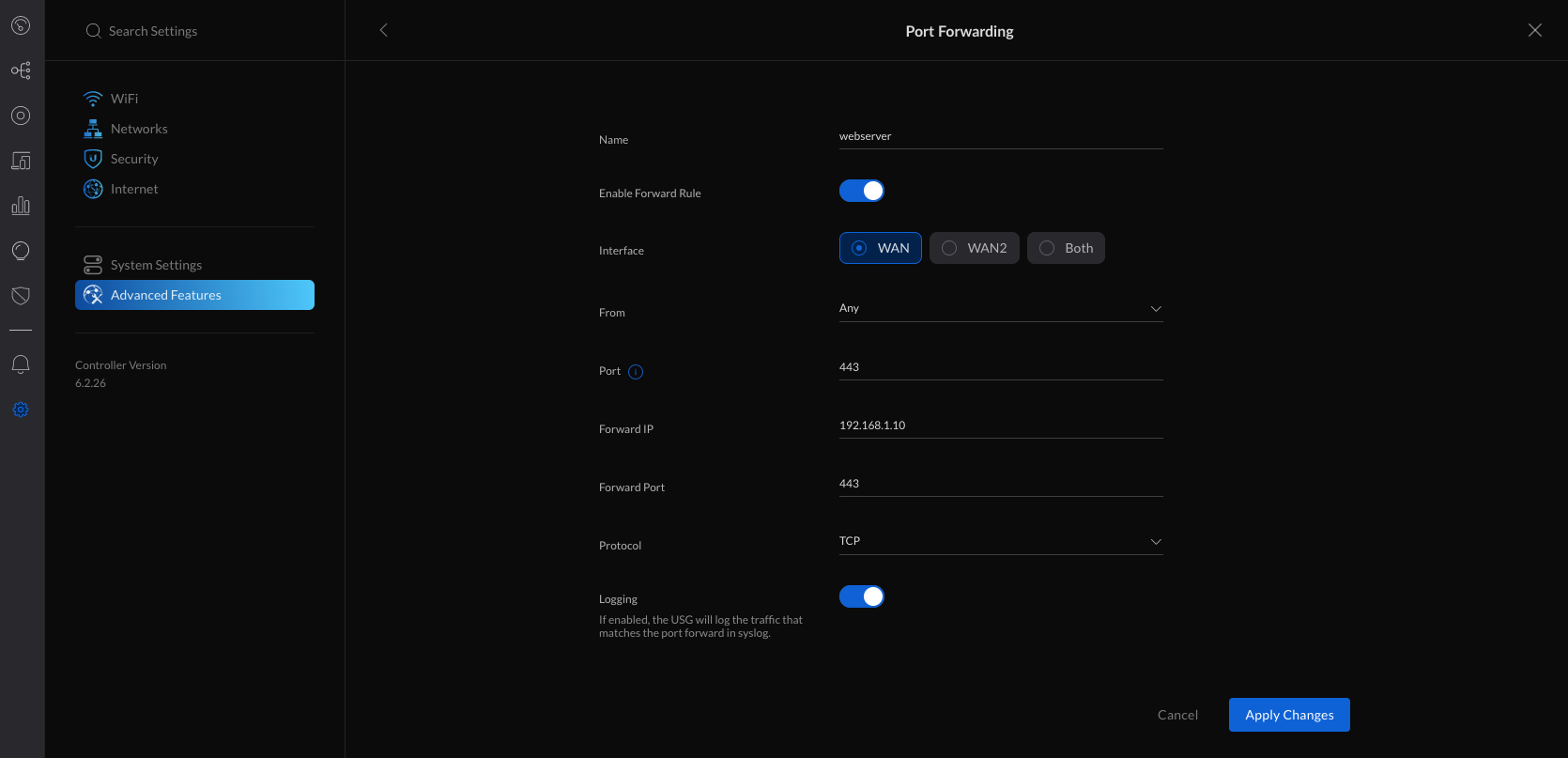
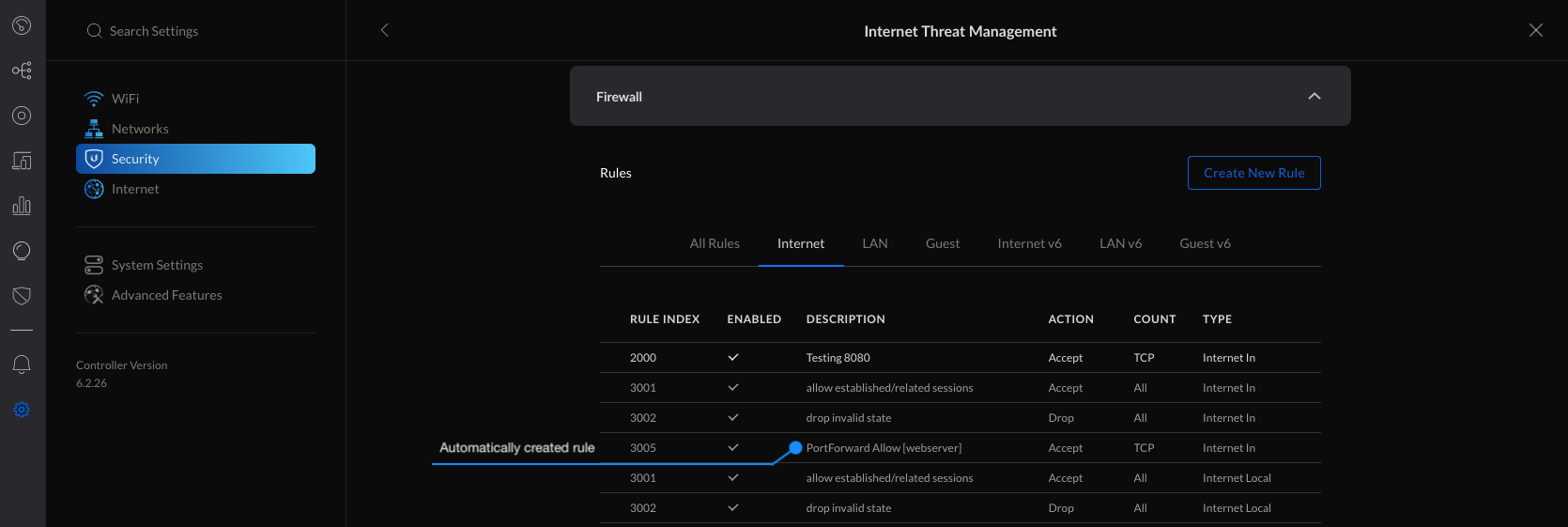
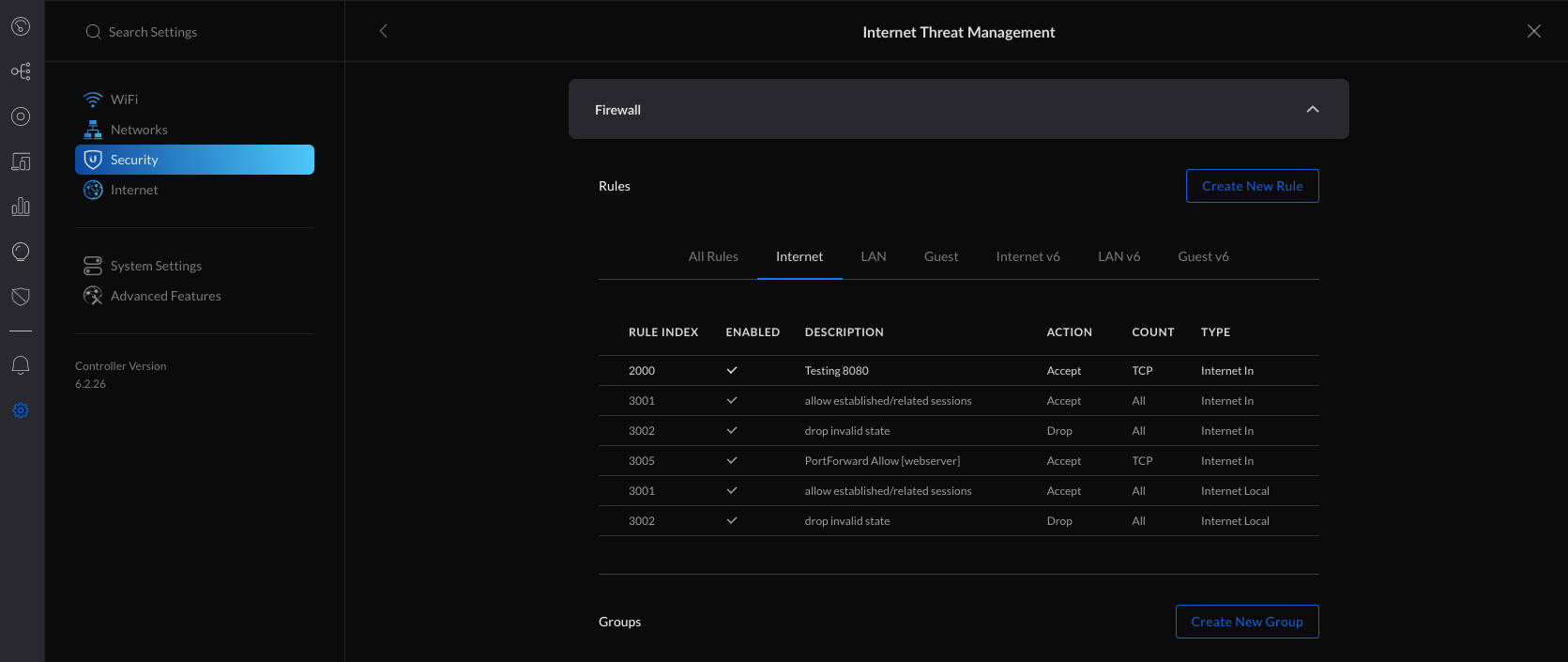
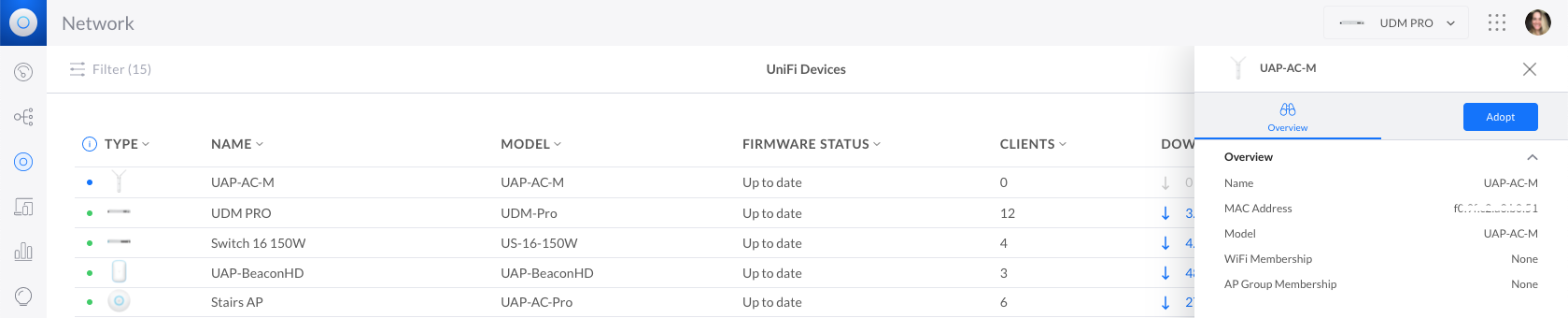
You can wirelessly adopt access points to your UniFi Network. This allows you to extend your coverage without adding cabling in hard-to-reach areas. When within range of your already-adopted access points, simply connect a new access point to power and it will appear as ready for adoption in the Network application.
- General troubleshooting
- Wireless uplink requirements
- Modifying existing wireless uplink connections
- Frequently Asked Questions
General troubleshooting
Wireless UAP does not appear for adoption
1. Verify that the UAP is powering properly and is ready for adoption (steady white LED).
2. Connect it via Ethernet cable to your network and wait for it to appear for adoption. If it still won’t appear while connected, please see our general adoption troubleshooting steps.
3. Update to the current firmware version if an upgrade is available.
4. Once the UAP is adopted and running the newest version available, disconnect it from the wired LAN, and wait a few minutes while it connects wirelessly. After that, you may disconnect it from power to move it to its final position. Once it powers up again, the UniFi Network application will recognize it and start broadcasting the network’s WiFi through your wireless UAP.
The UAP is adopted but it will not work when moved to wireless networks
1. Verify that the UAP is receiving enough power from the PoE injector. The LED must be a steady blue. Take a look at the UAP’s datasheet to verify power requirements.
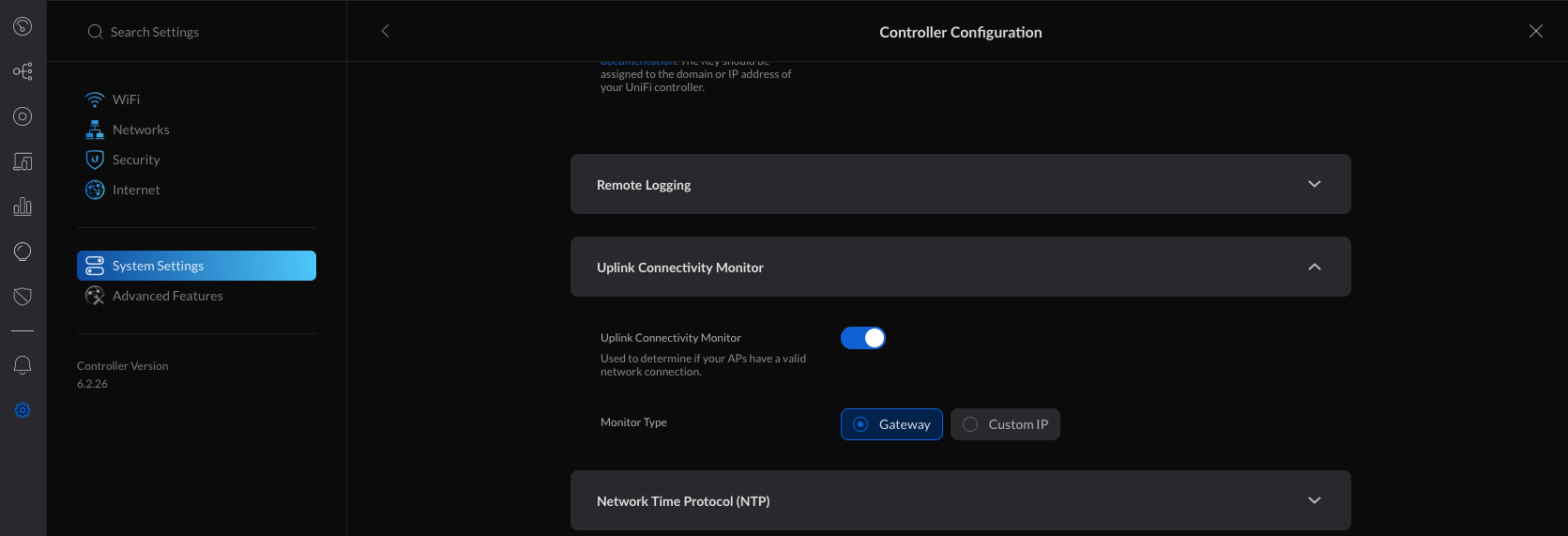
2. Verify that the Uplink Connectivity Monitor is enabled within Settings > System Settings > Controller Configuration > Uplink Connectivity Monitor.
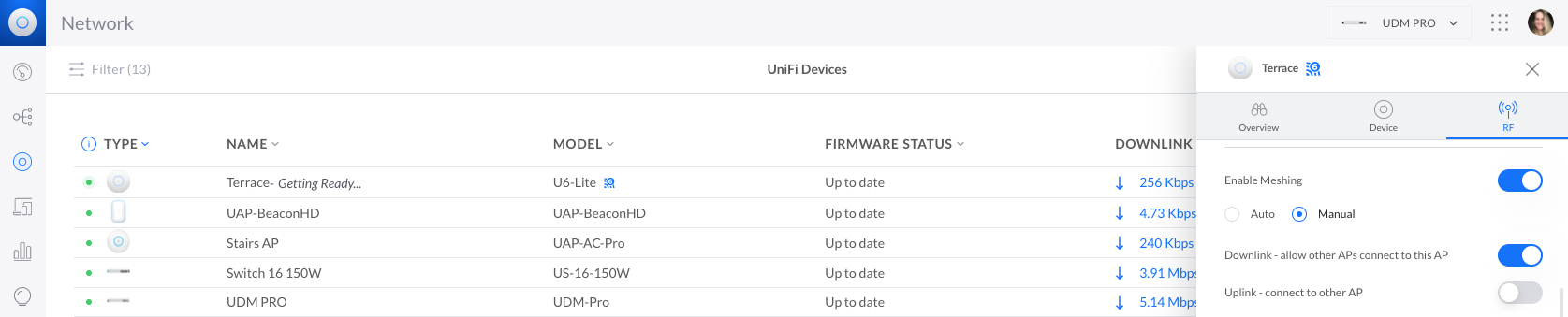
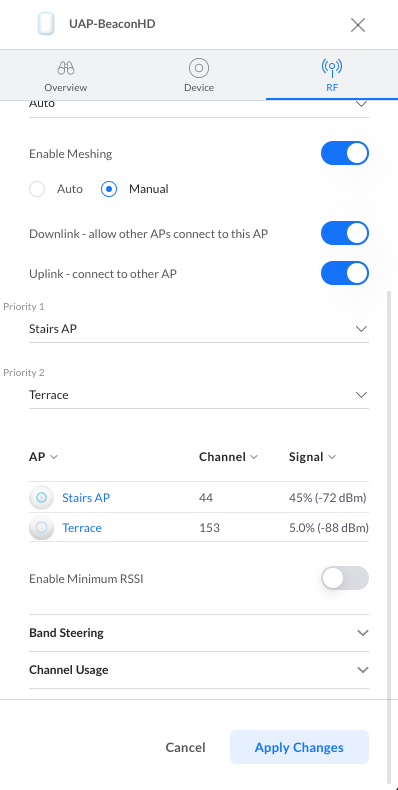
3. Verify that there is at least one wired UAP to act as an uplink and that Enable Meshing is turned on within the UAP’s properties panel > RF > Enable Meshing. And that the meshing configuration is set to Auto; or if set to Manual, that Downlink is enabled.
Wireless uplink requirements
- At least one wired access point to serve as the uplink UAP
- A power source (i.e PoE injector) for the wireless UAP (downlink UAP)
- (Recommended) Newest firmware and Network application versions.
Note: The wireless adoption process takes longer than the wired one; expect to wait a little longer for access point detection and for the adoption process to complete.
Modifying existing wireless uplink connections
You can design the topology to your liking by configuring how the wirelessly connected UAPs are linked. To change a UAP’s uplink:
- Select the UAP from the UniFi Devices section to open its properties panel.
- Go to the RF tab and select Manual under the Enable Meshing toggle. If the Enable Meshing option is not turned on, do so now to expose the wireless uplink settings.
- Select which UAP your wireless UAP will connect to (uplink).
Additionally, you can stipulate the uplink priority to define to which uplink your UAP will connect to if there is service degradation or if its current uplink goes offline. Use the Priority dropdown menus to select from the available uplinks.
Frequently Asked Questions
Can a wireless UAP be the uplink to another wireless UAP?
Yes. This is known as a multi-hop wireless uplink and is supported by UniFi, as long as there is one wired access point to provide the first “hop”. Keep in mind that each wireless uplink will suffer service degradation, so this should only be done when necessary.
Can I connect older UAPs wirelessly?
Yes, you just need to make sure to configure them correctly. Some older UAPs only broadcast on a single band (2.4GHz) and will not work the same as newer models. The following older generation UAPs do support wireless uplink on the band they operate on and do not support multi-hop: UAP, UAP-LR, UAP-PRO, UAP-Outdoor, UAP-Outdoor+, UAP-Outdoor5, UAP-IW.
UAP-AC and UAP-AC-Outdoor do not support wireless uplink or multi-hop.
If you have a UAP that does support wireless uplinking and it is still not working, make sure to take the following into account:
| Dual band uplink UAP to dual band downlink UAP: will uplink on 5GHz. | |
| Dual band uplink UAP to single band downlink UAP: will uplink on the supported frequency of the single band model. | |
| Single band uplink UAP to single band downlink UAP: will uplink, as long as the same band is supported on both sides of the link. | |
| Single band (2.4GHz only models) uplink UAP to dual band downlink AP will not be able to uplink. |
If you have several wired UAPs, these should have assigned channels that are different and do not overlap with other UAP channels to minimize interference.
- If using all dual band UAPs
- Set the wired UAP (uplink UAP) to static on 5GHz and to a static on 2.4GHz (1, 6 or 11 making sure it’s not a band also set for any of the other UAPs). Leave the wireless UAP (downlink UAP) set to Auto on the 5GHz radio and set a static channel on 2.4GHz not shared by others.
- If using all single band UAPs
- Set the wired UAP (uplink UAP) to a static channel on 2.4GHz. Leave the wireless UAP (downlink UAP) set to Auto on 2.4GHz.
- If using a dual band UAP as the uplink and single band UAP as the downlink
- Set the wired UAP (uplink) to a static channel on 2.4GHz. Leave the wireless UAP (downlink) set to Auto.
Source :
https://help.ui.com/hc/en-us/articles/115002262328-UniFi-Network-Troubleshooting-Wireless-Uplinks
- Set the wired UAP (uplink) to a static channel on 2.4GHz. Leave the wireless UAP (downlink) set to Auto.