BY AMINU ABDULLAHI MAY 16, 2023
Small and medium-sized businesses (SMBs) are increasingly becoming targets for cyber attacks. According to Verizon, about 61 percent of SMBs reported at least one cyber attack in 2021. Worse, Joe Galvin, chief research officer at Vistage, reported that about 60 percent of small businesses fold within six months of a cyber attack.
To protect your network from potential threats, you need a reliable and effective firewall solution. This tool will act as the first line of defense against unauthorized access and can help prevent malicious attacks from infiltrating a business’s network.
We reviewed the top SMB firewall solutions to help you determine the best one for your business.
- Perimeter 81: Best overall (Read more)
- pfSense: Best open-source-driven firewall (Read more)
- Comodo Free Firewall: Best firewall for Windows PCs (Read more)
- ManageEngine Firewall Analyzer: Best for log, policy, and firewall configuration management (Read more)
- Fortinet FortiGate: Best for hybrid workforces (Read more)
- SonicWall TZ400 Security Firewall: Best for advanced threat protection (Read more)
- Cisco Meraki MX68: Best for small branches with up to 50 users (Read more)
- Sophos XGS Series: Best for remote workers (Read more)
- Protectli Vault – 4 Port: Best for building your own OPNsense or pfSense router and firewall (Read more)
- OPNSense: Best for flexibility (Read more)
Top SMB firewall software comparison
| Best for | IPS | Content filtering | Starting price | |
|---|---|---|---|---|
| Perimeter 81 | Best overall | Yes | Yes | $8 per user per month, billed annually |
| pfSense | Open source | Yes | Yes | $0.01 per hour |
| Comodo Free Firewall | Windows PCs | Yes | Yes | Free |
| ManageEngine Firewall Analyzer | Log, policy, and firewall configuration management | Yes | Yes | $395 per device |
| Fortinet FortiGate | Hybrid workforces | Yes | Yes | Approx. $335 |
| SonicWall TZ400 Security Firewall | Advanced threat protection | Yes | Yes | Approx. $1,000–$1,500 |
| Cisco Meraki MX68 | Small branches with up to 50 users | Yes | Yes | Approx $640 |
| Sophos XGS Series | Remote workers | Yes | Yes | Approx. $520 |
| Protectli Vault – 4 Port | Building your own OPNsense or pfSense router and firewall | Yes | Yes | $269 for FW4B – 4x 1G Port Intel J3160 |
| OPNSense | Flexibility | Yes | Yes | Free, or $170.46/yr for business ed. |
Jump to:
- Key features of SMB firewall software
- How to choose the best SMB firewall software for your business
- Frequently Asked Questions (FAQ)
- Methodology

Perimeter 81
Best overall
Founded in 2018, Perimeter 81 is a cloud and network security company that provides organizations with a secure and unified platform for accessing and managing their applications and data.
It provides many security solutions, including firewall as a service (FWaaS), secure web gateway (SWG), zero trust network access (ZTNA), malware protection, software-defined perimeter, VPN-alternative and secure access service edge (SASE) capabilities, to ensure that data is secure and accessible to authorized personnel. It also provides centralized management and user access monitoring, enabling organizations to monitor and control user activity across the network.
Perimeter 81 provides granular access control policies that enable organizations to define and enforce access rules for their network resources based on the user’s identity, device type, and other contextual factors—making it easy for employees to access the company’s resources without compromising security.
Pricing
| Pricing plans | Minimum users | Cost per month, plus gateway cost | Cost per year, plus gateway cost | Cloud firewall | Agentless application access | Device posture check |
|---|---|---|---|---|---|---|
| Essential | 10 | $10 per user, plus $50 per month per gateway | $8 per user, plus $40 per month per gateway | No | 2 applications | No |
| Premium | 10 | $12 per user, plus $50 per month per gateway | $15 per user, plus $40 per month per gateway | 10 policies | 10 applications | 3 profiles |
| Premium Plus | 20 | $16 per user, plus $50 per month per gateway | $20 per user, plus $40 per month per gateway | 100 policies | 100 applications | 20 profiles |
| Enterprise | 50 | Custom quotes | Custom quotes | Unlimited | Unlimited | Unlimited |
Features
- Identity-based access for devices and users.
- Network segmentation.
- OS and application-level security and mutual TLS encryption.
- Enable traffic encryption enforcement, 2FA, Single Sign-On, DNS filtering, and authentication.
Pros
- Provides visibility into the company network.
- Allows employee access from on-premise.
- Automatic Wi-Fi security.
- 30-day money-back guarantee.
Cons
- Low and mid-tiered plans lack phone support.
- Limited support for Essential, Premium, and Premium Plus.

pfSense
Best open-source-driven firewall
pfSense is an open-source firewall/router network security solution based on FreeBSD. Featuring firewall, router, VPN, and DHCP servers, pfSense is a highly customizable tool that can be used in various network environments, from small home networks to large enterprise networks.
The tool supports multiple WAN connections, failover and load balancing, and traffic shaping, which can help optimize network performance. pfSense can be used on computers, network appliances, and embedded systems to provide a wide range of networking services.
Pricing
pfSense pricing varies based on your chosen medium—cloud, software, or hardware appliances.
For pfSense cloud:
- pfSense on AWS: Pricing starts from $0.01 per hour to $0.40 per hour.
- pfSense on Azure: Pricing starts from $0.08 per hour to $0.24 per hour.
For pfSense software:
- pfSense CE: Open source version available to download for free.
- pfSense+ Home or Lab: Available at no cost for evaluation purposes only.
- pfSense+ W/TAC LITE: Currently available at no charge, but vendor may increase rate to $129 per year in the future.
- pfSense+ W/TAC PRO: $399 per year.
- pfSense+ W/TAC ENT: $799 per year.
For pfSense appliances:
| pfSense+ appliances | Device cost | Best for | Firewall speed (IPERF3 TRAFFIC) | Firewall speed (IMIX TRAFFIC) |
|---|---|---|---|---|
| Netgate 1100 | $189 | Home | 607 Mbps(10k ACLs) | 191 Mbps(10k ACLs) |
| Netgate 2100 | $349 | Home Home Pro Branch/Small Business | 964 Mbps(10k ACLs) | 249 Mbps(10k ACLs) |
| Netgate 4100 | $599 | Home Pro Branch/Small Business Medium Business | 4.09 Gbps(10k ACLs) | 1.40 Gbps(10k ACLs) |
| Netgate 6100 | $799 | Home Pro Branch/Small Business Medium Business | 9.93 Gbps(10k ACLs) | 2.73 Gbps(10k ACLs) |
| Netgate 8200 | $1,395 | Branch/Small Business Medium Business Large Business | 18.55 Gbps | 5.1 Gbps |
| Netgate 1537 | $2,199 | Medium Business Large Business Data Center | 18.62 Gbps(10k ACLs) | 10.24 Gbps(10k ACLs) |
| Netgate 1541 | $2,899 | Medium Business Large Business Data Center | 18.64 Gbps(10k ACLs) | 12.30 Gbps(10k ACLs) |
Features
- Stateful packet inspection (SPI).
- IP/DNS-based filtering.
- Captive portal guest network.
- Time-based rules.
- NAT mapping (inbound/outbound).
Pros
- Anti-spoofing capability.
- Connection limits option.
- Community support.
Cons
- The tool’s open-source version support is limited to community or forum. It lacks remote login support, private login support, a private support portal, email, telephone, and tickets.
- Complex initial setup for inexperienced users.

Comodo Free Firewall
Best for Windows PCs
Comodo Firewall is a free firewall software designed to protect computers from unauthorized access and malicious software by monitoring all incoming and outgoing network traffic.
The firewall features packet filtering, intrusion detection and prevention, and application control. It also includes a “sandbox” feature that allows users to run potentially risky applications in a protected environment without risking damage to the underlying system.
The software works seamlessly with other Comodo products, such as Comodo Antivirus and Comodo Internet Security.
Pricing
Comodo is free to download and use. The vendor recommends adding its paid antivirus product (Comodo Internet Security Pro) to its firewall for added security. The antivirus costs $29.99 per year for one PC or $39.99 per year for three PCs.
Features
- Auto sandbox technology.
- Cloud-based behavior analysis.
- Cloud-based allowlisting.
- Supports all Windows OS versions since Windows XP (Note: Windows 11 support forthcoming).
- Website filtering.
- Virtual desktop.
Pros
- Monitors in/out connections.
- Learn user behavior to deliver personalized protection.
- Real-time malware protection.
Cons
- Lacks modern user interface.
- Pop-up notifications—some users may find the frequent alerts generated by the software annoying and intrusive.

ManageEngine Firewall Analyzer
Best for log, policy, and firewall configuration management
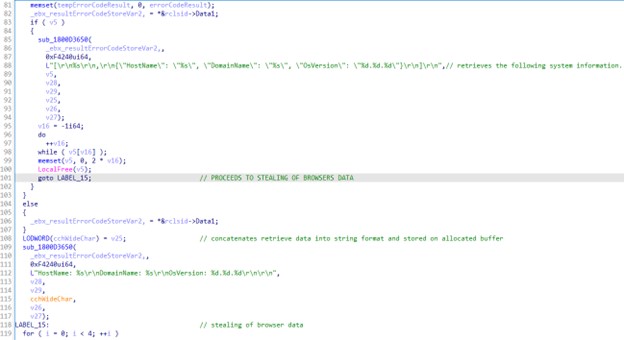
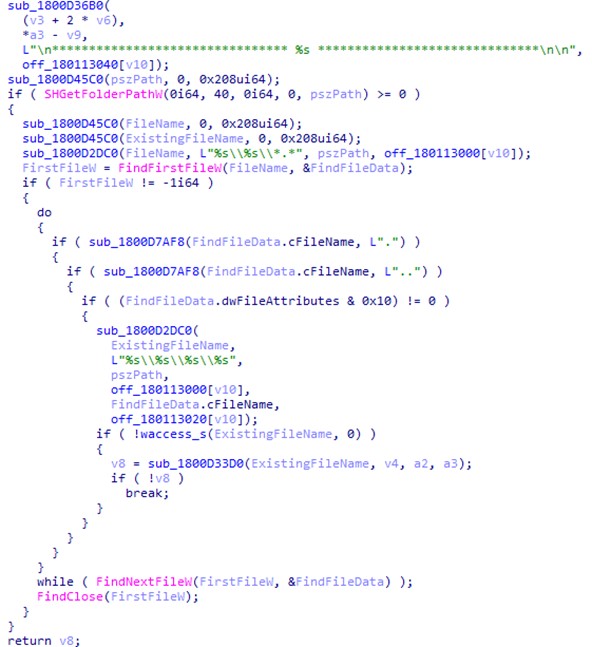
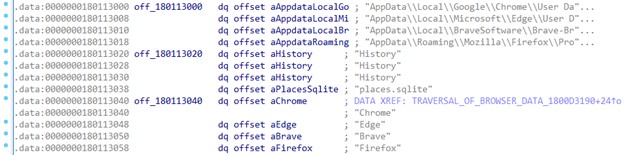
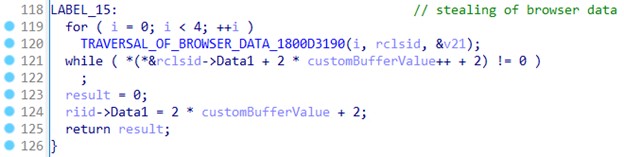
ManageEngine Firewall Analyzer is a web-based log analytics and configuration management software for firewall devices.
It provides real-time visibility into network activity and helps organizations identify network threats, malicious traffic, and policy violations. It supports various firewalls, including Cisco ASA, Palo Alto, Juniper SRX, Check Point, SonicWall, and Fortinet.
Firewall Analyzer helps monitor network security, analyze the security posture of the network, and ensure compliance with security policies. It also provides reports, dashboards, and automated alerting to ensure the network remains secure.
Pricing
The amount you will pay for this tool depends on the edition you choose and the number of devices in your organization.
You can download the enterprise edition’s 30-day free trial to test-run it and learn more about its capabilities. It’s available in two versions: Windows OS or Linux. You can also download it for mobile devices, including iPhone devices and Android phones or tablets.
- Standard Edition: Starts at $395 per device, up to 60 devices.
- Professional Edition: Starts at $595 per device, up to 60 devices.
- Enterprise Edition: Starts at $8,395 for 20 devices, up to 1,200 devices.
Feature
- Firewall rules report and firewall device audit report.
- Regulatory compliance with standards such as ISO, PCI-DSS, NERC-CIP, SANS, and NIST.
- Network behavioral anomaly alert.
- Security reports for viruses, attacks, spam, denied hosts, and event summaries.
- Historical configuration change tracking.
- Bandwidth report for live bandwidth, traffic analyzer, URL monitor, and employee internet usage.
- Compatible with over 70 firewall versions.
Pros
- Excellent technical support.
- Users praise its reporting capability.
- In-depth auditing with aggregated database entries capability.
- VPN and security events analysis.
Cons
- Complex initial setup.
- Users reported that the tool is occasionally slow.

Fortinet FortiGate
Best for hybrid workforces
Fortinet FortiGate is a network security platform that offers a broad range of security and networking services for enterprises of all sizes. It provides advanced threat protection, secure connectivity, and secure access control. It also provides advanced firewall protection, application control, and web filtering.
Business owners can use Fortinet’s super-handy small business product selector to determine the best tool for their use cases.
Small and mid-sized businesses may find the following FortiGate’s model suitable for their needs:
| IPS | NGFW | Threat Protection | Interfaces | Series | |
|---|---|---|---|---|---|
| FortiGate 80F | 1.4 Gbps | 1 Gbps | 900 Mbps | Multiple GE RJ45 | Variants with PoE, DSL,3G4G, WiFi and/or storage | FG-80F, FG-80F-PO, FG-80F-Bypass, FG-81F, FG-81F-PO, FG-80F-DSL, FWF-81F-2R-POE, FWF-81, F-2R-3G4G-POE, FWF-80F/81F-2R, and FWF-80F/81F-2R-3G4G-DSL |
| FortiGate 70F | 1.4 Gbps | 1 Gbps | 800 Mbps | Multiple GE RJ45 | Variants with internalstorage | FG-70F and FG-71F |
| FortiGate 60F | 1.4 Gbps | 1 Gbps | 700 Mbps | Multiple GE RJ45 | Variants with internalstorage | WiFi variants | FG-60F, FG-61F, FWF-60F, and FWF-61F |
| FortiGate 40F | 1 Gbps | 800 Mbps | 600 Mbps | Multiple GE RJ45 | WiFi variants | FG-40F, FG-40F-3G4G, FWF-40F, FWF-40F-3G4G |
Fortinet FortiGate is compatible with several operating systems and can easily be integrated into existing networks.
Pricing
Unfortunately, Fortinet doesn’t publish their prices. Reseller prices start around $335 for the FortiGate 40F with no support. Contact Fortinet’s sales team for quotes.
Features
- Offers AI-powered security services, including web, content, and device security, plus advanced tools for SOC/NOC.
- Continuous risk assessment.
- Threat protection capability.
Pros
- Top-rated firewall by NSS Labs.
- Intrusion prevention.
Cons
- According to user reviews, the CLI is somewhat complex.
- Complex initial setup.

SonicWall TZ400 Security Firewall
Best for advanced threat protection
The SonicWall TZ400 is a mid-range, enterprise-grade security firewall designed to protect small to midsize businesses. It supports up to 150,000 maximum connections, 6,000 new connections per second, and 7×1-Gbe.
The TZ400 features 1.3 Gbps firewall inspection throughput, 1.2 Gbps application inspection throughput, 900 Mbps IPS throughput, 900 Mbps VPN throughput, and 600 Mbps threat prevention throughput.
Pricing
This product’s pricing is not available on the Sonicwall website. However, resellers such as CDW, Staples, and Office Depot typically sell it in the $1,000–$1,500 range. You can request a quote for your particular use case directly from Sonicwall.
Features
- Deep memory inspection.
- Single-pane-of-glass management and reporting.
- SSL/TLS decryption and inspection.
- SD-WAN and zero-touch deployment capabilities.
Pros
- Optional PoE and Wi-Fi options.
- DDoS attack protection (UDP/ICMP/SYN flood).
- Fast performance with gigabit and multi-gigabit Ethernet interfaces.
- Protects against intrusion, malware, and ransomware.
- High-performance IPS, VPN, and threat prevention throughput.
- Efficient firewall inspection and application inspection throughput.
Cons
- Support can be improved.
- It can be difficult to configure for inexperienced users.

Cisco Meraki MX68
Best for small branches with up to 50 users
The Cisco Meraki MX68 is a security appliance designed for SMBs. It’s part of the Cisco Meraki MX series of cloud-managed security appliances that provide network security, content filtering, intrusion prevention, and application visibility and control.
The MX68 is equipped with advanced security features such as a stateful firewall, VPN, and intrusion prevention system (IPS) to protect your network from cyber attacks. The MX68 has a variety of ports and interfaces, including LAN and WAN ports and a USB port for 3G/4G failover. It also supports multiple WAN uplinks, providing redundancy and failover options to ensure your network remains online and available.
Pricing
The Cisco Meraki MX68 pricing isn’t listed on the company’s website, but resellers typically list it starting around $640. You can request a demo, free trial, or quotes by contacting the Cisco sales team.
Features
- Centralized management via web-based dashboard or API.
- Intrusion detection and prevention (IDS/IPS).
- Next-generation layer 7 firewalls and content filtering.
- SSL decryption/inspection, data loss prevention (DLP), and cloud access security broker (CASB).
- Instant wired failover with added 3G/4G failover via a USB modem.
Pros
- Remote browser isolation, granular app control, and SaaS tenant restrictions.
- Support for native IPsec or Cisco AnyConnect remote client VPN.
- Provides unified management for security, SD-WAN, Wi-Fi, switching, mobile device management (MDM), and internet of things (IoT)
Cons
- The license cost is somewhat high.
- Support can be improved.

Sophos XGS Series
Best for remote workers
Sophos XGS Series Desktop is a range of network security appliances designed to provide comprehensive protection for SMBs. These appliances combine several security technologies, including firewall, intrusion prevention, VPN, web filtering, email filtering, and application control, to provide a robust and integrated security solution.
Here’s a comparison table of the Sophos XGS series firewalls:
| Firewall | TLS inspection | IPS | IPSEC VPN | NGFW | Firewall IMIX | Threat protection | Latency (64 byte UDP) | |
|---|---|---|---|---|---|---|---|---|
| XGS Desktop Models | 3,850 Mbps | 375 Mbps | 1,200 Mbps | 3,000 Mbps | 700 Mbps | 3,000 Mbps | 280 Mbps | 6 µs |
| XGS 107 / 107w | 7,000 Mbps | 420 Mbps | 1,500 Mbps | 4,000 Mbps | 1,050 Mbps | 3,750 Mbps | 370 Mbps | 6 µs |
| XGS 116 / 116w | 7,700 Mbps | 650 Mbps | 2,500 Mbps | 4,800 Mbps | 2,000 Mbps | 4,500 Mbps | 720 Mbps | 8 µs |
| 126/126w | 10,500 Mbps | 800 Mbps | 3,250 Mbps | 5,500 Mbps | 2,500 Mbps | 5,250 Mbps | 900 Mbps | 8 µs |
| 136/136w | 11,500 Mbps | 950 Mbps | 4,000 Mbps | 6,350 Mbps | 3,000 Mbps | 6,500 Mbps | 1,000 Mbps | 8 µs |
The Sophos XGS Series Desktop appliances are available in several models with varying performance capabilities, ranging from entry-level models suitable for small offices to high-performance models suitable for large enterprises. They are designed to be easy to deploy and manage, with a user-friendly web interface and centralized management capabilities.
Pricing
Sophos doesn’t advertise the pricing for their XGS Series Desktop appliances online, but they typically retail starting at about $520 from resellers.
Potential customers are encouraged to request a free trial and pricing information by filling out a form on the “Get Pricing” page of their website.
Features
- Centralized management and reporting.
- Wireless, SD-WAN, application aware routing, and traffic shaping capability.
- SD-WAN orchestration.
- Advanced web and zero-day threat protection.
Pros
- Zero-touch deployment.
- Lateral movement protection.
- Users find the tool scalable.
Cons
- Performance limitations.
- Support can be improved.

Protectli Vault – 4 Port
Best for building your own OPNsense or pfSense router and firewall
The Protectli Vault is a small form-factor network appliance designed to act as a firewall, router, or other network gateway. The 4-Port version has four gigabit Intel Ethernet NIC ports, making it ideal for SMB or home networks.
The device is powered by a low-power Intel processor and can run a variety of open-source firewall and router operating systems, such as pfSense, OPNsense, or Untangle. It comes with 8GB DDR3 RAM and up to 32GB DDR4 RAM.
The Protectli Vault is designed to be fanless, silent, and compact, making it ideal for use in the home or office environments where noise and space may be an issue. It’s also designed to be energy-efficient, consuming only a few watts of power, which can save businesses considerable amounts of money on energy costs over time.
Pricing
The amount you will pay for this tool depends on the model you select and your desired configuration. The rates below are starting prices; your actual rate may vary based on your configuration. Note that all these items ship free to U.S. addresses.
- VP2410 – 4x 1G Port Intel J4125: Starts at $329.
- VP2420 – 4x 2.5G Port Intel J6412: Starts at $379.
- FW4B – 4x 1G Port Intel J3160: Starts at $269.
- FW4C – 4x 2.5G Port Intel J3710: Starts at $289.
Features
- Solid-state and fanless tool.
- Provides 2.5 GB ports unit.
- AES-NI, VPN, and coreboot options.
Pros
- A 30-day money-back guarantee.
- Transparent pricing.
- Coreboot support.
- CPU supports AES-NI.
Cons
- Steep learning curve.

OPNSense
Best for flexibility
OPNsense is a free and open-source firewall and routing platform based on the FreeBSD OS. It was forked from the popular pfSense and m0n0wall project in 2014 and was officially released in January 2015.
OPNsense provides a modular design that allows users to easily add or remove functionality based on their needs.
OPNsense is popular among IT professionals and network administrators who need a flexible and customizable firewall and routing platform that they can tailor to their specific needs. It’s also a good choice for small businesses and home users who want to improve their networks’ security without spending a lot of money on commercial solutions.
Pricing
OPNSense is a free, open source tool. It is available in two editions: Community edition and business edition. You can download the community version at no cost. For the business version, a one-year subscription costs $170.46 per year.
Features
- High availability and hardware failover.
- Intrusion detection and prevention.
- Captive portal.
- VPN (site-to-site and road warrior, IPsec, OpenVPN, and legacy PPTP support).
- Built-in reporting and monitoring tools, including RRD Graphs.
Pros
- Free, open source.
- Traffic shaper.
- Support for plugins.
- Multi-language support, including English, Czech, Chinese, French, German, Italian, Japanese, Portuguese, Russian, and Spanish.
Cons
- Reporting capability can be improved.
- The interface can be improved.
Key features of SMB firewalls
Firewalls designed for SMBs share many of the same characteristics as their enterprise-grade cousins—such as firewall rule and policy configuration, content filtering, reporting and analytics—while placing additional emphasis on affordability and ease of use.
Firewall rules and policies
Administrators should be able to set up firewall rules and policies that control traffic flow and block or permit traffic based on various criteria, such as source/destination IP addresses, ports, and protocols.
These rules and policies can be used to control the types of applications, services, and data that are allowed to traverse the network, as well as create restrictions on access.
Firewall rules and policies are essential to the security of a network, as they provide the first line of defense against malicious attacks.
Content filtering
Content filtering is the process of blocking or restricting certain types of content from entering or leaving a network. It can be used to block websites, applications, or data that may contain malicious or unwanted content, such as malware, viruses, or pornographic material.
Content filtering is typically implemented using a combination of hardware and software solutions. Hardware solutions, such as routers and switches, can be configured to block certain types of traffic or data or to restrict access to certain websites or applications. Software solutions, such as firewall rules and policies, can also be used to block or restrict certain types of content.
Reporting and analytics
Reporting and analytics are essential for any business network, as they provide important insights into the health and security of the network. Firewall reporting and analytics features allow network administrators to identify trends, detect potential threats, and analyze the performance of the network over time.
Reporting and analytics can also be used to identify any areas of the network that may be vulnerable to attack, as well as identify any areas where the network may not be performing optimally.
Affordability
For SMBs, affordability is a key factor when it comes to purchasing a firewall. SMB firewalls are typically more affordable than enterprise firewalls and can be purchased for as little as a few hundred dollars, so it is important to consider your budget when selecting a firewall.
Some SMB firewalls offer additional features for a fee, so consider what features are necessary for your network and the ones you can do without, as this will help you decide on the most cost-effective firewall solution. At the same time, be careful not to cut corners—your business’s data is too important to be insufficiently protected.
Ease of use and support
For SMBs, finding a firewall solution that is easy to use and has good support is essential. Firewalls should be easy to configure and manage so the network administrator can quickly and easily make changes as needed.
Additionally, good support should be available for any issues or questions that arise. This support should include an online knowledge base and access to technical support staff that can assist with any questions or problems, ideally 24/7.
How to choose the best SMB firewall software for your business
When shopping for the best SMB firewall software for your business, look for software that offers the features you need, easy installation and management, scalability to grow with your business, minimal impact on network performance, and an affordable price.
It’s also important to choose a vendor with a good reputation in the industry, backed up by positive reviews and customer feedback.
Frequently asked questions (FAQs)
What is an SMB firewall?
An SMB firewall is a type of network security device that is designed specifically for small and medium-sized businesses. It’s used to protect networks from unauthorized access, malicious attacks, and other security threats.
What features should I look for in an SMB firewall?
Above all you need a solution with a strong security profile. Look for specific security measures such as:
- Intrusion prevention
- Content filtering
- Malware protection
- Application control
- Traffic shaper
Other factors to consider include ease of management, scalability, and cost.
Do small businesses need a firewall?
Yes, small businesses need a firewall. It provides an essential layer of network security that helps protect against unauthorized access, malware, and other security threats. Without a firewall, small businesses are vulnerable to attacks that could compromise sensitive data, cause network downtime, and damage their reputation.
How much does a firewall cost for SMBs?
The cost of an SMB firewall can vary widely depending on the features, capabilities, and brand of the firewall. Generally, SMB firewalls can range in price from a few hundred to several thousand dollars.
How many firewalls do you need for a small business?
The number of firewalls needed for a small business will depend on the size and complexity of the network. In many cases, a single firewall may be sufficient to protect the entire network. However, in larger networks, it may be necessary to deploy multiple firewalls to provide adequate protection.
Factors such as network segmentation, geographic location, and compliance requirements may also influence the number of firewalls needed. It’s best to consult with a network security expert to determine the appropriate number of firewalls for your small business.
Methodology
We analyzed dozens of SMB firewall software and narrowed down our list to the top ten. We gathered primary data—including pricing details, features, support, and more—from each tool provider’s website, as well as third-party reviews. We selected each software based on five key data points: security, ease of use, affordability, quality of service, and user satisfaction.
Bottom line: Choosing an SMB firewall
The solutions we evaluated are some of the best SMB firewalls currently available on the market. They are designed to provide SMBs with advanced security features, easy management, and scalability at affordable rates.
If your business is growing fast and you need an enterprise-grade network firewall solution, we also reviewed the best firewall software for enterprise networks.
Read our complete guide to designing and configuring a firewall policy for your organization, complete with a free, downloadable template.
Source :
https://www.enterprisenetworkingplanet.com/guides/best-firewalls-for-small-medium-business/