You want a cybersecurity solution that safeguards your enterprise, not one that slows it down. So, finding a security partner that maintains a global data center network is crucial – this reduces latency and improves reliability. Fortunately, the Cisco Umbrella team backs an award-winning solution with an ever-expanding data center network that spans the globe.
Our data centers – located at key Internet Exchange Points (IXPs) around the world – improve Software-as-a-Service (SaaS) performance by up to 33% over direct internet access (DIA). And our engineers continue to build out this network to support global enterprise customers. We supplement this growing data center network with Anycast routing and a robust assortment of peering relationships, enabling Cisco Umbrella customers to experience the best of both worlds when it comes to security and performance.
Expanding Cisco Umbrella’s Data Center Network
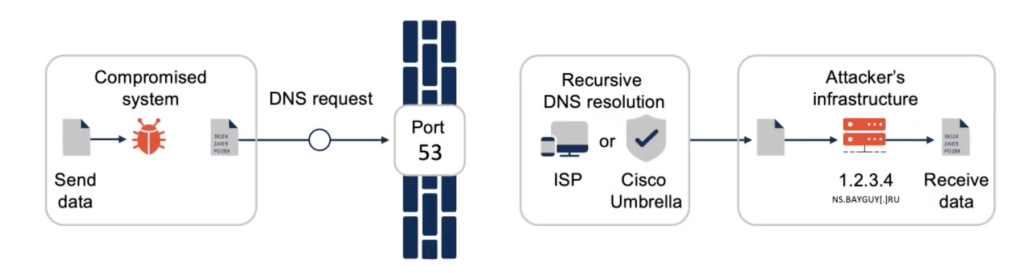
The Cisco Umbrella data center network allows our customers to utilize cybersecurity functionality that includes – but isn’t limited to – DNS-layer security, Secure Web Gateway (SGW), and Cloud Access Security Broker (CASB). A security efficacy test performed by AV-TEST found that Cisco Umbrella had the highest threat detection rate in the industry at 96.39%. And thanks in part to the network of data centers backing Umbrella, this security doesn’t come at the expense of performance.
The most recent additions to the Cisco Umbrella data center network include both brand-new locations and upgrades to existing facilities in:
- Cape Town, South Africa
- Johannesburg, South Africa
- Querétaro City, Mexico
- Madrid, Spain
- Stockholm, Sweden
Our team chooses new locations for their proximity to IXPs, allowing customers to take advantage of faster service. We also prioritize carrier-neutral data centers and heavily utilize colocation facilities. This gives users peace of mind, since Cisco Umbrella is fortified against downtime caused by carrier outages.
How Anycast Routing Makes a Difference
Anycast augmented routing allows our team to maximize performance for our customers. Anycast routing automatically selects the best path to a Cisco Umbrella data center, evaluating things like availability and connection quality.
Not only does Anycast routing reduce latency, but it also helps shield Cisco Umbrella users from outages. If one of the data centers in our network goes down, traffic will automatically fail over to the best available data center. Alternately, users can manually configure tunnels to a Cisco Umbrella data center of their choice to ensure ongoing availability and redundancy.
Reducing Latency With Peering Partners
Of course, a robust data center network isn’t the only factor affecting latency within a cybersecurity solution. That’s why Cisco Umbrella maintains peering partnerships with 1,000+ internet service providers (ISPs), Content Delivery Networks (CDNs), and Software-as-a-Service (SaaS) providers. These partnerships result in more than 6,000 peering sessions with our premier partners.

Peering partnerships serve as a valuable shortcut between customer networks, ISPs, CDNs, and SaaS solutions. This reduces routing hops and shrinks latency, allowing customers to enjoy enhanced performance without ever sacrificing Cisco Umbrella’s world-class security.
Ready to See the Cisco Umbrella Data Center Network In Action?
Explore the full potential of Cisco Umbrella when you sign up for a free, personalized demo today!
Source :
https://umbrella.cisco.com/blog/new-data-centers-show-cisco-investment-global-cloud-architecture