Often we’re asked about what are the best WordPress SEO plugins and tools that we recommend.
That’s because search engines are a major source of traffic for most websites on the internet. Optimizing your website for search engines can help you rank higher in search results and significantly grow your business.
In this article, we will share the best WordPress SEO plugins and tools that you should use. Some of these tools offer similar functionalities, so we will also highlight which ones are the best for specific use-cases.
Things You Must Know About WordPress SEO Plugins & Tools
When reading SEO WordPress tips or searching for “best free WordPress SEO plugins”, you will come across articles that feature several dozen tools.
This can be quite overwhelming for beginners and non-techy users.
The truth is that you don’t need dozens of top SEO tools to get higher search engine result rankings.
While most blog posts (including ours) will share the top most popular SEO plugins, it is extremely important for you to understand the use-cases of each tool.
For example, you never want to use more than one WordPress SEO plugin on your website. We will mention All in One SEO (formerly All in One SEO Pack), Yoast SEO, SEOPress, and Rank Math. You need to pick only one to avoid plugin conflict.
We’ll mention SEMRush, Ahrefs, and few other powerful tools, but you don’t need them all when you’re first starting out since they have a similar feature set. We will share what tools we use in our business, and which features are the best among each tool.
With that said, let’s take a look at our expert pick of the best WordPress SEO plugins and tools.
1. All in One SEO for WordPress (AIOSEO)
All in One SEO for WordPress (AIOSEO) is the best WordPress SEO plugin on the market. Used by over 3+ million users, it is the most comprehensive SEO toolkit that helps you improve search rankings without learning any complicated SEO jargon.
The free version of AIOSEO has all the essential features, but the pro version gives you everything you need to outrank your competitors.
It comes with the easiest setup wizard that automatically helps you choose the best SEO settings for your business. AIOSEO shows you TruSEO on-page analysis with an actionable checklist to optimize your posts and pages.
The on-page SEO checklist includes a smart meta tag generator where you can use dynamic values (current year, month, day, custom fields, author info, and much more) in your SEO title and meta descriptions. This means you don’t need to update a post just to change SEO titles.
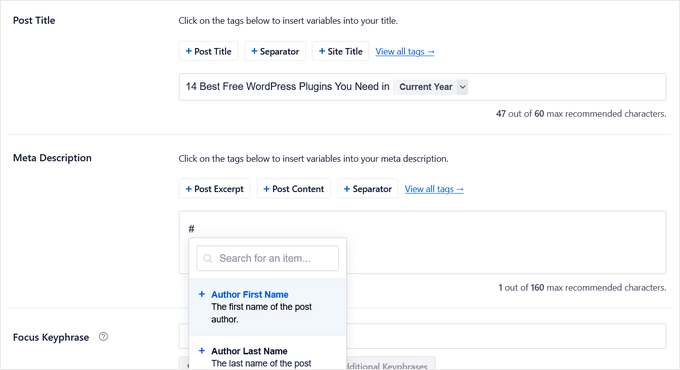
AIOSEO also comes with Rich snippet schema markup, smart XML sitemaps (with advanced controls), SEO health check, and other useful features to grow your search engine visibility.
There is a built-in social media integration to add Open Graph metadata as well. This means you can choose which image or thumbnail you want to show when your pages are shared on social media websites like Facebook, Twitter, Pinterest, etc.
AIOSEO also comes with built-in WooCommerce SEO tools for eCommerce sites. This includes features like dynamic optimizations, individual product page optimizations, product image SEO, and other handy features to bring more organic traffic to your online store.
For more SEO savvy users, it includes full control of RSS feeds, Robots.txt editor, local SEO, breadcrumbs, Google News sitemaps, video SEO, advanced redirect manager, 404 tracking, IndexNow integration, and more.
For business owners, it comes with SEO user roles, so you can manage access to important SEO features without handing over control of your website.
Update: Recently AIOSEO added a Link Assistant which is a game-changer for internal linking. It helps identify link opportunities, gives you linking suggestions in real-time, and you can bulk-add internal links with just a few clicks.
Overall, All in One SEO (AIOSEO) is the most beginner-friendly and comprehensive WordPress SEO plugin on the market. It’s easy to configure and eliminates the need to install multiple plugins to do things on your WordPress site. It works perfectly for all types of businesses, eCommerce, blogs, news, and other websites.
As a WPBeginner user, you get 50% off AIOSEO Pro.
For those who’re on a budget, you can use the free version of AIOSEO to get started.
2. SEMRush

SEMRush is the best overall SEO tool on the market. Used by professional SEO experts, marketers, bloggers, large and small businesses, it provides a comprehensive set of tools to grow your traffic.
You can use it to find organic keywords and search terms that you can easily rank for. It also allows you to do competitive research and see which keywords your competitors rank for, and how you can beat them.
SEMRush SEO Writing Assistant tool helps you improve your website content to beat the top 10 results for your focus keyword. It integrates with WordPress, and this will help you write more SEO-friendly content.
You can also generate SEO templates and get easy search engine optimization suggestions for your content along with advanced SEO recommendations.
SEMRush seamlessly integrates with All in One SEO (AIOSEO) to help you find additional keyphrases for your focus keyphrase. You can see related keyphrases and their search volume right from WordPress. Then, you can add them to your content with the click of a button.
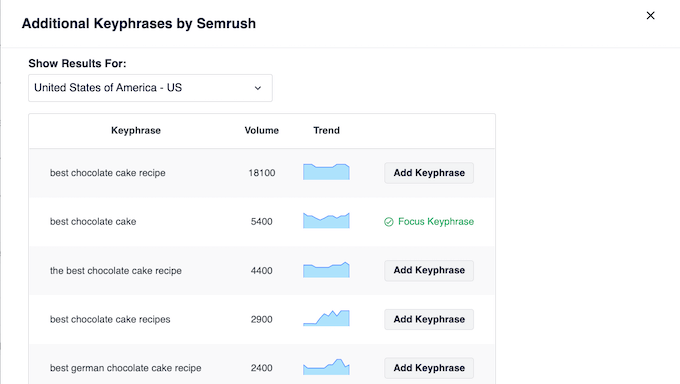
To learn more, see our complete guide on how to do keyword research for your website.
We use SEMRush for our websites because of their competitive intelligence and SEO rank tracker features.
3. Google Search Console
Google Search Console is a free tool offered by Google to help website owners and webmasters monitor and maintain their site’s presence in Google search results.
It alerts you when Google is unable to crawl and index pages on your website. You also get helpful tips on how to fix those crawl errors.
Most importantly, it shows which keywords your website is ranking for, anchor texts, average position, impressions, and more. You can use this data to find keywords where you can easily rank higher by simply optimizing your content. You can also use this keyword data to come up with new blog post ideas.
For more details, see our comprehensive Google Search Console guide for beginners.
Tip: You can use MonsterInsights to track your keyword rankings inside WordPress admin area using Google Seach Console data. We will cover this tool later in the article below.
4. Yoast SEO

Yoast SEO is a popular WordPress SEO plugin that allows you to optimize your WordPress website for search engines.
It lets you easily add SEO titles and descriptions to all posts and pages on your website. You can also use it to add Open Graph metadata and social media images to your articles.
Yoast SEO automatically generates an XML sitemap for all your website content which makes it easier for search engines to crawl your website. It also helps you easily import your SEO data if you have been using another SEO plugin.
Other features include readability analysis, Google and social previews, and faster load times for a better user experience.
For more details, see our complete guide on how to install and set up Yoast SEO plugin in WordPress.
5. Google Keyword Planner
Google Keyword Planner tool helps you generate your own keyword ideas from Google itself.
No one on the planet has more insights into what people are searching for than the search giant Google. This free tool is offered to Google’s advertisers for free and anyone can use it. Its main purpose is to show advertisers the keywords they can bid on for their advertising campaigns.
It also helps advertisers choose the right keywords by showing them an estimate of search volume, number of results, and difficulty level.
As a content marketer or blogger, you can use this data to find keywords with high search volume, high advertiser interest, and more importantly keywords where you can easily outrank all other sites.
Bonus: See these 103 Blog Post Ideas that your Readers will Love (Cheat Sheet).
6. Ahrefs

Ahrefs is an all-in-one SEO analysis tool for marketers, bloggers, and businesses. It is a popular alternative to SEMRush and offers a lot of similar tools and features.
It allows you to do keyword research, competition analysis, backlink research, SEO audit, monitor keyword rankings, and more.
It also offers a detailed content analysis tool that helps you improve content while targeting specific keywords.
While there’s a huge feature overlap, what Ahrefs does really well is backlink analysis. We can use it to see which sites are linking to multiple competitors, but not us. This helps us get more backlinks and build more partnerships.
They also help us identify which content multiple of our competitors are ranking for that we aren’t, so we can create content on those subjects to get more exposure.
Last but not least, Ahrefs helps us better identify duplicate content and keyword cannibalization which helps us merge and upgrade the right content to boost our rankings.
For the reasons above, we pay for both SEMRush and Ahrefs because they’re both good for specific use-cases.
7. SEOPress
SEOPress is another simple yet powerful WordPress SEO plugin. It includes all the features you would expect from an SEO plugin like meta title, description, open graph support, image and content XML sitemaps, redirects, and more.
It comes with a straightforward setup for beginners and advanced controls for more experienced users. It is comparable to other top WordPress SEO plugins on the market in terms of features and options.
The paid version of the plugin is cheaper than some other premium WordPress SEO plugins on the market.
Note: SEOPress is a WordPress SEO plugin. Remember, you only need one WordPress SEO plugin on your site.
8. Rank Math
Rank Math is another user-friendly WordPress SEO plugin that allows you to optimize your website for search engines and social media. It comes with a setup wizard and allows you to import data from other SEO plugins during the setup.
You can use it to easily add meta title, description, and Open Graph metadata to your blog posts. The plugin also allows you to generate an XML sitemap, connect Google Search Console, and control access to plugin features based on user roles.
Note: Rank Math is an AIOSEO alternative. Remember, you only need one WordPress SEO plugin on your site.
9. Schema Pro
Schema Pro allows you to add rich snippets to your website which makes it stand out in search results.
Rich Snippets allow you to make your website stand out in search results by showing star ratings below a review, prices below a product, image or video next to the description, and so on.
Top WordPress SEO plugins, like All in One SEO (AIOSEO) already add structured rich snippets data to your website. However, if you need more schema types or want to extend the functionality of your existing WordPress SEO plugin then Schema Pro is the way to go.
Schema Pro also allows you to use it alongside your existing WordPress SEO plugin by mapping the plugin data to Schema Pro fields.
10. KeywordTool.io
KeywordTool.io is one of the best free keyword research tools available right now. It allows you to simply generate keyword ideas by typing in a keyword. These keyword suggestions are gathered from Google’s autosuggest feature. It also shows you keyword suggestions from Bing, YouTube, Amazon, and more.
These keyword suggestions are a treasure of information. You can also get search volume, cost per click, and other data for each keyword by upgrading to their paid plan.
11. Redirection

Redirection helps you set up SEO friendly redirects in WordPress. It is a handy broken link checker that helps you easily fix 404 errors in WordPress by setting up redirects.
Broken links can affect your site’s SEO and create a bad experience for your users. If you have been running a blog for some time, then you should check your site from time to time for broken links and fix them.
There are multiple ways to easily find broken links in WordPress. Once you find a broken link, you may need to fix it by pointing users to the correct link or removing the incorrect link.
For more details, see our step by step guide on how to find and fix broken links in WordPress.
Alternative: AIOSEO Advanced Redirects is a powerful alternative to the Redirection plugin.
12. SEOQuake

SEOQuake is a useful SEO tool for website owners. It is available as a browser add-on for Google Chrome, Mozilla Firefox, Opera, and Safari web browsers.
It provides SEO related information for any website. This data includes page health, age, last updated, Alexa rank, and many other parameters. It is one of the most downloaded browser addons by SEO professionals.
Apart from that, the SEOQuake toolbar can show you all the same data search results when you type in a keyword. This information can be extremely useful if you are gauging competition for different keywords. You can even download search results in CSV format and prepare your own excel sheets of search data.
Alternative: Ahrefs SEO Toolbar
Bonus Plugins for WordPress Website Owners
These tools give you the additional advantage when optimizing your website for SEO. They do not advertise themselves as SEO tools but they are essential for every website and play a significant role in your website’s search performance.
13. WP Rocket

Site speed is a major factor in search rankings. That’s why you need to monitor your website speed & performance to make sure it’s not affecting your SEO.
The easiest way to boost your website speed is by enabling caching. WP Rocket is the best WordPress caching plugin on the market, which allows you to set up caching without diving into any technical stuff.
Alternative: WP Super Cache
14. MonsterInsights
Many beginners rely on their best guess to make their marketing decisions. You don’t need to do that when you can easily get the insights you need to improve your website’s SEO strategy.
MonsterInsights is the best Google Analytics plugin for WordPress. It allows you to easily install Google Analytics in WordPress and shows human-readable reports inside your WordPress dashboard.
It tells you where your users are coming from, your top content, what users do on your website, and more. It also allows you to track your eCommerce SEO by seeing which products are popular and where you are losing customers.
Bonus tip: See what other marketing data you must track on your website to grow your business.
Other Powerful Growth Tools:
Aside from the above plugins, we also recommend the following tools to increase your traffic and conversions from SEO visitors:
- PushEngage – connect and engage with SEO visitors after they leave your website with web push notifications.
- OptinMonster – convert abandoning visitors into email subscribers & customers.
- Constant Contact – stay in touch with SEO visitors through email marketing.
- WPForms – get more leads from your SEO traffic with #1 WordPress form builder.
- SeedProd – create SEO friendly custom landing pages with drag & drop WordPress page builder (no coding needed).
We hope this article helped you find the best WordPress SEO plugins and tools for your website. You may also want to see our proven tips to easily increase your website traffic, and our comparison of best chatbot software to boost conversions.
Source :
https://www.wpbeginner.com/showcase/9-best-wordpress-seo-plugins-and-tools-that-you-should-use/



![Global Corporate PPA Volumes - Chart [June 2022].jpg](https://storage.googleapis.com/gweb-cloudblog-publish/images/Global_Corporate_PPA_Volumes_-_Chart_June_.max-2000x2000.jpg)