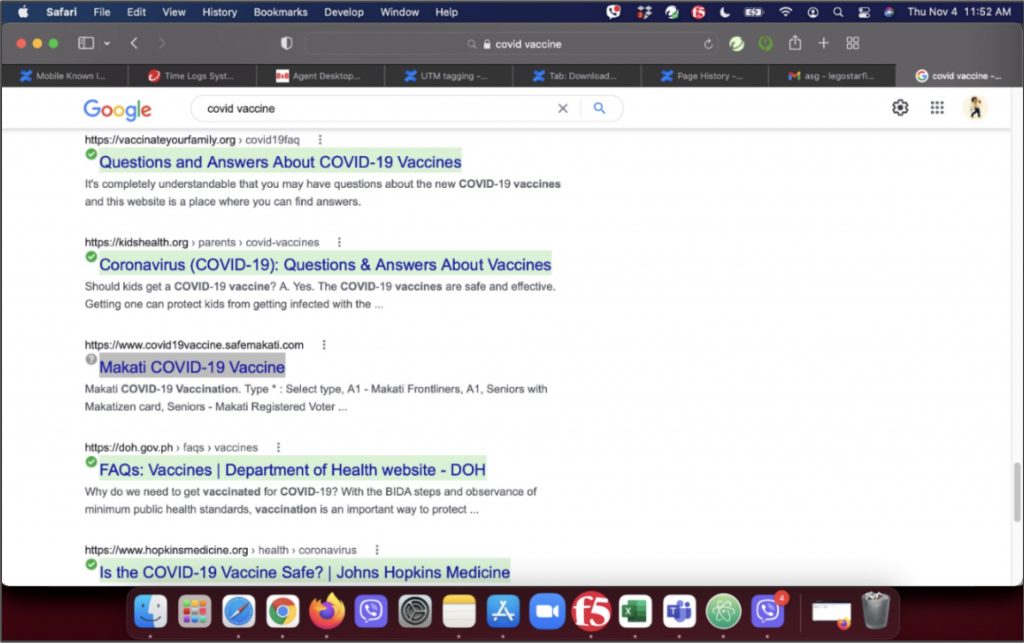
2. Install AdBlock One to stop annoying ads.
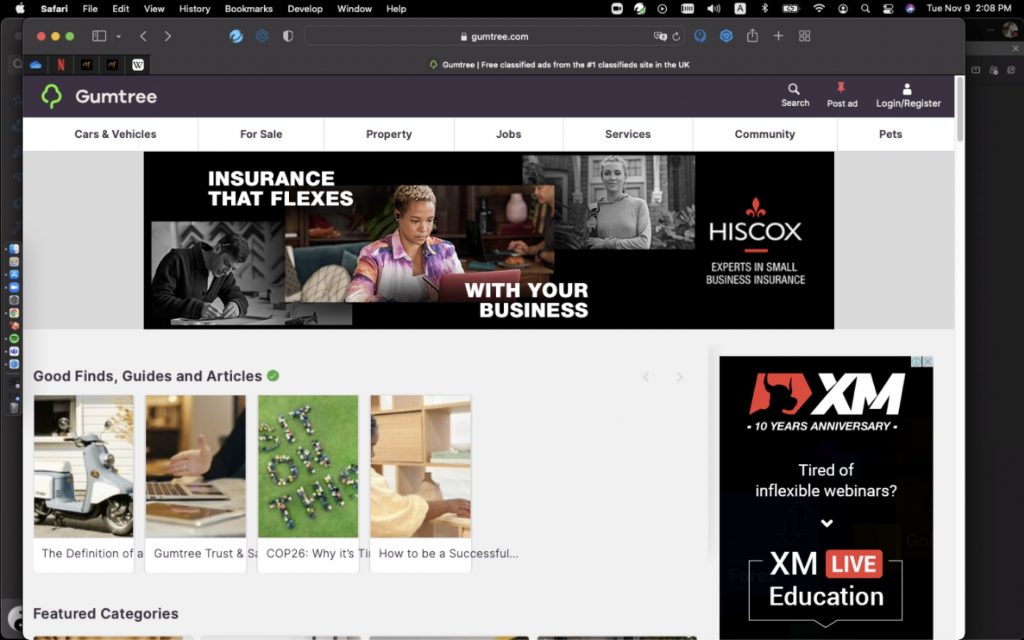
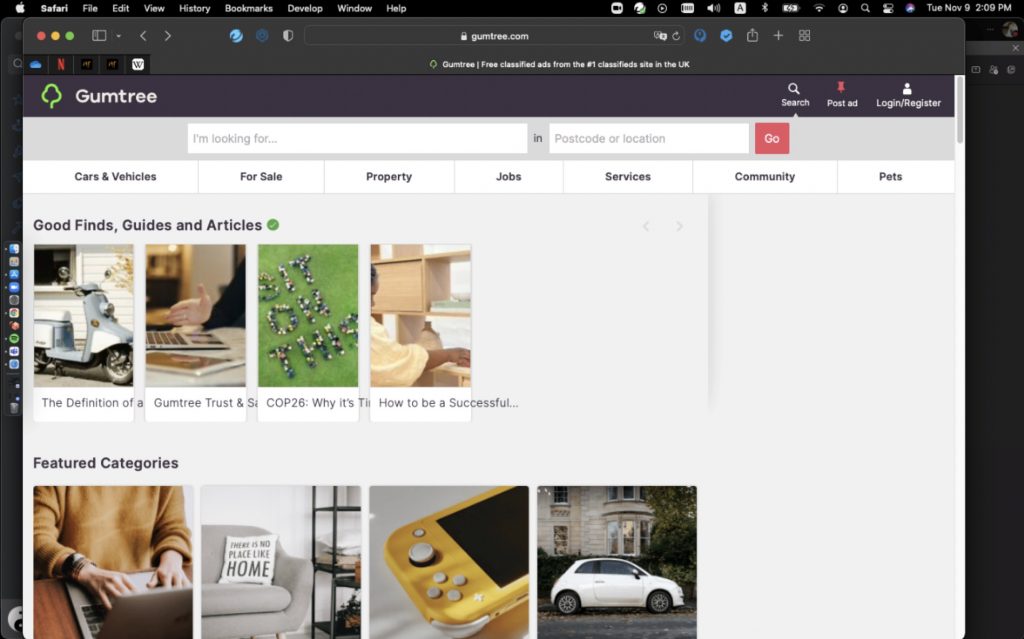
In addition, be sure to also use AdBlock One for Safari. This app stops annoying online ads from bothering you and helps load web pages faster — a significant boost in securing and improving your digital life.
Without AdBlock One
With AdBlock One
If you’ve found this article an interesting and/or useful read, please do SHARE with family and friends.
Source :
https://news.trendmicro.com/2021/11/25/top-10-most-used-search-engines-tips-for-browsing/