Last Update : 07/25/2022
Description
This article explains the 3 Actions available on an access rule
Resolution
Firewall rules, in general, based on concept of Implicit Deny. Implicit Deny basically means that the default answer to whether a communication is allowed to transit the firewall is always No or Deny. Therefore, the majority of Access Rules tend to be Allow. A firewall will process a communication, inbound or outbound, based on the highest priority rule to the lowest. Once a rule is found with conditions that match, that rule is executed by the firewall. Allow, Deny & Discard is the action that the firewall will take for any communication that meets the conditions of a particular Access Rule. Should a communication come into the firewall and no Access Rule meets the condition to allow it through, the firewall will Drop the communication.
Gen7 Add access rule dialog box
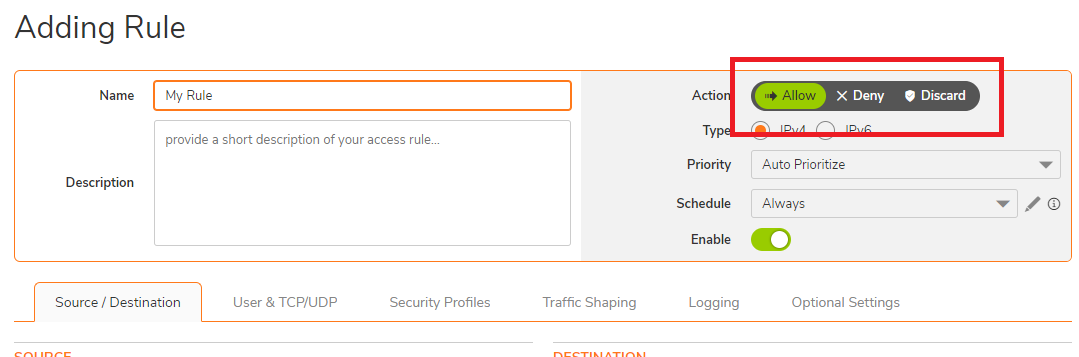
Allow – This means that the firewall will permit the communication to continue through the firewall to its destination.
 NOTE: When creating a new access rule, the default Action on your firewall is set to Allow.
NOTE: When creating a new access rule, the default Action on your firewall is set to Allow.
Gen6 Add access rule dialog box
Deny – This means that when a communication is found to match the conditions of an Access Rule with the Deny action, the communication will not be permitted to proceed. The communication is Dropped by the firewall. A RST (reset) packet sent back to the originating device and the communication will be ended. The RST packet is a communication that goes back to the originator of the traffic stating that the connection has been closed. Under most circumstances, you should not have to write a Deny rule as Deny is the default action as described above.
 NOTE: Be advised that the RST packet is a normal part of network communications and is not unique to the SonicWall.
NOTE: Be advised that the RST packet is a normal part of network communications and is not unique to the SonicWall.
Discard – This option is much like Deny in that it will stop and drop the communication. In this instance, the firewall will not send a RST packet as described in the Deny action above. When the RST packet does not go back as with Deny, the originator has no confirmation that there is a device to respond at the IP address that is trying to reach. Even if the originator suspects that it is a security function that is stopping it, they will still not know anything for sure. This is essentially Stealth Mode applied at the Access Rule level.
Related Articles
- How can I configure a Site to Site VPN policy using Main Mode?
- How can I configure Port Address Translation (PAT) or Port redirection?
- Best Practices when User Authentication using Access Rules is enforced on firewall