Cloud communications company Twilio says some of its customers’ data was accessed by attackers who breached internal systems after stealing employee credentials in an SMS phishing attack.
“On August 4, 2022, Twilio became aware of unauthorized access to information related to a limited number of Twilio customer accounts through a sophisticated social engineering attack designed to steal employee credentials,” Twilio said over the weekend.
“The attackers then used the stolen credentials to gain access to some of our internal systems, where they were able to access certain customer data.”
The company also revealed the attackers gained access to its systems after tricking and stealing credentials from multiple employees targeted in the phishing incident.
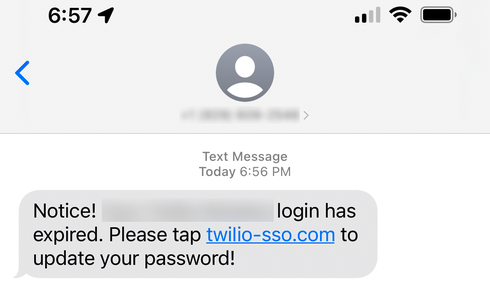
To do that, they impersonated Twilio’s IT department, asking them to click URLs containing “Twilio,” “Okta,” and “SSO” keywords that would redirect them to a Twilio sign-in page clone.
The SMS phishing messages baited Twilio’s employees into clicking the embedded links by warning them that their passwords had expired or were scheduled to be changed.
Twilio’s EMEA Communications Director Katherine James declined to provide more information when asked how many employees had their accounts compromised in the phishing attack and how many customers were affected by the breach, saying the company has “no additional comment to provide at this time beyond what is posted in the blog.”
“The text messages originated from U.S. carrier networks. We worked with the U.S. carriers to shut down the actors and worked with the hosting providers serving the malicious URLs to shut those accounts down,” Twilio added.
“We have heard from other companies that they, too, were subject to similar attacks, and have coordinated our response to the threat actors – including collaborating with carriers to stop the malicious messages, as well as their registrars and hosting providers to shut down the malicious URLs. Despite this response, the threat actors have continued to rotate through carriers and hosting providers to resume their attacks.”
Credentials revoked, attackers yet to be identified
The company has not yet identified the attackers, but it’s working with law enforcement as part of an ongoing investigation.
Twilio revoked the employee accounts compromised during the attack to block the attackers’ access to its systems and has started notifying customers affected by this incident.
“As the threat actors were able to access a limited number of accounts’ data, we have been notifying the affected customers on an individual basis with the details,” Twilio also revealed.
The company also disclosed in May 2021 that it was impacted by last year’s Codecov supply-chain attack where threat actors modified the legitimate Codecov Bash Uploader tool to steal credentials, secret keys, and user tokens from Codecov customers.
With more than 5,000 employees in 26 offices in 17 countries, Twillio provides programmable voice, text, chat, video, and email APIs used by over 10 million developers and 150,000 businesses to build customer engagement platforms.
Twilio also acquired Authy in February 2015, a popular two-factor authentication (2FA) provider for end users, developers, and enterprises with millions of users worldwide.
Source :
https://www.bleepingcomputer.com/news/security/twilio-discloses-data-breach-after-sms-phishing-attack-on-employees/