CUPERTINO, CALIFORNIA Apple today previewed macOS Ventura, the latest version of the world’s most advanced desktop operating system, which takes the Mac experience to a whole new level. Stage Manager gives Mac users an all-new way to stay focused on the task in front of them while seamlessly switching between apps and windows. Continuity Camera uses iPhone as the webcam on Mac to do things that were never possible before,1 and with Handoff coming to FaceTime, users can start a FaceTime call on their iPhone or iPad and fluidly pass it over to their Mac. Mail and Messages come with great new features that make the apps better than ever, while Safari — the world’s fastest browser on Mac2 — ushers in a passwordless future with passkeys. And with the power and popularity of Apple silicon, and new developer tools in Metal 3, gaming on Mac has never been better.
“macOS Ventura includes powerful features and new innovations that help make the Mac experience even better. New tools like Stage Manager make focusing on tasks and moving between apps and windows easier and faster than ever, and Continuity Camera brings new videoconferencing features to any Mac, including Desk View, Studio Light, and more,” said Craig Federighi, Apple’s senior vice president of Software Engineering. “With helpful new features in Messages, state-of-the-art search technologies in Mail, and an updated design for Spotlight, Ventura has so much to offer and enriches many of the ways customers use their Macs.”
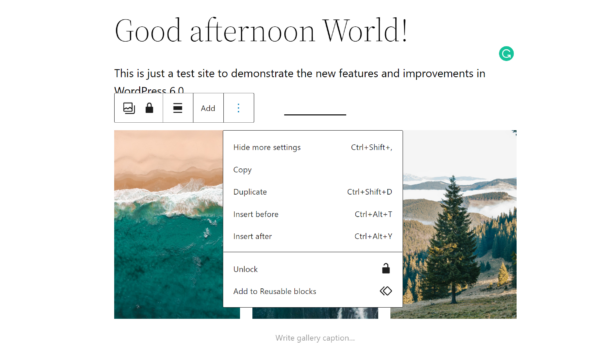
- The new Stage Manager feature stacking several app windows to the left of the Safari window on the 14-inch MacBook Pro.
- iPhone 13 Pro being used as a webcam with Continuity Camera on the new 13-inch MacBook Pro.


- previous
- next
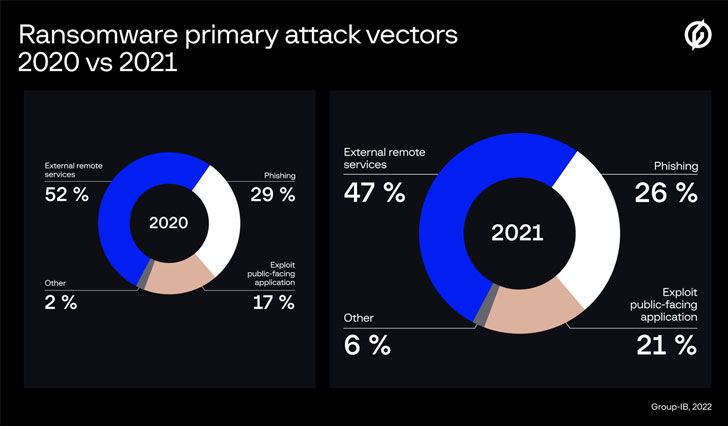
A New Way to Work Across Apps and Windows
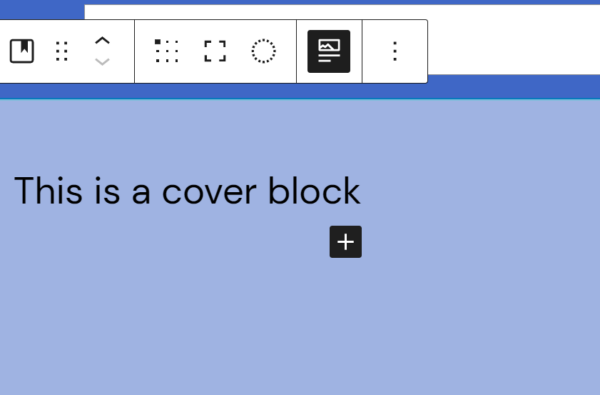
Stage Manager automatically organises open apps and windows so users can concentrate on their work and still see everything in a single glance. The current window users are working in is displayed prominently in the center, and other open windows appear on the left-hand side so they can quickly and easily switch between tasks. Users can also group windows together when working on specific tasks or projects that require different apps. Stage Manager works in concert with other macOS windowing tools — including Mission Control and Spaces — and users can now easily get to their desktop with a single click.
Pause playback of video: Stage Manager in macOS Ventura
Stage Manager automatically arranges open windows and puts the app the user is currently working with front and center.
Apple Devices Working Together with Continuity
Continuity Camera now gives Mac customers the ability to use their iPhone as a webcam, and unlocks new capabilities that were never possible before on a webcam. With the power of Continuity, Mac can automatically recognise and use the camera on iPhone when it is nearby — without the need to wake or select it — and iPhone can even connect to Mac wirelessly for greater flexibility.3 Continuity Camera delivers innovative features to all Mac computers including Center Stage, Portrait mode, and the new Studio Light — an effect that beautifully illuminates a user’s face while dimming the background. Plus, Continuity Camera taps into the Ultra Wide camera on iPhone to enable Desk View, which simultaneously shows the user’s face and an overhead view of their desk — great for creating DIY videos, showing off sketches over FaceTime, and so much more.4

Handoff now comes to FaceTime, allowing users to start a FaceTime call on one Apple device and seamlessly transfer it to another Apple device nearby. Users can be on a FaceTime call on iPhone or iPad, then move the call to their Mac with just a click, or start a call on their Mac and shift to iPhone or iPad when they need to continue on the go.
Powerful Updates to Key macOS Apps and Features
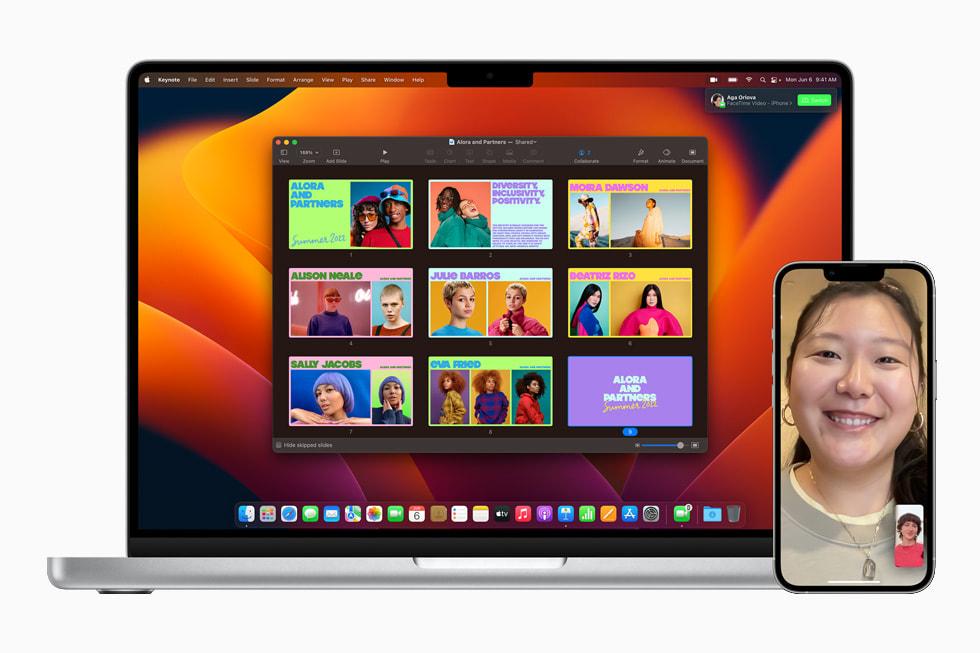
Safari offers the fastest and most power-efficient browsing experience on the Mac, along with trailblazing privacy features. In macOS Ventura, Safari introduces a powerful new way for users to browse together: With shared Tab Groups, friends, family, and colleagues can share their favorite sites in Safari and see what tabs others are looking at live. Users can also build a list of bookmarks on a shared Start Page, and even start a Messages conversation or FaceTime call right from Safari — great for planning a trip or researching a project together.
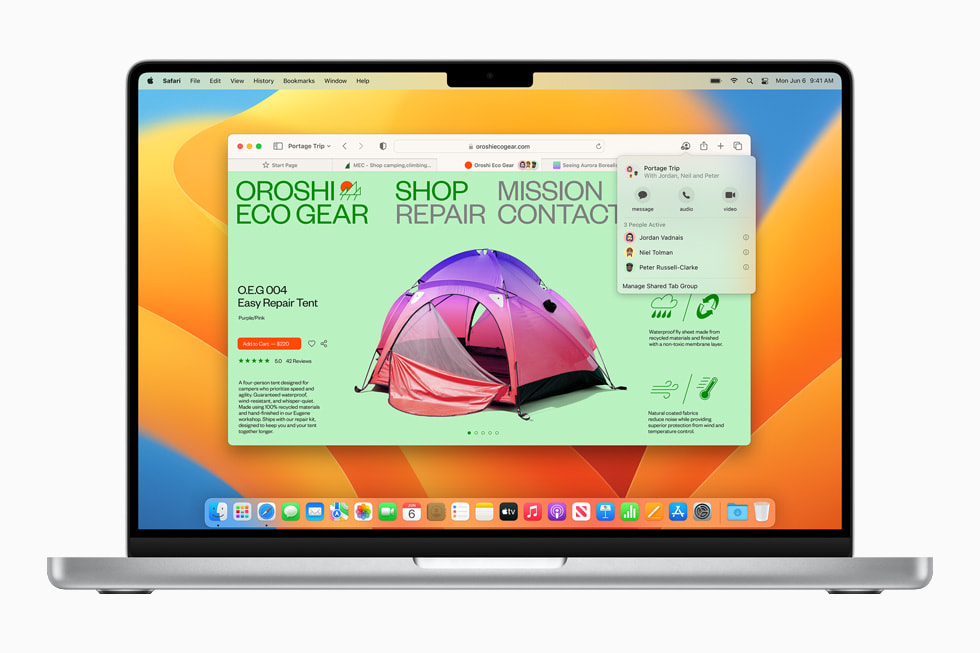
In the biggest overhaul to search in years, Mail now uses state-of-the-art techniques to deliver more relevant, accurate, and complete results. Users can quickly find what they are looking for as soon as they click into search, including recent emails, contacts, documents, photos, and more, all before they even start typing. Users can also schedule emails and even cancel delivery after hitting send,5 and Mail now intelligently detects if items such as an attachment or cc’d recipient is missing from their message. In Mail, users can set reminders to come back to a message at a particular date and time, and receive automatic suggestions to follow up on an email if there has been no response.
- The new search results in Mail displayed on MacBook Pro.
- The new scheduling feature in Mail displayed on MacBook Pro.
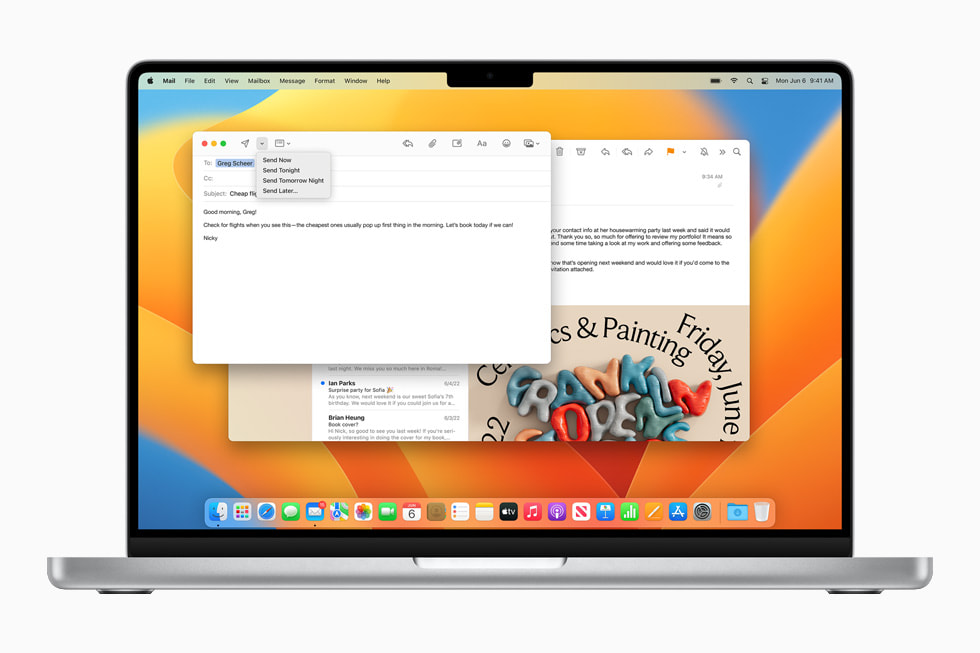
- previous
- next
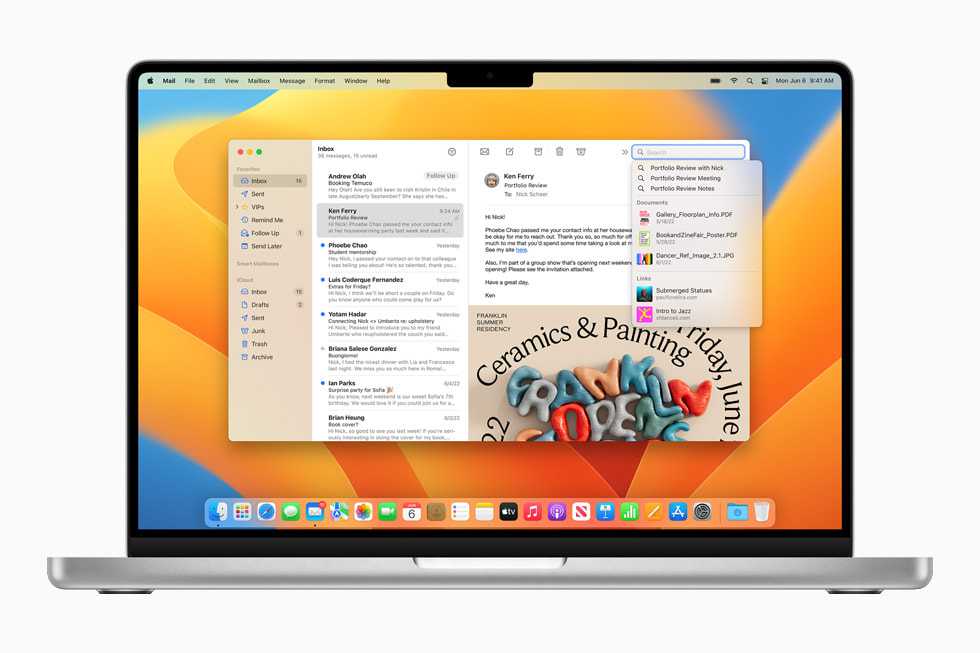
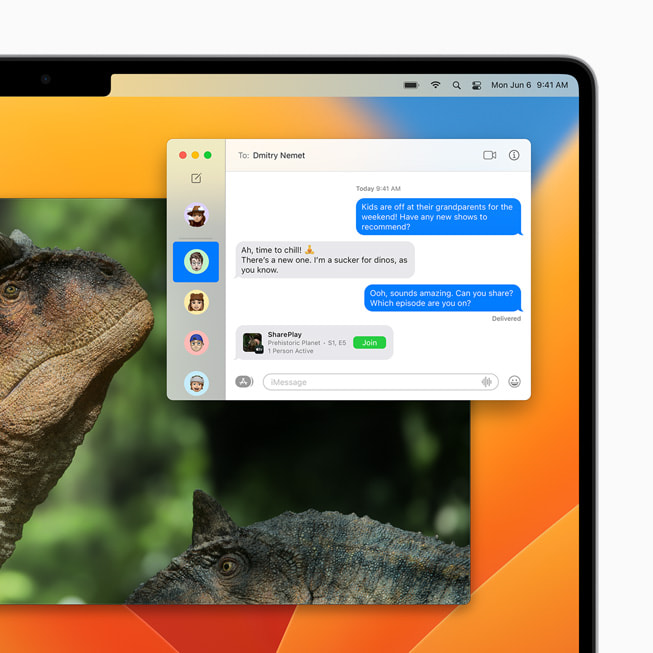
Messages on the Mac now includes the ability to edit or undo a recently sent message, mark a message as unread, or even recover accidentally deleted messages.6 New collaboration features make working with others quick and seamless. Now, when a user shares a file via Messages using the share sheet or drag and drop, they can choose to share a copy or collaborate. When they choose to collaborate, everyone on a Messages thread is automatically added. And when someone makes an edit to the shared document, activity updates appear at the top of the thread. Users can also join SharePlay sessions from their Mac right in Messages, so they can chat and participate in synchronised experiences.
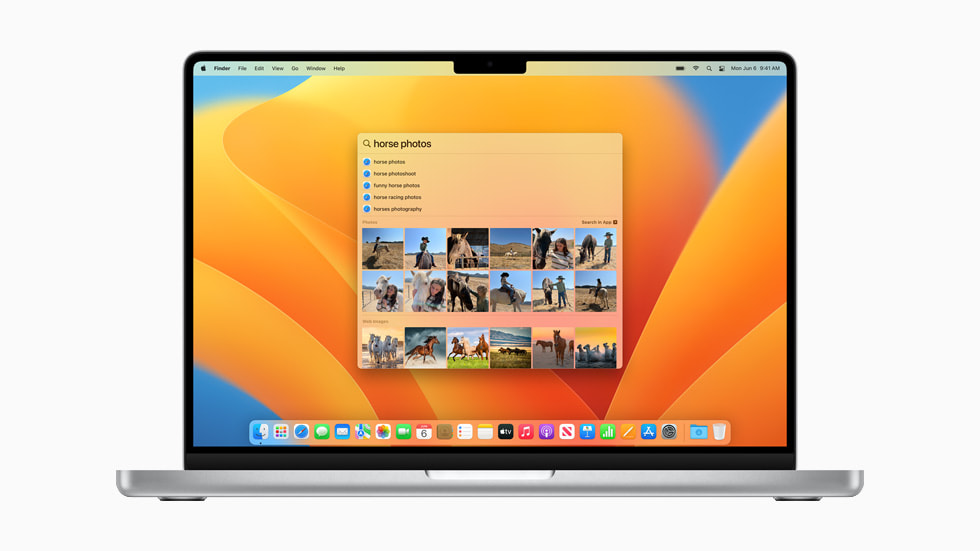
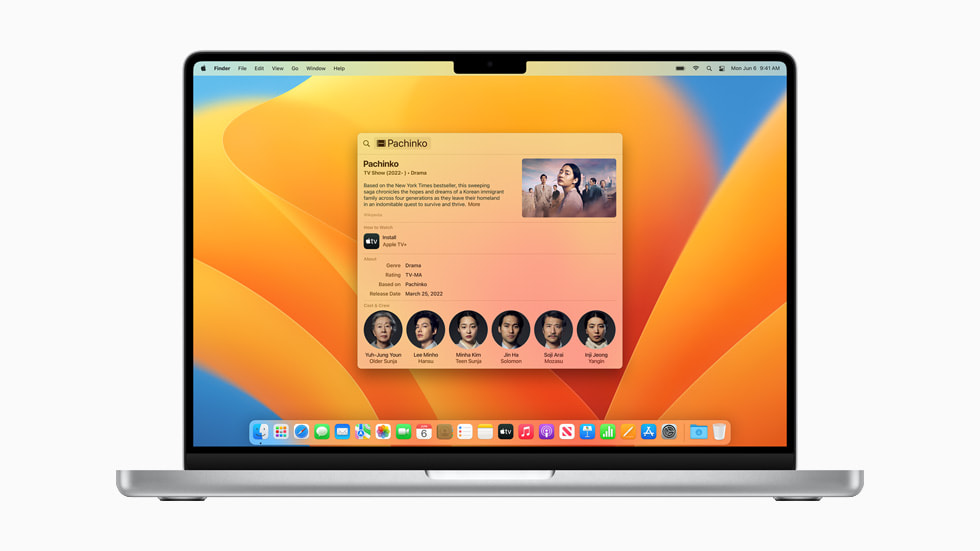
Spotlight includes an updated design that makes navigation easier, new features that provide a more consistent experience across Apple devices, and Quick Look for quickly previewing files. Users can now find images in their photo library, across the system, and on the web. They can even search for their photos by location, people, scenes, or objects, and Live Text lets them search by text inside images. To be even more productive, users can now take actions from Spotlight, like starting a timer, creating a new document, or running a shortcut. And Spotlight now includes rich results for artists, movies, actors, and TV shows, as well as businesses and sports.
- Spotlight search results across iPad and MacBook Pro.
- The new photo search experience in Spotlight on MacBook Pro.
- The new search results for a TV show in Spotlight on MacBook Pro.

- previous
- next
With iCloud Shared Photo Library, users can now create and share a separate photo library among up to six family members, so everyone can enjoy all of their family photos. Users can choose to share all of their existing photos from their personal libraries, or share based on a start date or people in the photos. To help keep their Shared Library up to date, users will receive intelligent suggestions to share relevant photo moments that include participants in the library and any other people they choose. Every user in the Shared Photo Library can add, delete, edit, or favorite the shared photos and videos, which will appear in each user’s Memories and Featured Photos so that everyone can relive more complete family moments.
More Secure Browsing in Safari
Browsing in Safari is even safer with passkeys, next-generation credentials that are more secure, easy to use, and designed to replace passwords. Passkeys are unique digital keys that stay on device and are never stored on a web server, so hackers can’t leak them or trick users into sharing them. Passkeys make it simple to sign in securely, using Touch ID or Face ID for biometric verification, and iCloud Keychain to sync across Mac, iPhone, iPad, and Apple TV with end-to-end encryption. They will also work across apps and the web, and users can even sign in to websites or apps on non-Apple devices using their iPhone.

Immersive Gaming Experiences
The power of Apple silicon enables every new Mac to run AAA games with ease, including upcoming titles such as EA’s GRID Legends and Capcom’s Resident Evil Village. And since Apple silicon also powers iPad, game developers can bring their AAA games to even more users, like No Man’s Sky from Hello Games, which is coming to both Mac and iPad later this year.
Metal 3, the latest version of the software that powers the gaming experience across Apple platforms, introduces new features that take the gaming experience on Mac to new heights and unleash the full potential of Apple silicon for years to come. MetalFX Upscaling enables developers to quickly render complex scenes by using less compute-intensive frames, and then apply resolution scaling and temporal anti-aliasing. The result is accelerated performance that provides gamers with a more responsive feel and graphics that look stunning. Game developers also benefit from a new Fast Resource Loading API that minimizes wait time by providing a more direct path from storage to the GPU, so games can easily access high-quality textures and geometry needed to create expansive worlds for realistic and immersive gameplay.
Pause playback of video: Gaming with Metal 3
Metal 3 brings new features that unleash the full potential of Apple silicon for even greater gaming experiences.
More Great Experiences Coming with macOS Ventura
- Live Text uses on-device intelligence to recognise text in images across the system, and now adds support for paused video frames, as well as Japanese and Korean text. Users can also now lift the subject away from an image and drop it into another app. And Visual Look Up expands its recognition capabilities to now include animals, birds, insects, statues, and even more landmarks.
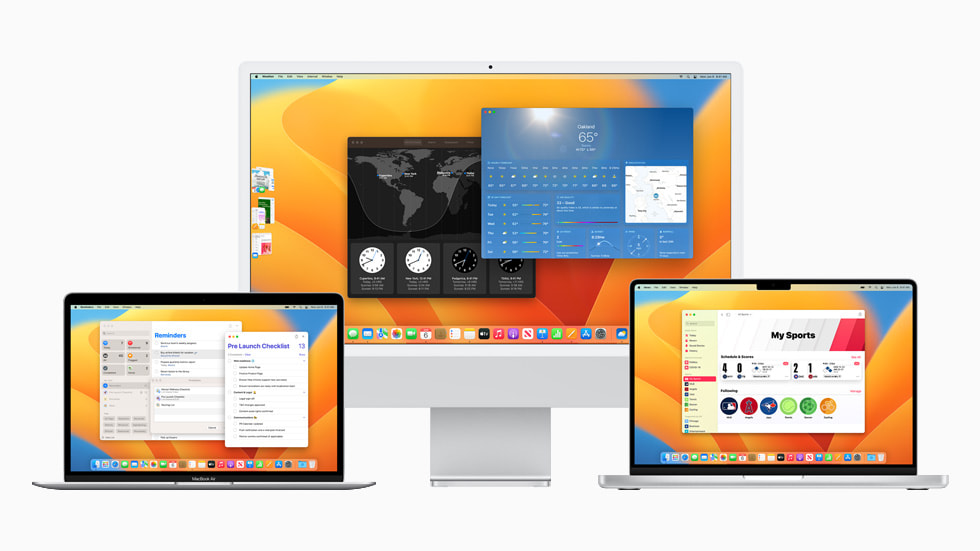
- The Weather and Clock apps, with all the features users know and love from iPhone, have been optimized for Mac.
- New accessibility tools include Live Captions for all audio content, Type to Speak on calls, Text Checker to support proofreading for VoiceOver users, and more.7
- System Settings is the new name for System Preferences, and comes with a refreshed and streamlined design that is easier to navigate and instantly familiar to iPhone and iPad users.
- macOS security gets even stronger with new tools that make the Mac more resistant to attack, including Rapid Security Response that works in between normal updates to easily keep security up to date without a reboot.
Availability
The developer beta of macOS Ventura is available to Apple Developer Program members at developer.apple.com starting today. A public beta will be available to Mac users next month at beta.apple.com. macOS Ventura will be available this fall as a free software update. For more information, including compatible Mac models, visit apple.com/in/macos/macos-ventura-preview. Features are subject to change. Some features may not be available in all regions or languages.
Source :
https://www.apple.com/in/newsroom/2022/06/macos-ventura-brings-powerful-productivity-tools-new-continuity-features-to-mac/