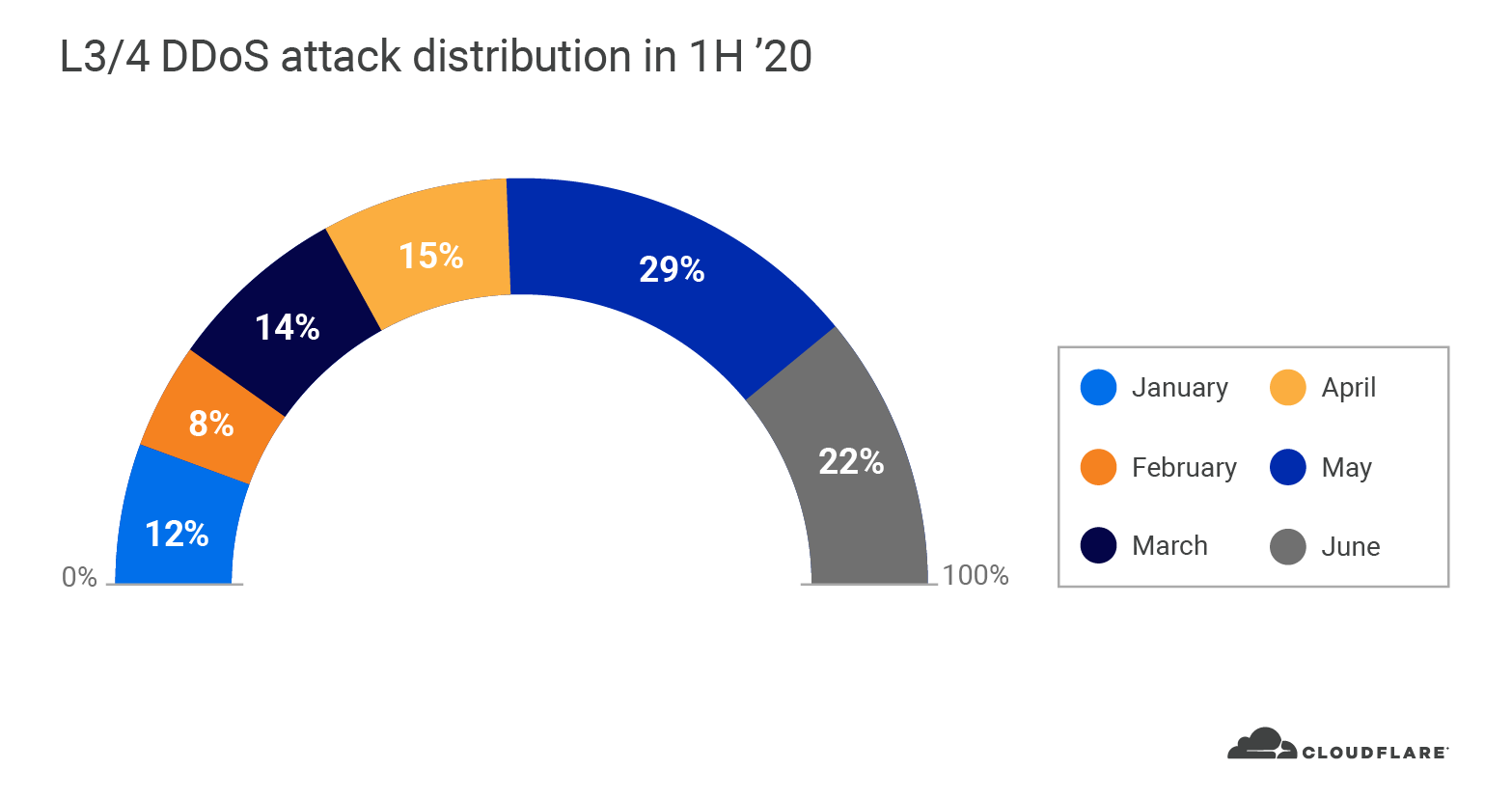
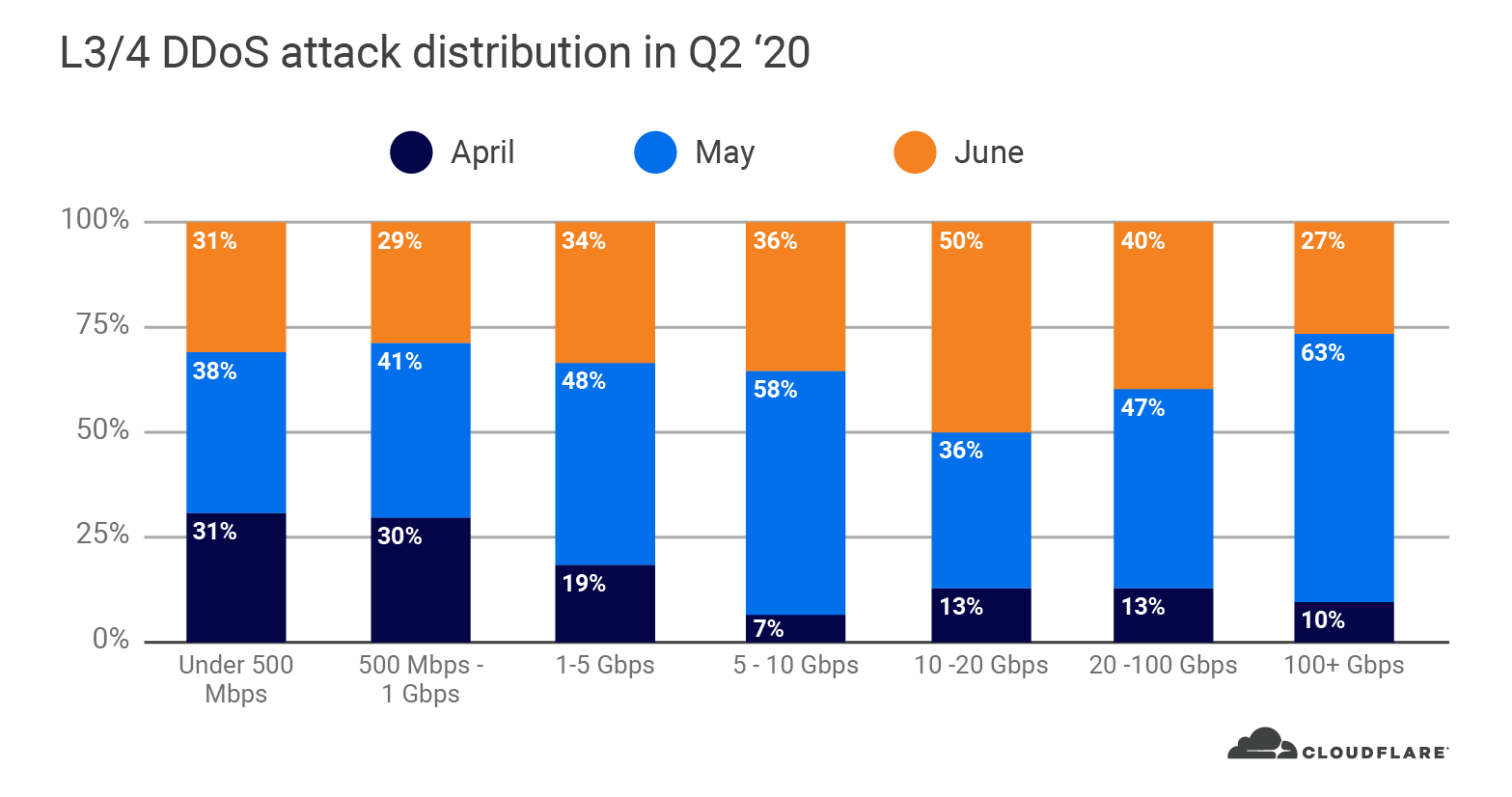
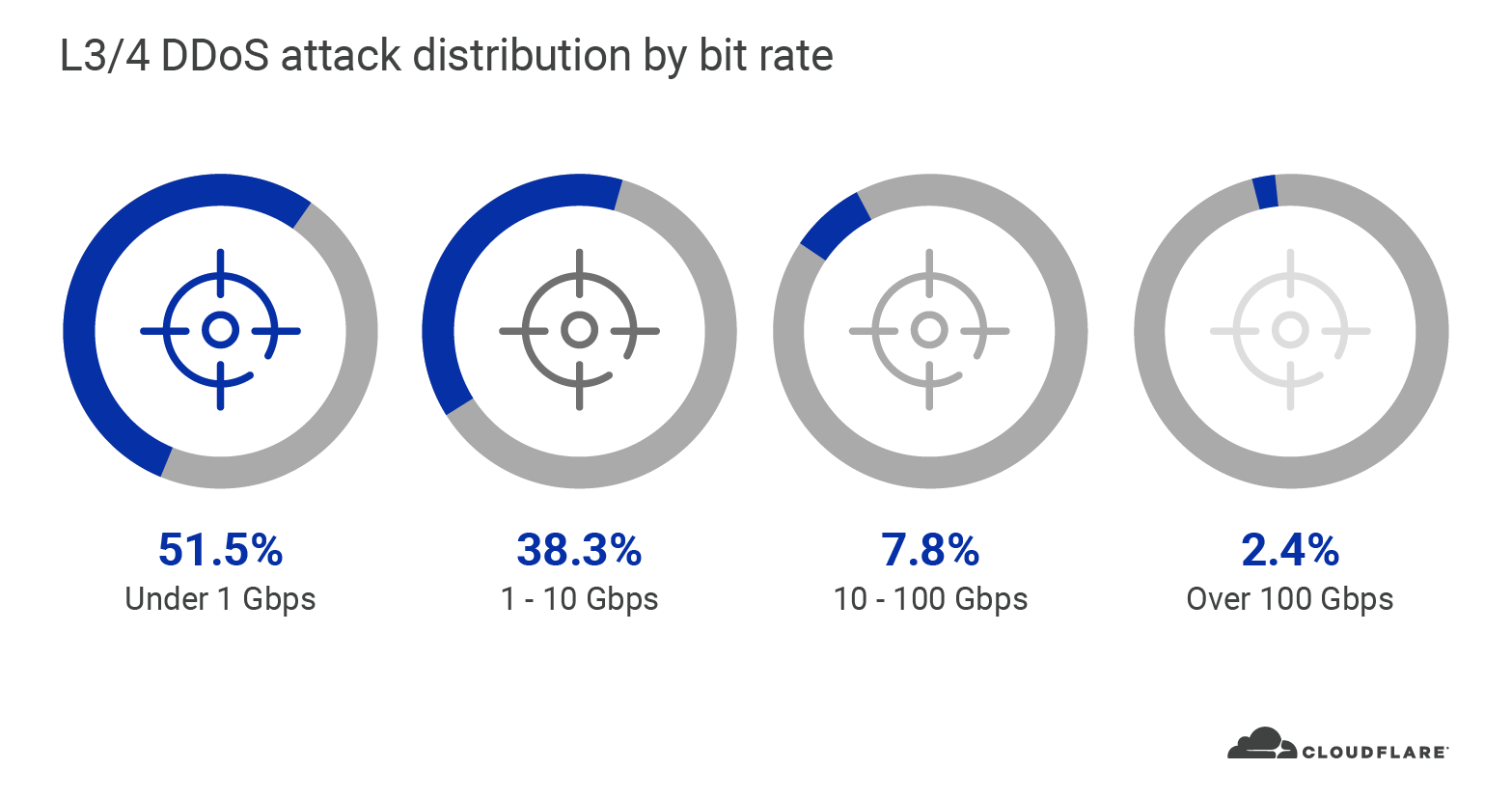
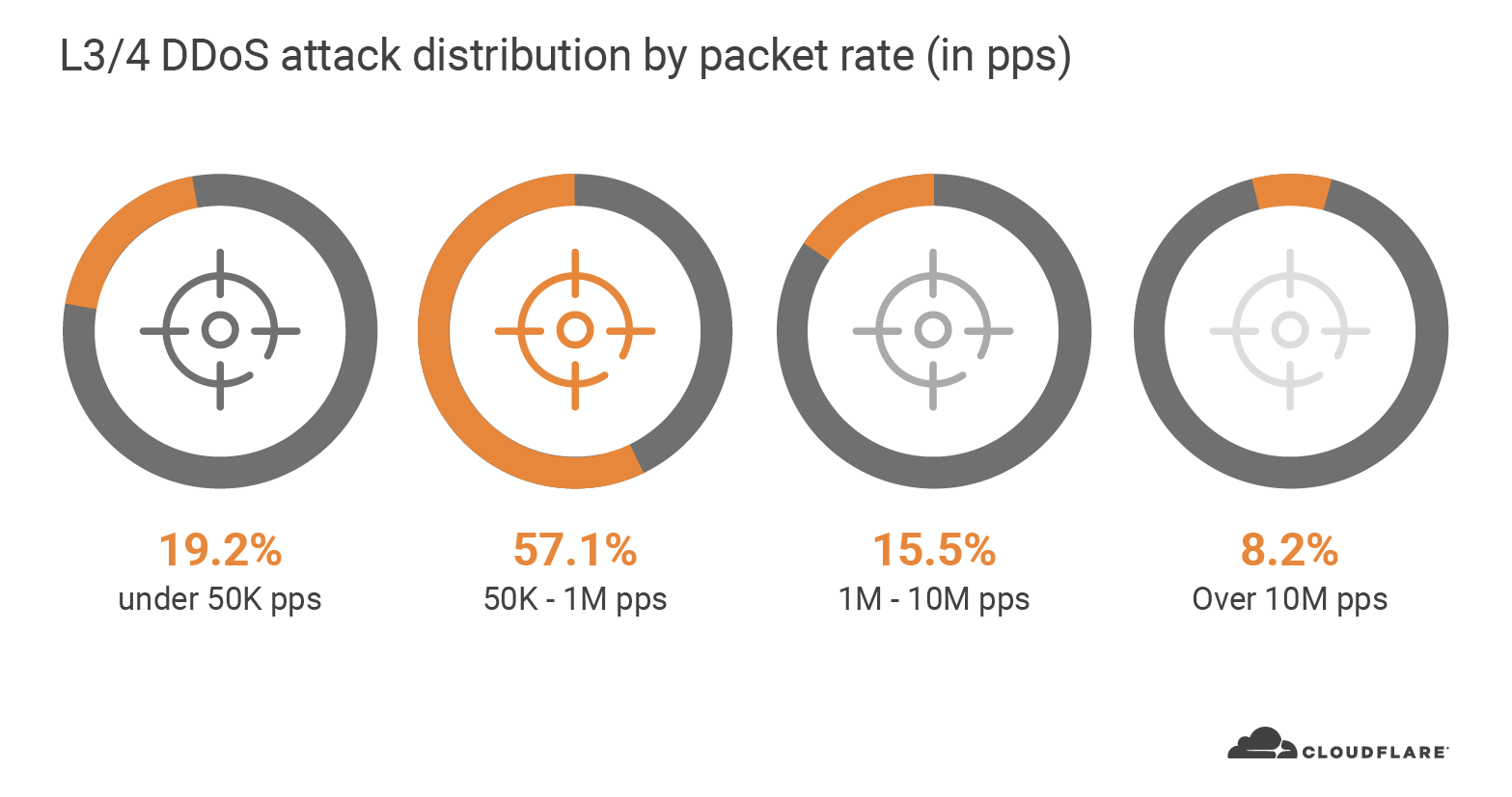
We’ve all been spending more of our time online since the crisis hit. Whether it’s ordering food for delivery, livestreaming concerts, holding virtual parties, or engaging in a little retail therapy, the digital interactions of many Americans are on the rise. This means we’re also sharing more of our personal and financial information online, with each other and the organizations we interact with. Unfortunately, as ever, there are bad guys around every digital corner looking for a piece of the action.
The bottom line is that personally identifiable information (PII) is the currency of internet crime. And cyber-criminals will do whatever they can to get their hands on it. When they commit identity theft with this data, it can be a messy business, potentially taking months for banks and businesses to investigate before you get your money and credit rating back. At a time of extreme financial hardship, this is the last thing anyone needs.
It therefore pays to be careful about how you use your data and how you protect it. Even more: it’s time to get proactive and monitor it—to try and spot early on if it has been stolen. Here’s what you need to know to protect your identity data.
How identity theft works
First, some data on the scope of the problem. In the second quarter of 2020 alone 349,641 identity theft reports were filed with the FTC. To put that in perspective, it’s over half of the number for the whole of 2019 (650,572), when consumers reported losing more than $1.9 billion to fraud. What’s driving this huge industry? A cybercrime economy estimated to be worth as much as $1.5 trillion annually.
Specialized online marketplaces and private forums provide a user-friendly way for cyber-criminals and fraudsters to easily buy and sell stolen identity data. Many are on the so-called dark web, which is hidden from search engines and requires a specialized anonymizing browser like Tor to access. However, plenty of this criminal activity also happens in plain sight, on social media sites and messaging platforms. This underground industry is an unstoppable force: as avenues are closed down by law enforcement or criminal in-fighting, other ones appear.
At-risk personal data could be anything from email and account log-ins to medical info, SSNs, card and bank details, insurance details and much more. It all has a value on the cybercrime underground and the price fraudsters are prepared to pay will depend on supply and demand, just like in the ‘real’ world.
There are various ways for attackers to get your data. The main ones are:
| Phishing: usually aimed at stealing your log-ins or tricking you into downloading keylogging or other info-stealing malware. Phishing mainly happens via email but could also occur via web, text, or phone. Around $667m was lost in imposter scams last year, according to the FTC.Malicious mobile apps disguised as legitimate software.Eavesdropping on social media: If you overshare even innocuous personal data (pet names, birth dates, etc.,) it could be used by fraudsters to access your accounts.Public Wi-Fi eavesdropping: If you’re using it, the bad guys may be too.Dumpster diving and shoulder surfing: Sometimes the old ways are still popular.Stealing devices or finding lost/misplaced devices in public places.Attacking the organizations you interact with: Unfortunately this is out of your control somewhat, but it’s no less serious. There were 1,473 reported corporate breaches in 2019, up 17% year-on-year.Harvesting card details covertly from the sites you shop with. Incidents involving this kind of “web skimming” increased 26% in March as more users flocked to e-commerce sites during lockdown. | |
The COVID-19 challenge
As if this weren’t enough, consumers are especially exposed to risk during the current pandemic. Hackers are using the COVID-19 threat as a lure to infect your PC or steal identity data via the phishing tactics described above. They often impersonate trustworthy institutions/officials and emails may claim to include new information on outbreaks, or vaccines. Clicking through or divulging your personal info will land you in trouble. Other fraud attempts will try to sell counterfeit or non-existent medical or other products to help combat infection, harvesting your card details in the process. In March, Interpol seized 34,000 counterfeit COVID goods like surgical masks and $14m worth of potentially dangerous pharmaceuticals.
Phone-based attacks are also on the rise, especially those impersonating government officials. The aim here is to steal your identity data and apply for government emergency stimulus funds in your name. Of the 349,641 identity theft reports filed with the FTC in Q2 2020, 77,684 were specific to government documents or benefits fraud.
What do cybercriminals do with my identity data?
Once your PII is stolen, it’s typically sold on the dark web to those who use it for malicious purposes. It could be used to:
| Crack open other accounts that share the same log-ins (via credential stuffing). There were 30 billion such attempts in 2018.Log-in to your online bank accounts to drain it of funds.Open bank accounts/credit lines in your name (this can affect your credit rating).Order phones in your name or port your SIM to a new device (this impacts 7,000 Verizon customers per month).Purchase expensive items in your name, such as a new watch or television, for criminal resale. This is often done by hijacking your online accounts with e-tailers. E-commerce fraud is said to be worth around $12 billion per year.File fraudulent tax returns to collect refunds on your behalf.Claim medical care using your insurance details.Potentially crack work accounts to attack your employer. | |
How do I protect my identity online?
The good news among all this bad is that if you remain skeptical about what you see online, are cautious about what you share, and follow some other simple rules, you’ll stand a greater chance of keeping your PII under lock and key. Best practices include:
| Using strong, long and unique passwords for all accounts, managed with a password manager.Enable two-factor authentication (2FA) if possible on all accounts.Don’t overshare on social media.Freeze credit immediately if you suspect data has been misused.Remember that if something looks too good to be true online it usually is.Don’t use public Wi-Fi when out-and-about, especially not for sensitive log-ins, without a VPN.Change your password immediately if a provider tells you your data may have been breached.Only visit/enter payment details into HTTPS sites.Don’t click on links or open attachments in unsolicited emails.Only download apps from official app stores.Invest in AV from a reputable vendor for all your desktop and mobile devices.Ensure all operating systems and applications are on the latest version (i.e., patch frequently).Keep an eye on your bank account/credit card for any unusual spending activity.Consider investing in a service to monitor the dark web for your personal data. | |
How Trend Micro can help
Trend Micro offers solutions that can help to protect your digital identity.
Trend Micro ID Security is the best way to get proactive about data protection. It works 24/7 to monitor dark web sites for your PII and will sound the alarm immediately if it finds any sign your accounts or personal data have been stolen. It features
| Dark Web Personal Data Manager to scour underground sites and alert if it finds personal info like bank account numbers, driver’s license numbers, SSNs and passport information.Credit Card Checker will do the same as the above but for your credit card information.Email Checker will alert you if any email accounts have been compromised and end up for sale on the dark web, allowing you to immediately change the password.Password Checker will tell you if any passwords you’re using have appeared for sale on the dark web, enabling you to improve password security. | |
Trend Micro Password Manager enables you to manage all your website and app log-ins from one secure location. Because Password Manager remembers and recalls your credentials on-demand, you can create long, strong and unique passwords for each account. As you’re not sharing easy-to-remember passwords across multiple accounts, you’ll be protected from popular credential stuffing and similar attacks.
Finally, Trend Micro WiFi Protection will protect you if you’re out and about connecting to WiFi hotspots. It automatically detects when a WiFi connection isn’t secure and enables a VPN—making your connection safer and helping keep your identity data private.
In short, it’s time to take an active part in protecting your personal identity data—as if your digital life depended on it. In large part, it does.
Source :
https://blog.trendmicro.com/identity-fraud-how-to-protect-your-identity-data-accounts-and-money-during-the-coronavirus-crisis/