Remote access VPN has long served us well, but the recent increase in remote working has cast a spotlight on the limitations of this aging technology.Written by Tejas KashyapMAY 20, 2022PRODUCTS & SERVICESZTNA
Remote access VPN has been a staple of most networks for decades, providing a secure method to remotely access systems and resources on the network. However, VPN was developed to mimic the experience of being in the office. Once you’re in, you’ve got broad access to everything.
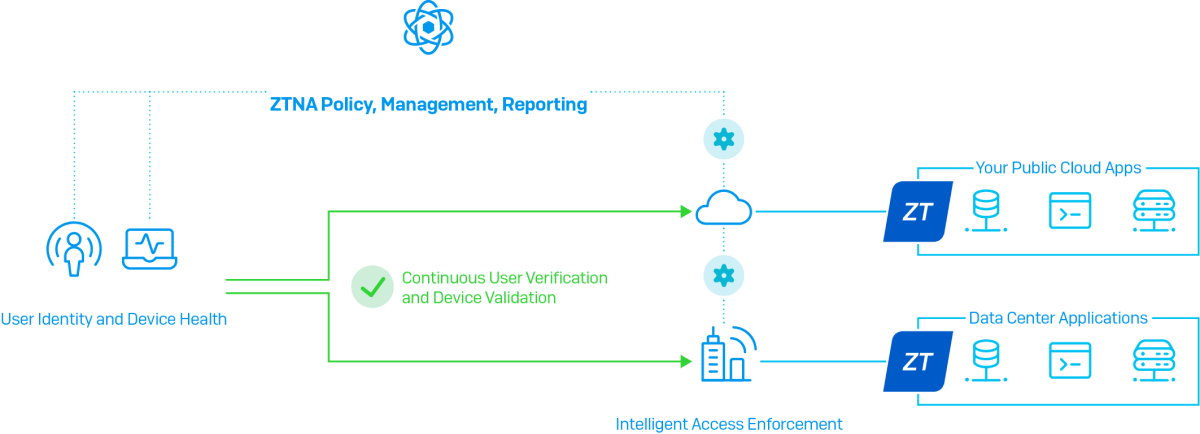
Zero trust network access (ZTNA), on the other hand, can be summed up in four words: trust nothing, verify everything. It’s based on the principle that any connection to your network should be treated as hostile until it’s been authenticated, authorized, and granted access to resources.
Simply put: with virtual private networking (VPN), you’re providing broad network access. With ZTNA, you’re providing specific application access.
Traditional remote access VPN vs. ZTNA
There are several differences between traditional remote access VPN and ZTNA. Here are some important ones, covering trust, device health, administration, and more.
Trust

With remote access VPN, users are implicitly trusted with broad access to resources, which can create serious security risks.
ZTNA treats each user and device individually so that only the resources that user and device are allowed to access are made available. Instead of granting users complete freedom of movement on the network, individual tunnels are established between the user and the specific gateway for the application they’re authorized to access – and nothing more.
Device health

Remote access VPN has no awareness of the health state of a connecting device. If a compromised device connects via VPN, it could affect the rest of the network.
ZTNA integrates device compliance and health into access policies, giving you the option to exclude non-compliant, infected, or compromised systems from accessing corporate applications and data. This greatly reduces the risk of data theft or leakage.
Remote connections

Remote access VPN provides a single point-of-presence on the network, which means a potentially inefficient backhauling of traffic from multiple locations, datacenters, or applications through the remote access VPN tunnel.
ZTNA functions equally well and securely from any connection point, be it home, hotel, coffee shop, or office. Connection management is secure and transparent regardless of where the user and device are located, making it a seamless experience no matter where the user is working.
ZTNA is also a great way to ensure greater security controls during Remote Desktop Protocol (RDP) sessions. Known challenges with RDP include exposed default ports, no support for multi-factor authentication (MFA), broad network access, and of course security vulnerabilities. RDP server vulnerabilities and mistakenly-open RDP connections can be directly exploited by attackers, who leverage such exploits to identify themselves as trusted RDP users. With ZTNA, such users would be treated as hostile by ZTNA authentication features.
Visibility

Remote access VPN is unaware of the traffic and usage patterns it is facilitating, making visibility into user activity and application usage more challenging.
Since ZTNA access is micro-segmented, it can offer increased visibility into application activity. This makes monitoring application status, capacity planning, and licensing management and auditing much easier.
User experience

Remote access VPN clients are notorious for offering a poor user experience, adding latency or negatively impacting performance, suffering from connectivity issues, and generally being a burden on the helpdesk.
ZTNA provides a frictionless, seamless end-user experience by automatically establishing secure connections on demand. This is all done behind the scenes, so most users won’t even be aware of the ZTNA solution that’s helping protect their data.
Administration

Remote access VPN clients are difficult to set up, deploy, enroll new users, and decommission departing users. VPN is also challenging to administer on the firewall or gateway side, especially with multiple nodes, firewall access rules, IP management, traffic flows, and routing. It quickly becomes a full-time job.
ZTNA solutions are often much leaner, cleaner, and easier to deploy and manage. They’re also more agile in quickly changing environments with users, apps, and devices coming and going – making day-to-day administration quick and painless.
What to look for in a ZTNA solution
Be sure to consider these important capabilities when comparing ZTNA solutions from different vendors:
Cloud-delivered, cloud-managed
Cloud management offers tremendous benefits: being able to get up and running quickly, reduced management infrastructure, easy deployment and enrollment, and instant, secure access from anywhere on any device.
Integration with your other cybersecurity solutions

While most ZTNA solutions can work perfectly fine as standalone products, there are significant benefits from having a solution that is tightly integrated with your other cybersecurity products, such as your firewalls and endpoints. A common, integrated cloud management console can be a force multiplier for reducing training time and day-to-day management overhead.
It can also provide unique insights across your various IT security products, especially if they share telemetry. This can dramatically bolster security and offer real-time response when a compromised device or threat gets on the network.
User and management experience
Make sure the solution you’re considering offers both an excellent end-user experience as well as easy administration and management. With more users working remotely, enrollment and efficient device setup is critical when it comes to getting new users productive as quickly as possible.
Be sure to pay attention to how the ZTNA agent is deployed and how easy it is to add new users to policies. Also ensure the solution you’re investing in offers a smooth, frictionless experience for end users. It should also provide visibility into application activity to help you be proactive in identifying peak load, capacity, license usage, and even application issues.
Sophos ZTNA
Sophos ZTNA has been designed from the start to make zero trust network access easy, integrated, and secure.
It’s cloud-delivered, cloud-managed, and integrated into Sophos Central, the world’s most trusted cybersecurity platform. From Sophos Central, you can not only manage ZTNA, but also your Sophos firewalls, endpoints, server protection, mobile devices, cloud security, email protection, much more.
Sophos ZTNA is also unique in that it integrates tightly with both Sophos Firewall and Sophos Intercept X-protected endpoints to share real-time device health between the firewall, device, ZTNA, and Sophos Central to automatically respond to threats or non-compliant devices. It acts like a round-the-clock administrator, automatically limiting access and isolating compromised systems until they’re cleaned up.
Sophos customers agree that the time saving benefits of a fully integrated Sophos cybersecurity solution are enormous. They say that using the Sophos suite of products together for automatic threat identification and response is like doubling the size of their IT team. Of course, Sophos ZTNA will work with any other vendor’s security products, but it’s unique in working better together with the rest of the Sophos ecosystem to provide tangible real-world benefits to visibility, protection, and response.
Visit Sophos.com/ZTNA to learn more or try it for yourself.
Source :
https://news.sophos.com/en-us/2022/05/20/zero-trust-network-access-ztna-versus-remote-access-vpn/