On Windows 11, a cumulative update (or quality update) is a service patch that Microsoft rolls out proactively to fix bugs, enhance security, and improve system performance. Although updates download automatically through Windows Update, sometimes it may still be necessary to install a specific patch manually.
For instance, after a new installation of Windows 11 or if the computer hasn’t been connected to the internet for some time. If Windows Update isn’t working, it might be necessary to install an update manually to fix the problem. A specific driver needs an update, or you want to upgrade to a newer version of Windows.
Regardless of the reason, Windows 11 has at least four ways to update the system using the Windows Update settings, manual download, Command Prompt, and PowerShell.
Microsoft offers three main types of updates (quality, optional, and feature updates). “Quality updates” are available every month with security and non-security fixes, improvements, and features (occasionally). “Optional updates” are not critical but necessary, and they include drivers and product updates. Finally, “feature updates” are meant to upgrade the device to a newer version (for example, Windows 11 22H2).
In this guide, you will learn six ways to install updates on Windows 11.
- Install updates on Windows 11 with Windows Update
- Install updates on Windows 11 with Microsoft Update Catalog
- Install updates on Windows 11 with Command Prompt
- Install updates on Windows 11 with PowerShell
- Install optional updates on Windows 11
- Install feature updates on Windows 11
Install updates on Windows 11 with Windows Update
To install Windows 11 updates manually with Windows Update, use these steps:
- Open Settings on Windows 11.
- Click on Windows Update.
- Click the Check for updates button.

- (Optional) Click the Download and install option to apply a preview of an upcoming update of Windows 11.Quick note: Optional updates usually include non-security changes that Microsoft plans to release in the next Patch Tuesday rollout.
- Click the Restart now button.
Once you complete the steps, if an update is available, it will download and install automatically on Windows 11.
Install updates on Windows 11 with Microsoft Update Catalog
To download and install an update manually on Windows 11, use these steps:
- Open Microsoft Update Catalog website.
- Search for the knowledge base number of the update – for example, KB5015814.Quick tip: If you do not know the latest update reference number, you can check the update history tracker.
- Click the Download button for the update to install on Windows 11.
 Quick note: The page usually lists two versions, including ARM64 and x64. Unless you have an ARM-based device, you need to download the x64 version of the cumulative update.
Quick note: The page usually lists two versions, including ARM64 and x64. Unless you have an ARM-based device, you need to download the x64 version of the cumulative update. - Click the link to download the .msu package to your computer.
- Click the Close button.
- Double-click the .msu file to launch the installer.
- Click the Yes button to install the update on Windows 11.
- Click the Restart now button.
After you complete the steps, the cumulative update will apply to Windows 11.
Install updates on Windows 11 with Command Prompt
Windows 11 doesn’t have a Command Prompt tool to check and download updates. However, you can use commands to install update packages manually.
To install Windows 11 updates with Command Prompt, use these steps:
- Open Microsoft Update Catalog website.
- Search for the knowledge base number of the update – for example, KB5015814.
- Click the Download button for the cumulative update you want to install.

- Click the link to download the .msu package.
- Click the Close button.
- Open Start.
- Search for Command Prompt, right-click the top result, and select the Run as administrator option.
- Type the following command to install a new update on Windows 11 and press Enter:wusa c:\PATH\TO\UPDATE.msu /quiet /norestartIn the command, update the path with the location and name of the .msu update package. This example installs the KB5015814 update:wusa c:\Users\USERACCOUNT\Downloads\windows10.0-kb5015814-x64.msu /quiet /norestart

- Type the following command to confirm the update was installed correctly and press Enter:wmic qfe list brief /format:table
- Type the following command to restart the device and press Enter:shutdown /r /t 00
After you complete the steps, the quality update will install quietly, and the computer will restart to finish applying the changes on Windows 11.
Install updates on Windows 11 with PowerShell
Alternatively, you can also install a PowerShell module to download and install updates on Windows 11.
To install Windows 11 updates with PowerShell, use these steps:
- Open Start.
- Search for PowerShell, right-click the top result, and select the Run as administrator option.
- Type the following command to install the PowerShell module to update Windows 11 and press Enter:Install-Module PSWindowsUpdate

- Type Y to accept and press Enter.
- Type A to accept and install the module and press Enter.
- Type the following command to allow scripts to run on PowerShell and press Enter:Set-ExecutionPolicy RemoteSigned
- Type the following command to import the installed module and press Enter:Import-Module PSWindowsUpdate

- Type the following command to check for Windows 11 updates with PowerShell and press Enter:Get-WindowsUpdate
- Type the following command to select, download, and install a specific update and press Enter:Install-WindowsUpdate -KBArticleID KBNUMBERIn the command, make sure to replace KBNUMBER with the update number you want to install. This example downloads and applies the KB5015814 update for Microsoft Defender:Install-WindowsUpdate -KBArticleID KB5015814

- Type A to confirm the installation and press Enter.
- (Optional) Type the following command to download and install all available updates and press Enter:Install-WindowsUpdateQuick note: When using this command, you will be applying system updates as well as optional updates that may include driver updates.
- Type A to confirm the installation and press Enter.
- Type Y to confirm the restart and press Enter (if applicable).
- (Optional) Type the following command to view a list of previously installed updates and press Enter:Get-WUHistory
Once you complete the steps, the Windows 11 updates will download and install on your device.
Install optional updates on Windows 11
On Windows 11, optional updates are not critical, but they may be necessary for other functionalities. Typically, these updates are available for Microsoft and other products, feature updates, and third-party drivers (such as printers, cameras, network adapters, graphics cards, and Bluetooth peripherals).
To install optional updates on Windows 11, use these steps:
- Open Settings.
- Click on Windows Update.
- Click the Advanced options tab.
- Under the “Additional options” section, click the Optional updates setting.

- Click the category to see the optional updates – for example, Driver updates.
- Check the optional updates to install on Windows 11.

- Click the Download and install button.
After you complete the steps, Windows Update will install the packages on your computer.
Install feature updates on Windows 11
Feature updates refer to new versions of Windows 11 that bring new changes and features. These updates are optional, and you must install them manually unless the current release of Windows 11 is reaching the end of service, in which case the feature update will install automatically.
To install a feature update on Windows 11, use these steps:
- Open Settings.
- Click on Windows Update.
- Click on Check for updates button (if applicable).
- Click the Download and Install now button.

- Click the Restart now button.
In addition to Windows Update, you can also install feature updates using the Installation Assistant or the official ISO file to perform an in-place upgrade.
Source :
https://pureinfotech.com/install-updates-manually-windows-11/
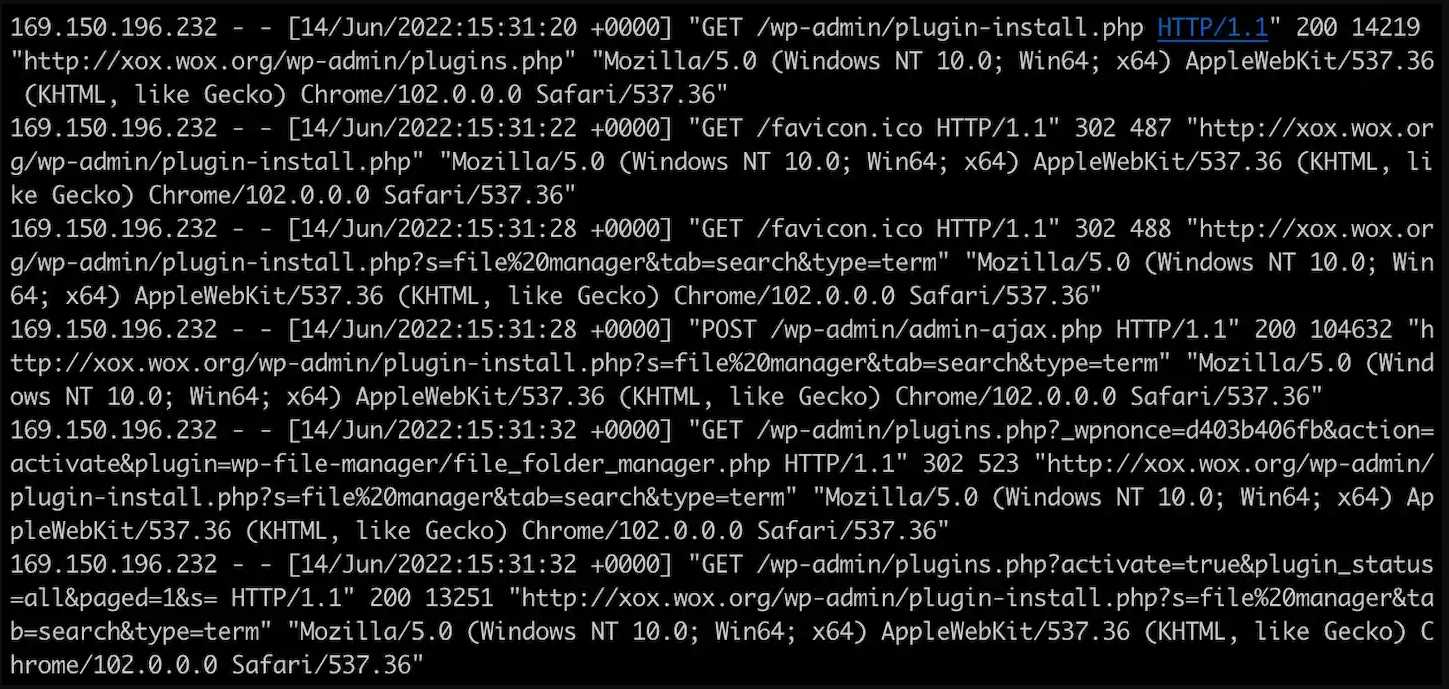
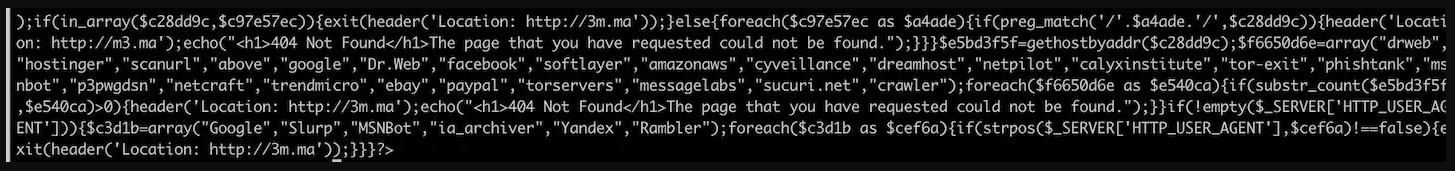
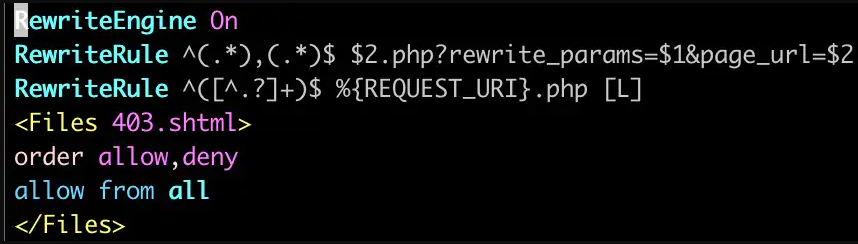
.png)
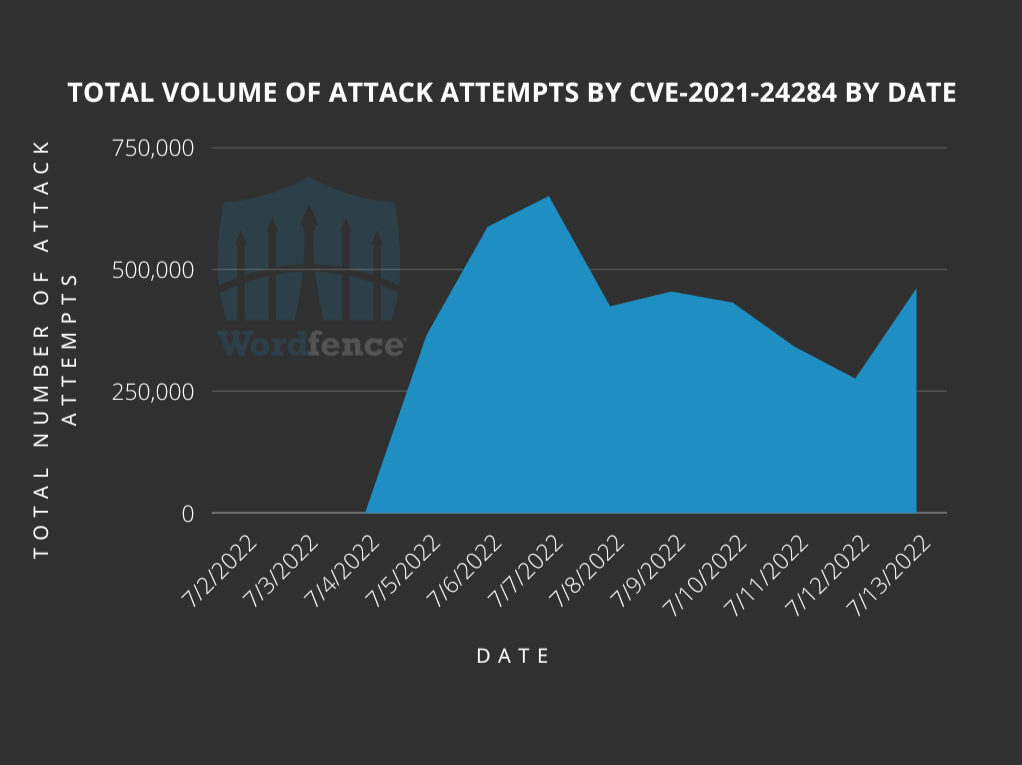


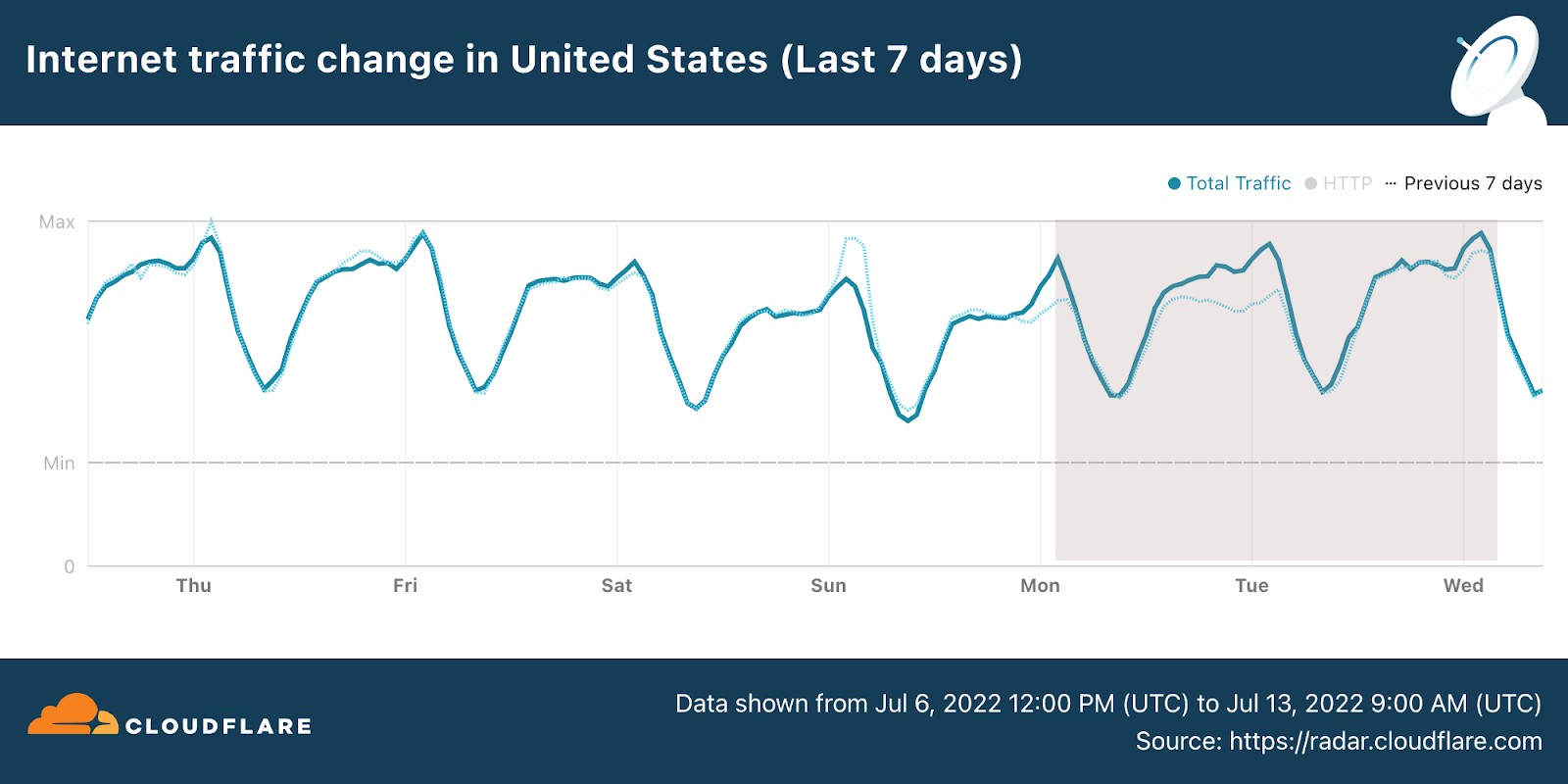

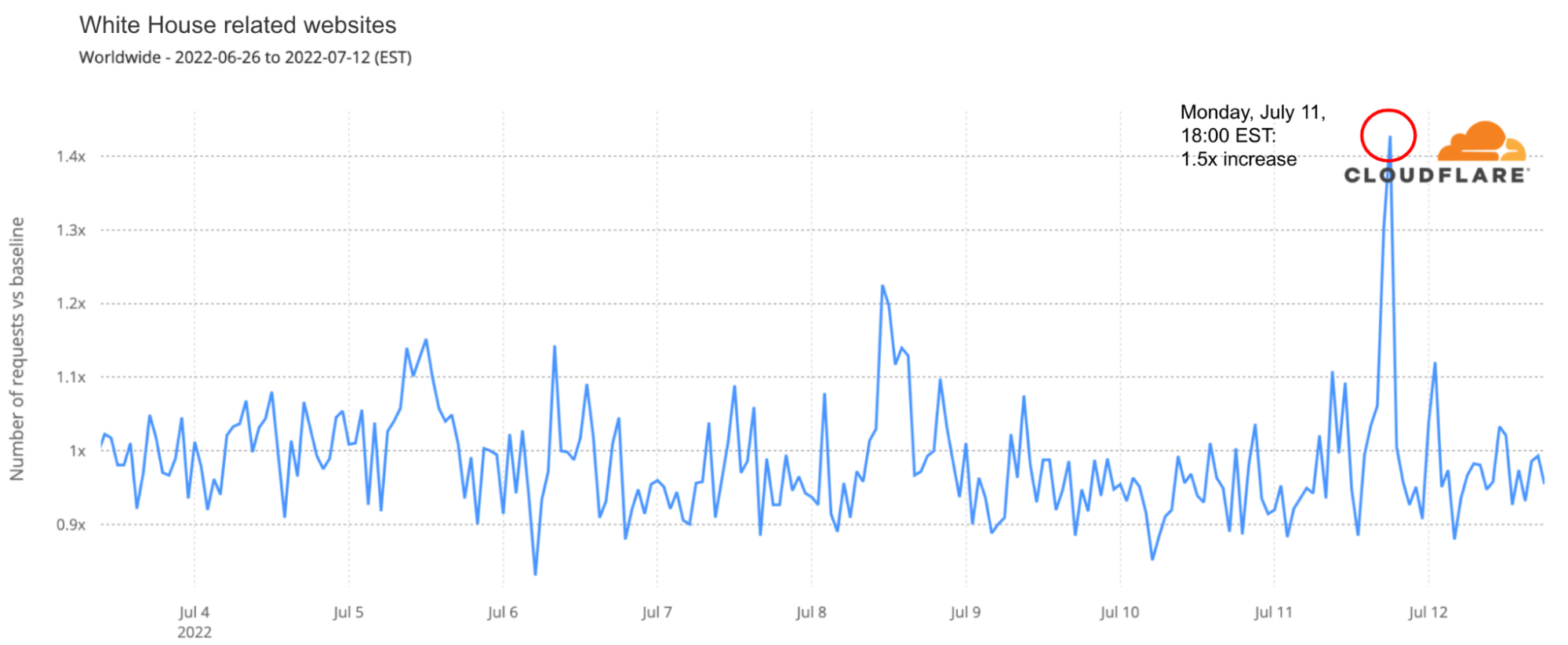

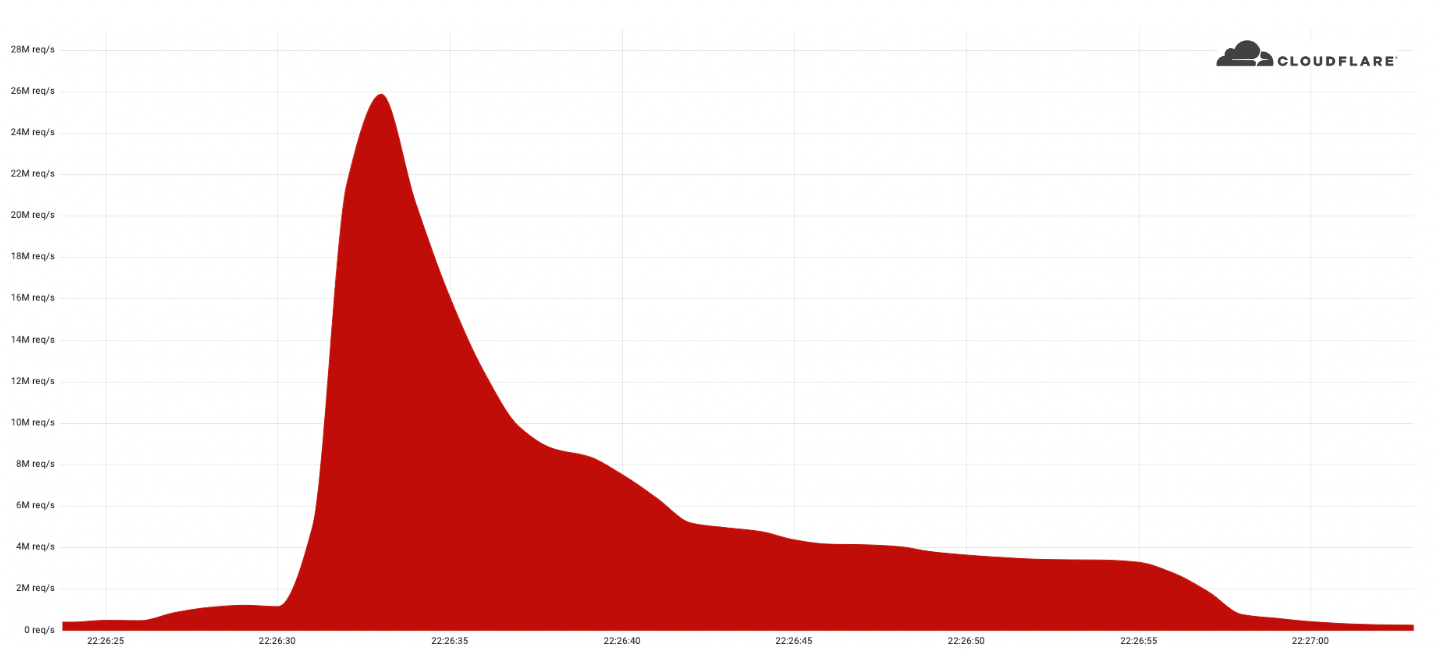
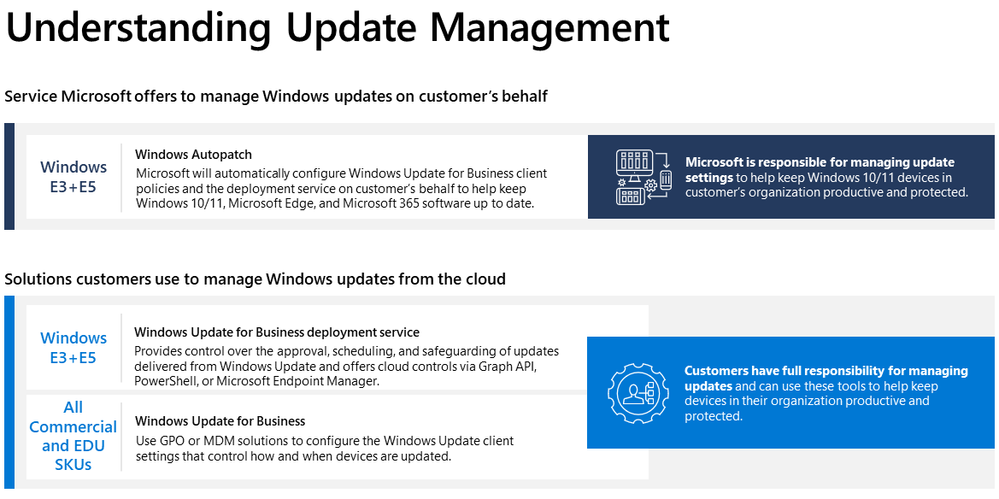 Windows Autopatch is a service that uses the Windows Update for Business solutions on your behalf.
Windows Autopatch is a service that uses the Windows Update for Business solutions on your behalf.