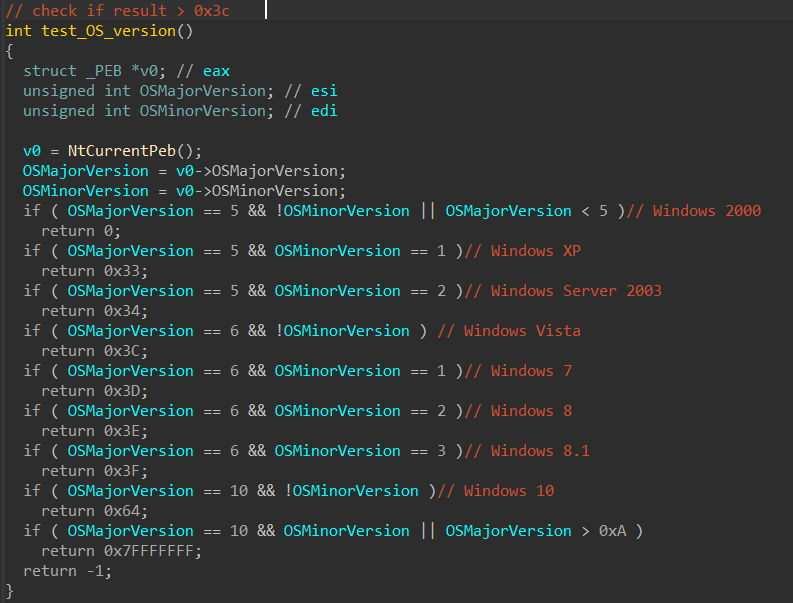
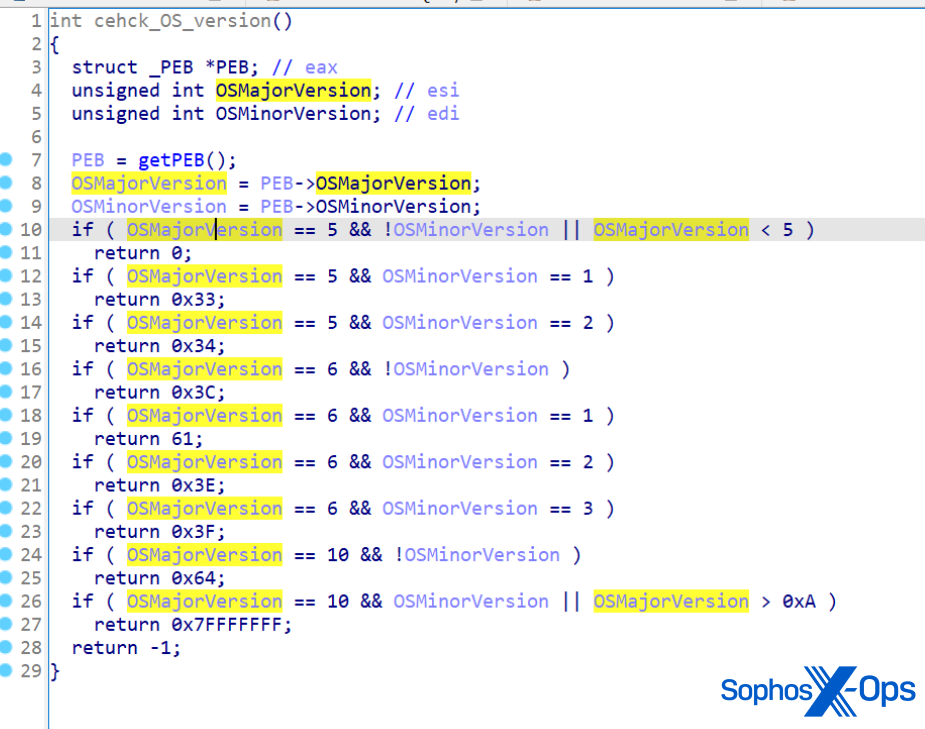
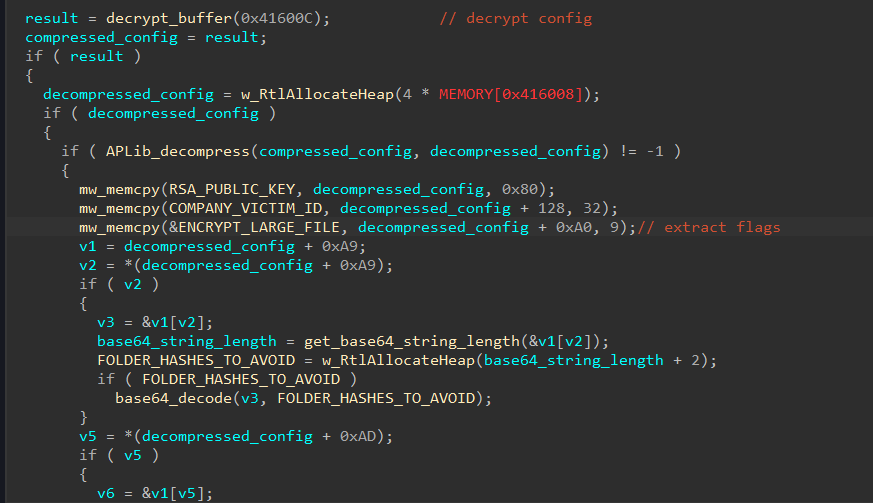
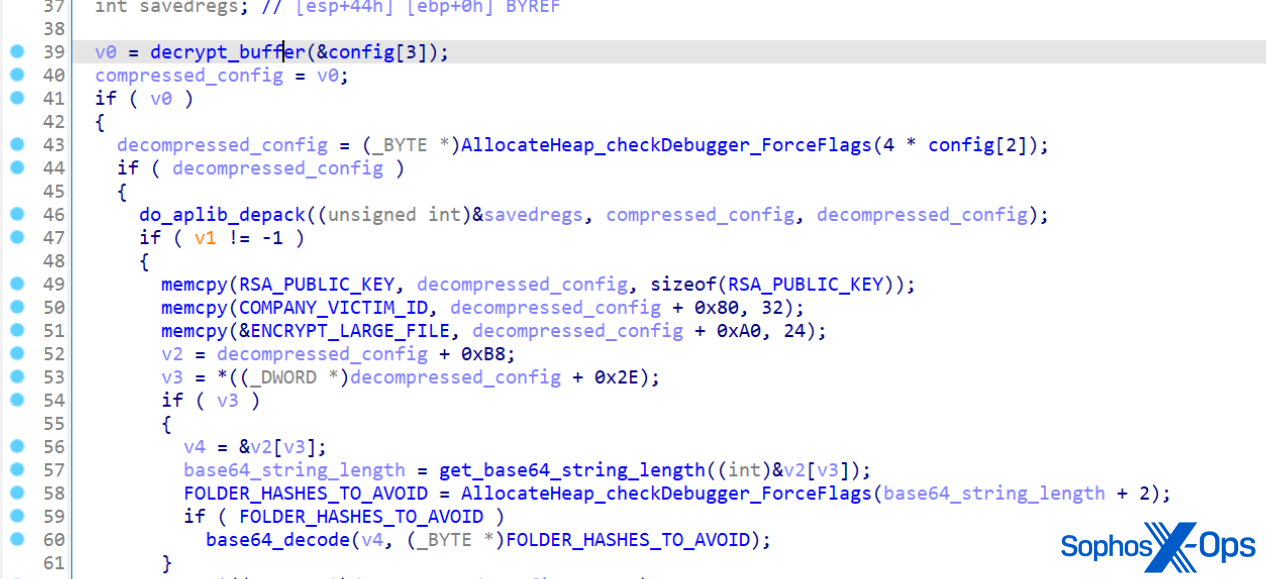
Cortex XDR 3.5 and Cortex XDR Agent 7.9 Deliver Stronger Security, Better Search and Broader Coverage, Including iOS Support
Your employees probably expect to work from anywhere, at any time they want, on any device. With the rise of remote work, users are accessing business apps and data from mobile devices more than ever before. Cortex XDR Mobile for iOS lets you protect your users from mobile threats, such as malicious URLs in text messages and malicious or unwanted spam calls.
Cortex XDR Mobile for iOS is just one of over 40 new features in our Cortex XDR 3.5 and Cortex XDR Agent 7.9 releases. In addition to iOS protection, we’ve bolstered endpoint security, improved the flexibility of XQL Search, and expanded visibility and normalization to additional data sources. Even more new advancements make it easier than ever to manage alert exceptions and granularly control access to alerts and incidents.
Let’s dive in and take a deeper look at the new capabilities of Cortex XDR 3.5 and Cortex XDR Agent 7.9.
iOS Protection with Cortex XDR Mobile
With the rapid shift to remote work, flexible BYOD policies are a must have, now, for many companies. Whether employees are working at home, from a café, or in a corporate office, they often have a phone within reach, and for good reason. 62% of U.S. workers say mobile phones or tablets help them be productive at work, according to a broad 2021 survey.
Phishing and Smishing and Spam, Oh My!
| If you own a smartphone (like 85% of Americans do) you’ve probably received suspicious text messages claiming your bank or Amazon or PayPal account has been blocked. Or you’ve received messages saying that you need to click a link to complete a USPS shipment. And if you are receiving these messages, you can assume your users are also receiving similar messages. It’s only a matter of time before a user clicks one of these links and supplies their credentials, possibly even the same credentials they use at work. These smishing attacks, or phishing performed through SMS, are on the rise.If your organization is like many others, you’ve probably deployed an email security solution that filters spam and phishing URLs. However, you may not be protecting your mobile devices – BYOD or corporate-owned – from spam calls and phishing attacks. | 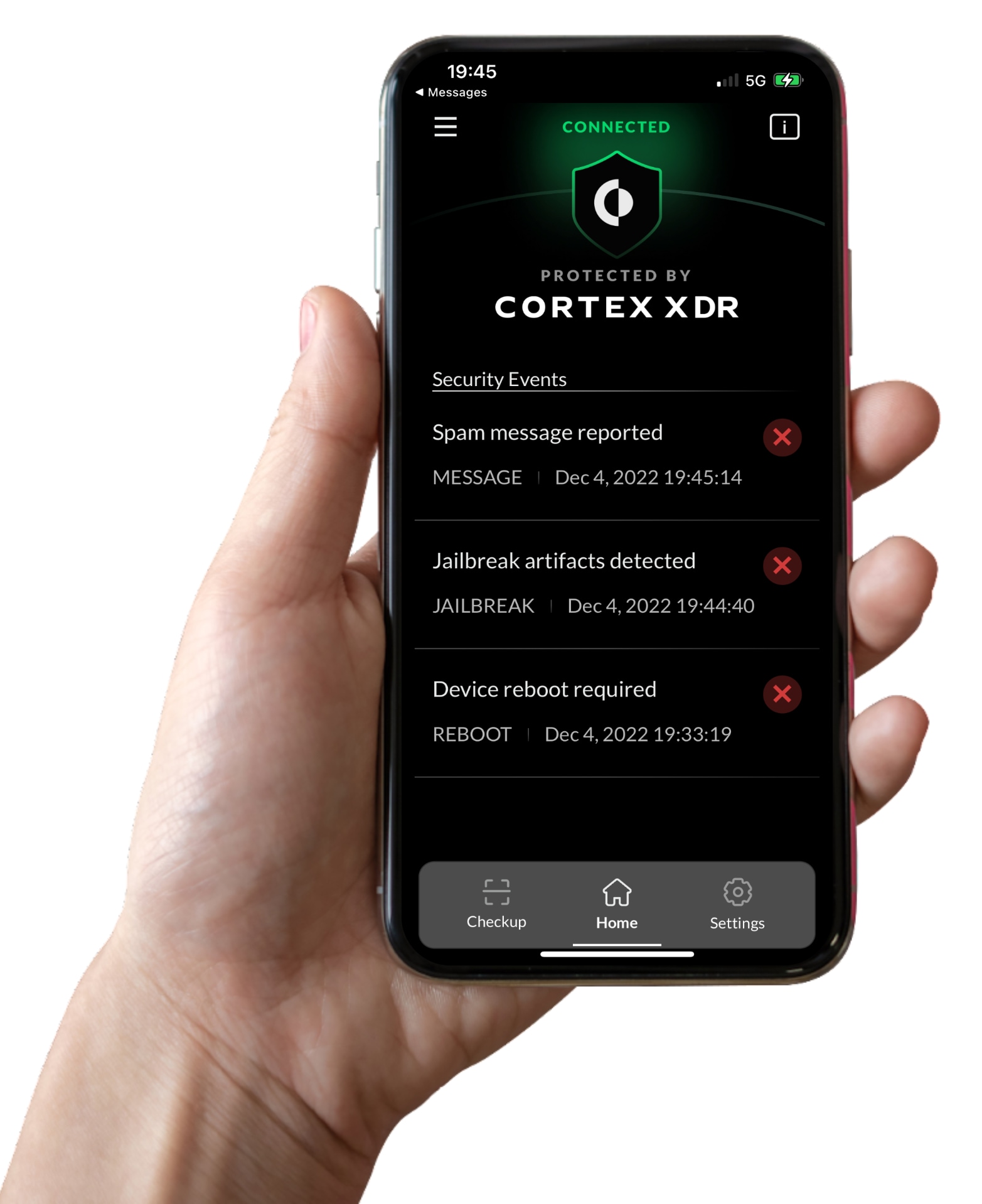 |
|---|
With Cortex XDR Mobile for iOS, you can now secure iOS devices from advanced threats like smishing. The Cortex XDR agent blocks malicious URLs in SMS messages with URL filtering powered by Unit 42 threat intelligence. It can also block spam calls, safeguarding your users from unwanted and potentially fraudulent calls. Users can also report a spam call or message, allowing the Cortex XDR administrator to block the phone number.
Hunting Down Jailbroken Devices
Some of your iPhone users might “jailbreak” their phones to remove software restrictions imposed by Apple. Once they gain root access to their phones, they can install software not available in the App Store. Jailbreaking increases the risk of downloading malware. It can also create stability issues.
The Cortex XDR agent detects jailbroken devices, including evasion techniques designed to thwart security tools. Overall, the Cortex XDR provides strong protection for iPhones and iPads, while balancing privacy and usability requirements.
Now you can protect a broad set of endpoints, mobile devices and cloud workloads in your organization, including Windows, Linux, Mac, Android, Chrome and now iOS, with the Cortex XDR agent.
In-Process Shellcode Protection
Threat actors can attempt to bypass endpoint security controls using shellcode to load malicious code into memory. Cortex XDR’s patent-pending in-process shellcode protection module blocks these attempts. To understand how, let’s look at a common attack sequence.
After threat actors have gained initial access to a host, they typically perform a series of steps, including analyzing the host operating system and delivering a malicious payload to the host.
They may use a stager to deliver the payload directly into memory rather than installing malware on the host machine. By loading the payload directly into memory, they can circumvent many antivirus solutions that will either ignore or perform more limited security checks on memory.
Many red team tools or hacking tools, such as Cobalt Strike, Sliver or Brute Ratel, have made it easier for attackers to perform these sophisticated steps.
If a process, including a benign process, executes and allocates memory in a suspicious way, the Cortex XDR agent will single out that memory allocation and extract and analyze the buffer. If the Cortex XDR agent detects any signature or indicator that the payload is malicious, the agent conducts additional analysis on the process and shellcode, including analyzing the behavior of the code and the process, using EDR data enrichment.
If the Cortex XDR agent determines the shellcode or the process loaded by the shellcode are malicious, it will terminate the process that loaded the shellcode and the allocated memory. By killing the process chain, or the “causality,” Cortex XDR prevents the malicious software from executing.
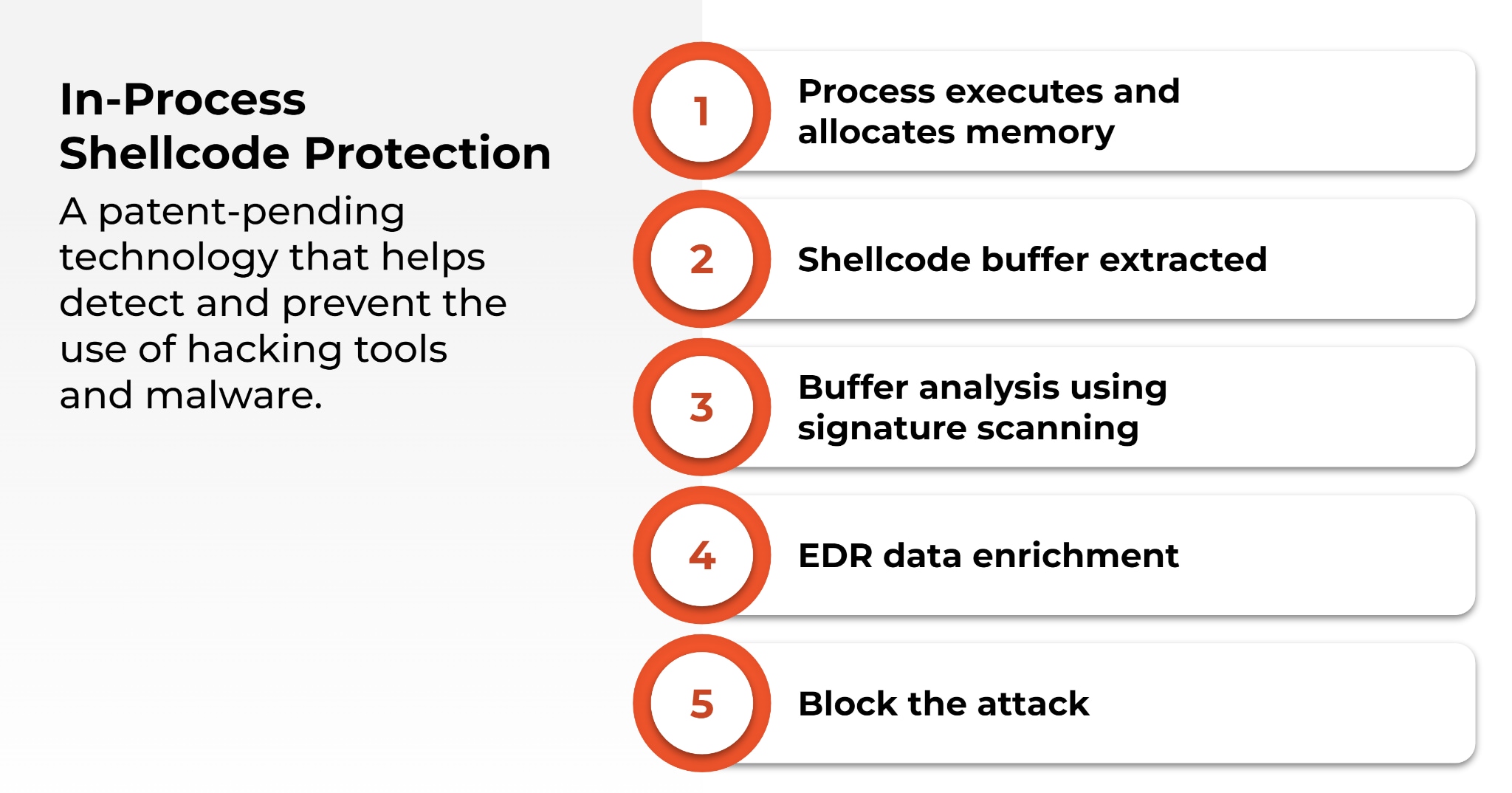
Our in-process shellcode protection will block red team and hacking tools from loading malicious code, without needing to individually identify and block each tool.
This means that if a never-before-seen hacking tool is released, Cortex XDR can prevent the tool from using shellcode to load a payload into memory.
Cortex XDR will terminate the implant once it’s loaded on the machine before it can do anything malicious.
Financial Malware and Cryptomining Protection
Whether stealing from bank accounts or mining for cryptocurrency, cybercriminals always have new tricks up their collective sleeves. To combat these dangerous threats, we’ve added two new behavior-based protection modules in Cortex XDR Agent 7.9. Let’s take a brief look at these threats and how you can mitigate them with Cortex XDR.
Banking Trojans emerged over a decade ago, typically stealing banking credentials by manipulating web browser sessions and logging keystrokes. Criminals deployed large networks of Trojans, such as Zeus, Trickbot, Emotet and Dridex, over the years. They infected millions of computers, accessed bank accounts, and transferred funds from victims. Now, threat actors often use these Trojans to deliver other types of malware to victims’ devices, like ransomware.
Cryptojacking, or malicious and unauthorized mining for cryptocurrency, is an easy way for threat actors to make money. Threat actors often target cloud services to mine cryptocurrency because cloud services provide greater scale, allowing them to mine cryptocurrency faster than a traditional endpoint. According to Unit 42 research, 23% of organizations with cloud assets are affected by cryptojacking, and it’s still the most common attack on unsecured Kubernetes clusters.
The new banking malware threat protection and cryptominers protection modules in the Cortex XDR agent automatically detect and stop the behaviors associated with these attacks. For example, to block banking malware, the module will block attempts to infect web browsers during process creation, as well as block other browser injection techniques. The cryptominers protection module will detect unusual cryptographic API or GPU access and other telltale signs of cryptojacking.
Both of these modules augment existing banking and cryptomining protection already available with Cortex XDR. You can enable, disable or set these modules to alert-only mode on Windows, Linux and macOS endpoints. You can also create exceptions per module or module rule for granular policy control.
Scope-Based Access Control for Alerts and Incidents
To address data privacy and security requirements, you might wish to control which Cortex XDR alerts and incidents your users can view. With Cortex XDR 3.5, you can control which alerts and incidents users can access based on endpoint and endpoint group tags.
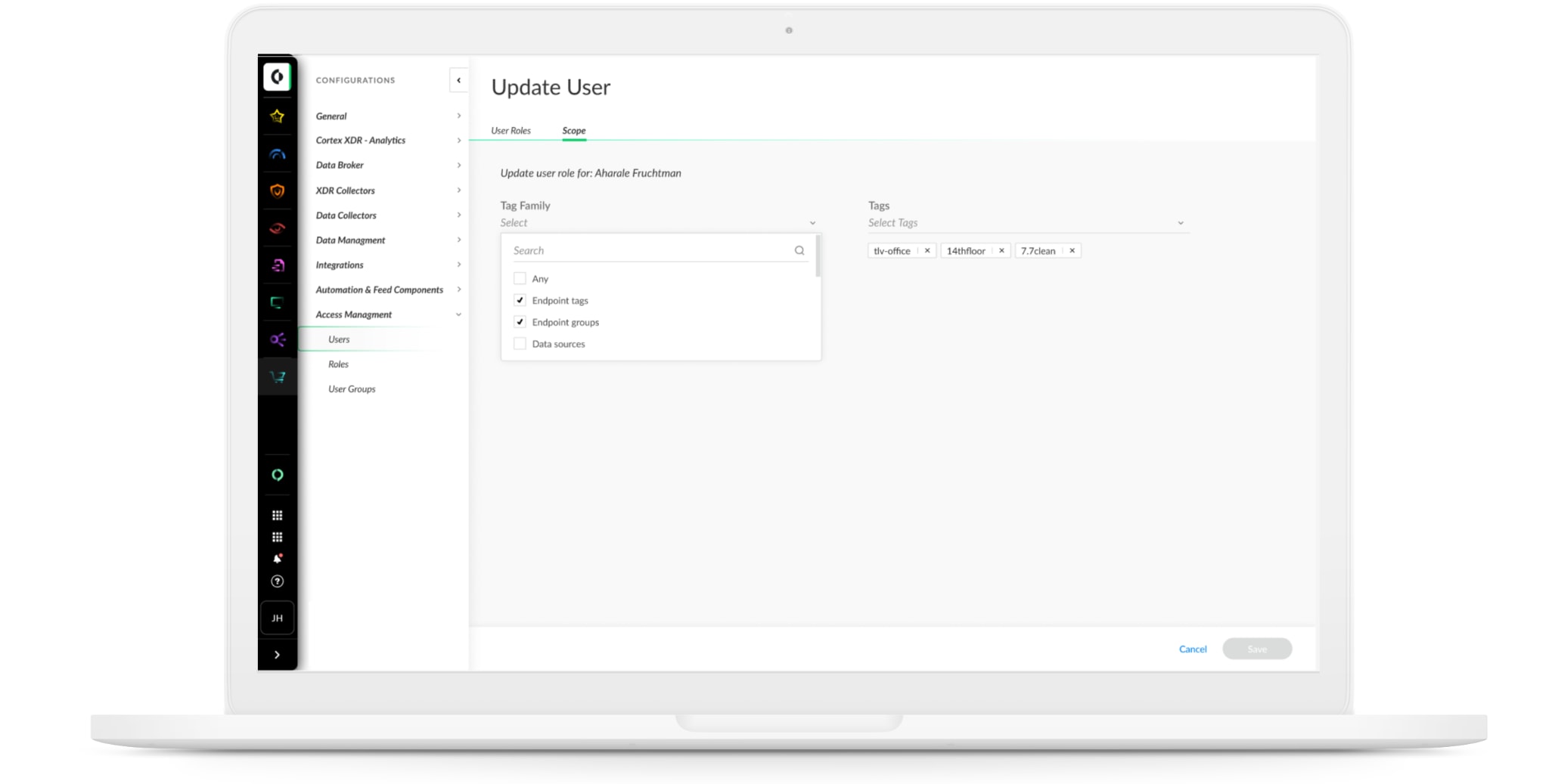
You can tag endpoints or endpoint groups by geographic location, organization, business unit, department or any other segmentation of your choice. Then, you can flexibly manage access to alerts and incidents based on the tags you’ve defined.
Alert Management Made Simple
Cortex XDR 3.5 provides several enhancements to ease alert management and reduce noise. First, you can now view and configure alert exclusions and agent exception policies from a central location. You are able to configure which alerts to suppress. You can also configure exceptions to IOC and BIOC rules to prevent matching events from triggering alerts.
A new Disable Prevention Rules feature enables you to granularly exclude prevention actions triggered by specific security modules. The Legacy Exceptions window shows legacy “allow list rules,” which are still available.
 XQL Search Integration with Vulnerability Assessment
XQL Search Integration with Vulnerability Assessment
To help you quickly hunt down threats and discover high risk assets, we have enhanced our XQL search capability. Now you can uncover vulnerable endpoints and gain valuable exposure context for investigations by viewing Common Vulnerabilities and Exposures (CVEs), as well as installed applications per endpoint. You can also list all CVEs detected in your organization, together with the endpoints and applications impacted by each CVE.
In addition, XQL search supports several new options that offer greater flexibility and control to streamline investigation and response. Notably, a new top stage command reveals the top values for a specific field quickly, with minimal memory usage. By default the top stage command displays the top ten results.
For a complete list of new features, see the Cortex XDR 3.5 and Cortex XDR Agent 7.9 release notes. To learn more about the in-process shellcode protection feature, attend the session “Today’s Top Endpoint Threats, and Advancements to Stop Them” on Tuesday, December 13, at 10:30 AM PST at the Ignite ’22 Conference.
Source :
https://www.paloaltonetworks.com/blog/2022/12/ios-devices-with-cortex-xdr-mobile/
 XQL Search Integration with Vulnerability Assessment
XQL Search Integration with Vulnerability Assessment