Ransomware is a kind of malware used by cybercriminals to stop users from accessing their systems or files; the cybercriminals then threaten to leak, destroy or withhold sensitive information unless a ransom is paid.
Ransomware attacks can target either the data held on computer systems (known as locker ransomware) or devices (crypto-ransomware). In both instances, once a ransom is paid, threat actors typically provide victims with a decryption key or tool to unlock their data or device, though this is not guaranteed.
Oliver Pinson-Roxburgh, CEO of Defense.com, the all-in-one cybersecurity platform, shares knowledge and advice in this article on how ransomware works, how damaging it can be, and how your business can mitigate ransomware attacks from occurring.
What does a ransomware attack comprise?
There are three key elements to a ransomware attack:
Access
In order to deploy malware to encrypt files and gain control, cybercriminals need to initially gain access to an organization’s systems.
Trigger
The attackers have control of the data as soon as the malicious software is activated. The data is encrypted and no longer accessible by the targeted organization.
Demand
The victims will receive an alert that their data is encrypted and cannot be accessed until a ransom is paid.
Big business for cybercriminals
The motives of cybercriminals deploying malware may vary but the end goal is typically that of financial gain.
What is the cost of being targeted by ransomware?
The average pay-out from ransomware attacks has risen from $312,000/£260,000 in 2020 to $570,000/£476,000 in 2021 – an increase of 83%. One report also showed that 66% of organisations surveyed were victims of ransomware attacks in 2021, nearly double that of 2020 (37%). This highlights the need for businesses to understand the risks and implement stronger defenses to combat the threats.
Ransomware continues to rank amongst the most common cyberattacks in 2022, due to its lucrative nature and fairly low level of effort required from the perpetrators. This debilitating attack causes an average downtime of 3 weeks and can have major repercussions for an organization, for its finances, operations and reputation.
Because there is no guarantee that cybercriminals will release data after a ransom is paid, it is crucial to protect your data and keep offline backups of your files. It’s also very important to proactively monitor and protect entry points that a hacker may exploit, to reduce the possibility of being targeted in the first place.
Who is at risk of being a target of ransomware?
In the past, cybercriminals have typically targeted high-profile organizations, large corporations and government agencies with ransomware. This is known as ‘big game hunting’ and works on the premise that these companies are far more likely to pay higher ransoms and avoid unwanted scrutiny from the media and public. Certain organizations, such as hospitals, are higher-value targets because they are far more likely to pay a ransom and to do so quickly because they need access to important data urgently.
However, ransomware groups are now shifting their focus to smaller businesses, in response to increased pressure from law enforcement who are cracking down on well-known ransomware groups such as REvil and Conti. Smaller companies are seen as easy targets that may lack effective cybersecurity defenses to prevent a ransomware attack, making it easier to penetrate and exploit them.
Ultimately, threat actors are opportunists and will consider most organizations as targets, regardless of their size. If a cybercriminal notices a vulnerability, the company is fair game.
How is ransomware deployed?
Phishing attacks
The most common delivery method of ransomware is via phishing attacks. Phishing is a form of social engineering and is an effective method of attack as it relies on deceit and creating a sense of urgency. Threat actors trick employees into opening suspicious attachments in emails and this is often achieved by imitating either senior-level employees or other trusted figures of authority.
Malvertising
Malicious advertising is another tactic used by cybercriminals to deploy ransomware, where ad space is purchased and infected with malware that is then displayed on trusted and legitimate websites. Once the ad is clicked, or even in some cases when a user accesses a website that’s hosting malware, that device is infected by malware that scans the device for vulnerabilities to exploit.
Exploiting vulnerable systems
Ransomware can also be deployed by exploiting unpatched and outdated systems, as was the case in 2017, when a security vulnerability in Microsoft Windows, EternalBlue (MS17-010), led to the global WannaCry ransomware attack that spread to over 150 countries.
It was the biggest cyberattack to hit the NHS: it cost £92m in damages plus the added costs of IT support restoring data and systems affected by the attack, and it directly impacted patient care through cancelled appointments.
Four key methods to defend your business against ransomware
It is crucial that businesses are aware of how a ransomware attack may affect their organization, and how they can prevent cybercriminals from breaching their systems and holding sensitive data to ransom. Up to 61% of organizations with security teams consisting of 11–25 employees are said to be most concerned about ransomware attacks.
The NHS could have avoided being impacted by the WannaCry ransomware attack in 2017 by heeding warnings and migrating away from outdated software, ensuring strategies were in place to strengthen their security posture.
It’s essential that your business takes a proactive approach to cybersecurity by implementing the correct tools to help monitor, detect, and mitigate suspicious activity across your network and infrastructure. This will reduce the number and impact of data breaches and cyberattacks.
Defense.com recommend these four fundamental tactics to help prevent ransomware attacks and stay one step ahead of the hackers:1 — Training
Cybersecurity awareness training is pivotal for businesses of all sizes as it helps employees to spot potentially malicious emails or activity.
Social engineering tactics, such as phishing and tailgating, are common and successful due to human error and employees not spotting the risks. It’s vital for employees to be vigilant around emails that contain suspicious links or contain unusual requests to share personal data, often sent by someone pretending to be a senior-level employee.
Security training also encourages employees to query visitors to your offices to prevent ransomware attacks via physical intrusion.
Implementing cybersecurity awareness training will help your business routinely educate and assess your employees on fundamental security practices, ultimately creating a security culture to reduce the risk of data breaches and security incidents.2 — Phishing simulators
These simulator tools support your security awareness training by delivering fake but realistic phishing emails to employees. Understanding how prone your staff are to falling for a real cybercriminal’s tactics allows you to fill gaps in their training.
When you combine phishing simulators with security training, your organization can lessen the chance of falling victim to a ransomware attack. The combination of training and testing puts you in a better position to prevent the cunning attempts of cybercriminals to infiltrate your IT systems and plant malware.3 — Threat monitoring
You can make your business less of a target for cybercriminals by actively monitoring potential threats. Threat Intelligence is a threat monitoring tool that collates data from various sources, such as penetration tests and vulnerability scans, and uses this information to help you defend against potential malware and ransomware attacks. This overview of your threat landscape shows which areas are most at risk of a cyberattack or a data breach.
Being proactive ensures you stay one step ahead of hackers and by introducing threat monitoring tools to your organization, you ensure any suspicious behaviour is detected early for remediation.4 — Endpoint protection
Endpoint protection is key to understanding which of your assets are vulnerable, to help protect them and repel malware attacks like ransomware. More than just your typical antivirus software, endpoint protection offers advanced security features that protect your network, and the devices on it, against threats such as malware and phishing campaigns.
Anti-ransomware capabilities should be included in endpoint protection so it can effectively prevent attacks by monitoring suspicious behaviour such as file changes and file encryption. The ability to isolate or quarantine any affected devices can also be a very useful feature for stopping the spread of malware.
In summary
With ransomware groups continually looking for vulnerabilities to exploit, it’s important that businesses develop robust strategies to prevent ransomware threats: ensure your staff takes regular security awareness training, set up threat monitoring tools to detect and alert you of vulnerabilities, and implement endpoint protection to protect your devices across your network.
Following the above guidelines will increase your chances of safeguarding your business against ransomware attacks that could cost your organization a substantial amount of money and reputational damage.
Defense.com believes world-class cyber protection should be accessible to all companies, regardless of size. For more information, visit Defense.com.
Source :
https://thehackernews.com/2022/08/what-is-ransomware-how-to-defend-your.html

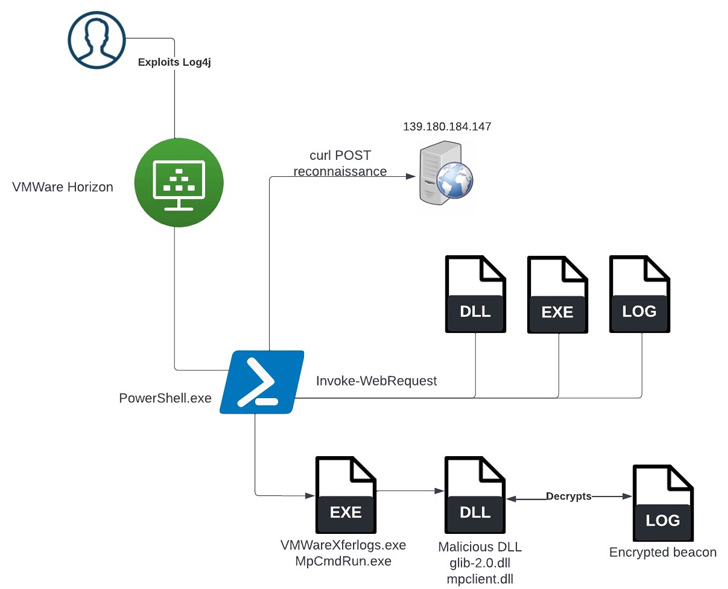

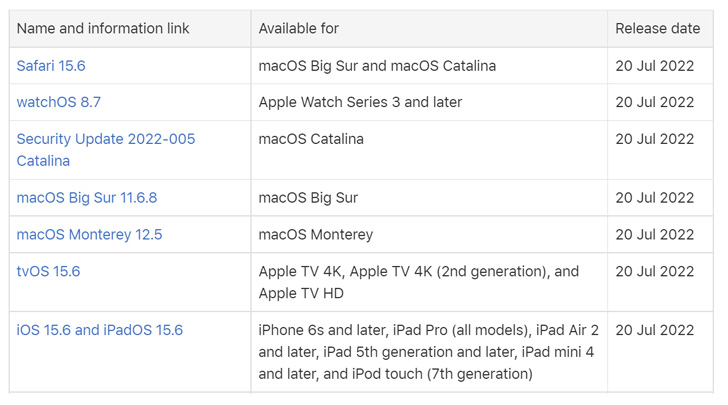
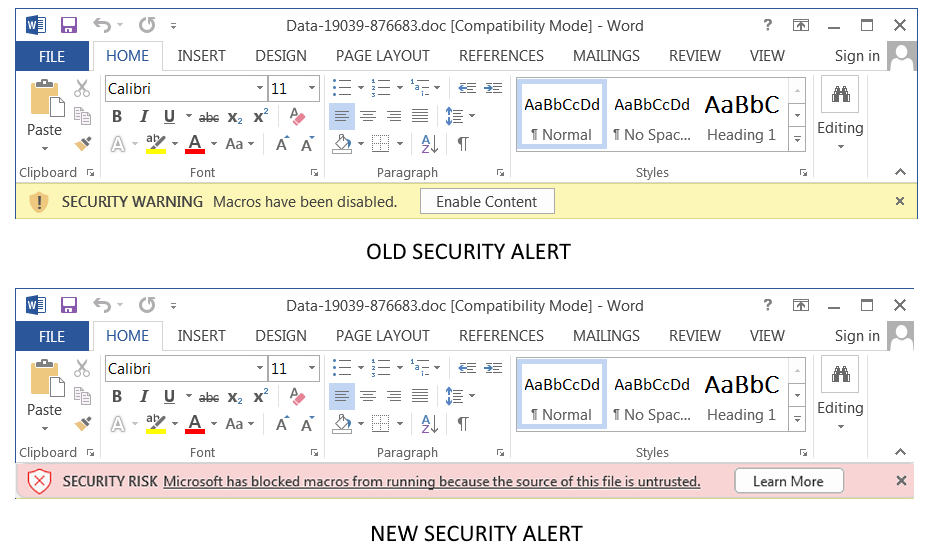
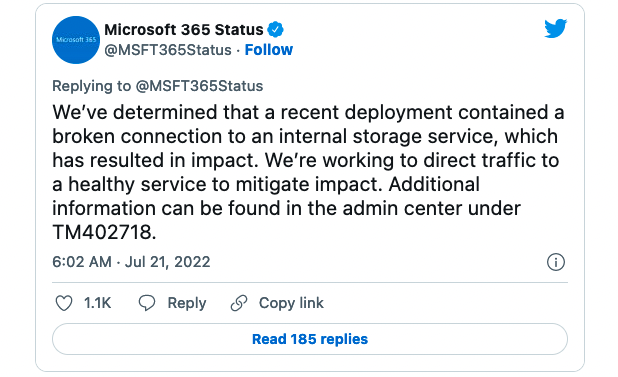






 Quick note: The page usually lists two versions, including ARM64 and x64. Unless you have an ARM-based device, you need to download the x64 version of the cumulative update.
Quick note: The page usually lists two versions, including ARM64 and x64. Unless you have an ARM-based device, you need to download the x64 version of the cumulative update.





