The Recovery Mode User Interface (UI) is a special interface for UniFi OS Consoles (UDMP, UNVR, etc.) and gateways used to recover from various failure modes (indicated on the LCM screen of that device). From the Recovery Mode, you can perform the following actions:
- Reset to Factory Defaults: Completely reset the device. Note this will also wipe out any stored backup files.
- Reboot: Restart the device and re-load the existing configuration.
- Power-off: Initiate a software shutdown on the device, after which you can safely remove the power cable.
- Check Filesystems: Check the integrity of the file system.
- Firmware Update: Upload a previously downloaded firmware image (.bin) file in order to upgrade the firmware.
You should only resort to using recovery mode if you are prompted by the LCM screen found on your device.
Performing a Device Recovery
- Download the most recent firmware for your device. You can find information on our latest releases here.
- Completely power-off the UniFi device and unplug it from its power source.
- Press and hold the reset button and then power on the device by connecting it to the power source once again.
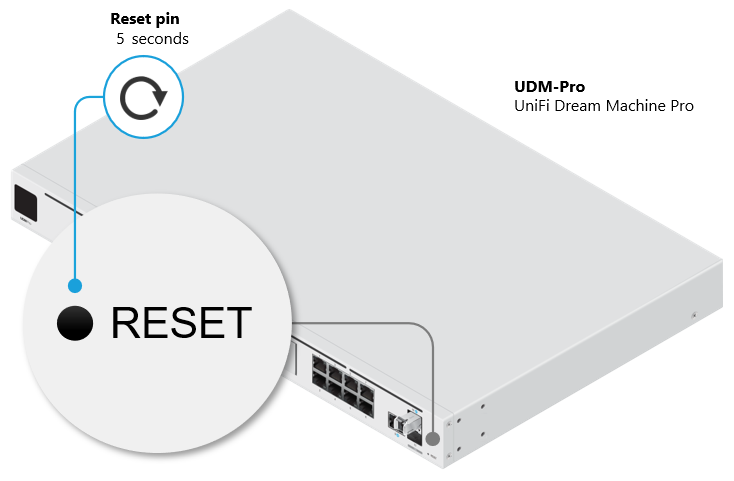
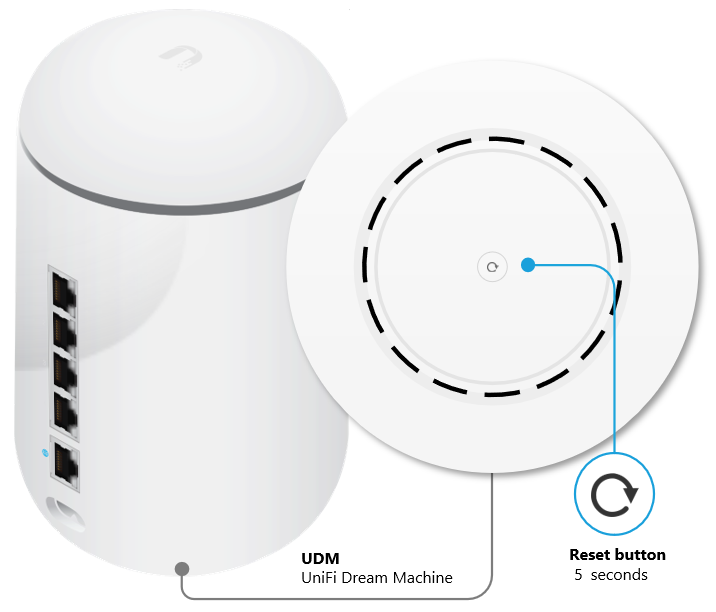
- Keep the reset button pressed for about 5 seconds. After some time the display (in supported models) will indicate that the gateway is in Recovery Mode.
- Connect an Ethernet cable from your computer to the first LAN port (port 1) on the UniFi gateway.
Note: Port 1 is always the first one. Either the top port, or the top left corner one, depending on the layout of your device’s ports. - Configure a static IP address on your computer in the 192.168.1.0/24 range (for example 192.168.1.11). Windows ClientmacOS clientNote: If a wireless adapter is enabled and connected to another network it could conflict with the connection to the UniFi device. Disable the wireless adapter if necessary.
- Open a compatible web browser navigate to http://192.168.1.30 to access the Recovery Mode UI.
Note: The Recovery Mode UI is accessible via HTTP only and not HTTPS. It is possible that your browser will automatically try to redirect your session to HTTPS. Make sure to navigate to the http://192.168.1.30 address and use a different browser if necessary. - Select Firmware Update > Choose and browse your computer for the previously download firmware (.bin) image file.
- Wait for the upgrade process to complete and reboot the device afterwards.
Source :
https://help.ui.com/hc/en-us/articles/360043360253-UniFi-Console-and-Gateway-Recovery-Mode
 We strongly recommend staying with the stable release, but for those users who wish to do otherwise, click here to expand and see possible suite names, as well as code names in the table within.
We strongly recommend staying with the stable release, but for those users who wish to do otherwise, click here to expand and see possible suite names, as well as code names in the table within.


