No matter how big or small your WordPress site, unwanted WordPress spam in comments sections, site registrations and contact form messages are issues that you’ll need to address.
Left unchecked, WordPress spam comments and spam user registration issues can quickly take over your site with intrusive content that detracts from the message your site is intended to portray.
In this guide, we’ll take you step-by-step through the process of stopping WordPress comment spam. You’ll also learn the best ways to prevent spam registration WordPress messages, end spam user registration efforts, stop WordPress contact form spam, and a lot more. Let’s take a closer look.In This Guide:
- What Is WordPress Spam?
- WordPress Contact Form Spam Explained
- WordPress User Registration Spam Explained
- WordPress Comment Spam Explained
- More Powerful WordPress Spam Protection Techniques
- Make Spam on WordPress a Problem of the Past
What Is WordPress Spam?
Spam has been an annoying, and often serious issue since the Internet became a staple in our lives. In the early days of being online, we became familiar with spam when unsolicited messages started to overtake our email inboxes, promoting everything from car insurance to cheap vacations. In fact, you probably continue to deal with this kind of unwanted spam every time you log into your email.
When discussing the spam that bombards a WordPress website, it’s a more multi-faceted subject than traditional email spam.
In a nutshell, WordPress spam attacks happen in many forms. As a WordPress site owner, chances are that you’ve dealt with these 3 types of WordPress spam:
- Comment spam
- User registration spam,
- Contact form spam
While these WordPress spam attempts are, of course, highly annoying to both you and your site visitors, it’s important to understand that there are also some major security components that are tied to the spam you’re experiencing.

While attacking and defeating WordPress spam head-on might seem like an overwhelming task, protecting your site actually isn’t that difficult. All you need is the right approach and the best tools.
With the many different types of spam attacks happening on WordPress, it’s important to understand the different approaches that spammers take. Then we’ll look at the specific tools and tips that will allow you to take full control of the problem.
WordPress Contact Form Spam Explained
For most websites, a contact form is an absolute necessity. Contact forms help facilitate communication between you and your site visitors in a way that’s streamlined and user-friendly.
However, spammers see your contact form as a way to further promote their agenda.
WordPress contact form spam is different than other types of spam that attack your site. This is because your contact form requires the use of a plugin, unlike site registrations and comments that are natively built-in to your WordPress core installation.
When employing a contact form, you can choose from popular WordPress forms plugins such as Gravity Forms, Ninja Forms, or Contact Form 7. Just as each of these contact form plugins has its own unique set of features, they also employ different ways of eliminating WordPress contact form spam.
The specific features to protect your site from spam will be found in the settings of the plugin you choose. In some cases, you may need to download and install a companion plugin for full spam protection.
More on that later.
How To Stop WordPress Contact Form Spam
While the annoyance factor of receiving contact form spam emails is high, the solution for stopping them dead in their tracks is quite simple.
The first thing you’ll want to do is install a WordPress spam blocker plugin like Askismet.
If you’re using WPBruiser or Akismet, it’s good to know that either one is ready to work in unison with a wide variety of WordPress contact form plugins. In fact, Akismet will work directly out-of-the-box with Jetpack, Ninja Forms, Gravity Forms and Contact Form 7.
Conversely, WPBruiser is a little different in the way it combats WordPress contact form spam. WPBruiser requires a commercial extension in order to work with your WordPress contact form plugin.
With that said, WPBruiser has a much wider range than Akismet for spam protection options on plugins such as Formidable Forms, Fast Secure Contact Form, and the other popular contact form plugins detailed above.
Additionally, you’ll get a free Jetpack contact form extension in the core WPBruiser plugin installation.
No matter the contact form plugin you’re using, Akismet and WPBruiser will use robust spam blocking tools to help keep your contact forms safe from unwanted spam messages.
WordPress User Registration Spam Explained
The WordPress user registration feature is built directly into WordPress core.
The user registration feature is extremely useful for:
- Membership sites
- Online communities
- eCommerce site customer accounts
Unfortunately, spam user registration is an area where spammers can easily focus their bots on malicious spam attacks. To prevent spam registration WordPress issues, it’s important to look at the root of the problem. WordPress stop spam registrations begins there.
A spam user registration consists of a phony site registration by spam bots that intend on spreading their message throughout your site. These spam user registrations will often lead to spam comments in your blog. They can even lead to more malicious attacks involving site security or a cluttered site with an unwanted front-facing membership directory.
What’s more, many WordPress plugins and themes have security vulnerabilities that can allow low-level site users, such as subscribers, to garner access to the administrative settings on your site. This is an important reason to prevent spam registrations WordPress is infamous for.
While the security flaws in themes and plugins typically require a spammer to work in a roundabout method to exploit the built-in vulnerabilities, it’s important to understand that even the most dormant-looking WordPress user registration spam account could be waiting and ready to exploit your site at any time.
Understanding the need to prevent spam registration WordPress attacks is the first step to solving the issue. Then, it’s time to employ a robust spam user registration blocker to put the issue to rest.
The aforementioned WPBruiser plugin will go a long way toward preventing WordPress user registration spam. It’s your first layer of defense in the WordPress stop spam registrations game.
However, there are a few other simple steps you should take in the WordPress stop spam registrations battle. Make sure to read this guide until the end for full details.
WordPress Comment Spam Explained
When you use the built-in WordPress comment section on your website, you’re automatically inviting conversation from users and readers.
Unfortunately, you’re also inviting a bunch of unwanted spam comments. These spam comments distract users from meaningful conversations about your content and severely muddy the overall experience for the user.
As discussed, spambots are constantly looking to exploit vulnerabilities in your WordPress security, which is a major reason to download and install the best WordPress security plugin.
But these same bots also search out and exploiting your comments section in a very malicious way. If you leave your site unprotected, the spambots will litter your entire site with more nonsense comments than you can keep up with. And they can do it in an extremely short timeframe.
WordPress Comment Spam Examples
WordPress comment spam, aside from the obvious blatant advertisements or garbled-up characters that don’t make sense, should quickly stand out to you because they’re highly complementary, but don’t contain any specific information or questions.
For example, you may see WordPress spam comments that read something like:
“Great blog you’ve got here! Beyond that, your website loads quickly and is easy to use. What site host do you use? Would it be possible to get your affiliate link to the host you use? I really wish my site would load as fast as yours. This is great $4/month hosting with a free domain and SSL, if you’re interested.”
“It looks like you’ve really thought through all of what you’ve presented in this post. Your words are very convincing and I think they’ll work. Even still, the posts your write are perfect for newbies. I do think that you should lengthen your future posts a bit. But thank you for this one.”
“I’m a frequent blogger and sincerely appreciate the information you’ve presented. The article really piqued my interest from the very first word. I just bookmarked your site and will check back for new content once every week. I also subscribed to your RSS feed.”
As you can see, these types of comments are very general and don’t address anything specific about your content. Once you understand this very obvious WordPress comment spam technique, they become quite easy to spot.

You may also see lots of question marks in a spam comment. Lots of question marks are a good indicator of spam.
Is Having a Comment Section On WordPress Worth the Trouble?
The easiest and most effective way to immediately put a stop to WordPress comment spam is to simply turn off the commenting function. If you’re not committed to keeping up with user comments, this is the best way to be free from spam comments cluttering up your site.
To turn off comments on individual posts and pages, you can do so from Post or Page settings. Scroll down to the Discussion section.

There are also several comment disabling options from the WordPress dashboard > Settings > Discussion page. From this screen, you can enable additional settings that can help curb comment spam, like requiring users to register to comment.
The WordPress comment moderation field on this page also allows you to set certain words or even IP addresses that will flag a comment to be held in the comment moderation queue, meaning the comment won’t automatically go live on your site.

That said, there are many different types of WordPress sites that have a need for a live and active comments section. This is especially true for blog sites that are content-based and thrive with heavy user interaction.
If your website falls under that category, the first thing you need to do is stop the spam comments from overtaking your little slice of the online world.
Stopping spam comments is going to take a healthy combination of plugins, along with some common sense spam administrative practices.
To start out, the default WordPress settings for the comment section (Settings > Discussion) can easily be adjusted to limit the harm that comment spammers do. When you look under the “Other Comment Settings” heading, it’s important to check the box next to “Automatically close comments on posts older than ___ days,” and “Users must be registered and logged in to comment.”
These are fast resolutions that’ll cut down on your WordPress comment spam immediately.
How to Stop WordPress Spam Comments
If you’ve chosen to make your comments active, the next best thing to do is install a WordPress spam blocker plugin. The plugins you can use for this purpose typically require very little in terms of ongoing maintenance and are quite simple to use.
After the initial setup process, these tools will do their job to keep you from dealing first-hand with the spam that continually bombards your comments.
1. Use a Spam Blocker Plugin like Akismet
Akismet is the first spam blocker to look at for preventing spam comments. It’s one of the few default plugins that come in every installation of WordPress core. Because of this, many WordPress users find Akismet to be one of the best WordPress spam blockers for comment section spam.https://wordpress.org/plugins/akismet/embed/#?secret=2x8NVUsWwL#?secret=Mm1J0eHr1Y
The Askismet plugin works 24 hours per day to filter out any potential spam comments and set questionable ones aside for your moderation. But beyond that, Akismet has a discard feature that automatically blocks out all known spam, which saves you the time and hassle of ever seeing it.
While Akismet does offer a free spam comment blocking feature, it’s important to note that your protection is normally only as good as what you’re willing to pay for. If you’re running a personal site or blog with relatively low traffic, you should be able to get away with running on the free plan.
If, however, your site is for business and pulls in a lot of traffic and comments, it’s best to upgrade to one of the paid commercial protection plans. The paid plans for commercial and business sites begin at only $5 per month. That small fee is more than worth it when you consider the amount of spam that you’ll never need to deal with.
WPBruiser is another option for fully ridding your comments section of unwanted spam posts.
With the WPBruiser application, you’ll get a customizable and free WordPress comment spam blocker plugin that doesn’t rely on any other third-party services. In other words, you won’t need to fumble around with API keys or open your site up to additional privacy or security concerns.
This plugin creates a comment blacklist, which prevents spam bots from even submitting comments at all. You can also set the plugin to clear out your logs after a specified period of time, and it won’t slow down your site like some other spam plugins.
More Powerful WordPress Spam Protection Techniques
To prevent spam registrations WordPress gives us several more options. WordPress user registration spam, comment spam and contact form spam are all enemies of running a successful WordPress website.
1. WordPress CAPTCHA or reCAPTCHA
While we’ve already covered WordPress stop spam registrations techniques and know how to prevent spam registration WordPress is infamously famous for, putting a complete end to spam requires implementing a CAPTCHA.
The best way to do this is by using the iThemes Security Pro plugin to add a WordPress reCAPTCHA to all user comments, user registrations, password resets and logins. This is an incredibly effective tool that determines exactly what a bot is and who your real users are.
To get started using Google reCAPTCHA, enable the option on the main page of the security settings.

The next step is to select which version of reCAPTCHA you want to use and generate your keys from your Google admin.Note: We recommend using reCAPTCHA v3. We cover each of the 3 versions in more detail in the Understanding Different reCAPTCHA versions section.)

Now enable reCAPTCHA on your WordPress user registration, reset password, login, and comments.

Finally, set the number of failed reCAPTCHAs need to trigger a lockout with the Lockout Error Threshold.

Selecting different versions of reCAPTCHA will display different settings.
2. Honeypots
Another helpful idea for throwing bots off your tail is to create a “honeypot field.” This is a form that’s hidden within your page’s code and is invisible to any real people that browse your WordPress site.
However, it attracts spambots.
They view it as another contact form or field to clutter up with spam messages.
The idea with this technique is that the bots will fill out the honeypot field, unaware that it will immediately expose them as spam. The entry is immediately rejected and the message will never land your inbox or cause any other mayhem on your site.
The honeypot technique, in theory, is a simple way to filter spam out of your life. But the reality is that it can sometimes be hit-and-miss. Some of today’s more sophisticated bots may be capable of getting around your honeypot trap.
While a lot of WordPress security plugins and contact form plugins include built-in honeypot features, make sure it isn’t the only solution you use. When you combine it with CAPTCHA and a spam filter plugin, you’ll have robust, multi-layered protection from spam attacks.
It’s also critical to employ a powerful WordPress backup plugin such as BackupBuddy. With the sophistication of today’s spambots, they can wreak all kinds of havoc on your site without warning. If and when that happens, the BackupBuddy plugin will automatically have a fully-functioning backup copy of your WordPress site ready to go, that you can get online immediately.
Make Spam on WordPress a Problem of the Past
WordPress stop spam registrations is a process that none of us want to deal with. However, to prevent spam registration WordPress has given us powerful tools to use.
As we’ve covered in this guide, spam on WordPress comes in many different forms, including emails, comments, and spam registrations. Fortunately, the techniques and tools discussed in this article will give you a strong upper hand on reducing spam on WordPress to an absolute minimum.
Remember, spam is a constant nuisance and, unfortunately, part of our everyday lives. It’s safe to say that none of us, or our websites, are immune to the problem. As such, we have to limit its impact.
Source :
https://ithemes.com/blog/how-to-stop-wordpress-spam/



















 Copy the code and click on the enter code hyperlink and enter the code
Copy the code and click on the enter code hyperlink and enter the code









 We can also now connect to the VM using integrated RDP console in WAC
We can also now connect to the VM using integrated RDP console in WAC



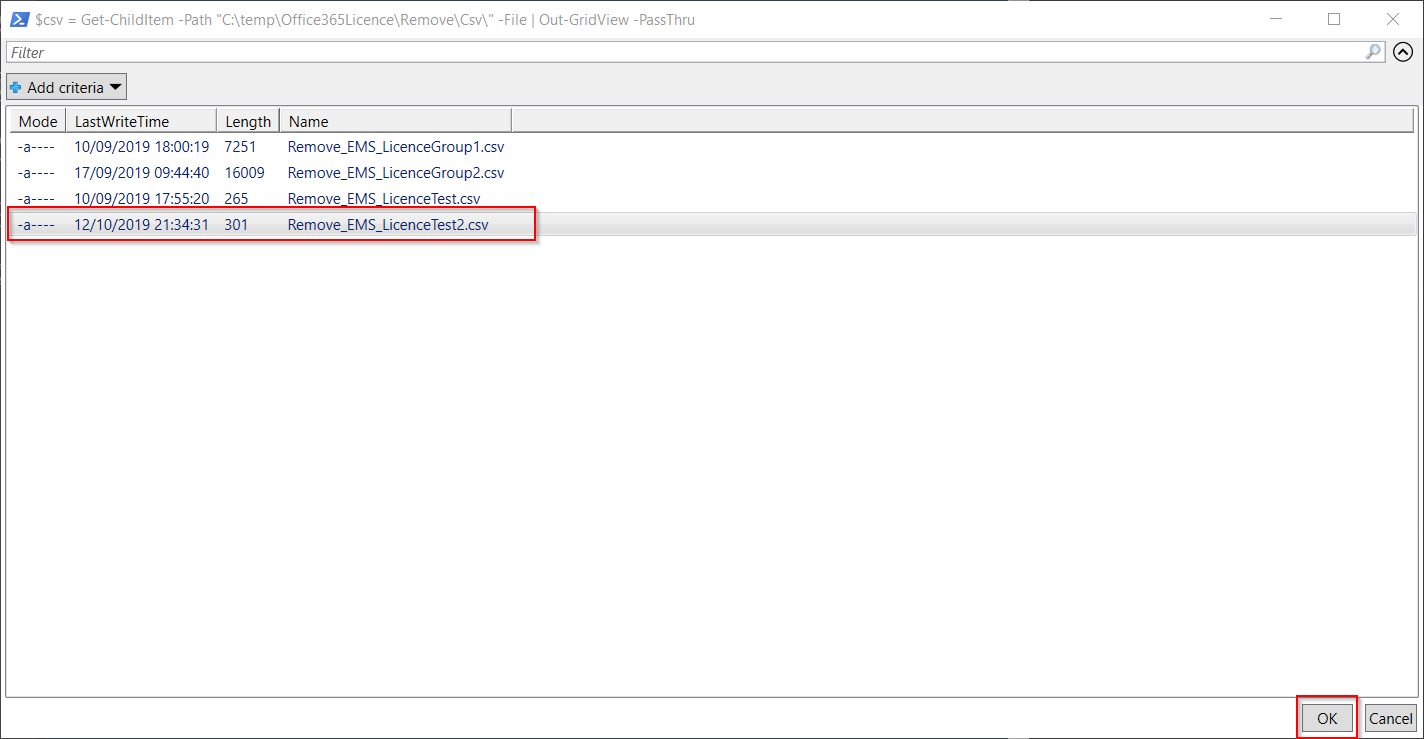

 The full remove license script is below. The only part that needs to be updated is the $csv variable to point to the correct folder where the csv files will be kept.
The full remove license script is below. The only part that needs to be updated is the $csv variable to point to the correct folder where the csv files will be kept.