From the above topic, we can guess that today, we are going to discuss the top 10 DNS attacks and how to mitigate them. DNS stands for Domain Name System which remains under constant attacks, and thus we can assume there is no end in sight because the threats are growing increasingly nowadays.
DNS generally uses UDP fundamentally and in some cases, uses TCP as well. When it uses the UDP protocol, which is connectionless and can be tricked easily.
Thus DNS protocol is remarkably popular as a DDoS tool, and DNS, recognized as the internet’s phonebook, which is a component of the global internet foundation that transmutes between well-known names and the number that a computer needed to enter a website and send an email.
DNS has long been the target of attackers looking to take all custom of corporate and secret data, hence, the warnings in the past year indicate a worsening of the condition.
As per the IDC’s research, the average costs correlated with a DNS mugging rose by 49% associated with a year earlier. However, in the U.S., the average price of a DNS attack trims out at more than $1.27 million.
Approximately half of the respondents (48%) state that wasting more than $500,000 to a DNS attack, and about 10% say that they lost more than $5 million on each break. In extension, the preponderance of U.S. companies says that it needed more than one day to determine a DNS attack.
Shockingly, as per the information both in-house and cloud applications were destroyed, the 100% growth of threats in the in-house application interlude, frothingly it is now the most widespread destruction experienced that IDC composed.
Thus the “DNS attacks are running away from real brute-force to more complicated attacks running from the internal network. Thus the complicated attack will push the organizations to use intelligent mitigation tools so that they can easily cope with insider threats.”
Therefore we have provided the top 10 DNS attacks and the proper solutions to fix them, so that it will be easy for the organizations to recognize the attacks and can quickly solve it.
Famous DNS Attacks Type:
- DNS Cache Poisoning Attack
- Distributed Reflection Denial of Service (DRDoS)
- DNS Hijacking
- Phantom Domain Attack
- TCP SYN Floods
- Random Subdomain Attack
- DNS Tunneling
- DNS Flood Attack
- Domain Hijacking
- Botnet-based Attacks
DNS Cache Poisoning Attack
At first, we have the cache poisoning, it’s one of the frequent attacks, and its main aim is to take the web users towards the scam websites, as for example, a user accesses gmail.com through the web browser to consult their mailbox.
Moreover, the DNS is becoming poisoned, and it’s not the gmail.com page which is exposed but a scam page determined by the criminal, in order, for example, to reclaim the email box accesses. Thus the users accessing the correct domain name will not see that the website they’re entering is not the right one but a scam one.
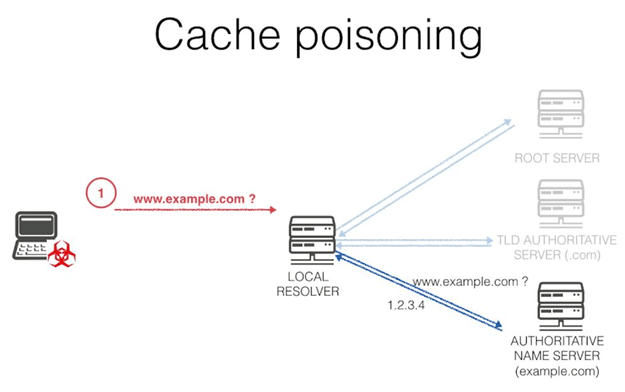
Basically, it generates an excellent possibility for cybercriminals to use phishing techniques to steal information, both identification information or credit card information from ingenuous victims. The attack can be devastating, depending on several factors, the attacker’s purpose, and the DNS poisoning impact.
DNS Attack Mitigation – Cache poisoning
As per the information, there are several forms to solve or to prevent this attack. For beginners, the IT teams should configure DNS servers to rely as small as possible on trust relations with other DNS servers. Performing so will make it more difficult for attackers to practice their DNS servers to debased their targets’ servers. There is another method to prevent cache poisoning attacks, as IT teams should also configure their DNS name servers to:-
- To restrict recursive queries.
- To store only data associated with the requested domain.
- To restrict query responses to only given information about the demanded domain.
Not only this, but there are also some cache poisoning tools accessible to help organizations for preventing cache poisoning outbreaks. And the most famous cache poisoning prevention tool is the DNSSEC (Domain Name System Security Extension), a tool that is produced by the Internet Engineering Task Force, which provides reliable DNS data authentication.
Distributed Reflection Denial of Service (DRDoS)
Distributed reflective denial of service (DRDoS) attacks concentrate on bringing down the availability of an asset within an authoritative volume of UDP acknowledgments. In some instances, the attacker would transfer a DNS, NTP, etc.
They demand a parodied source IP, with the purpose of a more extensive acknowledgment being transferred to the host who indeed continues at the address that was forged.

UDP is the protocol of different choices for this variety of attacks, as it does not build a connection state. For example, suppose a spoofed source of IP in the SYN package of a TCP connection would cause immediate termination just because the SYN/ACK will go away.
This practice makes reflection potential and possible, meanwhile, regulating these attacks at the proper scale, the idea of shared reflection becomes clear; hence, various endpoints transmitting spoofed UDP offers, generating acknowledgments that will be concentrated upon a target.
Once these response packs begin to appear, the goal experiences a loss of availability.
How to Prevent?
Usually, organizations should commence on preparing for DDoS attacks in advance, it is exceedingly harder to answer after an attack because it is already underway.
Moreover, DDoS attacks can’t be stopped, therefore some steps can be taken to make it more troublesome for an attacker to perform a network unresponsive. The following steps will help you to scatter organizational assets to bypass performing a single deep target to an attacker.
- First, locate servers in different data centers.
- Assure that your data centers are located on various networks.
- Make sure that data centers have several paths.
- Make sure that the data centers, or the networks that the data centers are related to, have no essential security holes or single points of failure.
An organization that relies on servers and Internet port, for them, it is essential to make sure that devices are geographically scattered and not located in a particular data center.
Moreover, if the resources are already geographically dispersed, then it’s essential to inspect each data station is having more than one channel to the internet and assure that not all data stations are attached to the corresponding internet provider.
DNS Hijacking
DNS hijacking is a method in which an individual can divert to the doubtful DNS (Domain Name System). However, it may be achieved by using malicious software or unauthorized alteration of a server.

Meanwhile, the individual has the authority of the DNS; they can guide others who obtain it to a web page that seems identical but carries extra content like advertisements. They can also guide users to pages carrying malware or a third-party search engine as well.
How to Prevent?
A DNS name server is a compassionate foundation that needs necessary protection measures because it can be hijacked and used by several hackers to raise DDoS attacks on others, thus, here we have mentioned some prevention of DNS hijacking.
- See for resolvers on your network.
- Critically restrict access to a name server.
- Utilize measures against cache poisoning.
- Instantly patch known vulnerabilities.
- Separate the authoritative name server from the resolver.
- Restrain zone alterations.
Phantom domain attack
Phantom domain attacks are kind of comparable to casual subdomain attacks. Thus in this kind of attack, the attackers attack your DNS resolver and overpower it to use up supplies to determine that’s what we name “phantom” domains, as these phantom domains will never respond to the queries.
The main motive of this attack is to let the DNS resolver server await for the answer for a long time, ultimately leading to failure or deteriorated DNS performance problems.
How to Prevent?
To identify phantom domain attacks, you can analyze your log messages. Moreover, you can also follow the steps that we have mentioned below to mitigate this attack.
- First, increase the number of recursive clients.
- Use a proper sequence of the following parameters to gain optimum results.
- Restrict recursive queries per server and Restrict recursive inquiries per zone.
- Empower to hold down for non-responsive servers and Check recursive queries per zone.
When you allow any of the options, the failure values are set at an excellent level for overall operations. However, you should keep the default charges while using these commands, moreover, it guarantees that you know the consequences if you want to replace the default values.
TCP SYN Floods
An SYN Flood is a simple form of Denial-of-Service (DDoS) attack that can target any operation related to the internet and thus implementing Transmission Control Protocol (TCP) services.
An SYN wave is a type of TCP State-Exhaustion attack that endeavors to utilize the connection element tables present in common infrastructure elements, for example, load balancers, firewalls, Intrusion Prevention Systems (IPS), and the utilization servers themselves.

Hence, This type of attack can bring down even high-capacity devices fitted to managing millions of links. Moreover, a TCP SYN flood attack occurs when the attacker overflows the system with SYN questions to destroy the target and make it incapable of reacting to new real connection offers.
Thus it encourages all of the target server’s information ports into a half-open state.
How to Prevent?
So, the firewalls and IPS devices, while important to network security, are not sufficient to protect a network from complex DDoS attacks.
Nowadays, the more sophisticated attack methodologies demand a multi-faceted program that allows users to look beyond both internet foundation and network availability.
Thus there are some capabilities that you can count for more powerful DDoS security and faster mitigation of TCP SYN flood attacks.
- At first, provide proper support to both inline and out-of-band deployment to assure that there is not only one single point of collapse on the network.
- Extensive network distinctness with the capacity to see and examine traffic from various parts of the network.
- Different sources of threat intelligence, including statistical exception detection, customizable entrance alerts, and fingerprints of known threats that assure fast and reliable detection.
Extensible to handle attacks of all sizes, extending from low-end to high-end and high-end to low-end.
Random Subdomain Attack
This is not the most prevalent type of DNS attack, but it can happen from time to time on several networks. Hence, the random subdomain attacks can often be identified as DoS attacks, as their creation adheres to the same goal as simple DoS.
Incase, spoilers send a lot of DNS inquiries against a healthy and active domain name. However, the questions will not target the primary domain name, but it will harm a lot of non-existing subdomains.
Basically, the main motive of this attack is to build a DoS that will immerse the authorized DNS server that receives the primary domain name, and finally let the interruption of all DNS record lookups.
Thus It’s an attack that’s hard to identify, as the queries will come from infected users who don’t even understand they’re sending certain types of questions, from what are eventually legitimate computers.
How to Prevent?
Thus we have provided you a simple method for preventing the random subdomain attack only in a 30-minute.
- In the beginning, you have to learn the techniques to mitigate the attacks that generate extreme traffic on resolvers and web resources that are connected with the victim the names that can be taken down.
- Next, Hear about modern capabilities like Response Rate Limiting for preserving DNS experts that provoke attacks.
DNS tunneling
This is a cyber attack that is used to carry encoded data from different applications inside DNS acknowledgments and queries.
Meanwhile, this system wasn’t formerly created to attack multitudes, but to bypass interface controls, now it is mostly used to achieve remote attacks.
To implement DNS tunneling, attackers demand to gain entrance to a settled system, as well as access to an internal DNS server, a domain name, and a DNS authoritative server.
How to Prevent?
To configure the firewall to identify and block DNS tunneling by designing an application rule that uses some protocol object, we have mentioned three steps to mitigate these types of attacks.
- Create an access rule.
- Create a protocol object.
- Create an application rule.
DNS Flood Attack
This is one of the most primary types of DNS attacks, and in this Distributed Denial of Service (DDoS), the intruder will hit your DNS servers.
The main motive of this kind of DNS flood is to completely overload your server so that it cannot maintain serving DNS requests because all the treated DNS zones influence the purpose of resource records.
Thus this kind of attack is relieved easily as the source usually comes from one single IP. However, it can get complicated when it becomes a DDoS where a hundred or thousand gatherings are involved.
While a lot of questions will be immediately identified as malicious bugs and a lot of legitimate requests will be made to mislead defense devices, hence, this makes the mitigation method a little bit difficult sometimes.
How to Prevent?
Domain Name System (DNS) has developed a target of the Distributed Denial of Service (DDoS) attacks. When a DNS is below a DDoS flood attack, all the domain data under that DNS enhances unreachable, thus ultimately creating the unavailability of those appropriate domain names.
Hence, for this type of attack, we have introduced a method that includes the periodic stale content update and manages a list of the most commonly queried domain names of several DNS servers. Hence our simulation outcomes show that our method can work more than 70% of the total cache replies during a massive DNS Flood attack.
Domain Hijacking
This type of attack involves settings in your DNS servers and domain registrar that can manage your traffic away from the actual servers to new destinations.
Domain hijacking is usually affected by a lot of determinants related to exploiting a vulnerability in the domain name registrar’s system, but can also be performed at the DNS level when attackers take command of your DNS records.

Hence when the attacker hijacked your domain name, it will be used to originate malicious movements such as installing up a fake page of repayment systems like PayPal, Visa, or bank systems. Attackers will produce an identical copy of the real website that reads critical personal knowledge, such as email addresses, usernames, and passwords.
How to Prevent?
Thus you can simply mitigate the domain hijacking by practicing a few steps that we have mentioned below.
- Upgrade your DNS in the application foundation.
- Use DNSSEC.
- Secure access.
- Client lock.
Botnet-based Attacks
If we talk about the botnet, then let me clarify that it is a number of Internet-connected devices, and it can be practiced to implement a distributed denial-of-service attack (DDoS attack), which steal data, transmit spam, and enables the attacker to obtain access to the device and its connection.

Moreover, botnets are diverse and evolving threats, hence, all these attacks are bound to develop in parallel with our growing dependence on digital devices, the internet, and new future technologies.
The botnets can be counted as attacks, as well as programs for future attacks, with this as the foundational prospect, this study explores how a botnet described and organized, how it is created, and used.
How to Prevent?
This is one of the frequent DNS attacks which have been faced by the victims every day, thus to mitigate these type of attacks, we have mentioned below few steps so that it will be helpful for you.
- At first, understand your vulnerabilities properly.
- Next, secure the IoT devices.
- Identify both your mitigation myths from facts.
- Discover, classify and control.
Conclusion
As you see, DNS service is essential for preserving your companies’ websites and online assistance working day-to-day. Thus if you’re looking for methods to evade these kinds of DNS attacks, then this post will be helpful for you. So, what do you think about this? Simply share all your views and thoughts in the comment section below. And if you liked this post then simply do not forget to share this post with your friends and family.


 NOTE: Edit the alt_names section to include any SAN names that are needed, no other sections need to be edited at this time
NOTE: Edit the alt_names section to include any SAN names that are needed, no other sections need to be edited at this time



 CAUTION: Using the converter is not recommended due to exposure of the private key to the internet
CAUTION: Using the converter is not recommended due to exposure of the private key to the internet TIP: Use the CA followed by the expiration date of the certificate; e.g. Comodo20181212
TIP: Use the CA followed by the expiration date of the certificate; e.g. Comodo20181212