Tried to upgrade your PC to Windows 11, but run into the dreaded ‘This PC can’t run Windows 11’ error message? Don’t give up, it could be because your system doesn’t have two security settings turned on: Secure Boot and TPM 2.0.
Trend Micro Windows 11 Upgrade Helper checks eight aspects of your computer, and perhaps most crucially, which TPM version it is running. Windows 11 requires TPM 2.0, so if your PC is not currently running or is not capable of running TPM 2.0, Windows 11 Upgrade Helper will let you know.Get Windows 11 Upgrade Helper
What are TPM and Secure Boot?
Trusted Platform Module (TPM) is a technology designed to provide hardware-based, security-related functions. A TPM chip is a secure crypto-processor that is designed to carry out cryptographic operations. The chip includes multiple physical security mechanisms to make it tamper-resistant. Malicious software isn’t able to tamper with the security functions of the TPM, either.
Secure Boot is a feature from the latest Unified Extensible Firmware Interface (UEFI). It offers another layer of protection against potential malware infections. It can detect when boot loaders or key operating system files are being tampered with by malware and actively block them before they can infect the system. Both TPM and Secure Boot offer unique ways of strengthening the protection of Windows 11.
Is my device capable of TPM 2.0 and Secure Boot?
To check if your device has Secure Boot, you can follow these steps:
1. In the Windows search box, type “System Information” and open the System Information app.
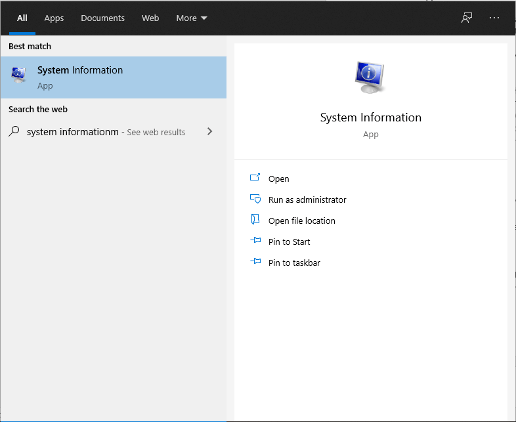
2. Select System Summary, and in the panel on the right side, look for “Secure Boot State”.
3. The value indicates the status of Secure Boot. “On” means it is turned on, “Off” means it is disabled, and “Unsupported” means your hardware does not support Secure Boot.
To check if your device has TPM, follow the steps below:
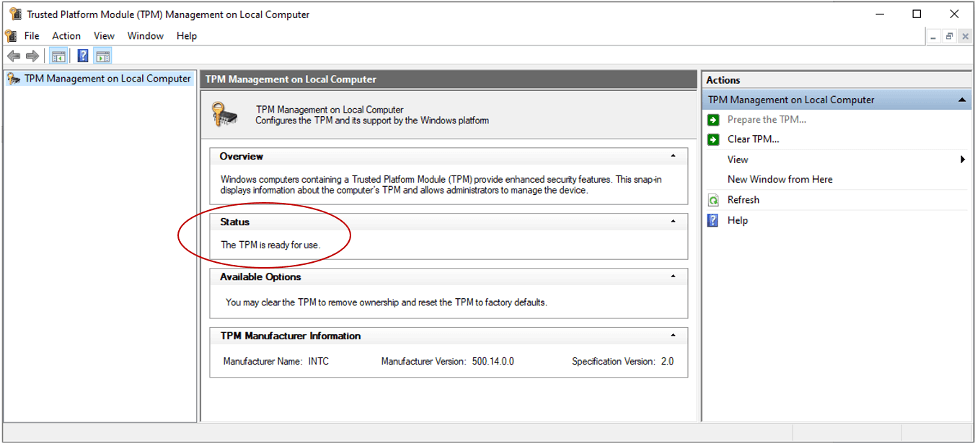
1. In the Windows search box, type “tpm.msc” and click Open.
2. Under Status, if you see “The TPM is ready for use”, you know that the TPM is present and available. If you see the message “Compatible TPM cannot be found”, it means that either your computer cannot find the TPM or that it has been disabled in the BIOS or UEFI.
You can also check if your device is using TPM 2.0 through Device Manager. Here’s how to do so:
1. Right-click on the Windows Start menu icon located in the lower left of your screen, then select Device Manager.
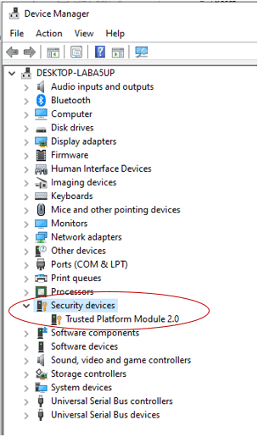
2. Select Security Devices from the list and it will show you what TPM chip you have. If it says Trusted Platform Module 2.0, you are good to go.
How to enable TPM and Secure Boot
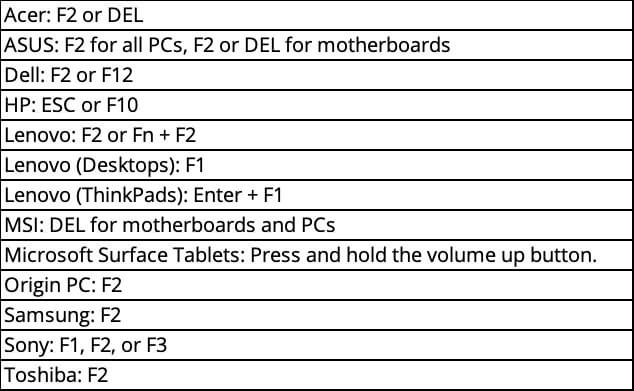
To enable TPM and Secure Boot, you need to restart your computer to access the BIOS settings. After restarting, at the boot screen, press your computer’s BIOS access key. The most common BIOS access keys are DEL and F2. Here’s a reference for popular PC and motherboard brands and their BIOS access keys:
In the example below, we show you how to enable TPM on an ASUS TUF Gaming Z490-PLUS [WI-FI] motherboard, but the instructions will almost certainly differ depending on which brand of PC or motherboard you have.
1. At the UEFI BIOS Utility screen, press F7 to access Advanced Mode.
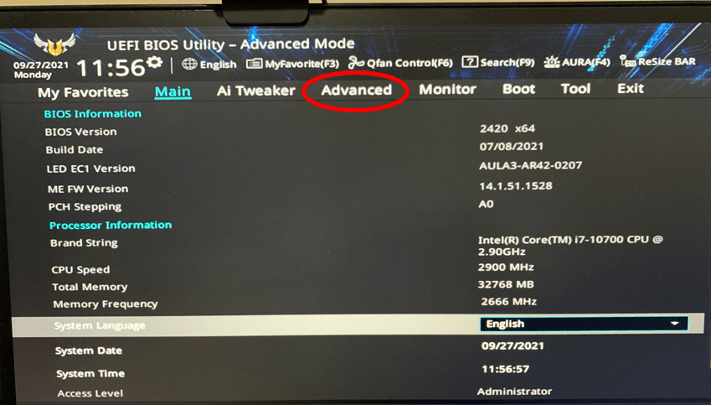
2. Click the “Advanced” tab and select “PCH-FW Configuration”.
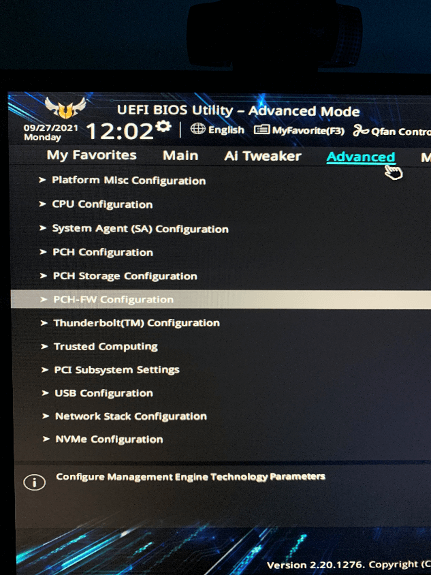
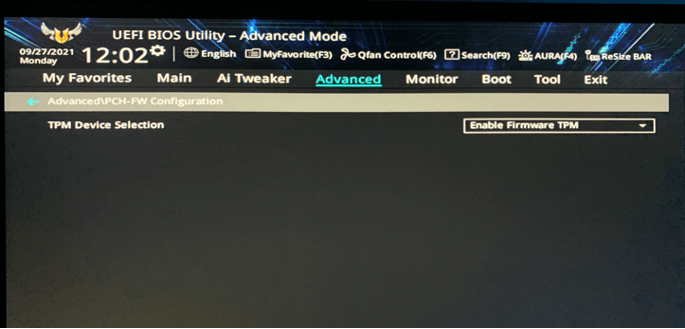
3. Alongside “TPM Device Selection”, select “Enable Firmware TPM”.
To enable Secure Boot, in the “Boot” tab, follow the steps below:
1. Select “Secure Boot”.
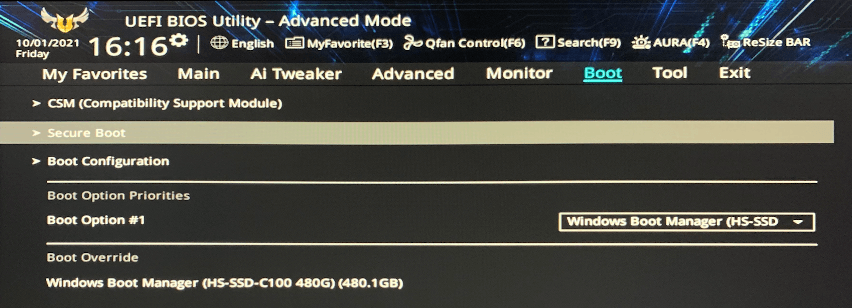
2. Select “OS Type” and beside it, select “Windows UEFI Mode”.
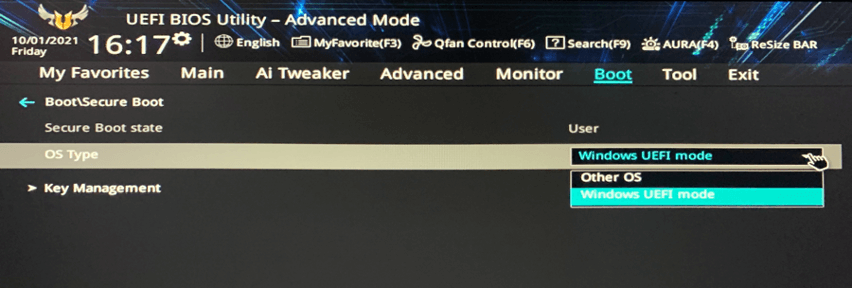
3. Go to the “Exit” tab to save the changes and restart the computer. TPM and Secure Boot will be enabled after the restart.
What can I do if I don’t have a TPM chip?
Your device may have a TPM chip, but you need to update your BIOS to have access to it. Please contact your PC or motherboard manufacturer to learn more about how to enable TPM on your device.
You could also buy a TPM module online, but you must know which TPM module is compatible with your motherboard. You also need to install the module onto the motherboard, which might not be an easy task — especially if you don’t have any experience in working with motherboards. If you would like to go down this route, we advise that you contact a technician or take it to a local PC repair shop.
Alternatively, you could upgrade to a new computer.
What’s the most convenient way to check if I can upgrade to Windows 11?
There are tools created that can help you assess if your computer is ready for Windows 11. One of those tools is Trend Micro Windows 11 Upgrade Helper .
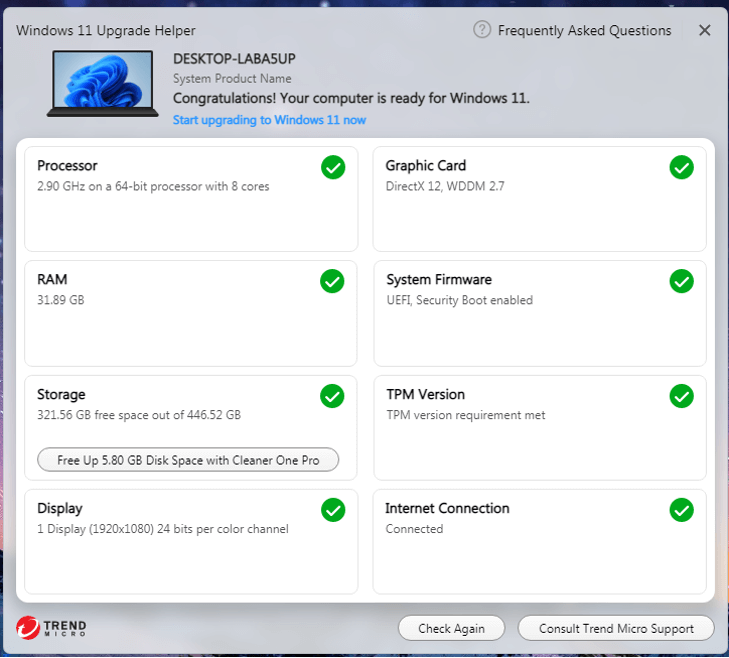
Trend Micro Windows 11 Upgrade Helper can check if your computer meets all the requirements for Windows 11. You can talk to Premium Support Service if you need assistance in making your computer Windows 11 ready, too.Get Windows 11 Upgrade Helper
Source :
https://news.trendmicro.com/2021/10/04/fix-the-this-pc-cant-run-windows-11-error-how-to-enable-tpm-and-secure-boot/