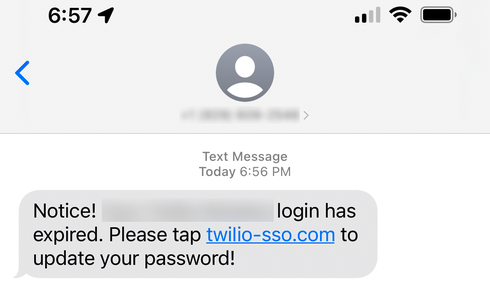
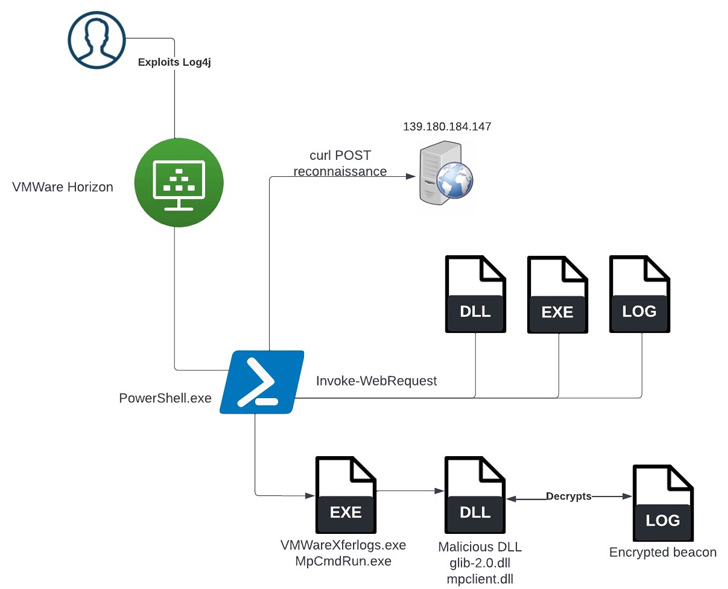
Upselling and cross-selling are tactics that you can use to sell more, with less—less time, less money, less resources. Simple as that. And both tactics can be applied to virtually every industry: software, retail, finance, telecom, manufacturing, real estate—you name it.
I run Tee Tweets, a clothing brand that lets you wear any tweet in the world, and cross-selling and upselling are two of the most important tactics in my business strategy. Both techniques are designed to get customers to buy more, and since there are hundreds of thousands of tweets generated every minute, I certainly have plenty of products for buyers to add to their cart.
Sell more and keep your customers happy
Upselling and cross-selling are often confused because, in some ways, they accomplish the same goal of increasing the amount that a customer will buy. But there are distinct differences between the two, and if you can master them, they can both be uniquely instrumental to your business’s success.
What’s the difference?
Both cross-selling and upselling involve convincing an existing customer to increase the amount they’re buying. But here’s the difference:
- When you’re cross-selling, you’re working specifically to get the customer to make additional purchases that would go well with what they originally intended to buy.
- When you’re upselling, you’re not necessarily suggesting more items, but convincing the customer to buy the bigger, better, and more expensive version of their original purchase.
For example, when I send out marketing or confirmation emails to recent buyers, I make sure to include products that are similar to whatever that recipient bought. Often this results in a new sale, but even when it doesn’t, it still exposes the customer to other products they may not have known existed. That’s cross-selling.
There’s not as much upselling involved in TeeTweets, but I’ve come across plenty of upselling opportunities in my freelance consulting career at Swyftlight. I had one particular client who wanted me to build a simple marketing website, so they gave me their specs and budget and asked me to put together a proposal. I pitched the idea of adding eCommerce capabilities to their site, quoting them a rate that was still within their budget but was more than I would have quoted them for the simple site alone. They took me up on it—I effectively upsold them on a better version of their original product.
Those are two basic examples, but if you really want to make sure you’re capitalizing on every upselling and cross-selling opportunity you encounter, it’s important to understand both tactics in depth.
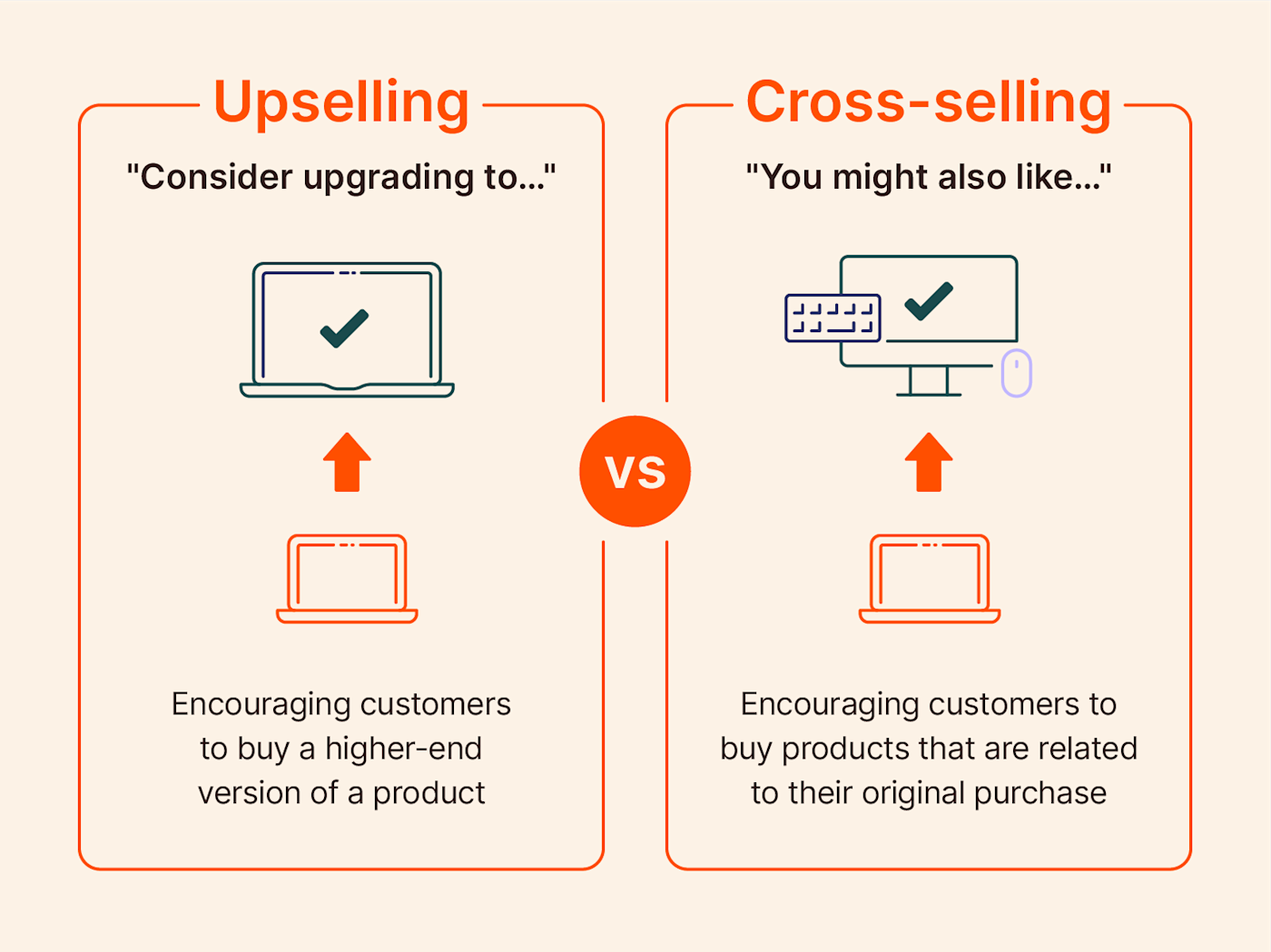
What is upselling?
Upselling is about upgrading the customer to a bigger or better version of the product or service they’re already buying. Virtually every modern business does some form of upselling, but one of the most common examples can be seen in an industry we all know and love: food.
Think specifically of the fast food industry, where customers are always encouraged to “supersize” the size of an item. Ordering small fries? Make it a large for only an extra 25 cents.
Upselling works in all industries, not just consumer-focused ones. If your business pays for software, for example, you’ve almost definitely seen upselling in action. Let’s take a look at Airtable.
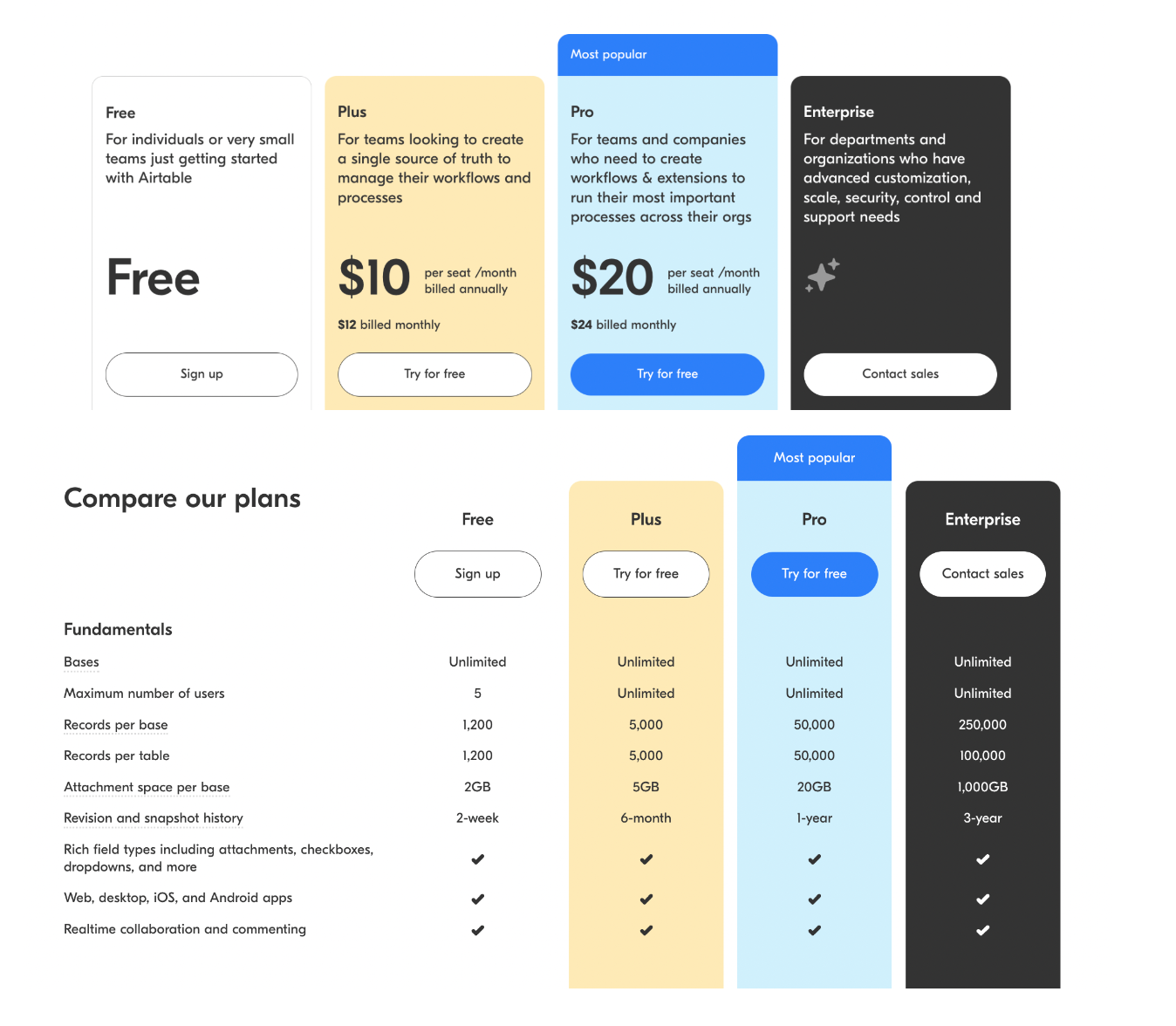
Airtable’s pricing structure is laid out in such a way that you can see every plan’s capabilities all in one place. When you’re making your purchase, this page encourages you to stop and wonder: will 5,000 automation runs be enough? Will 5GB hold what I need?
As you’re contemplating how much you need, you’ll also notice that the prices don’t increase proportionately with the increase in services. The Pro plan costs twice as much as the Plus plan, but offers four times more attachment space and ten times more automation runs. When the higher overall price means a lower price-per-item, people are much more susceptible to being upsold.
Those are just two examples. Once you know what upselling looks like, you’ll start to notice it everywhere. More examples include:
- Promoting a warranty when someone buys an appliance
- Suggesting upgrading to a spa package when someone goes to book a massage
- Offering more analytical accounting services in addition to your standard transitional bookkeeping services
- When someone hires you to design their logo, proposing an entire branding package instead
- Suggesting the fleece-lined version when someone’s about to buy leggings
What is cross-selling?
Cross-selling is about getting customers to buy different, related items in addition to what they’re already buying. The most effective cross-sellers pitch items that will enhance whatever the person is buying, or will make using that item much easier.
The most clear-cut example is Amazon. Whenever you’re looking at a product, if you scroll down, you’ll always see a “Customers also bought” section. Amazon also uses automated purchase history analysis to look at what you’ve bought in the past, find customers with similar buying habits, and suggest items that are popular among people who are looking for the same things you are.
Have a look at this small business in the candle game:

In this case, when you buy a relaxing candle, the site is going to recognize more types of relaxing candles. But cross-selling isn’t just about getting customers to buy more similar items right this moment—it’s also about exposing your customers to new products they might not be familiar with.
The most important thing to keep in mind is that while products you suggest don’t need to be extremely similar, they do need to be complementary. Cross-selling isn’t just about getting customers to buy more items right this moment—it’s about exposing your customers to new products and offerings they may not have seen before. When coupled with a purchase your customer is already set on buying, your brand exposure can have more significant weight than you might expect. You may not make the extra sale today, but you increase the likelihood that the customer comes back at some point down the line.
Upselling vs. cross-selling in action
One of the easiest ways to learn the difference between upselling and cross-selling is to look for examples of both within the same industry or even at the same company.
Let’s say you buy a new desk chair for your home office. The upsell would be a better, fancier chair with ergonomic features and fancy wheels. The cross-sell would be an under-desk mat, which you’ll need to keep those fancy wheels from tearing up the hardwood.
Applying upselling and cross-selling to your business
Upselling and cross-selling are both an art and a science. You need to think creatively about your offerings (and potential offerings) and how they might complement existing purchases. But you also need to dive into your analytics and make some data-driven decisions about what your customers are buying, when they’re buying them, and why. After all, upselling and cross-selling won’t do anything for you if no one actually buys what you’re promoting.
I’ve found that the most effective strategy when it comes to using upselling and cross-selling well is to reverse engineer what makes the most sense for your customers. What adds the most value for them? What questions do they have when buying from you? What products or services do they ask you about that you don’t yet offer? Talking directly to existing customers or clients about what they might want is a great place to start.
And remember: there’s always room to experiment. If people who buy product X often also buy product Y, you should absolutely be trying to sell product Y to everyone who buys product X. But don’t stop there. Try promoting product Z to those same people, or try upselling them to a higher quality version. Think outside the box, and you’ll find some creative ways to sell more—and better.
This article was originally published in March 2021 and was most recently updated in August 2022 with contributions from Amanda Pell.
Source :
https://zapier.com/blog/cross-selling-vs-upselling/