In part one, we discussed what numerical control machines do and their basic concepts. These concepts are important to understand the machines better, offering a wider view of their operations. We also laid out how we evaluated the chosen vendors for our research.
For this blog, we will continue discussing our evaluated vendors and highlighting findings that we discovered during our research.
Haas

Haas was the first vendor we focused on because of the fast availability of its controller. We began our analysis by conducting port scanning on the controller simulator and identifying the protocols exposed by the controller. After that, we evaluated the options with which an attacker could abuse the protocols to perform attacks aimed at the security of the machine and verified these attacks in practice on a real-world machine installation.
Okuma

Okuma stands out in the market of CNC controllers for one interesting feature: the modularity of its controller. While the vendor offers in the device’s simplest form a tiny controller, it also provides a mechanism, called THINC API, to highly customize the functionalities of the controller. With this technology, any developer can implement a program that, once installed, runs in the context of the controller, in the form of an extension. This approach is very similar to how a mobile application, once installed, can extend a smartphone’s functionalities.
Heidenhain

In the spirit of the Industry 4.0 paradigm, Heidenhain offers the Heidenhain DNC interface to integrate machines on modern, digital shop floors. Among the many scenarios, Heidenhain DNC enables the automatic exchange of data with machine and production data acquisition (MDA/PDA) systems, higher level enterprise resource planning (ERP) and manufacturing execution systems (MESs), inventory management systems, computer-aided design and manufacturing (CAD/CAM) systems, production activity control systems, simulation tools, and tool management systems
In our evaluation, we had access to the library provided by Heidenhain to the integrators to develop interfaces for the controller. The manufacturer provides this library, called RemoTools SDK,35 to selected partners only.
Fanuc

Like Heidenhain, Fanuc offers an interface, called FOCAS,36 for the integration of CNC machines in smart network environments. Even though this technology offers a restricted set of remote-call possibilities compared with the other vendors’ (that is, a limited number of management features), our experiments showed that a miscreant could potentially conduct attacks like damage, DoS, and hijacking.
What we found
As our evaluation identified 18 different attacks (or variations), we grouped them into five classes: compromise, damage, and denial of service (DoS):
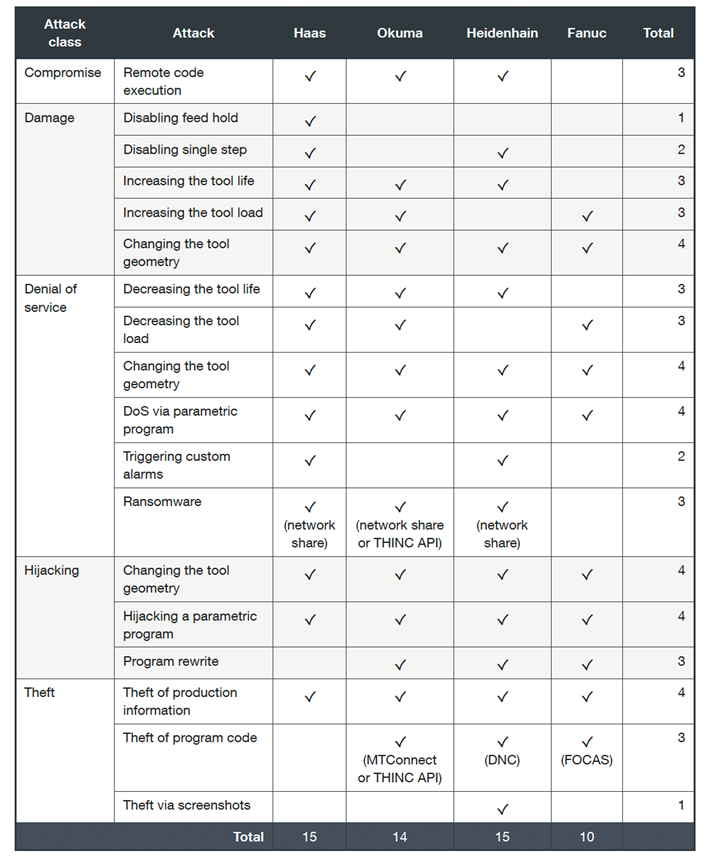
Controller manufacturers like Haas, Okuma, and Heidenhain have been found to have a similar number of issues, around 15. Fanuc had 10 confirmed attacks. Unfortunately, our research shows that this domain lacks awareness concerning security and privacy. This creates serious and compelling problems.
The need for automation-facing features like remote configuration of tool geometry or parametric programming with values determined by networked resources is becoming more common in manufacturing.
With these findings, we determined countermeasures that enterprises can do to mitigate such risks, which we’ll discuss in our final installation. In the last part, we’ll also discuss our responsible disclosure process.
Source :
https://www.trendmicro.com/en_us/research/22/l/cnc-machine-security-risks-part-2.html