This article describes how to access your UniFi Protect application locally or remotely, the factors that create access issues, and how to solve said issues.
- How to connect to UniFi Protect
- Identifying issues
- My camera streams load slowly or buffer frequently
- I can access Protect locally but not remotely
- I can’t access Protect from the mobile app
- I can’t access Protect from my web browser
- I can’t access Protect on a specific browser
- I’m a new user and see a No Controllers Detected notification
- Advanced troubleshooting processes
How to connect to UniFi Protect
There are two ways to access your UniFi Protect application:
- Locally by accessing the IP address of the UniFi OS Console hosting Protect; or
- Remotely on the Protect web application (unifi.ui.com ) or mobile app (iOS / Android ).
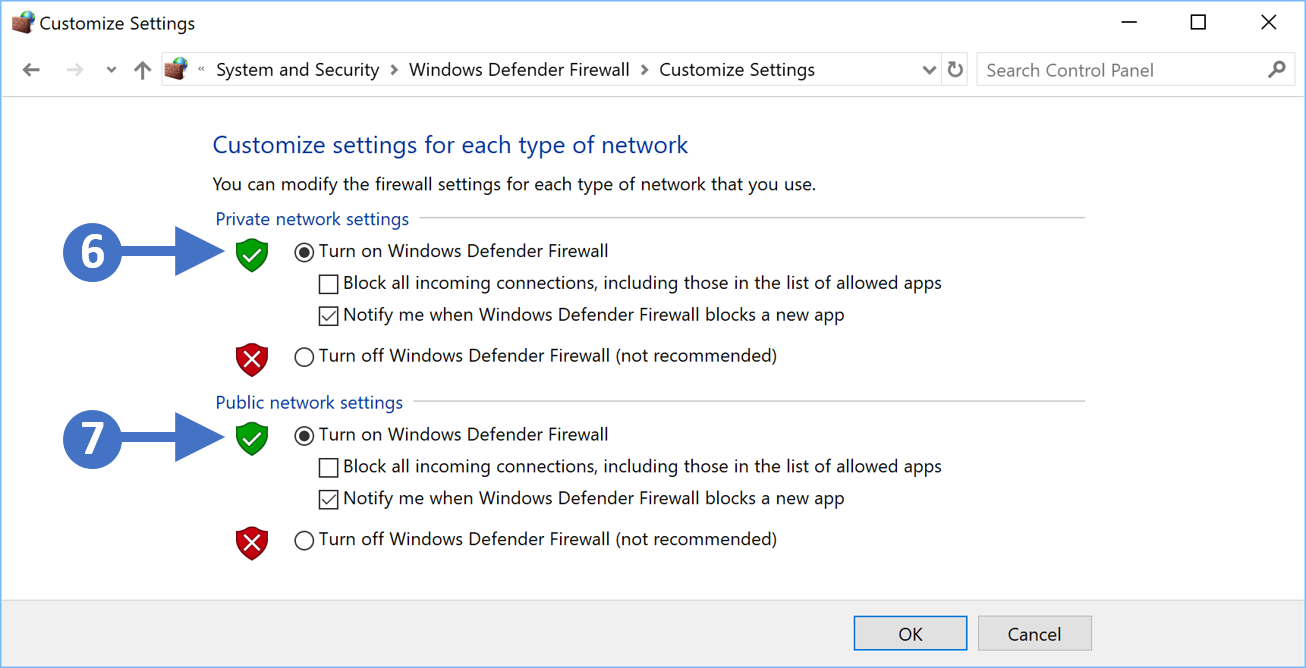
Note: Remote access must be enabled in your Protect application. It is enabled by default.
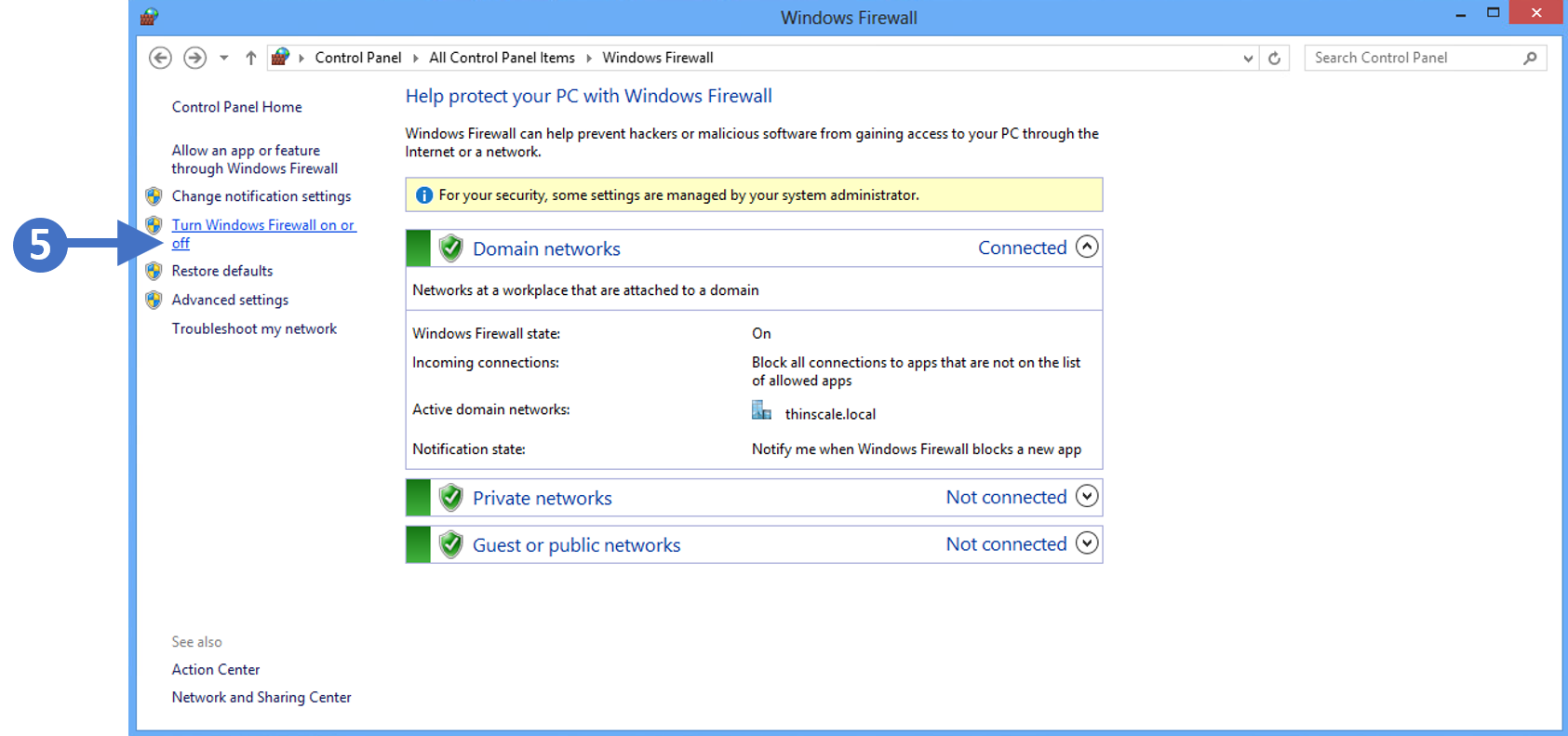
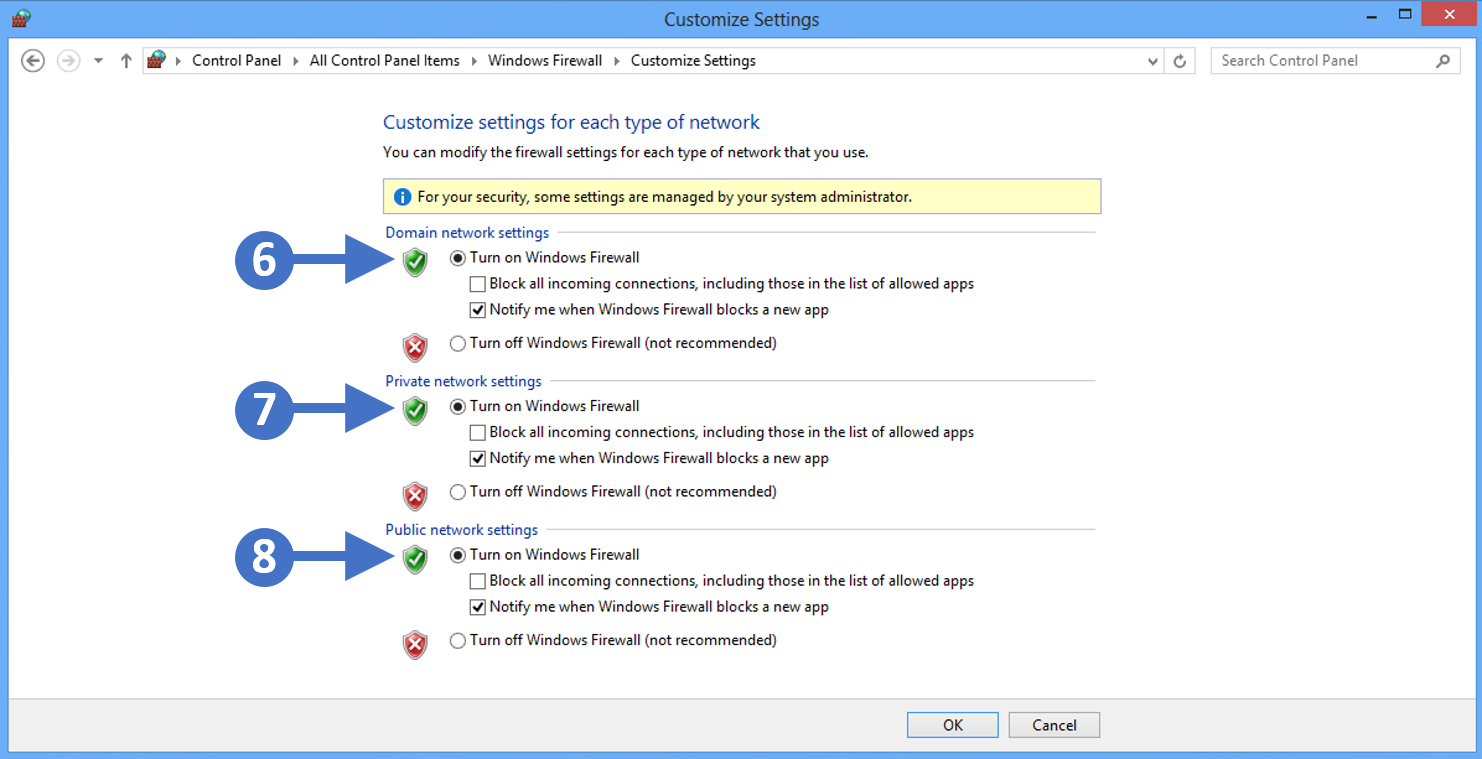
To enable Remote Access in your UniFi Protect application:
- Access the UniFi OS Console hosting Protect via its IP address.
- If you don’t know your UniFi OS Console’s IP address , use the WiFiman app (iOS / Android ) to locate it on your WiFi network.
- Log in to your Ubiquiti SSO account.
- Go to the System Settings > Advanced menu, and enable the Remote Access toggle.
Identifying issues
To identify potential reasons for Protect connectivity issues:
- Try accessing your UniFi OS Console locally by entering its IP address in your web browser, or remotely via Protect web application (unifi.ui.com ) or mobile app.
- Use different mobile devices, ideally running different operating systems (iOS, Android).
- Use different supported browsers, such as Chrome, Firefox, or Safari, on different computers.
- Connect to different client locations, such as:
- A local network with the same subnet as the Protect application.
- A mobile carrier network via a mobile device or tethering.
- A remote network, such as a workplace or public WiFi network.
- Have multiple users, ideally with different system roles, attempt to access the Protect application.
Note: Note your observations. They may be helpful if you need to contact our technical support team.
My camera streams load slowly or buffer frequently
To identify potential reasons for slow stream loading and/or frequent buffering:
- Check the stability of network connection:
- Perform a speed test using the Wifiman app while connected to the same network as your UniFi OS Console. UniFi Protect should perform well with a network connection better than 5 Mbps and decently with a connection of at least 2.5 Mbps. Below this, performance may suffer.
- Ensure that your computer or mobile network is not limiting bandwidth:
- A VPN could be preventing client devices from making a peer-to-peer connection with your UniFi OS Console, meaning that all data is first relayed through Ubiquiti’s Remote Management Service—leading to diminished performance. If so, disable the VPN.
- Check if there’s a subnet conflict where the UniFi OS Console is on a different subnet than the client, but still on LAN. If the client needs to reach your UniFi OS Console’s subnet but doesn’t have a route, it will hit the gateway (the local router), which knows how to route to the UniFi OS Console. If a VPN is enabled and there’s a configured route on the VPN that goes to another network with the same subnet, it will override.
- Inspect your UniFi OS Console’s performance data by making sure you haven’t exceeded its maximum supported camera limit . If so, streaming performance will be diminished.
- Check your computer’s CPU utilization. A lower-specialization computer may not be capable of playing back multiple video streams. If the CPU utilization is nearing 100%, try playing back fewer video streams (e.g., fewer cameras on the live view matrix).
I can access Protect locally but not remotely
If you can’t access the Protect application remotely:
- Check if Remote Access is enabled:
- If it is enabled , try disabling it and enabling again.
- Confirm that you have permission to access Protect remotely. For more information, see UniFi Protect – Add and manage users .
- Visit status.ui.com to see if there are any issues with Ubiquiti’s Remote Management Service currently being resolved.
I can’t access Protect from the mobile app
If you can’t access Protect from the mobile app:
- Verify that the UniFi Protect mobile app is updated to the latest version.
- Ensure that the UniFi Protect mobile app is not restricted from accessing WiFi or cellular data:
- For iOS devices , go to the Settings > Cellular Data menu and make sure UniFi Protect is toggled on.
- For Android devices , go to the Settings > WiFi & Internet > Data Usage > Cellular Data Usage menu, select UniFi Protect, and make sure WiFi and cellular data are not disabled in the App data usage section.
- Disable VPN if one is enabled since some VPNs may block WebRTC connectivity, which is used by Protect.
- For Android devices with VPN enabled , try disabling the Private DNS in the Settings > WiFi & Internet > Private DNS menu. On some WiFi and mobile carrier networks, certain Private DNS providers such as CloudFlare’s 1.1.1.1 may interfere with WebRTC.
- Disable or remove any third-party security or privacy apps that may interfere with network connectivity.
- Force-quit the mobile app and open it again.
- Uninstall the mobile app, reinstall, and open it.
I can’t access Protect from my web browser
If you’re having trouble accessing Protect from a web browser, but you can connect with the mobile app or a web browser on a different network, there may be an issue with your network configuration. For more information, see the Advanced troubleshooting processes section.
If you have a UniFi Cloud Key Gen2 Plus (UCK G2 Plus) updated to Version 2.0.24 running Protect application Version 1.14.0 or higher , it operates via UniFi OS and, therefore, can be accessed remotely at unifi.ui.com , not protect.ui.com.
If you don’t see your Cloud Key-hosted Protect application on unifi.ui.com , make sure your UCK G2 Plus’s firmware is up to date. For more information, see UniFi – How to manage & upgrade the Cloud Key .
If your Cloud Key’s firmware is up to date and can see the Protect application at unifi.ui.com but can’t access it , check if Remote Access is enabled. The recent firmware upgrade might have disabled Remote Access functionality. Follow the steps in the How to connect to UniFi Protect section.
I can’t access Protect on a specific browser
Browser-specific access failures are most often caused by third-party software, such as a browser extension or an application on the host computer.
Common extensions, software, and other features known to cause issues include:
- uBlock Origin
- Privacy Badger
- WebRTC Leak Prevent
- Various VPN services, such as Tunnelbear
- Ad or traffic blockers that interfere with WebRTC connectivity used by UniFi Protect
To troubleshoot browser issues:
- Disable all suspected third-party security or privacy-related browser extensions and software.
- If you can now access Protect , re-enable the extensions and software, one at a time, and test your Protect access after each one. This will help you identify the inhibiting software.
- (For Chrome only ) Disable the feature flag, Anonymize local IPs exposed by WebRTC :
- Copy and paste the following into your address bar: chrome://flags/#enable-webrtc-hide-local-ips-with-mdns
- Select Disabled , then restart Chrome.
Once you’ve found the inhibiting software, leave it disabled or uninstall it. If it’s essential, however, contact the developer’s support team for further guidance on how to configure it so it doesn’t prevent Protect access.
I’m a new user and see a No Controllers Detected notification
If you’re a new user signing in via unifi.ui.com or the Protect mobile app and the UniFi OS Console that hosts your Protect application isn’t appearing , make sure that your user permissions include remote access to the UniFi OS Console. For more information on creating users, see UniFi Protect – Add and manage users .
In some cases, a new user can accept a Protect application invitation, log in to their Ubiquiti account via web browser, initially see their UniFi OS Console, then receive a No Controllers Detected notification.
If you’re a new user and see a No Controllers Detected notification after trying to access Protect web application :
- Make sure that your UniFi OS Console and Protect application versions are up to date.
- Make sure that you have permission to remotely access the UniFi Protect application. For more information, see UniFi Protect – Add and manage users .
- Verify that you are a verified and active user by going to unifi.ui.com , clicking on your UniFi OS Console, navigating to the Users menu, and checking your user status.
- If this doesn’t resolve the issue , delete the custom users and user roles created, reboot the UniFi OS Console, and recreate the users:
- Log in to your UniFi OS Console from the Owner account.
- Go to unifi.ui.com , click on your UniFi OS Console, navigate to the Users menu, and delete all custom users and user groups.
- Click on the dot grid icon in the top-right corner of the dashboard, navigate to Protect > Roles , and delete all custom user roles.
- Click on the dot grid icon in the top-right corner of the dashboard, click the Settings > Advanced tab on the left side of the following screen, and click Restart Device .
- Once the device reboots, log in again with the Owner account and recreate all desired users, groups, and roles.
Advanced troubleshooting processes
Check if a WebRTC connection can be established
UniFi Protect uses WebRTC technology to establish connections between your UniFi OS Console and client devices through NAT and firewalls, such as a UniFi gateway, without requiring explicit port forwarding or the revision of firewall rules.
Typically, you won’t need to make any changes to your network, device, or client configurations in order to access Protect locally or remotely.
However, to establish a WebRTC connection needed to access Protect, both networks (i.e., the one that your Protect application connects to and the one that your client device(s) connect to) must meet these requirements:
- Reliable access to Internet and DNS service
- Adequate bandwidth for basic connectivity and video transfer
- Outbound TCP connection capability on Port 443
- Outbound UDP connection capability on Ports 0–65535
Note: Port forwarding is not required for TCP or UDP connectivity. - A firewall configured to accept solicited, inbound UDP traffic
- No network security appliances (e.g., IPS) or services blocking WebRTC (e.g., STUN or DTLS)
- No gateways configured to use Symmetric NAT, which either block peer-to-peer connections, force the use of a relay server (i.e., TURN), or cause said relay to fail
Note: For more information on the technical aspects of WebRTC, please visit webrtc.org .
Troubleshooting WebRTC connection issues caused by Symmetric NAT
Symmetric NAT , while uncommon, can cause issues when establishing WebRTC and other peer-to-peer connections because it does not maintain a 1:1 port mapping ratio for established connections, causing them to fail.
If that happens, WebRTC will attempt to connect via a relay server (i.e., TURN), which will result in either diminished connection quality or outright connection failure.
If you are behind a Symmetric NAT , you can either:
- Establish a VPN connection between the client and Protect; or
- Configure your router to a mode other than Symmetric NAT, such as Cone NAT.
The UniFi OS Console hosting your UniFi Protect application will automatically detect and log Symmetric NAT on its side but will be unable to determine the NAT type on the clients’ side.
If you suspect Symmetrical NAT on the console-side connection:
- Establish an SSH connection to your UniFi OS Console.
- Execute the following command: grep -Ri “symmetric” /srv/unifi-protect/logs
Any results will confirm that the connection failed due to Symmetric NAT.
Troubleshooting issues with a particular network
If you identify connectivity problems within a particular network , focus your troubleshooting efforts there. For example, if you can connect to your business’s Protect deployment from home, but not while at a friend’s house, focus on troubleshooting the latter network.
If you can’t access Protect from any remote location , focus first on the application’s on-site network.
In both cases:
- Verify that the UniFi OS Console hosting Protect and all client device(s) have a stable internet connection, including a valid gateway IP and DNS servers. Some DNS providers are known to cause problems, such as 1.1.1.1. Try changing it to Google’s 8.8.8.8.
- Verify that selected DNS servers properly resolve the following domains:
- Device.svc.ubnt.com
- Device.amplifi.com
- Global.stun.twilio.com
- Global.turn.twilio.com
- Review your firewall configuration to ensure it meets the requirements listed in the Check if a WebRTC connection can be established section. If you’ve configured custom firewall rules, try disabling them temporarily to test.
- Remove any port forwards for UniFi Protect that may have been configured incorrectly.
- Disable any network-level security appliance or service rules intended to block WebRTC’s internal protocols, STUN or DTLS. If you are using a UniFi gateway , the UniFi Intrusion Prevention System (IPS) does not require a specific configuration to prevent WebRTC connectivity blockage.
Source :
https://help.ui.com/hc/en-us/articles/360034238233-UniFi-Protect-Optimizing-Camera-Connectivity