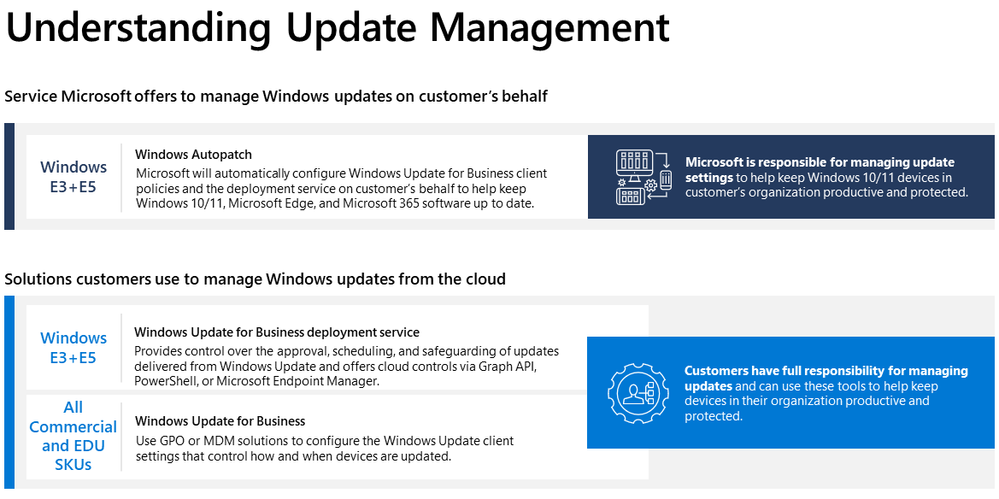
IT teams rely on Active Directory (AD) to keep networks secure and maintain user accounts — but they often need to adhere to strict budget limitations when it comes to selecting software to help. That’s why we’ve put together this list of the top free Active Directory management tools.
Our picks focus on AD tools that will help you complete routine AD management tasks much faster so your team has time to focus on other priorities. We’ve grouped these free Active Directory tools into three categories:
Active Directory Reporting, Monitoring and Auditing Tools
Microsoft Active Directory Explorer
Microsoft Active Directory Explorer is an advanced administration tool that makes it easy to search for, view and edit extended information about AD objects. It is similar to AD Users and Computers but has at least one key additional benefit — it allows you to view object properties and attributes without opening additional dialog boxes.
AD Explorer also enables you to save snapshots of an AD database for offline viewing and database version comparisons. When you load a saved snapshot, you can work with it as you would use a live database.
Other features include:
- Defining favorite locations
- Editing permissions
- Viewing an object’s scheme
- Executing sophisticated searches that you can save and re-execute
Handpicked related content:
Netwrix Auditor for Active Directory
Netwrix Auditor for Active Directory (free community edition) gives you visibility into what’s happening inside domains while eliminating the time-consuming tasks of analyzing endless native logs. Netwrix Auditor tracks logons and all changes to Active Directory users, groups, organizational units and Group Policy. It generates a daily activity summary that details all changes and logon activity that occurred during the previous 24 hours, including the before and after values for each modification.
Netwrix Account Lockout Examiner
Netwrix Account Lockout Examiner is well known as one of the best Active Directory tools for quickly resolving one of the most pressing issues with AD: account lockouts. It enables you to identify the root cause of lockouts in a single keystroke, slashing troubleshooting time by up to 90 percent. This lightweight and intuitive tool empowers you to investigate issues like why the same account repeatedly locks out without having to slog through a mountain of cryptic event logs — just enter the username and click a button.
Netwrix Effective Permissions Reporting Tool
Netwrix Effective Permissions Reporting Tool simplifies auditing of access permissions in Active Directory. You can view a user’s account group membership, the permissions the account has to every AD object and how those permissions are granted. It also shows file and folder effective permissions, so you can determine who has access to your data and how their access was gained. You can export this information to an HTML file.
Netwrix Bulk Password Reset
Netwrix Bulk Password Reset enables you to reset local admin and user passwords across multiple workstations at once, remotely, without actually logging into them. This functionality enhances Windows Server security.
Netwrix Inactive User Tracker
Netwrix Inactive User Tracker provides insight into stale Active Directory user accounts so you can disable or delete unneeded accounts before malicious actors can exploit them to gain access to resources and services on your network.
Netwrix Password Expiration Notifier
Netwrix Password Expiration Notifier automatically sends notifications about upcoming AD password expiration to users and their managers. This proactive approach enables you to remain in compliance with password security best practices without sacrificing user productivity or increasing helpdesk workload.
Cjwdev Active Directory Info
Cjwdev Active Directory Info is a free Active Directory reporting and analysis tool that enables you to review the configuration settings of AD objects. You can quickly generate CSV, HTML or TXT reports to gain insight into things like:
- Locked accounts
- Users who have never logged on
- Users with the “password never expires” flag
- Enabled and disabled users
- Deleted groups
- Computers deleted in the last 30 days
- Group Policy objects modified in the last 30 days
Cjwdev Active Directory Permissions Reporter
Cjwdev Active Directory Permissions Reporter extracts all permissions for every object in your domain. Note that the free edition of Cjwdev AD Permissions Reporter does not support the command line and you cannot filter or export results.
ENow Compass
ENow Compass provides real-time network monitoring to help you identify issues that could evolve into bigger problems. ENow Compass is a powerful toolset, but the company does not offer a free version. Users can start with a 14-day free trial with registration.
MaxPowerSoft Active Directory Reports Lite
MaxPowerSoft Active Directory Reports Lite allows you to load up to 200 objects from Active Directory and generate auditing reports on users, groups, organizational units, computers and GPOs. The paid version of grants access to more reports and many more features.
Active Directory FastReporter
Active Directory FastReporter generates a variety of predefined reports on your AD infrastructure. The free version doesn’t allow you to create custom reports, export reports or use automation features.
LDAPSoft Active Directory Browser
LDAPSoft Active Directory Browser simplifies SSL communication and streamlines the process of browsing your AD hierarchy. You can search for entries, view all available attributes and run SQL-LDAP statements.
Softerra Browser for LDAP
Softerra Browser for LDAP is a lightweight tool that allows you to view, browse, search and export information from LDAP. It is free to use for 30 days — you’ll need to register a paid account to use it past this point.
WiseSoft Password Control
WiseSoft Password Control can reset user passwords in bulk, which saves time and effort when managing service account passwords. It also includes the ability to make other bulk changes, such as enabling and disabling user accounts, group membership functions, descriptions and departments.Handpicked related content:
Active Directory Management Tools
Albus Bit Active Directory Administrator
Albus Bit Active Directory Administrator enables you to manage user and computer accounts across your Active Directory domain from a single interface. You can use the built-in search templates or create your own, and use the results to disable inactive accounts, move accounts to different organizational units or remove users from groups.
CjWdev Active Directory Tidy
CjWdev Active Directory Tidy allows you to easily manage your AD accounts in bulk. For example, you can add multiple accounts to a specific security group, or set random passwords or a particular expiry date for a set of accounts.
The tool’s filtering functionality makes it easy to clean up your AD. For example, you can filter by last login date to find all inactive user and computer accounts to determine whether you should remove them from your domain. The paid version of this tool also enables you to export AD settings to XML.
Spiceworks People View
Spiceworks People View allows you to view and update AD user account properties, such as email, phone number, title and department. You can also add devices to user profiles to monitor installed software programs and update it when needed. You can also reset passwords and enable or disable user accounts. The tool also offers self-administered password and user profile management on a self-service web portal, and real-time status monitoring of all your devices.
Spiceworks offers other useful tools. For example, Network Monitor performs real-time status monitoring of all your devices.
Microsoft AdRestore
Microsoft AdRestore is a single-task tool that enumerates all tombstoned objects in your AD domain and enables you to restore them individually as needed.
Windows PowerShell
Windows PowerShell is undoubtedly the most powerful Active Directory tool. However, it can be challenging to use because it lacks a graphical interface. To accomplish your tasks, you’ll need to use cmdlets and scripts like the following:
- Disable a user account: Disable-ADAccount username
- Enable a user account: Enable-ADAccount username
- Unlock a user account: Unlock-ADAccount username
- Delete a user account: Remove-ADUser username
- Find all empty groups: Get-adgroup -filter * | where {-Not ($_ | get-adgroupmember)} | Select Name
- Add a member to a group: Add-adgroupmember “groupname” –username
- Enumerate the members of a group: Get-ADGroupMember “groupname”
- See what groups a user account is a member of: Get-aduser username -property Memberof | Select -ExpandProperty memberOf
- Disable a computer account: Disable-ADAccount -Identity “computername”
- Find computers by type: Get-ADComputer -Filter * -Properties OperatingSystem | Select OperatingSystem -unique | Sort OperatingSystem
- Create an organizational unit: New-ADOrganizationalUnit -Name OUname -Path “dc=domainname,dc=com”
- Create a computer account: New-ADComputer -Name username -Path “ou=OUname,dc=DCname,dc=com”
- Create a user account: New-ADUser -Name username -Path “ou=OUname,dc=DCname,dc=com”
Adaxes
Adaxes streamlines routine management functions in Active Directory, Microsoft Exchange and Microsoft 365 environments. You can use it to delegate privileges, control authorizations and stay in compliance with data mandates. Softerra offers a 30-day free trial.
CENTREL Solutions XIA Automation
CENTREL Solutions XIA Automation helps you automate IT management tasks, such as account provisioning, user management and password changes. It includes time-saving features like bulk provisioning of accounts from CSV to AD, Exchange, Google or Office 365.
Dameware Remote Everywhere
Dameware Remote Everywhere is a pricey commercial-grade tool at $540 (and up), but it is notable for its powerful functionality — especially for enterprise-level network needs.
“Remote Everywhere” refers to the tool’s cloud-based solutions. Users enjoy safe, remote support with advanced encryption and multifactor authentication, essential endpoint support for any computer or device, and a reporting engine that can handle virtually any reporting task. New users can get a fully functional version of Dameware Remote Everywhere for 14 days.
Active Directory Utility Tools
Microsoft Active Directory Replication Status (ADREPLSTATUS) Tool
Microsoft ADREPLSTATUS Tool is a single-purpose tool that helps you analyze the replication of domain controllers in your network.
Cjwdev Group Manager
Cjwdev Group Manager allows the manager of a group to manage roles and settings for the group, including adding and removing other users and exporting group members to a CSV file. The free edition enables you to manage only a single group, and you cannot or add new members from other domains.
Cjwdev Active Directory Photo Edit
Cjwdev Active Directory Photo Edit enables you to import and upload images to an AD attribute that can be displayed in Outlook 2010, Lync and SharePoint. The free edition can’t process pictures for users and contacts in bulk, but the paid version offers this feature.
Cjwdev Managed Service Accounts GUI
Cjwdev Managed Service Accounts GUI helps you configure managed service accounts using an intuitive GUI that eliminates the need for PowerShell commands.
Specops Password Auditor
Specops Password Auditor scans your Active Directory and identifies password-related vulnerabilities so you can reduce your attack surface and maintain compliance.
Specops Software Gpupdate
Specops Software Gpupdate enables remote administration of computers and organizational units. For example, you can refresh Group Policy or wake up, shut down or restart a PC remotely.
Specops Command
Specops Command is a PowerShell and VBScript interface that helps you automate many Active Directory administrative tasks.
Zohno Z-Hire and Z-Term
Zohno Z-Hire and Z-Term are single-task tools. Z-Hire speeds the user account creation process for new hires, while Z-Term helps with account removal when an employee leaves the organization.
SysOpsTools Active Directory Query
SysOpsTools Active Directory Query is a free executable tool — no installation required — that can be used to quickly search AD for information about a specific user or computer, including schema attributes that are normally not readable.
RIA-Media SysAdmin and SysAdmin Anywhere
RIA-Media SysAdmin and RIA-Media SysAdmin Anywhere are helpful for facilitating a long list of activities:
- Resetting user passwords
- Adding, editing and deleting AD objects
- Adding photos
- Shutting down and restarting computers remotely
- Checking for updates
- Monitoring hardware and computers
SysAdmin and SysAdmin Anywhere both offer a free trial.
Codeplex ADModify.NET
Codeplex ADModify.NET is a single-use tool that allows you to modify multiple user attributes at once.
WiseSoft Bulk Password Control
WiseSoft Bulk Password Control enables you to change passwords on multiple accounts at the same time using the tool’s password generator feature. You can also enable, disable and unlock AD accounts in bulk.
Conclusion
With so many options to choose from, it can be challenging to find the right mix of AD management tools for your needs. The most effective way to make that choice is to install different tools and try them out in your AD environment. This will give you insight into how well they will work for your specific needs and preferences.
Source :
https://blog.netwrix.com/2021/03/10/active-directory-tools/