What is the first thing you do when you need new marketing ideas? What about when you decide it’s time to find a new accounting software? Or even when you notice a flat tire in the car?
My guess is you turn to Google.
Impact Plus reported that 61% of marketers named SEO as a top marketing priority in 2021. And so, it’s a cold, harsh truth that without at least some presence on Google, your business faces a digital uphill battle. In this guide, you’ll discover a strategy to build your online presence — Search Engine Optimization (SEO). You’ll learn what SEO is, how it works, and what you must do to position your site in search engine results.
→ Download Now: SEO Starter Pack [Free Kit]
But before we begin, I want to reassure you of something.
So many resources make SEO complex. They scare readers with technical jargon, advanced elements, and rarely explain anything beyond theory.
I promise you, this guide isn’t like that.
I’m going to break SEO into its most basic parts and show you how to use all its elements to construct a successful SEO strategy. (And to stay up-to-date on SEO strategy and trends, check out HubSpot’s Skill Up podcast.)
Keep on reading to understand SEO, or jump ahead to the section that interests you most.
- What is SEO?
- How Google Ranks Content
- How to Build an SEO Strategy
- How to Measure SEO
- Local and Black Hat SEO
- SEO Resources
What is SEO?
SEO stands for search engine optimization. The goal of SEO is to expand a company’s visibility in organic search results. As a result, these efforts drive more visitors to the company’s website, increasing their chances for more conversions which leads to more customers and more revenue.
When asked to explain what SEO is, I often choose to call it a strategy to ensure that when someone Googles your product or service category, they find your website.
But this simplifies the discipline a bit.
There are a ton of ways to improve the SEO of your site pages. Search engines look for elements including title tags, keywords, image tags, internal link structure, and inbound links (also known as backlinks). Search engines also look at site structure and design, visitor behavior, and other external, off-site factors to determine how highly ranked your site should be in their SERPs.
With all of these factors taken into account, SEO primarily drives two things — rankings and visibility.
How Does SEO Work?
SEO works by optimizing a website’s content, conducting keyword research, and earning inbound links to increase that content’s ranking and the website’s visibility. While you can generally see results take effect on the SERP once the webpage has been crawled and indexed by a search engine, SEO efforts can take months to fully materialize.
Rankings
This is what search engines use to determine where to place a particular web page in the SERP. Rankings start at position number zero through the final number of search engine results for the query, and a web page can rank for one position at a time. As time passes, a web page’s ranking might change due to age, competition in the SERP, or algorithm changes by the search engine itself.
Visibility
This term describes how prominent a particular domain is in the search engine results. Lower search visibility occurs when a domain isn’t visible for many relevant search queries whereas with higher search visibility, the opposite is true.
Both are responsible for delivering the main SEO objectives – traffic and domain authority.
What’s the importance of SEO?
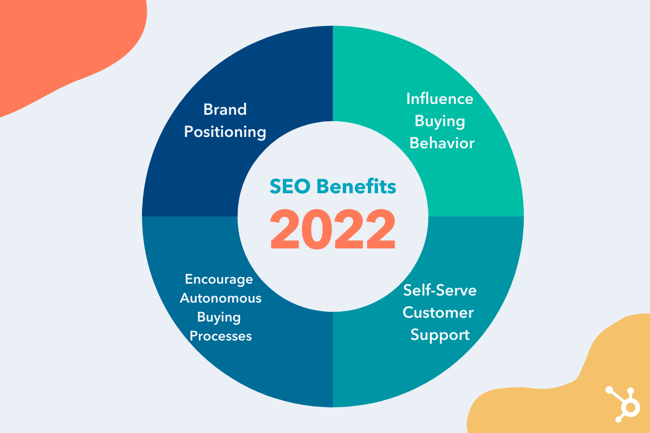
There is one more important reason why you should be using SEO: The strategy virtually helps you position your brand throughout the entire buying journey.
In turn, SEO can ensure that your marketing strategies match the new buying behavior.
Because, as Google admitted, customer behavior has changed for good.
As of June 2021, 92% of internet searches happen on a Google property.
What’s more, they prefer going through the majority of the buying process on their own.
For example, Ststista found that 60% of people research a brand online before making a purchase. What’s more, this process has never been more complicated.
Finally, DemandGen’s 2022 B2B Buyer’s Survey found that 67% of B2B buyers start the buying process with a broad web search.
But how do they use search engines during the process?
Early in the process, they use Google to find information about their problem. Some also inquire about potential solutions.
Then, they evaluate available alternatives based on reviews or social media hype before inquiring with a company. But this happens after they’ve exhausted all information sources.
And so, the only chance for customers to notice and consider you is by showing up in their search results.
Featured Resource
How does Google know how to rank a page?
Search engines have a single goal only. They aim to provide users with the most relevant answers or information.
Every time you use them, their algorithms choose pages that are the most relevant to your query. And then, rank them, displaying the most authoritative or popular ones first.
To deliver the right information to users, search engines analyze two factors:
- Relevancy between the search query and the content on a page. Search engines assess it by various factors like topic or keywords.
- Authority, which is measured by a website’s popularity on the Internet. Google assumes that the more popular a page or resource is, the more valuable its content is to readers.
And to analyze all this information they use complex equations called search algorithms.
Search engines keep their algorithms secret. But over time, SEOs have identified some of the factors they consider when ranking a page. We refer to them as ranking factors, and they are the focus of an SEO strategy.
When determining relevance and authority, following the E-A-T framework can help tremendously. E-A-T in SEO stands for “expertise”, authoritativeness”, and “trustworthiness”. And although these are not direct ranking factors, they can improve your SEO content which can impact direct ranking factors.
As you’ll shortly see, adding more content, optimizing image filenames, or improving internal links can affect your rankings and search visibility. And that’s because each of those actions improves a ranking factor.
What is SEO strategy?
An SEO marketing strategy is a comprehensive plan to get more visitors to your website through search engines. Successful SEO includes on-page strategies, which use intent-based keywords; and off-page strategies, which earn inbound links from other websites.
What is SEO strategy?
An SEO marketing strategy is a comprehensive plan to get more visitors to your website through search engines. Successful SEO includes on-page strategies, which use intent-based keywords; and off-page strategies, which earn inbound links from other websites.
Three Core Components of a Strong SEO Strategy
To optimize a site, you need to improve ranking factors in three areas — technical website setup, content, and links. So, let’s go through them in turn.
1. Technical Setup
For your website to rank, three things must happen:
First, a search engine needs to find your pages on the web.
Then, it must scan them to understand their topics and identify their keywords.
And finally, it needs to add them to its index — a database of all the content it has found on the web. This way, its algorithm can consider displaying your website for relevant queries.
Seems simple, doesn’t it? Certainly, nothing to worry about. After all, since you can visit your site without any problem, so should Google, right?
Unfortunately, there is a catch. A web page looks different for you and the search engine. You see it as a collection of graphics, colors, text with its formatting, and links.
To a search engine, it’s nothing but text.
As a result, any elements it cannot render this way remain invisible to the search engine. And so, in spite of your website looking fine to you, Google might find its content inaccessible.
Let me show you an example. Here’s how a typical search engine sees one of our articles. It’s this one, by the way, if you want to compare it with the original.

Notice some things about it:
- The page is just text. Although we carefully designed it, the only elements a search engine sees are text and links.
- As a result, it cannot see an image on the page (note the element marked with an arrow.) It only recognizes its name. If that image contained an important keyword we’d want the page to rank for, it would be invisible to the search engine.
That’s where technical setup, also called on-site optimization, comes in. It ensures that your website and pages allow Google to scan and index them without any problems. The most important factors affecting it include:
Website navigation and links
Search engines crawl sites just like you would. They follow links. Search engine crawlers land on a page and use links to find other content to analyze. But as you’ve seen above, they cannot see images. So, set the navigation and links as text-only.
Simple URL structure
Search engines don’t like reading lengthy strings of words with complex structure. So, if possible, keep your URLs short. Set them up to include as little beyond the main keyword for which you want to optimize the page, as possible.
Page speed
Search engines use the load time — the time it takes for a user to be able to read the page — as an indicator of quality. Many website elements can affect it. Image size, for example. Use Google’s Page Speed Insights Tool for suggestions on how to improve your pages.
Dead links or broken redirects
A dead link sends a visitor to a nonexistent page. A broken redirect points to a resource that might no longer be there. Both provide poor user experience but also, prevent search engines from indexing your content.
Sitemap and Robots.txt files
A sitemap is a simple file that lists all URLs on your site. Search engines use it to identify what pages to crawl and index. A robots.txt file, on the other hand, tells search engines what content not to index (for example, specific policy pages you don’t want to appear in search.) Create both to speed up crawling and indexing of your content.
Duplicate content
Pages containing identical or quite similar content confuse search engines. They often find it to be nearly impossible to display any of those pages at all. If search engines do find them, your website can be penalized. For that reason, search engines consider duplicate content as a negative factor.
Featured Resource
2. Content
Every time you use a search engine, you’re looking for content — information on a particular issue or problem, for example.
True, this content might come in different formats. It could be text, like a blog post or a web page. But it could also be a video, product recommendation, and even a business listing.
It’s all content.
And for SEO, it’s what helps gain greater search visibility.
Here are two reasons why:
- First, content is what customers want when searching. Regardless of what they’re looking for, it’s content that provides it. And the more of it you publish, the higher your chance for greater search visibility.
- Also, search engines use content to determine how to rank a page. It’s the idea of relevance between a page and a person’s search query that we talked about earlier.
While crawling a page, they determine its topic. Analyzing elements like page length or its structure helps them assess its quality. Based on this information, search algorithms can match a person’s query with pages they consider the most relevant to it.
The process of optimizing content begins with keyword research.
Keyword Research
SEO is not about getting any visitors to the site. You want to attract people who need what you sell and can become leads, and later, customers.
However, that’s possible only if it ranks for the keywords those people would use when searching. Otherwise, there’s no chance they’d ever find you. And that’s even if your website appeared at the top of the search results.
That’s why SEO work starts with discovering what phrases potential buyers enter into search engines.
The process typically involves identifying terms and topics relevant to your business. Then, converting them into initial keywords. And finally, conducting extensive research to uncover related terms your audience would use.
We’ve published a thorough guide to keyword research for beginners. It lays out the keyword research process in detail. Use it to identify search terms you should be targeting.
With a list of keywords at hand, the next step is to optimize your content. SEOs refer to this process as on-page optimization.
On-Page Optimization
On-page optimization, also called on-page SEO, ensures that search engines a.) understand a page’s topic and keywords, and b.) can match it to relevant searches.
Note, I said “page” not content. That’s because, although the bulk of on-page SEO work focuses on the words you use, it extends to optimizing some elements in the code.
You may have heard about some of them — meta-tags like title or description are two most popular ones. But there are more. So, here’s a list of the most crucial on-page optimization actions to take.
Note: Since blog content prevails on most websites, when speaking of those factors, I’ll focus on blog SEO — optimizing blog posts for relevant keywords. However, all this advice is equally valid for other page types too.
Featured Resource
a) Keyword Optimization
First, ensure that Google understands what keywords you want this page to rank. To achieve that, make sure you include at least the main keyword in the following:
- Post’s title: Ideally, place it as close to the start of the title. Google is known to put more value on words at the start of the headline.
- URL: Your page’s web address should also include the keyword. Ideally, including nothing else. Also, remove any stop word.
- H1 Tag: In most content management systems, this tag displays the title of the page by default. However, make sure that your platform doesn’t use a different setting
- The first 100 words (or the first paragraph) of content: Finding the keyword at the start of your blog post will reassure Google that this is, in fact, the page’s topic.
- Meta-title and meta-description tags: Search engines use these two code elements to display their listings. They display the meta-title as the search listing’s title while the meta-description provides content for the little blurb below it. But above that, they use both to understand the page’s topic further.
- Image file names and ALT tags: Remember how search engines see graphics on a page? They can only see their file names. So, make sure that at least one of the images contains the keyword in the file name.
The alt tag, on the other hand, is text browsers display instead of an image (for visually impaired visitors.) However, since ALT tag resides in the image code, search engines use it as a relevancy signal as well.
Also, add semantic keywords — variations or synonyms of your keyword. Google and other search engines use them to determine a page’s relevancy better.
Let me illustrate this with a quick example. Let’s pretend that your main keyword is “Apple.” But do you mean the fruit or the tech giant behind the iPhone?
Now, imagine what happens when Google finds terms like sugar, orchard, or cider in the copy? The choice of what queries to rank it for would immediately become obvious, right?
That’s what semantic keywords do. Add them to ensure that your page doesn’t start showing up for irrelevant searches.
b) Non-Keyword-Related On-Page Optimization Factors
On-page SEO is not just about sprinkling keywords across the page. The factors below help confirm a page’s credibility and authority too:
- External links: Linking out to other, relevant pages on the topic helps Google determine its topic further. Plus, it provides a good user experience. How? By positioning your content as a valuable resource.
- Internal links: Those links help you boost rankings in two ways. One, they allow search engines to find and crawl other pages on the site. And two, they show semantic relations between various pages, helping to determine its relevance to the search query better. As a rule, you should include at least 2-4 internal links per blog post
- Content’s length: Long content typically ranks better. That’s because, if done well, a longer blog post will always contain more exhaustive information on the topic, thus keeping a reader on your site longer. That’s called dwell time, and it’s an important ranking factor for the search engines
- Multimedia: Although not a requirement, multimedia elements like videos, diagrams, audio players can signal a page’s quality. It keeps readers on a page for longer just like longer content does. And in turn, it signals that they find the content valuable and worth pursuing.
3. Links
From what you’ve read in this guide so far, you know that no page will rank without two factors — relevance and authority.
In their quest to provide users with the most accurate answers, Google and other search engines prioritize pages they consider the most relevant to their queries but also, popular.
The first two areas — technical setup and content — focused on increasing relevance (though I admit, some of their elements can also help highlight the authority.)
Links, however, are responsible for popularity.
But before we talk more about how they work, here’s what SEOs mean when talking about links.
What is a backlink?
Links, also called backlinks, are references to your content on other websites. Every time another website mentions and points their readers to your content, you gain a backlink to your site.
For example, this article in Entrepreneur.co mentions our Not Another State of Marketing Report page. It also links to it allowing their readers to see other stats than the one quoted.
Google uses the quantity and quality of links like this as a signal of a website’s authority. Its logic behind it is that webmasters would reference a popular and high-quality website more often than a mediocre one.
But note that I mentioned link quality as well. That’s because not all links are the same. Some — low-quality ones — can impact your rankings negatively.
Links Quality Factors
Low quality or suspicious links — for example, ones that Google would consider as built deliberately to make it consider a site as more authoritative — might reduce your rankings.
That’s why, when building links, SEOs focus not on building any links. They aim to generate the highest quality references possible.
Naturally, just like with the search algorithm, we don’t know what factors determine a link’s quality, specifically. However, over time, SEOs discovered some of them:
- The popularity of a linking site: Any link from a domain that search engines consider an authority will naturally have high quality. In other words, links from websites that have good quality links pointing to them will yield better results.
- Topic relevance: Links from domains on a topic similar to yours will carry more authority than those from random websites.
- Trust in a domain: Just like with popularity, search engines also assess a website’s trust. Links from more trustworthy sites will always impact rankings better.
Link Building
In SEO, we refer to the process of acquiring new backlinks as link building. And as many practitioners admit, it can be a challenging activity.
Link building, if you want to do it well, requires creativity, strategic thinking, and patience. To generate quality links, you need to come up with a link building strategy. And that’s no small feat.
Remember, your links must pass various quality criteria. Plus, it can’t be obvious to search engines that you’ve built them deliberately.
Here are some strategies to do it:
- Editorial, organic links: These backlinks come from websites that reference your content on their own.
- Outreach: In this strategy, you contact other websites for links. This can happen in many ways. You could create an amazing piece of content, and email them to tell them about it. In turn, if they find it valuable, they’ll reference it. You can also suggest where they could link to it.
- Guest posting: Guest posts are blog articles that you publish on third-party websites. In turn, those companies often allow including one or two links to your site in the content and author bio.
- Profile links: Finally, many websites offer an opportunity to create a link. Online profiles are a good example. Often, when setting up such a profile, you can also list your website there as well. Not all such links carry strong authority, but some might. And given the ease of creating them, they’re worth pursuing.
- Competitive analysis: Finally, many SEOs regularly analyze their competitors’ backlinks to identify those they could recreate for their sites too.
Now, if you’re still here with me, then you’ve just discovered what’s responsible for your site’s success in search.
The next step, then, is figuring out whether your efforts are working.
How to Monitor & Track SEO Results
Technical setup, content, and links are critical to getting a website into the search results. Monitoring your efforts helps improve your strategy further.
Measuring SEO success means tracking data about traffic, engagement, and links. And though, most companies develop their own sets of SEO KPIs (key performance indicators), here are the most common ones:
- Organic traffic growth
- Keyword rankings (split into branded and non-branded terms)
- Conversions from organic traffic
- Average time on page and the bounce rate
- Top landing pages attracting organic traffic
- Number of indexed pages
- Links growth (including new and lost links)
Local SEO
Up until now, we focused on getting a site rank in search results in general. If you run a local business, however, Google also lets you position it in front of potential customers in your area, specifically. But for that, you use local SEO.
And it’s well worth it.
46% of Google searches are for local businesses. They look for vendor suggestions, and even specific business addresses.
What’s more, they act on this information: 72% of searchers visit a local store or company’s premises within 24 hours of the search.
But hold on, is local SEO different from what we’ve been talking about all along?
Yes and no.
Search engines follow similar principles for both local and global rankings. But given that they position a site for specific, location-based results, they need to analyze some other ranking factors too.
Even local search results look different:
- They appear only for searches with a local intent (for example, “restaurant near me” or when a person clearly defined the location.)
- They contain results specific to a relevant location.
- They concentrate on delivering specific information to users that they don’t need to go anywhere else to find.
- They target smartphone users primarily as local searches occur more often on mobile devices.
For example, a localpack, the most prominent element of local results, includes almost all information a person would need to choose a business. Here are local results Google displays for the phrase “best restaurant in Boston.”
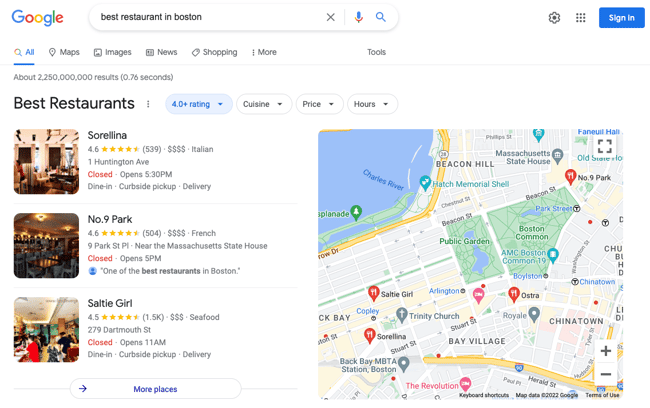
Note that these results contain no links to any content. Instead, they include a list of restaurants in the area, a map to show their locations, and additional information about each:
- Business name
- Description
- Image
- Opening hours
- Star Reviews
- Address
Often, they also include a company’s phone number or website address.
All this information combined helps customers choose which business to engage. But it also allows Google to determine how to rank it.
Local Search Ranking Factors
When analyzing local websites, Google looks at the proximity to a searcher’s location. With the rise of local searches containing the phrase, “near me,” it’s only fair that Google will try to present the closest businesses first.
Keywords are essential for local SEO too. However, one additional element of on-page optimization is the presence of a company’s name, address, and phone number of a page. In local SEO, we refer to it as the NAP.
Again, it makes sense, as the search engine needs a way to assess the company’s location.
Google assesses authority in local search not just by links. Reviews and citations (references of a business’s address or a phone number online) highlight its authority too.
Finally, the information a business includes in Google My Business — the search engine’s platform for managing local business listings — plays a huge part in its rankings.
The above is just the tip of the iceberg. But they are the ones to get right first if you want your business to rank well in local search.
What is black hat SEO?
The final aspect of SEO I want to highlight to you is something I also hope you’ll never get tempted to use. I mean it.
Because, although it might have its lure, using black hat SEO typically ends in a penalty from search listings.
Black hat practices aim at manipulating search engine algorithms using strategies against search engine guidelines. The most common black hat techniques include keyword stuffing, cloaking (hiding keywords in code so that users don’t see them, but search engines do), and buying links.
So, why would someone use black hat SEO? For one, because, often, ranking a site following Google’s guidelines takes time. Long time, in fact.
Black hat strategies let you cut down the complexity of link building, for example. Keyword stuffing helps users to rank one page for many keywords, without having to create more content.
But as said, getting caught often results in a site being completely wiped out from search listings.
And the reason I mention it here is that I want you to realize that there are no shortcuts in SEO. And be aware of anyone suggesting strategies that might seem too good to be true.
Should you outsource SEO or keep it in-house?
Whether you work on SEO yourself, delegate it to another team member, or outsource it completely, you’ll want to make this decision with as much knowledge as possible.
Doing SEO Yourself
Be honest with yourself — are you interested in learning SEO? Do you have time to learn the basics? Do you have the resources to bring in help if you redesign your website and accidentally deindex several pages? If the answer to any of these questions is “no,” then you might not want to take on the responsibility of SEO yourself. SEO is a long term play, and just like a muscle, you have to work at it consistently to see results. That can take a substantial amount of commitment. If you have any doubts, try the next best thing — delegating the work.
Delegate SEO to a Team Member
If you’re not quite sure about taking on SEO yourself, consider delegating the work to a team member. If you have a person who’s interested in growth marketing, development, or even web design, this would be a valuable skill to help grow their career. You could also hire a full-time search engine optimization specialist if you have the budget.
The person in this role can report to the marketing team, development team, or even design team. Because SEO touches nearly every function of a business while maintaining a unique set of skill requirements, this position won’t be subject to frequent changes if departments need to be restructured later on. The person you delegate to this job will contribute cross functionally more often than not, so you’ll have some liberty with managing them.
Outsource SEO to an Agency
You don’t have the interest in SEO, your team’s at full capacity, and you can’t spare the budget to fill a full time SEO role. Now what? The best bang for your buck is to outsource SEO to a reputable consultant. Why? First, a well-respected SEO consultant is highly skilled in bringing organic traffic, leads, and conversions to businesses. They do this day in and day out, so they won’t need the ramp up time that you or a member of your team would need in order to learn the basics.
Second, a consultant can be less expensive than hiring someone full-time for the role because they don’t require insurance benefits, payroll taxes, etc. But how much exactly would you be looking at for outsourcing your SEO?
SEO can cost between $100 and $500 per month if you do it yourself with a keyword research tool. It can cost between $75 and $150 per hour for a consultant, and up to $10,000 per month if you hire a full-service marketing agency. Small businesses generally spend less on SEO than big brands, so be sure to take that into account.
Incurring SEO costs can mean one of two things: the investment in your organic search strategy, or how much you pay for paid search engine marketing (SEM) services like Google Ads. If you’re paying for a tool, consultant, or marketing agency to help you optimize your web content, your bill can vary wildly with the depth of the services you’re receiving.
SEO Resources & Training
This guide is just a starting point for discovering SEO. But there’s much more to learn.
Here are online training resources to try next if your or someone on your team wants to take on this skill:
You can also pick SEO knowledge from industry experts and their blogs. Here are some worth reading:
- SEMrush
- MOZ
- Yoast
- BrightLocal (local SEO advice)
- Search Engine Journal
- Search Engine Watch
- Search Engine Land
- Bruce Clay Inc.
Over To You
Without actively positioning its content in search results, no business can survive long.
By increasing your search visibility, you can bring more visitors, and in turn, conversions and sales. And that’s well worth the time spent becoming an expert in SEO.
Editor’s note: This post was originally published in November 2019 and has been updated for comprehensiveness.

Source :
https://blog.hubspot.com/marketing/seo







 Passwordless phone sign in experience in Microsoft Authenticator for Azure AD accounts.
Passwordless phone sign in experience in Microsoft Authenticator for Azure AD accounts. End user experience for Temporary Access Pass in Windows 11 onboarding.
End user experience for Temporary Access Pass in Windows 11 onboarding.





