How to find free stock images for business and commercial use
Stock photo sites are a dime a dozen, so it can be tough to know where to find free, high-quality images that aren’t also on every other website.
And as a freelancer and a business owner, I’ve done my fair share of scouring the web for that perfect stock photo. So I spent several weeks reviewing dozens of stock photo websites—and I narrowed it down to the nine best for your next project.
The 9 best free stock photo sites
- Unsplash for the widest variety of free stock images (and integrations)
- Pixabay for a variety of media types
- Gratisography for quirky images you won’t see anywhere else
- Canva for adding simple enhancements and overlays
- Burst for eCommerce companies
- New Old Stock for vintage photos
- Reshot for UX/UI designers
- 123RF for photo sizes optimized for social media
- Flickr for interacting with the photography community
How to find the best websites with 100% free stock photos
How we evaluate and test apps
All of our best apps roundups are written by humans who’ve spent much of their careers using, testing, and writing about software. We spend dozens of hours researching and testing apps, using each app as it’s intended to be used and evaluating it against the criteria we set for the category. We’re never paid for placement in our articles from any app or for links to any site—we value the trust readers put in us to offer authentic evaluations of the categories and apps we review. For more details on our process, read the full rundown of how we select apps to feature on the Zapier blog.
Finding images that are free for commercial use isn’t as hard as it might sound, thanks to a number of sites that aggregate photos, illustrations, vectors, and more. These sites usually let you search and filter by keyword or category, making it easy to find what you’re looking for. But that doesn’t mean every stock photo site is worth perusing.
The best free stock image sites all meet the following criteria:
5 things you should automate today
- They must contain images that can be used without payment for both commercial and personal purposes.
- I focused on sites that have at least 500 photos, but I favored ones that offer thousands of images.
- A lot of free stock photo sites essentially offer the same pictures. I looked for sites that offered unique images, so your content can stand out.
- If you plan to use stock photos for your website or branded content, you’ll need high-quality resolutions. Every site on this list offers at least one high-quality download size for its photos.
- And of course, the website itself should be fast, easy to navigate, and from this century.
When reviewing these sites, I visited each one and signed up for an account if necessary. I explored the site’s menus and conducted a number of searches to see what types of photos would come up. I reviewed the quality of the photos and took note of things like how advanced the search filters were, whether there were high-resolution download sizes available, and if there was anything uniquely useful about the stock photo site in question.
Best free stock photos site for a variety of photos and integrations
Unsplash (Web, iOS, Android)
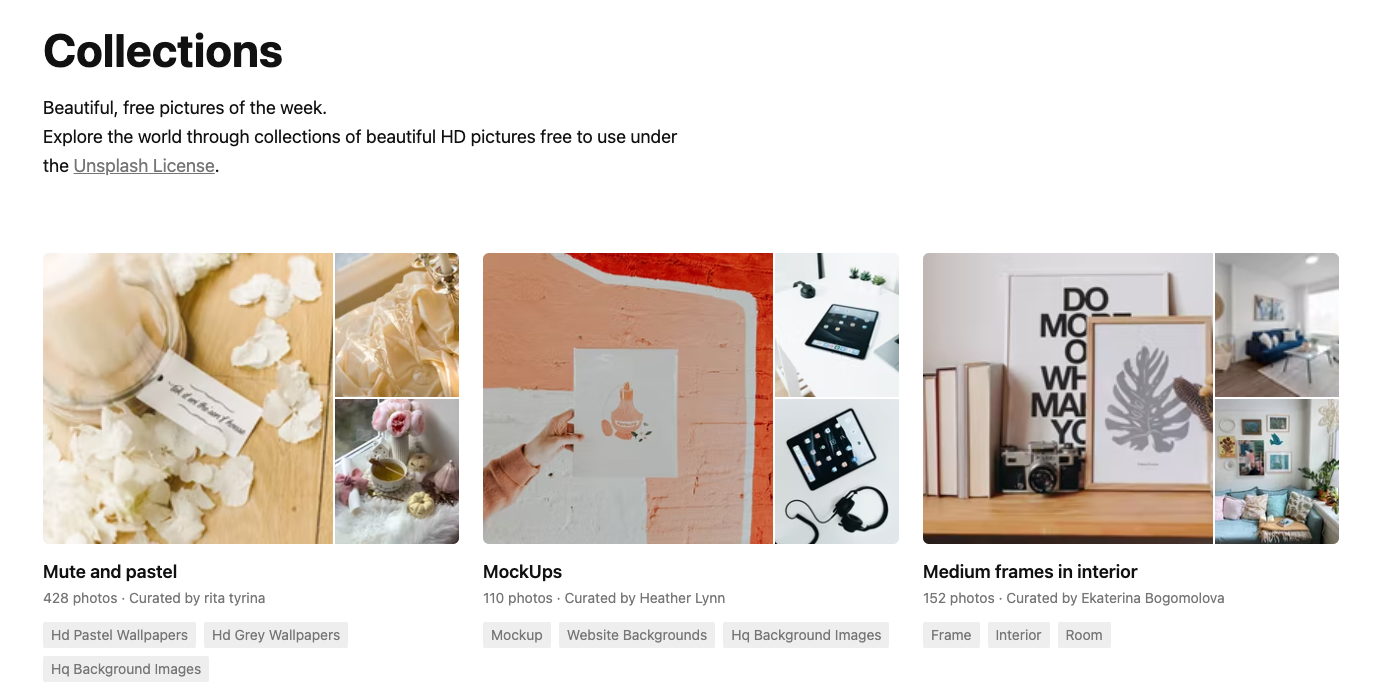
With more than three million photos and multiple plugins, Unsplash is one of the most easily accessible and largest collections of stock photos available.
It comes with native apps like an iOS app, an Android photo picker, Apple TV and desktop wallpaper apps, and even a Chrome extension that randomly selects a background image when you open your browser. Unsplash’s API is also already natively integrated into popular tools like Figma, Notion, Trello, and Squarespace, letting you search and use high-quality stock photos without leaving your favorite platform.
The site is also easy to use: type a keyword into the search bar at the top of the page, and browse the results to find the best images for your purposes. And if you don’t know what you’re looking for, there are category tabs along the top of the homepage for inspiration.
Another feature that sets Unsplash apart from other free photo sites is its Collections section. Users of the site are able to create Collections—like “Christmas Traditions,” “Autumn,” and “Milkyway“—by curating photos they come across. If you want several similar photos of a specific theme, Unsplash may be your best option.
Best free stock photos site for a variety of media types
Pixabay (Web, iOS, Android)
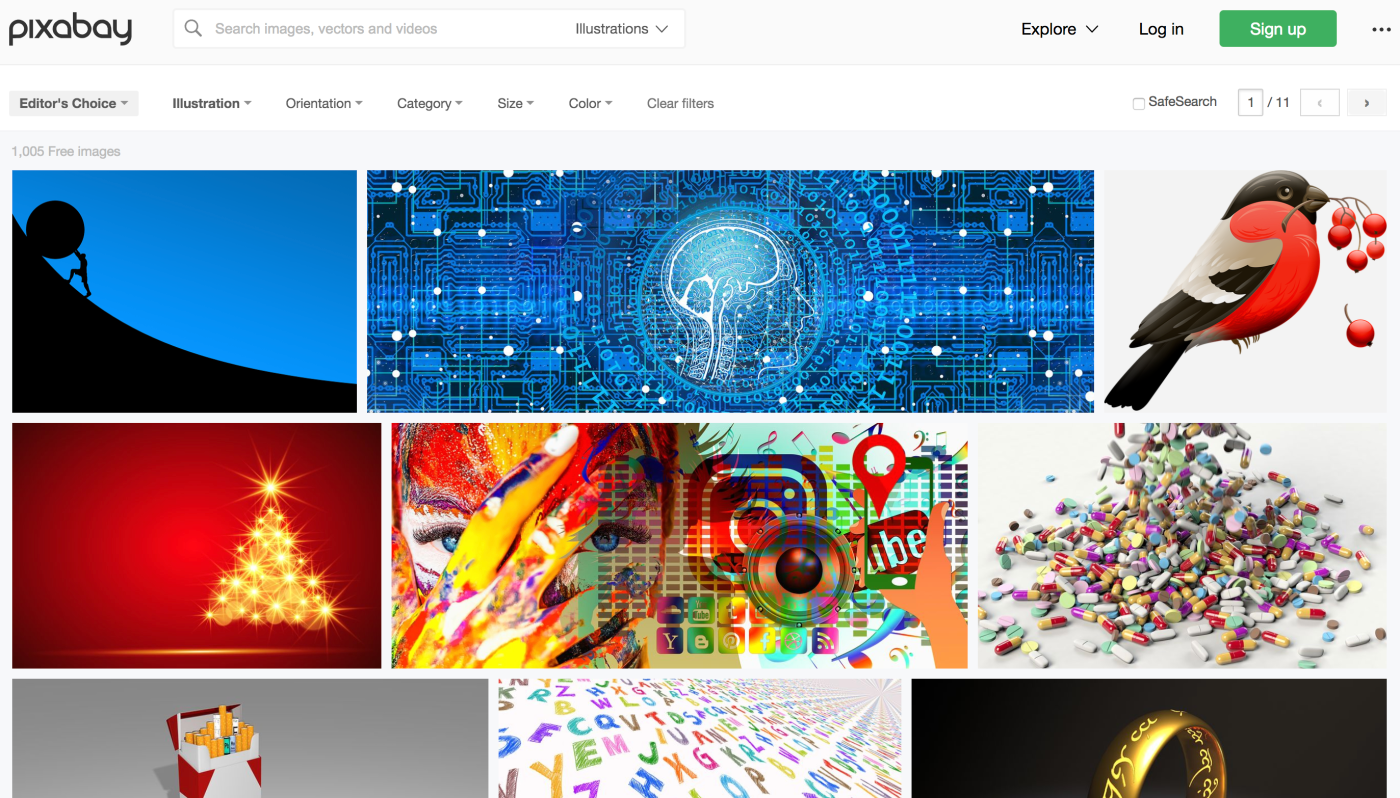
Pixabay hosts more than 2.6 million photos, illustrations, vector graphics, and videos—all of which are free to use. Click Images next to the search bar to look for images by type, or you can search more granularly by becoming familiar with Pixabay’s advanced search options. Pixabay lets you search by photographer, orientation (i.e., landscape or portrait), size, and even color. The site also features an Editor’s Choice curation section, which highlights the best images chosen by the Pixabay team. Click the Explore dropdown menu in the upper-right corner of the site to see their selections.
If you need a professional-looking illustration—i.e., a hand-drawn image or a computer-generated graphic—you should begin your search here. Royalty-free illustrations can be tricky to find on many free image sites, but Pixabay has loads of them. Just click Images, select Illustrations, enter in your search terms, and that’s that. You can also use Pixabay to search for vector graphics, videos, music, and even sound effects.
Best free stock photos site for quirky images you won’t see anywhere else
Gratisography (Web, Android)
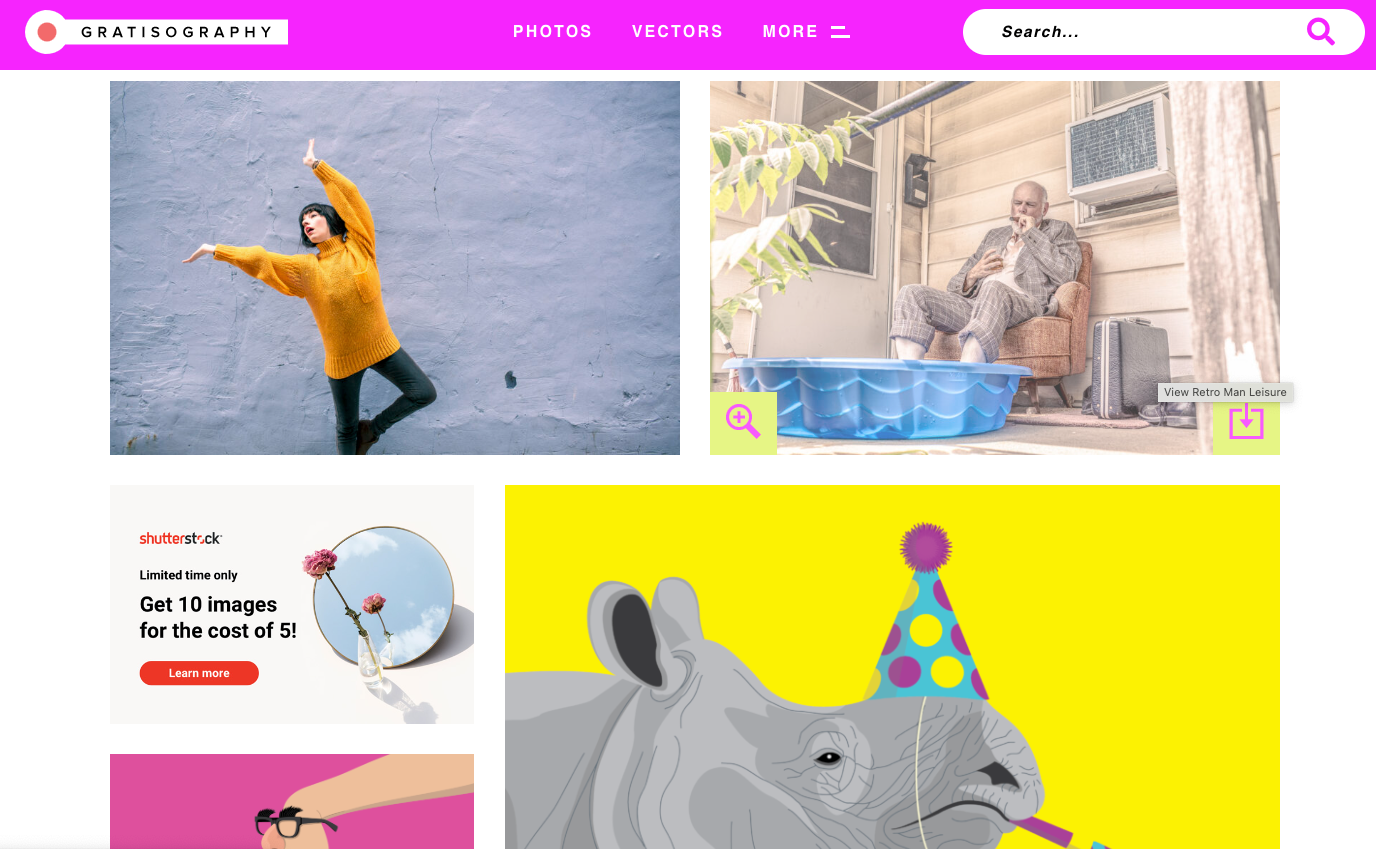
Gratisography doesn’t have thousands of pictures for you to browse through. What it does have is some of the quirkiest images you will find on the web—images you won’t be able to find anywhere else, like a young kid spray painting and an alarm clock that looks like it’s on the moon.
The site is pretty barebones—and its color scheme is distracting at best, with bright neon colors and cartoonish UI elements. Photos are organized into only nine different categories: Animals, Business, Fashion, Food, Nature, Objects, People, Urban, and Whimsical. And while the photo resolutions are high-quality, they only come in one size (and you have to download each photo to find out).
But if you’re looking for an odd image that will bring your content to life, Gratisography is definitely the place to start.
Best free stock photos site for adding simple enhancements and overlays
Canva (Web, macOS, Windows, iOS, Android)
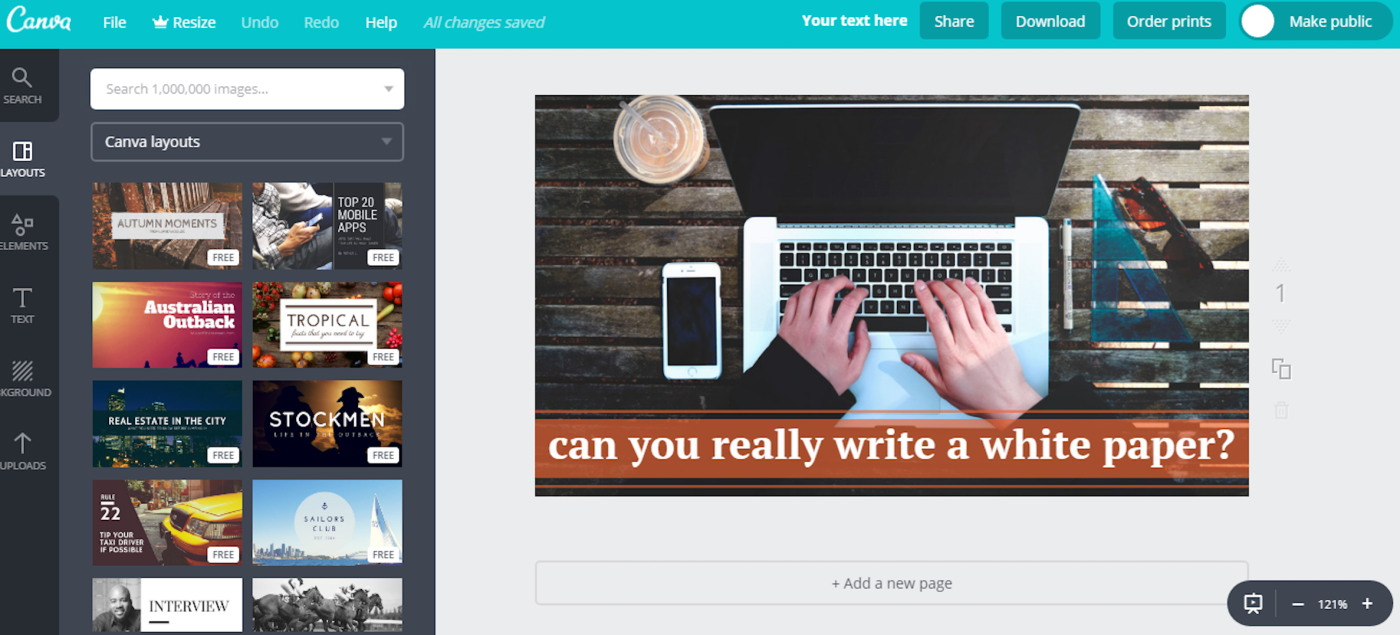
Canva is a web-based graphic design tool that makes modifying images easy. If you’re looking for stock photos for a graphic design project—like designing a social media banner or a flyer—Canva is a one-stop shop for your needs. Even with a free account, the platform offers a library of over 1.6 million free images you can use for any purpose.
If you’re planning on enhancing the images you find with simple text overlays or tweaking the transparency or vibrancy of photos on a regular basis, Canva will help you streamline the process. Find photos, and then use Canva’s built-in design tool to enhance them on the spot.
One helpful feature is that Canva automatically generates a color palette for any photo you choose. If you’re building a vision board or a design presentation, you can easily use the hex color codes to keep your project’s color scheme consistent.
Canva does come with a few downsides, though. As I was testing, I noticed that you can’t directly download a stock photo as you would from another stock photo site. Instead, you’ll have to click Use in a design. Canva takes you to the design dashboard with the stock photo on your digital canvas. While this is helpful if you intend to add text or graphics to the image, it’s an unnecessary complication if you plan to download a stock photo as-is.
Also, many of the best stock photo sites let you choose the size of your photo before downloading it. Canva only provides one size—though the photos are all in high resolution.
If you’re looking for more stock photo sites for graphic design, PikWizard and Kaboompics are both great Canva alternatives. PikWizard is linked to DesignWizard, a design tool similar to Canva. And Kaboompics focuses on color palettes; you can even download your chosen photo along with with the color scheme it uses, which is useful for putting together vision boards and presentations. Kaboompics also lets you choose a custom pixel width when downloading an image, which is a helpful feature.
Best free stock photos site for eCommerce businesses
Burst (Web, iOS, Android)
Burst is a free stock photo site powered by leading eCommerce platform Shopify. The platform offers thousands of free images you can use to strengthen your content, including a large selection of business-oriented photos (e.g., retail, eCommerce, money, and products). The site serves up 28 different categories, several of which are broken down into subcategories to make it even easier to find the images you need.
Browsing, searching, and downloading are standard fare, but as an added bonus, Burst and Shopify offer advice on things like how to turn your online business ideas into reality.
Best free stock photos site for vintage photos
New Old Stock (Web)
New Old Stock publishes vintage photos from the public archives. If you think old photos—like a group of men sitting outside a storefront in the late 1800s or a British dispatch rider in France—would match your brand, spend a few minutes scrolling through New Old Stock to see if anything catches your eye.
Unfortunately, the site doesn’t have as much variety as other stock photo sites—and not all of the photos are free for commercial use. The site creator advises commercial users to check with the originating institution’s rights statement through the provided link to the original Flickr posting of each photo.
The site’s search functionality also leaves much to be desired. And unlike most free image sites, New Old Stock doesn’t offer any way to filter photos. If you’re feeling lucky, though, click the magnifying glass in the upper-left corner of the site, type in a search phrase, and you may strike (vintage) gold.
Best free stock photos site for UX/UI designers
Reshot (Web)
Reshot is a relatively new resource for designers, whether they need stock photos, vector illustrations, or icons. The site’s collection is provided by the design team over at Envato Elements, a paid creative subscription service for templates, photos, music, and more. But Reshot provides free visual resources for designers on a budget.
Unlike many other stock photo sites, Reshot has a wide variety of vector illustrations and icons as well. The site boasts millions of images that are free for personal and commercial use. The website is minimalist in design, with a left-hand menu where you can choose to browse collections of icons, illustrations, or photos. Or if you know what you’re looking for, type your search terms into the search bar and narrow the results by media type and orientation.
If you find an illustration you like, you have the option to download a vector or PNG—while icons come in SVG code or SVG. And since you’ll likely want to make additions or changes to these images, Reshot makes it easy to download files straight into Figma.
One downside I noticed as I was testing is that while illustrations and icons have multiple download types, it appears that photos can only be downloaded as JPEGs—and only in one size. Those sizes are in high-quality resolution, but you can’t choose from a variety of sizes. But in general, if you’re looking for ideas or raw images for your wireframes or prototypes, Reshot is a great option.
Best free stock photos site for optimizing images for social media
123RF (Web, iOS, Android)
If you’re looking for free stock photos for Instagram or other social media sites, 123RF makes your search easy. The stock photo site not only provides a variety of free photos and vector illustrations, but it also lets you choose from a selection of download sizes, including Facebook cover, email header, Pinterest post, and even brochure cover.
These pre-selected sizes can save you hours of cumulative time spent cropping and resizing images for social media. You can even apply a filter, add text, and remove the image’s background directly from the site before downloading it.
As I was testing, I did notice that you can’t reposition an image after choosing a social media-optimized size. So if you choose an image whose focal point isn’t the center, you may run into issues if you pair it with a small or narrow aspect ratio.
Overall, the site is clean and easy to navigate. And if you’re willing to pay a few dollars per image, 123RF provides a wider variety of images as well as a variety of stock footage and audio for use in your next project.
Best free stock photos site for interacting with the photography community
Flickr (Web, iOS, Android)
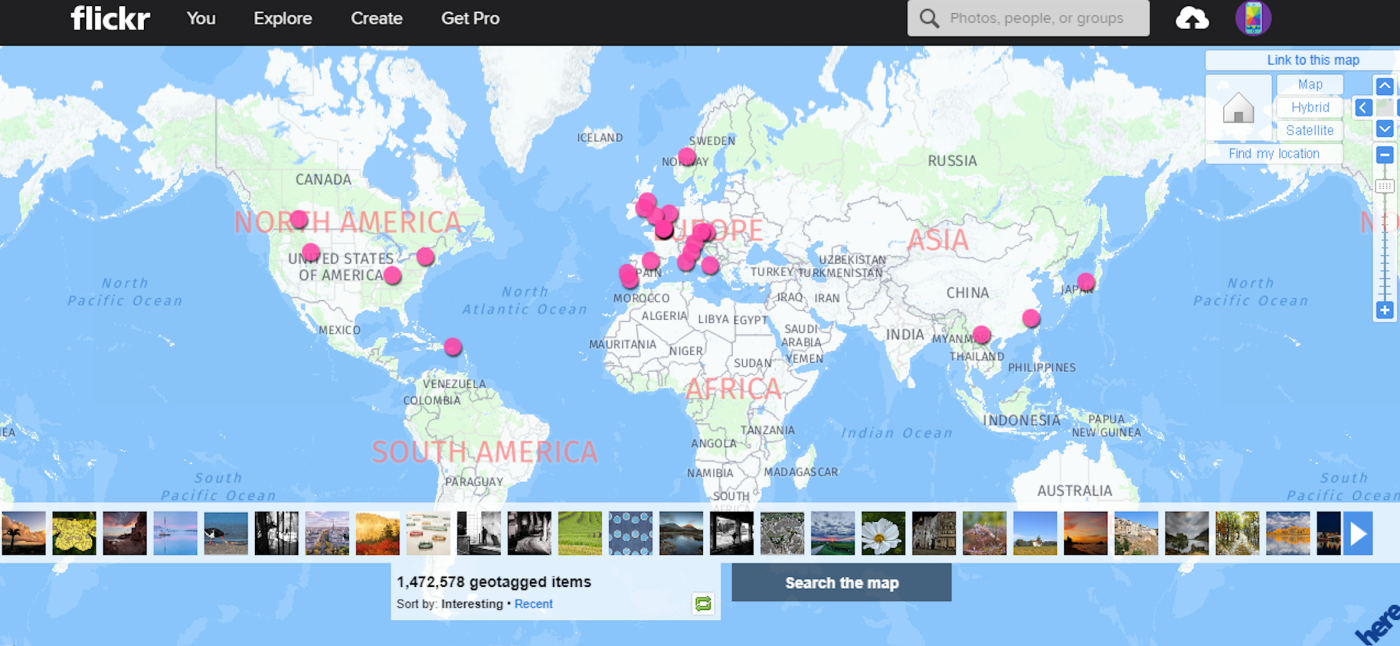
Flickr is a photo sharing social network. The site—which boasts more than five billion images—brings together professional and amateur photographers from around the world.
The thing I appreciate about Flickr is that it places artists front and center. When you navigate to Flickr’s homepage, you’ll immediately see a gallery of suggested people to follow. Click into any one of their profiles to see a “Photostream,” or a feed of their latest and most popular images. Flickr is a great way to discover talented photographers, learn more about the field, and refine your own artistic eye.
The photos on Flickr are known for containing rich metadata, including geolocation information, EXIF data, tags, and more. So if you want to find photos taken in France, select the World Map under the Explore dropdown, and click on one of the pink dots that pop up in that country. If you want to find images of golden retrievers, simply type the term into the search bar in the upper-right corner of the Flickr homepage, and thousands of results will come back. Plus, Flickr lets you search by trending photos and most recently added photos. You can even explore galleries and search specific photographers’ collections by clicking on their usernames.
And if you’re a budding photographer yourself, you can even click Camera Finder under the Explore dropdown to see the most popular cameras currently being used in the Flickr community.
Keep in mind that you can’t use every photo you find on Flickr for free—especially for commercial use. But it’s easy to figure out which ones are usable. Run a search for an image, and then click the Any license dropdown menu and select Commercial use allowed.
If you get sick of seeing ads as you browse Flickr, you can upgrade to an ad-free experience for $5.54/month. The premium subscription also comes with unlimited storage (free users get one terabyte of storage). And if you want to even more with your stock photos, connect Flickr to Zapier to do things like share new Flickr photos on social media or back up new Flickr photos to Google Drive.
Share new Flickr photos on Twitter, Facebook, and Pinterest

- +2

Facebook Pages, Flickr, Pinterest, Twitter
Facebook Pages + Flickr + Pinterest + 1 moreMore details
Back up new Flickr photos to Google Drive
Flickr, Google Drive
Flickr + Google DriveMore details
If you’re looking for more sites that prioritize the photography community, Pexels is a great Flickr alternative. Pexels offers hundreds of thousands of photos that are free for both commercial and personal use. The site has a leaderboard and a number of photography contests for contributors, which makes it a great site for finding photographers who are engaged with the platform and constantly uploading fresh content.
Other stock photo sites to consider
If you’re looking for something a little more unique (and you have the budget for it), you could try a paid option like Shutterstock, iStock by Getty, or Adobe Stock. These sites are all very well-established resources for paid—but relatively affordable—stock photos. You can subscribe to any of these sites for $29 per month for up to ten monthly image downloads.
There are also many niche stock photography sites out there (like Foodiesfeed, which specializes in food photography). So if you’re looking for a specific type of image, it’s worth seeing if there’s a niche site available. These sites might give you a wider range of options in the specific category you’re looking for.
If you’re publishing content on a regular basis, you’ll likely get the best results by using a combination of our recommended sites. Just be sure that you keep your branding consistent: using too many eclectic images can muddy your brand and make it hard to stand out from the crowd.
A note on copyrights
Why can’t you just scour the web for an image you like and publish it? Because creators own the rights to their images, and if you publish one of them without their approval, you may be guilty of copyright infringement. In a worst-case scenario, that could land you a $150,000 fine for each violation, and possibly even jail time. Of course, you’ll receive a cease-and-desist letter first, telling you to take the images down, but even still, you’ll waste time and effort removing them—in addition to the time and effort you wasted finding them in the first place.
But some creators are happy to share their images with others. Creative Commons offers a number of different licenses that creators can use to enable other people to leverage their work freely. Of course, it’s not all or nothing: some licenses allow for personal use, while others allow for commercial use. Some licenses require you to attribute images to creators, while others don’t. Some allow you to adapt or modify an image, while others require you to use it in its original form. When using an image licensed through Creative Commons, be sure to read the fine print and abide by the terms.
Source :
https://zapier.com/blog/best-free-stock-photos/



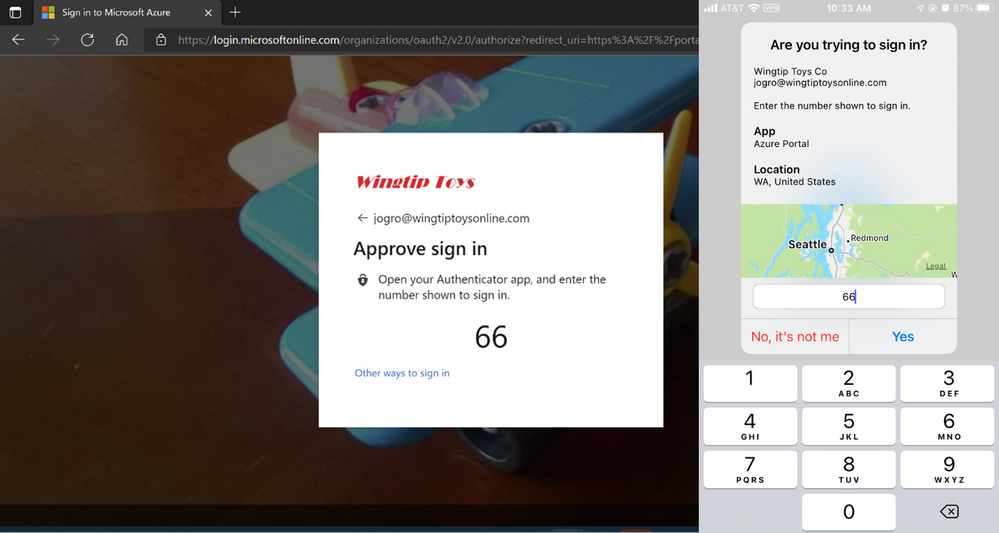 Passwordless phone sign in experience in Microsoft Authenticator for Azure AD accounts.
Passwordless phone sign in experience in Microsoft Authenticator for Azure AD accounts.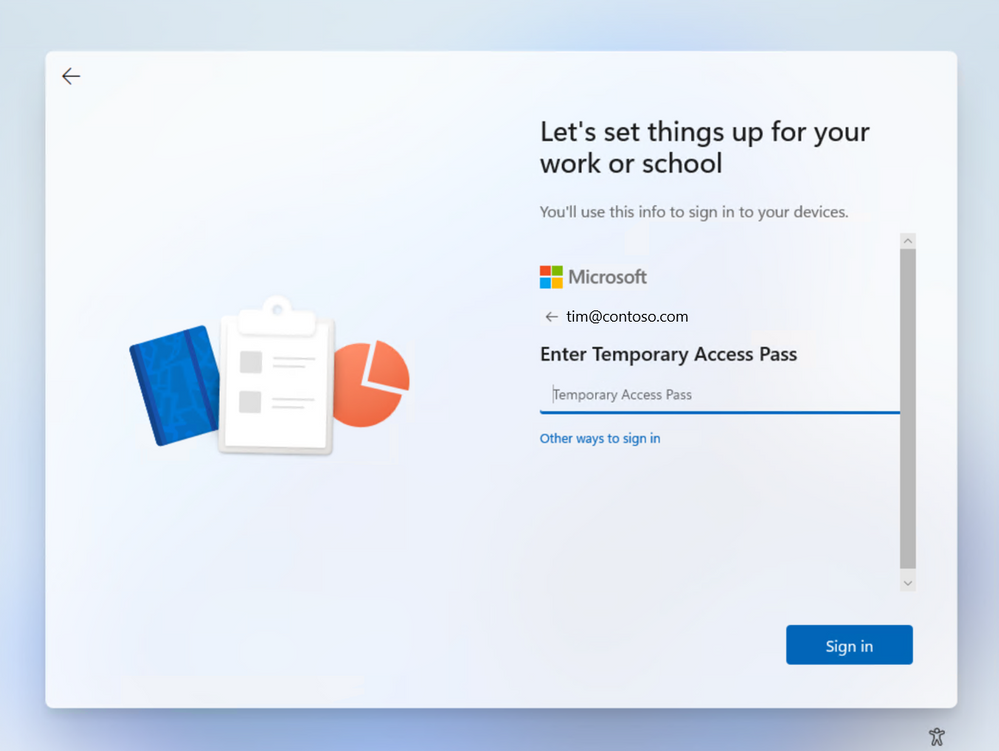 End user experience for Temporary Access Pass in Windows 11 onboarding.
End user experience for Temporary Access Pass in Windows 11 onboarding.








