Do you want to use Google Search Console to grow your website traffic?
Google Search Console is a powerful free tool created by Google to help website owners understand how Google sees their website. Unfortunately, most businesses don’t know how to effectively use the full power of Google Search Console to increase their website traffic.
In this article, we will show you how to properly use Google Search Console to improve your website SEO and get more visitors.

What is Google Search Console?
Google Search Console is a free tool offered by Google to help website owners monitor and maintain their site’s presence in Google search results.
It provides essential marketing data that you need to start tracking from day one. It also alerts you about errors, security issues, and indexing problems that may affect your website’s search rankings.
You can use all this information in your WordPress SEO strategy to increase your website traffic.
The sad part is that most businesses don’t utilize the full power of Google Search Console because most of them think that just adding their website to Google Search Console is enough.
There’s so much more that you can do with the tool.
If you’re not leveraging all of the powerful features that Google Search Console offers, then you’re missing out.
Luckily, we’re here to help. We have created this ultimate Google Search Console guide to help you grow your website like a Pro.
Note: Since this is a comprehensive guide, we have added a table of contents for easier navigation.
Setting up Google Search Console
- Adding your website to Google Search Console
- Adding XML Sitemap
- Connect Google Search Console to Google Analytics
Fixing Crawling Issues
- Finding and fixing search indexing issues
- Fixing 404 errors in Google Search Console
- Fixing soft 404 errors in Search Console
- Fix server errors in Search Console
- Finding and fixing security issues
- Fixing manual actions and requesting review
Growing Your Website
- Using Google Search Console to grow traffic
- Mining keyword data in Google Search Console
- Finding low-hanging keywords where you can easily rank
- Using link reports in Google Search Console
- Getting more backlinks from third-party websites
- Improving internal linking to boost rankings
- Using Core Web Vitals in Search Console
Useful Google Search Console Tools
- Create Rich Snippets for Your WordPress Pages
- Using Google Search Console to improve mobile usability
- Mastering the fetch as Google tool
- Removing URLs from Google Search
- Adding users to access Google Search Console
1. Adding Your Website to Google Search Console
If you haven’t already done so, then you need to go ahead and add your website to Google Search Console. It is really simple and will only take a few minutes.
Simply go to Google Search Console website and click on the Start Now button.
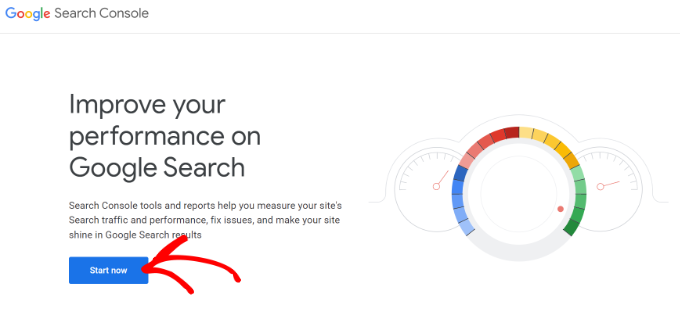
You’ll be asked to sign in using a Google / Gmail account. Once logged in, you will need to enter your website URL.
Google Search Console offers 2 methods for site verification, including domain name or URL prefix. We recommend using the URL Prefix method as it provides more flexibility.
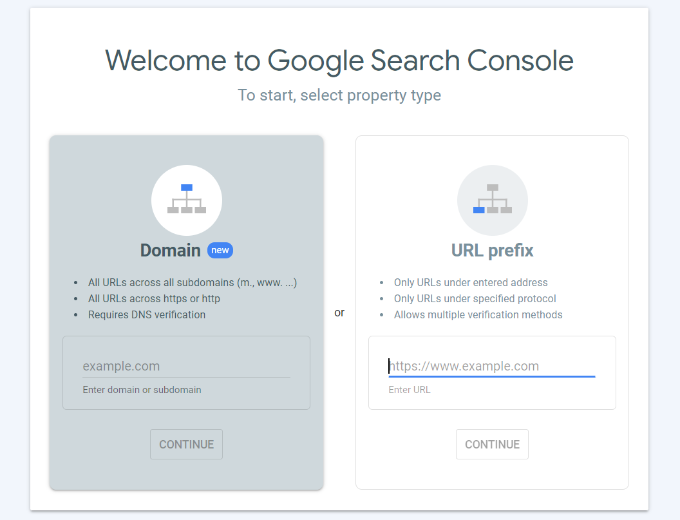
Do remember that Google considers HTTP and HTTPS as two different protocols. It also considers https://www.example.com and https://example.com as two different websites.
You’ll need to make sure that you enter the correct URL of your website.
If you are unsure, then simply login to your WordPress admin area and go to Settings » General page. There you will see your website’s URL in the site address field.
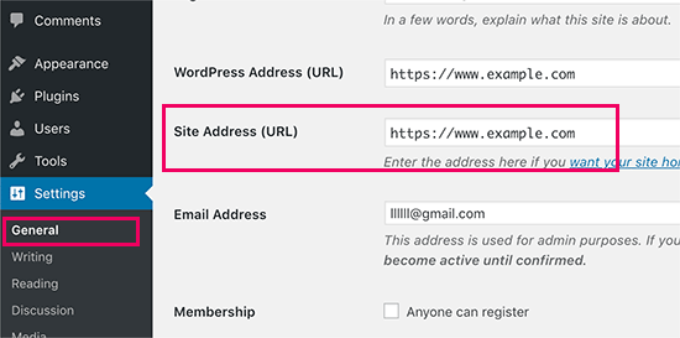
After entering your website address, click on the ‘Continue’ button.
Next, you will be asked to verify ownership of your website. There are several ways to do that, but we will show the HTML tag method because it is the easiest one.
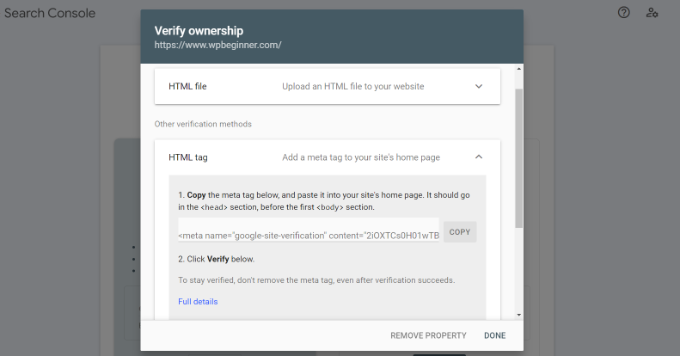
Click on the HTML tag to expand it and then copy the code inside it.
Next, you’ll need to add the code to your WordPress website so that Google can verify the ownership. However, this requires coding, which can be tricky for beginners.
An easier way of adding Google Search Console to WordPress is by using All in One SEO (AIOSEO). It’s the best SEO tool for WordPress and used by over 3 million users.
First, you’ll need to install and activate the AIOSEO Lite plugin. For more details, see our step by step guide on how to install a WordPress plugin.
Upon activation, you can go to AIOSEO » General Settings page and then click the ‘Webmaster Tools’ tab. Next, select the ‘Google Search Console’ option under Webmaster Tools Verification.
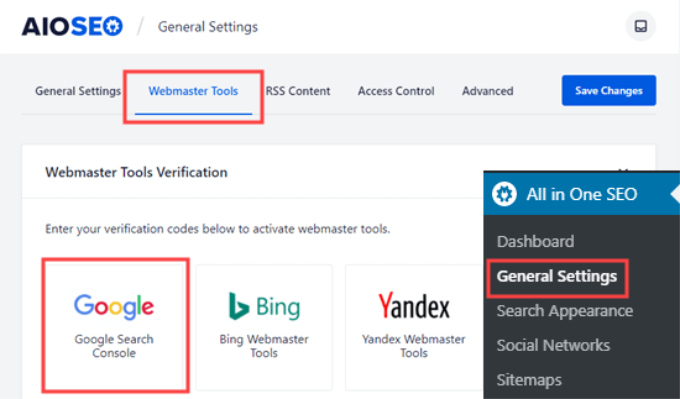
After that, go ahead and enter the code you copied earlier from Google Search Console into the ‘Google Verification Code’ box.

Don’t forget to click on the ‘Save Changes’ button to store your changes.
You can now go back to Google Search Console settings and click on the ‘Verify’ button.
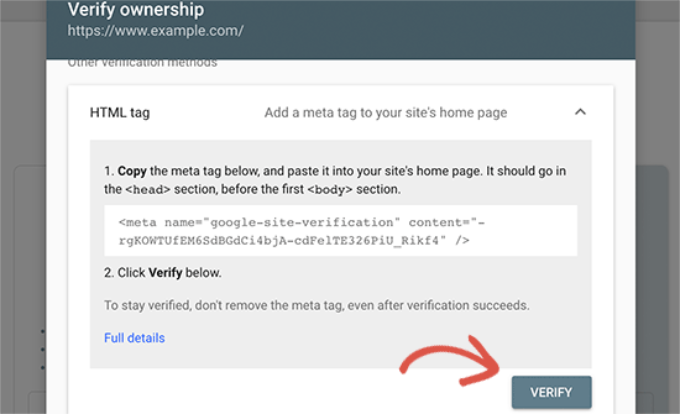
Google Search Console will now look for the HTML tag in your website code and show you a success message.
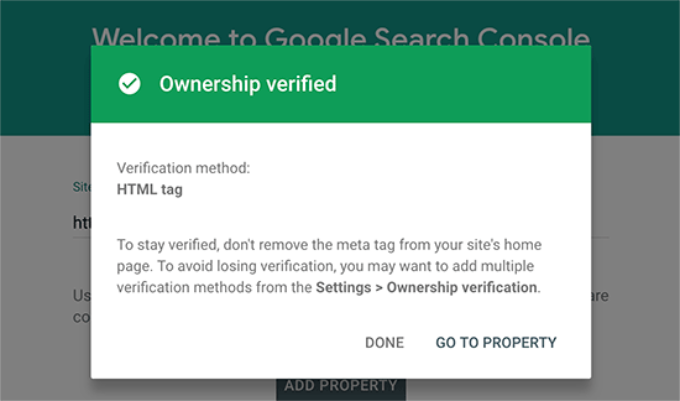
That’s all. You have successfully added your site to Google Search Console. You can now click on the ‘Go to Property’ link to visit your Google Search Console dashboard.
Note: if Google Search Console cannot verify your website after you have added the code in Insert Headers and Footer plugin, then you need to make sure to clear your WordPress cache and try again.
2. Adding an XML Sitemap
An XML sitemap is a way for website owners to tell search engines about all the pages that exist on their website. It also tells search engines which links on your website are more important than others.
Adding an XML sitemap to your website helps search engines better crawl your website. While it doesn’t give you a boost in search rankings, it can definitely help search engines index your content more efficiently.
The best part is that if you installed All in One SEO (AIOSEO) in the first step, then the plugin automatically adds an XML sitemap to your site.
To see the sitemap, you can head over to All in One SEO » Sitemaps and make sure that the toggle for ‘Enable Sitemap’ is switched on.
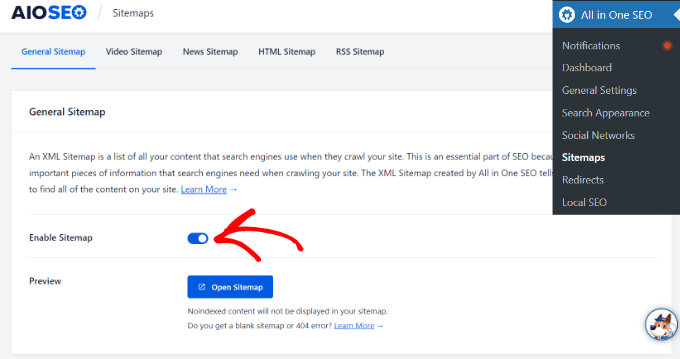
The plugin will automatically generate an XML sitemap for your website, and you can find it at the URL that looks like this:
http://example.com/sitemap_index.xml
Don’t forget to replace example.com with your own domain name. You can now submit this URL in Google Search Console.
Next, head over to the Google Search Console dashboard and then click on the ‘Sitemaps’ option from the left column. After that, you can paste the URL and click the ‘Submit’ button.
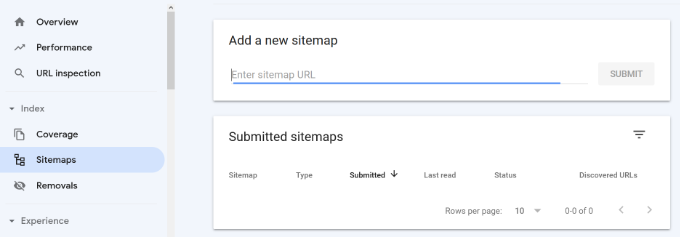
Google Search Console will now check your sitemap and use it to improve your website’s crawling. You can go through our guide on how to add a sitemap page in WordPress for more details.
3. Connect Google Search Console to Google Analytics
Connecting Google Search Console to your Google Analytics account helps you analyze search console data in Google Analytics. This provides you with a new perspective on your top-performing content and keywords.
If you haven’t already done so, then you will need to install Google Analytics on your WordPress website.
We recommend using MonsterInsights for that. It is the best Google Analytics plugin for WordPress, and it will automatically show your top keywords from Google Search Console in your WordPress admin area.
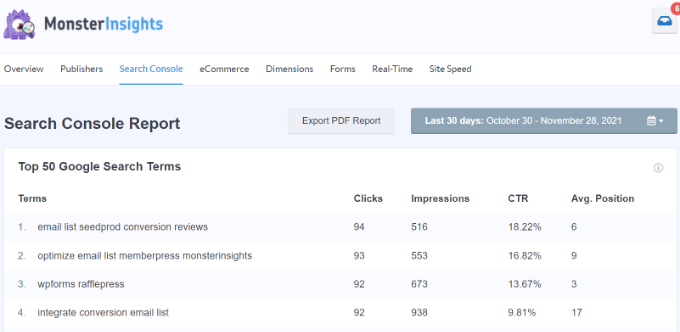
To connect Google Search Console to your Analytics account, you need to head over to Google Analytics dashboard for your website. From the bottom left corner of the screen, click on the ‘Admin’ button.
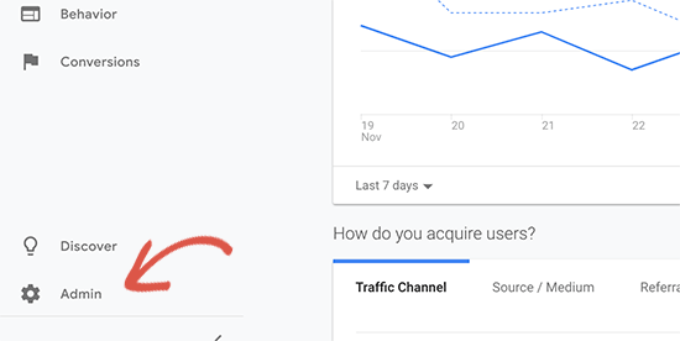
Google Analytics will now switch to the admin view. From here, you need to click on the ‘Property Settings’ section and then click on the ‘Adjust Search Console’ button.
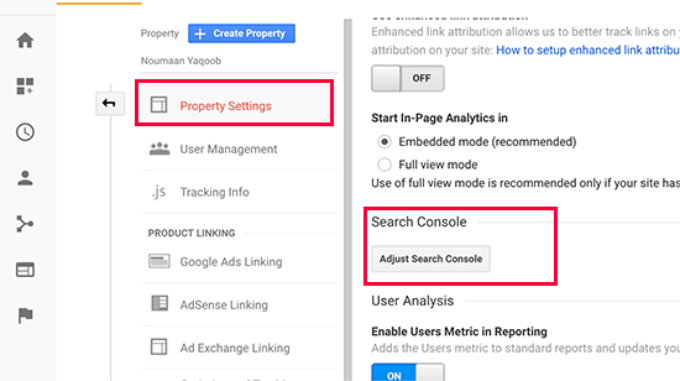
On the next screen, you need to click on the Add button to select your website.
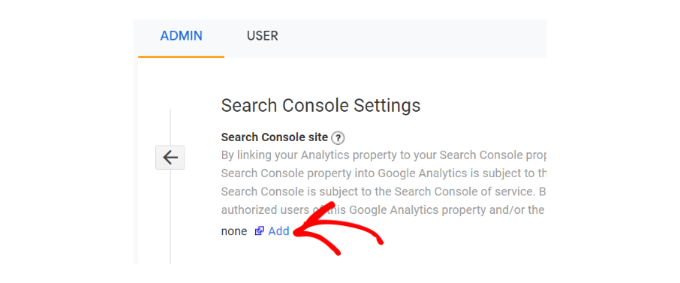
Analytics will now take you to the Google Search Console website showing you the list of all websites you have added to the search console. Select the property you want to link to Google Analytics from the dropdown menu.
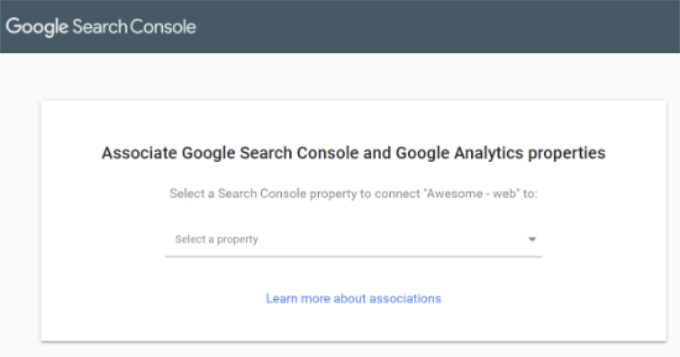
After that, you’ll need to select the Google Analytics property you’d like to connect with Search Console and click the ‘Continue’ button.
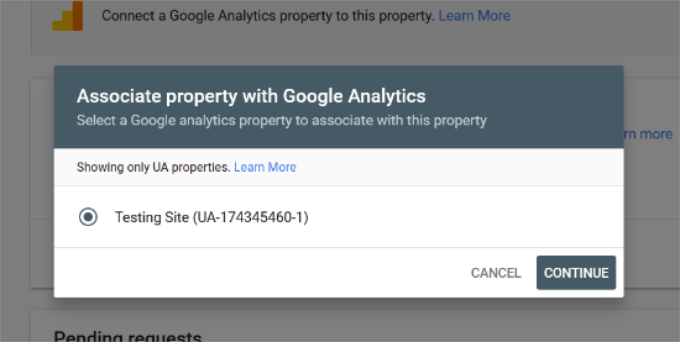
You’ll now see a popup window showing that you’ve successfully connected Google Analytics and Search Console.
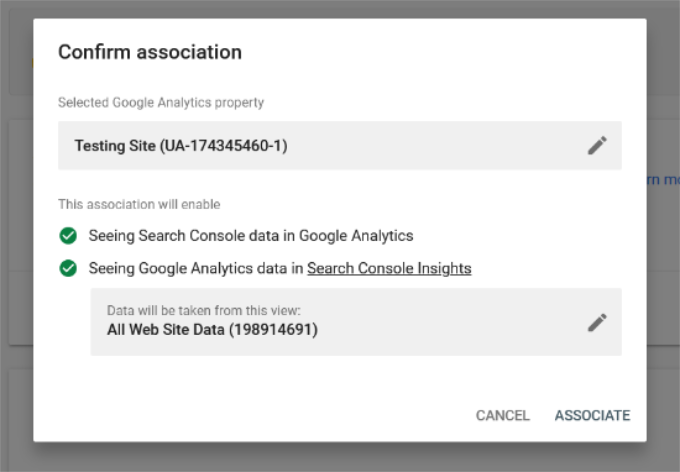
That’s all. You have successfully connected your Google Search Console data to your Analytics account. You can go back to the Google Analytics Search Console settings page to see the connected Search Console and click the ‘Save’ button.
You can now view the newly unclocked Search Console reports in your Google Analytics account under Acquisition reports. It also helps unlock keywords not provided in Google Analytics.
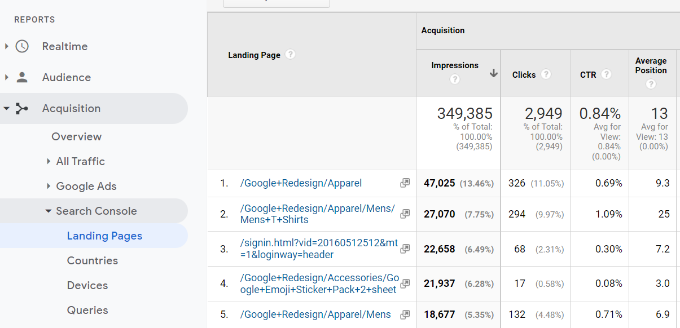
The first report you will find there is the ‘landing pages’ report.
For each landing page, you’ll see the impressions (number of times a page appeared in search results), clicks, click-through rate (CTR), and average position in the search results. Combined with that page’s analytics parameters like bounce rate, sessions, and pages per session.
Clicking a landing page will show you the actual keywords that brought users to this landing page.
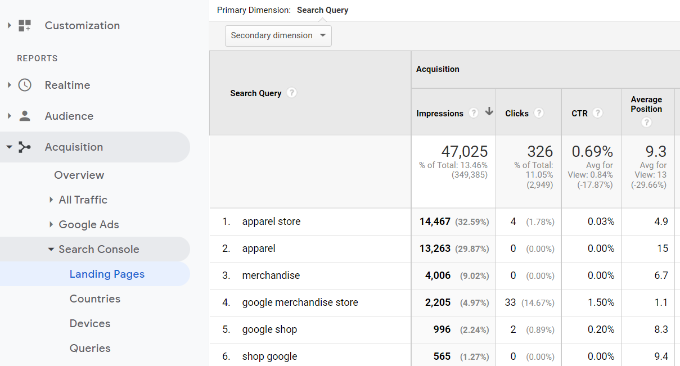
Next, you can Switch to the ‘Countries’ report, and you will see countries listed in the same order. This helps in creating content and geolocation marketing campaigns for people from different regions.
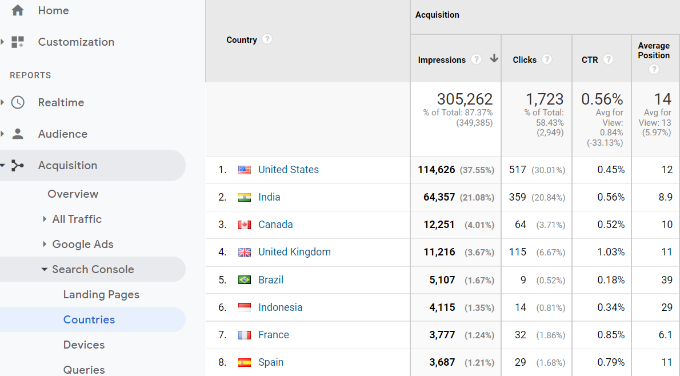
The devices report will show you how your site performed in desktop, mobile, and tablet search results.
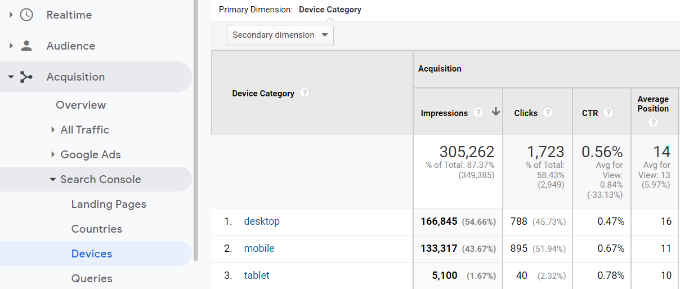
Next, Queries are the most important of all reports among this data. It shows you the keyword data missing from your Google Analytics reports. You can see which search terms are driving traffic to your site.
4. Finding and Fixing Search Indexing Issues
The most helpful feature of Google Search Console is that you can troubleshoot indexing errors.
These errors can affect your search rankings by stopping the search engine from crawling and indexing the pages on your website.
You can easily locate these errors under the Coverage report.
It shows you which pages from your website are indexed by Google and which pages resulted in an error or a warning.
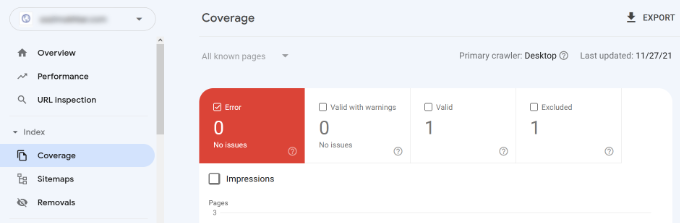
Next, scroll down, and you will see the detailed list of all the errors. Clicking on a link will open the detailed view, where you will also find the link to learn more about the error and how to fix it.
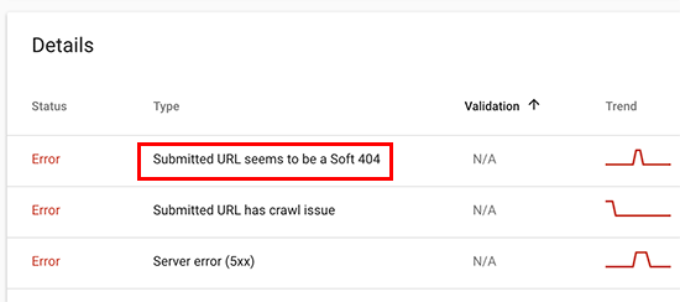
Following are a few common indexing errors you may see:
- 404 error – This error means that the crawler followed a URL and saw a 404 error.
- Soft 404 error – This error occurs when the crawler sees a 404 error page, but the page’s status code is sending a 200 (success) message to the browser.
- Server error – This means that your website server timed out or didn’t respond. This could happen if your website were under heavy traffic, was under maintenance, or unavailable for any other reason.
- Not followed – This error occurs when Google is not able to follow a content type. This could be a flash, javascript, iframe, or other resources that the crawler cannot fetch.
Now let’s take a look at how to fix some of these crawl errors.
5. Fixing 404 Errors in Google Search Console
First, you need to keep in mind that not all 404 errors are equal. You can safely ignore some of them and only fix those that are actually an error.
For example, if you deleted a blog post and don’t want to redirect users to a newer post, then it is ok to let Google see a 404 error page. Google will eventually deindex that page if it keeps seeing the 404 error.
However, the reason Google wants you to look at those 404 errors is that you may not be aware of them. For example, you accidentally deleted something or forgot to redirect users to the new updated version.
Simply click on the error in the Index Coverage report, and it will show you all the pages displaying that error. Carefully review the pages and if you see a page that shouldn’t be there, then copy its URL and open it in a new browser window.
If you see a 404 error page in your browser, then this means that you need to fix this page.
Now, if it is a page that no longer exists but you have a newer or similar version of it, then you would want to redirect users to that page. See our guide on how to set up redirects in WordPress.
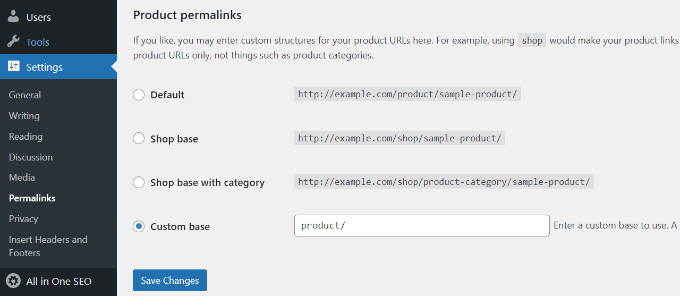
However, sometimes 404 errors may occur due to a misconfiguration in WordPress permalink structure. To fix this, simply visit Settings » Permalinks and then click on the ‘Save Changes’ button without changing anything.
6. Fixing Soft 404 Errors in Google Search Console
Soft 404 errors are a bit tricky to troubleshoot.
Basically, these errors occur when the Google bot sees what looks like a 404 error document instead of content. However, your server is sending a 200 (success) code. Normally, your server sends a 200 success code when a page is displayed without an error or redirect.
To resolve soft 404 errors, go ahead and click on the errors in the Coverage report to view the list of affected pages.
Now, you need to open the page in a new browser tab to see what’s happening. If the page displays correctly, then you can safely ignore the error.
On the other hand, if the page is showing a 404 error document, then you may want to investigate further.
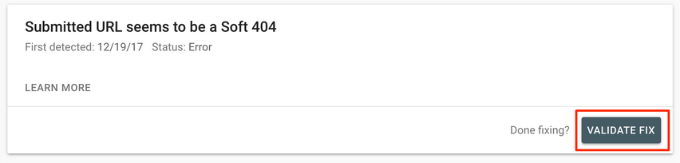
Start by clicking the ‘Submitted URL seems to be a Soft 404’ link from the Coverage report. Next, you can open the link in a new tab to check if it’s not a false alarm.
If the page is valid and you want it to appear in the search results, then simply click the ‘VALIDATE FIX’ button. Google will then recrawl the page and change the status error.
If the WordPress search function causes the soft 404 errors you are seeing, then the easiest solution is to stop the Google bot from crawling search URLs.
To do that you need to add the following lines to your robots.txt file.
| 123 | User-agent: *Disallow: /?s=Disallow: /search/ |
Usually, Google Bot doesn’t crawl search URLs. However, some spammers might try to spam Google search console reports by linking to search URLs with random strings. This way, they hope you will see their link in your Search Console report and click on it.
If the affected URLs are not searched queries, then you may want to redirect them to a proper page on your site.
7. Fixing Server Error in Google Search Console
Server Errors in Google Search Console are caused by a number of reasons. The most common of them is when your server times out during a crawl, throws an unexpected error or does not appear to be online.
Use the ‘URL inspection’ tool to make sure that the affected URL is working.
If it is working, then you can ignore the error. If you are on a reliable WordPress hosting provider, then most server errors would disappear automatically.
However, if you can confirm the error by visiting the URL, then there are several things you can do to fix it. See our list of most common WordPress errors guide to find a fix for the specific error message you are seeing.
8. Finding and Fixing Security Issues
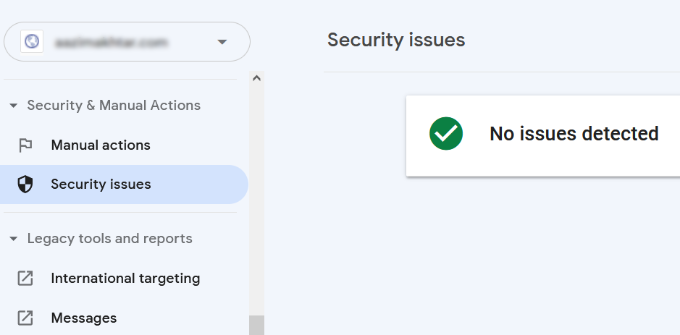
Security issues not only stop Google from crawling your website, but they could also cause a sudden drop in search traffic. Google may temporarily remove affected pages, show a warning to users, and drop a page’s ranking.
Security issues will be highlighted on the overview screen as you login to your Google Search Console account. The most common security issue is websites affected by malware and trojans.
To fix this, see our guide on how to clean a hacked WordPress website for step by step instructions.
For more details, see our article on how How to fix a website after getting de-indexed by Google and ultimate WordPress security guide.
9. Finding Manual Actions and Requesting Review
While security issues are automatically triggered, manual actions are the penalties that are imposed by human staff from the Google Search team after a careful review. If a manual action is taken against your website, then this is pretty significant and can immediately take away all your search traffic.
These manual actions usually occur when a website is involved in illegal activities, spamming, and other fraudulent or fishy activities.
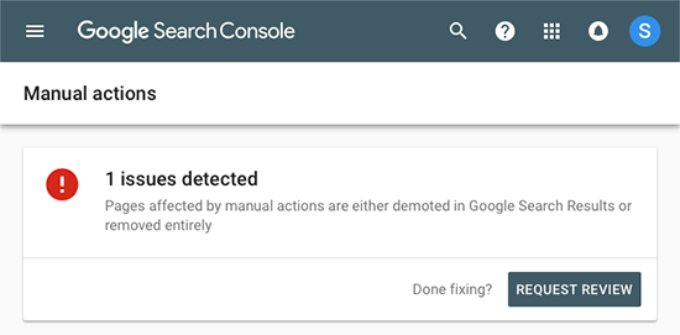
Clicking on the Manual Actions link will show you the actions in your search console report. You will also find detailed information about the issue that triggered it and how to clean it up.
Once you have removed the objectionable content, you can click on the request review button. Your website will now be reviewed and reconsidered by the Google Search team, and they can decide on removing the penalty.
10. Using Google Search Console To Grow Traffic
Now that we have covered the technical bits, let’s get to the fun part of growing your website traffic by utilizing the data available in Search Console.
Google Search Console helps you uncover keyword data, find out your top-performing keywords, and discover hundreds of potential keywords where you can easily rank and get more traffic.
We will also look at links and how to use them to improve search rankings.
Ready? Let’s get started.
11. Mining Keyword Data in Google Search Console
Keywords are the search terms users type in search engines to find information.
Marketers and website owners can optimize their content to target desired keywords and improve their chances of appearing on top in search results.
Previously, keyword data was available in website stats and analytics reports in Google Analytics. However, Google encrypted that information in 2013 when they switched to HTTPS.
As a result, if you try to view search queries in Google Analytics, you’ll most likely see ‘not provided’ keywords. A simple solution to this issue is connecting Google Analytics with Search Console.
You can also view the keyword data in your Google Search Console reports.
It gives you a full view of the keywords your website is ranking for, average position, clicks, and impressions (number of times your site appears for that keyword).
You can see this information in your Google Search Console reports under the ‘Performance’ tab.
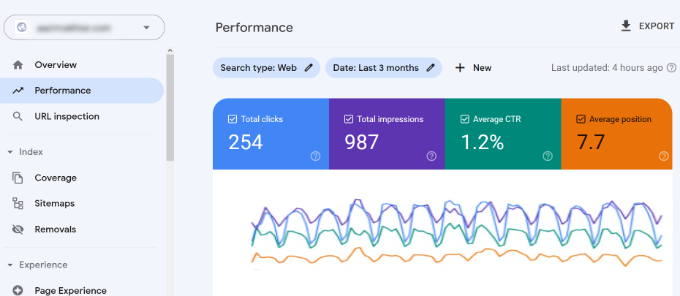
On the top, you will see a graph of your website’s performance in search results. Below that, you will see the keywords data, which you can filter by position, impression, and click-through rate.
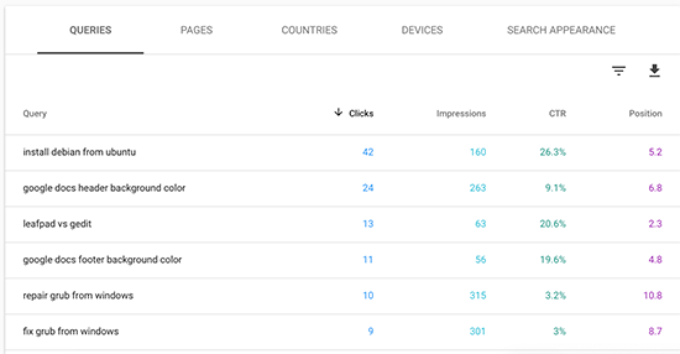
You can sort this data by clicking on any column or using the filter option to narrow down the results.
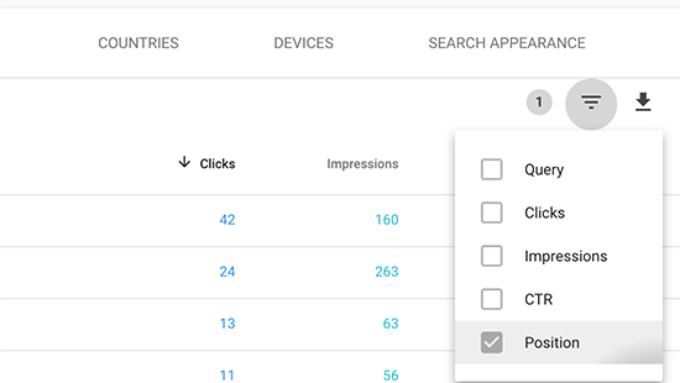
You can also switch to the Pages tab to see the performance of your pages in search results.
Clicking on any page in the list will filter the results for that page. You can then switch to the ‘Queries’ tab to see the keywords that bring the traffic to that particular page.
Now that we have covered how to browse and view this data, let’s see how actually to use this in your SEO and content planning.
12. Finding Low-hanging Keywords That You Can Easily Rank
A lot of your pages may be ranking on page 2 or 3 of Google search results for different keywords. These are the keywords that you can quickly work on to rank higher and get more traffic.
Let’s find out those keywords.
In your Performance report, click on the filter icon and then select the ‘Position’ option. Next, you’ll be looking for keywords where the average position is higher than 7.
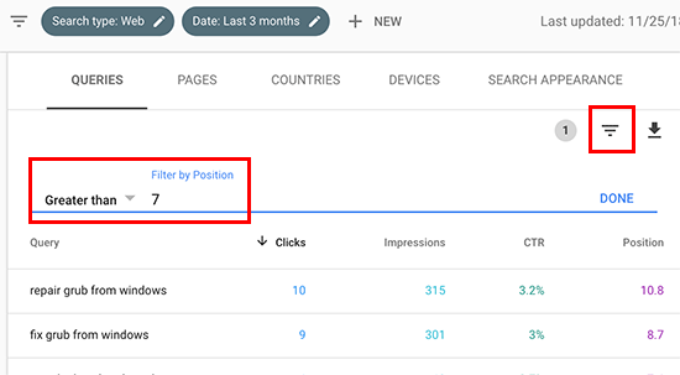
Search Console will now only show the keywords where your site appears on an average position of 7 or higher. Now, click twice on the position column to sort the list in ascending order.
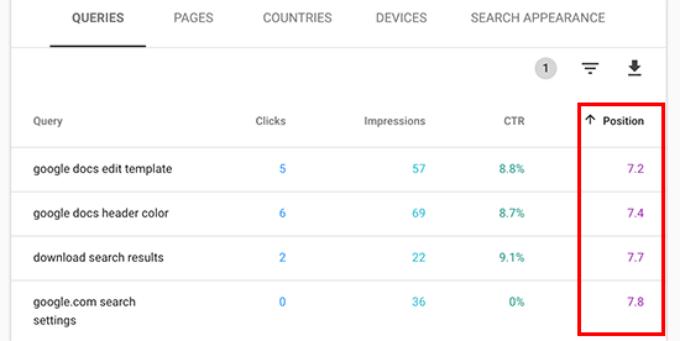
As you scroll down, you will find tons of keywords that rank between 7 and 30. All these keywords are low-hanging fruits where you can easily rank higher.
To view more results, scroll to the bottom and select a higher number for ‘Rows per page.’
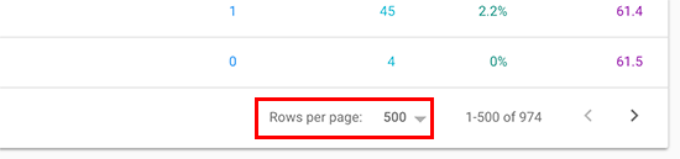
When choosing the keywords to work on, you would want to choose keywords based on their number of impressions. Higher impressions mean more search traffic for those keywords.
To do that, you can export the data in CSV format and then open it in spreadsheet software.
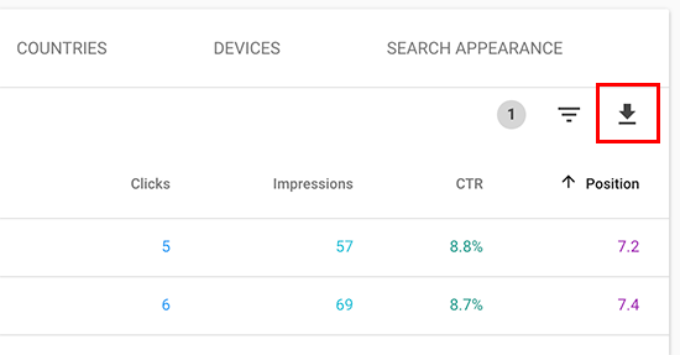
Now that you have mined the low-hanging keywords with higher impressions, the question is how do you improve your rankings for those keywords?
Here are some tips to help you improve your rankings for those keywords.
1. Improve the content by adding more useful information
The #1 reason your page isn’t ranking for a keyword is that Google finds other content more valuable. To counter that, you need to review your article or blog post and add helpful content.
Look at the articles ranking on top five positions for that keyword and cover all the information that your article is missing in more detail.
We are not saying that you should just add more text to it. You need to make it more useful, informative, and comprehensive.
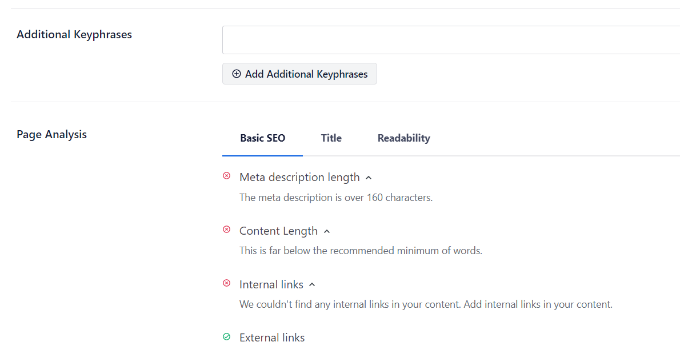
2. Evaluate On-page SEO
Use All in One SEO (AIOSEO) to improve the on-page SEO score for that article. It gives practical tips on improving a page by analyzing the content, keyword density, title, readability, links, and more.
You can also check out our guide on the SEO audit checklist to boost your rankings.
3. Increase time users spend on that page
Google considers it a success when users click on a search result and spend time viewing it. This means your content needs to be highly engaging and instantly provide users with the information they were looking for.
Here are some crazy simple things you can do to increase user engagement.
- Use images – users find images much easier to look at than text. Adding more images makes it easier for users to scan the information and keeps them engaged.
- Use videos – Videos are the most engaging form of content available. Adding video to a page significantly increases the time users spend viewing that page.
- Make text more readable – Use smaller paragraphs, lots of white space, simpler sentences, and keep your style casual and conversational. All these things make reading easier for users.
For more tips, see this article on how to increase time users spend on your site.
13. Using Link Reports in Google Search Console
Links play an important role in WordPress SEO. Search engines use them as a metric to determine how important a page is and where it should rank in search results.
The Links report in Google Search helps you see your website’s performance in terms of links.
It shows you external links, internal links, top linking sites, and top linking text. More importantly, it shows top linking sites, how often they link to your site, and how many pages they link to.
Let’s see how you can use these reports to get more backlinks, improve internal links, and boost your rankings.
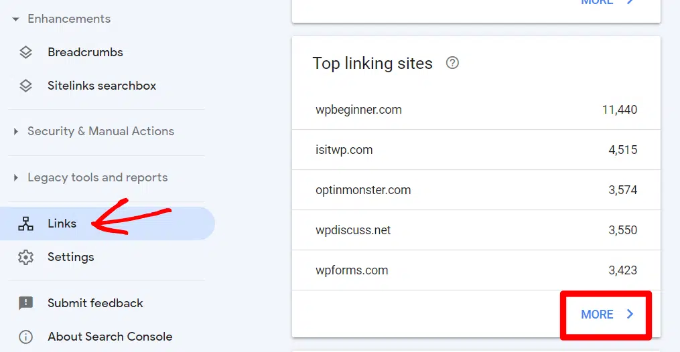
14. Getting More Backlinks from Third-Party Websites
Search console shows third-party websites that have linked to your site in the ‘Top linking sites’ report. You can expand the report by clicking on the ‘More’ link at the bottom.
If you click on a domain name to expand the report, you will see all the pages they have linked to. Next, click on each page to get the exact URL linked to that particular page.
You can now use this data to get more backlinks for your site. Simply visit the website and see how they have linked to you. After that, see what other content they have where your site can be linked from.
Next, simply reach out to the website via email or contact form on their website.
First, thank them for linking to your article and then politely mention that they may want to include a link to an article of yours.
Now, this direct approach may not always work. In that case, you need to be creative. You can offer them to write a guest post for their blog, leave comments on their articles, follow them on social media, or retweet their articles.
Repeat the process for all important external links on your website. With consistent effort, you can get proper backlinks without spending any money.
15. Improving Internal Links to Boost Rankings
It is harder to get third-party websites to link to your content. However, it is way easier to link to your own content from your own site. This practice is called internal linking.
Internal linking helps search engines understand the context and relationships among different pages on your website. It also helps them understand which pages are important based on how often you have linked to them.
This is why you should make internal linking a habit when writing new content on your website or blog.
Now let’s see how to use the links reports in Search Console to help you build internal links.
In Google Search Console, click on the Links report and then click on the ‘More’ link under the ‘Internal Links’ column. The report shows how often you have linked to other pages on your site.
Go ahead and click the filter icon and then select the ‘Target page’ option.
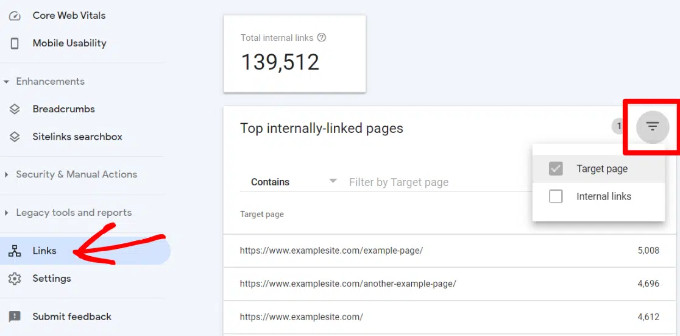
Search Console will now show you how many pages are linking to this page. You can now compare it with other pages and see whether pages with more internal links are ranking higher than posts with many internal links.
If that’s the case, then go ahead and start adding internal links to pages that you want to rank higher. Make sure you are only linking to the article when it makes sense. Adding links where they don’t make sense would create a bad user experience.
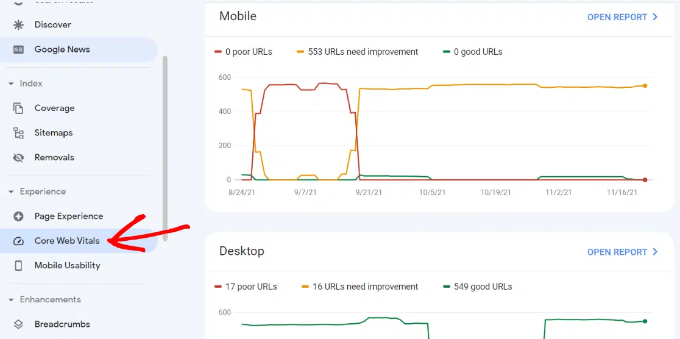
16. Using Core Web Vitals in Search Console
Did you know that Google now considers your website loading speed as a ranking factor?
In 2020, Google introduced Core Web Vitals that measures how fast your website is and help the search engine measure your site’s user experience.
In Google Search Console, you can view the ‘Core Web Vitals’ report under the Experience menu on your left. It provides a complete report about your site’s speed score for mobile and desktop.
The best part is that you also get recommendations on how to improve your Core Web Vitals score and improve your site’s load time.
For more information, please refer to our guide on how to boost WordPress speed and performance.
17. Create Rich Snippets for Your WordPress Pages
Rich snippets or schema markup allows Google to display additional information in its search results. These include star ratings, prices, reviews, and more.
Rich snippets make your page more noticeable in the search results. As a result, you get more clicks and website traffic.
Many WordPress themes automatically include some basic structured data. If you publish recipes, run a reviews site, or an online store, then rich snippets can give your site an SEO boost.
Google Search Console makes it very easy to find pages that are displaying rich snippets. It also shows the type of rich snippets for your website.
You can view them by going to ‘Overview’ and then scrolling down to the ‘Enhancements’ section.
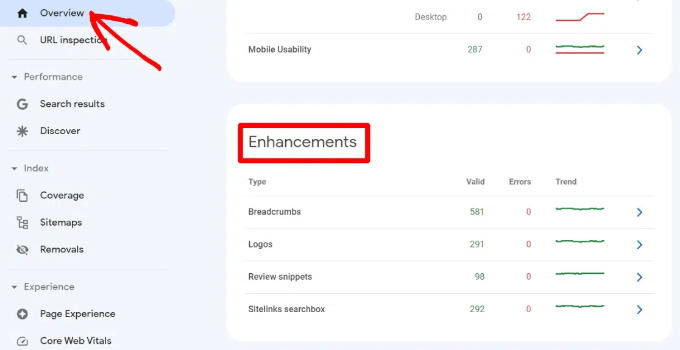
The real useful part is that the report allows you to quickly look at pages that have errors while displaying rich snippets so that you can fix them.
If you want to learn more about setting up rich snippets, then please see our guide on how to add schema markup in WordPress and WooCommerce.
18. Using Search Console to Improve Mobile Usability
Nearly 63% of all Google searches in the United States come from mobile devices. That’s why Google gives an SEO bump to mobile-friendly websites in the search results.
Google has a Mobile-Friendly test tool that allows you to quickly examine a page. The Mobile Usability report in Search Console tells you how Google sees your entire website in mobile performance.
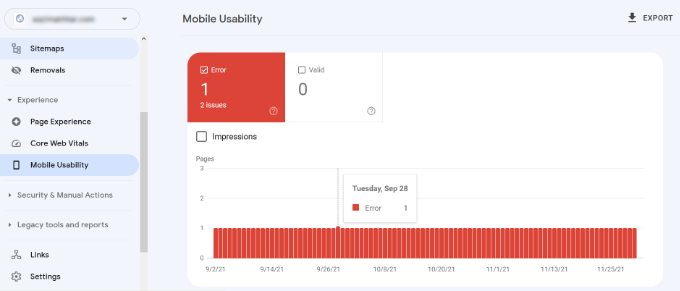
If you see errors on this page, then this means that these issues may affect your site’s rankings.
To see the affected pages, you can scroll down to the ‘Details’ section and click on the error.
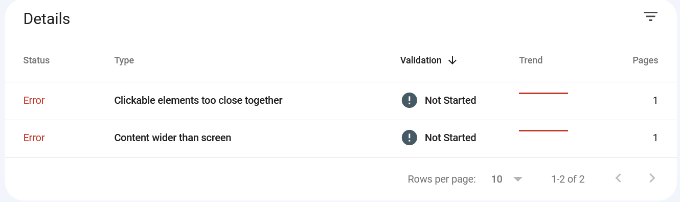
Poorly coded WordPress themes or plugins cause most mobile usability issues. The easiest way to fix those issues is by using a better responsive WordPress theme.
19. Use URL Inspection Tool in Search Console
The URL Inspection tool in Google Search Console provides information about a page if it’s on Google search results or not.
You can check the status of a page and also request Google to recrawl a page. To start, simply enter a URL in the top search bar.
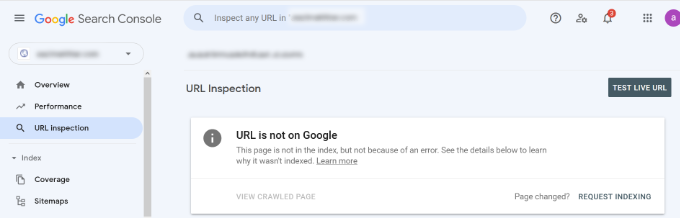
Google Search Console will then show you the status of the page is indexed by Google. If it’s not indexed, then you’ll see a message saying ‘URL is not on Google.’
You can click the ‘Requesting Indexing’ button and request Google to manually fetch the page from your website.
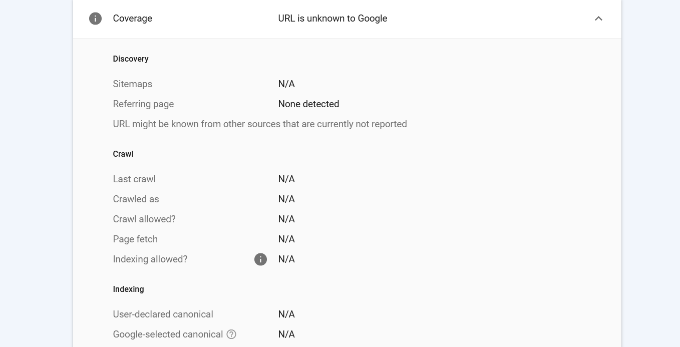
Besides that, you can scroll down and see more details in the ‘Coverage’ report. It will show information about sitemaps, crawl history, and indexing.
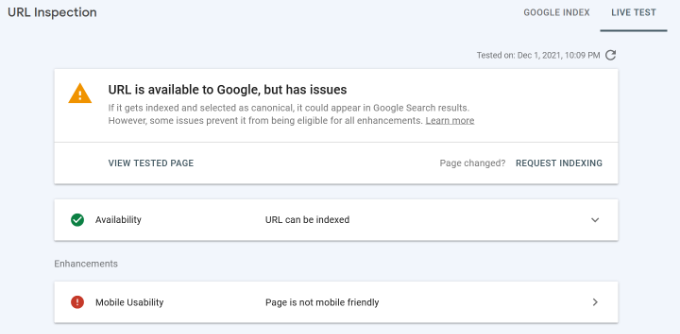
You can also live test a URL and see if there is an indexable version available. If there is, then simply click the ‘Request Indexing’ option.
20. Removing URLs from Google Search
So far, we have focused on using Search Console to get your content indexed and improve rankings in Google Search. However, sometimes you may want to remove content from Google Search as well.
One way to do this is to add a noindex meta tag to the page you want to remove from search results. However, depending on how often Google crawls your website, this could take some time before your page actually disappears from search results.
Search Console’s Remove URL tool allows you to request a URL to be removed from the search results. Simply click on ‘Removals’ under Index in the menu on your left.
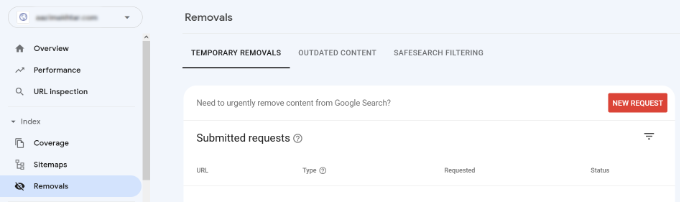
Now click on the ‘New Request’ button, and a popup window will appear. Go ahead and enter the URL you want to remove, select whether you want to remove this URL only or with this prefix, and click the ‘Next’ button.
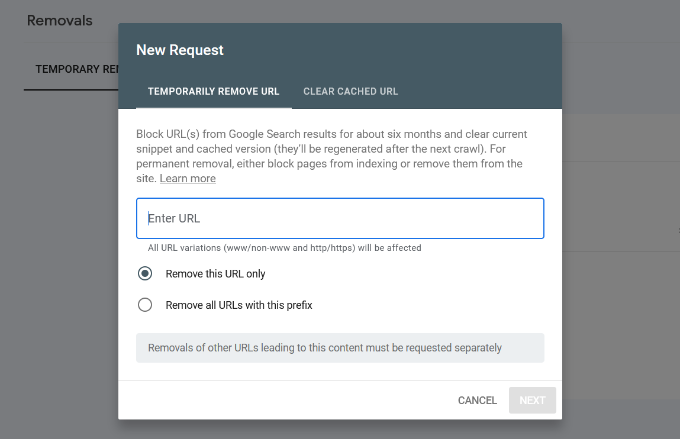
Google will now block the URL from its search results for about six months. You can add as many URLs as you want and see them in the Removals section in the Search Console.
21. Adding Users to Access Google Search Console
If you have a marketing team or you have hired someone to help you with SEO, then those users may need access to Google search console data.
Search Console allows you to easily add users and give them access to view all reports without sharing your Google account credentials with them.
To add a new user, simply click on the Settings » Users and permissions option under Property settings and then click on ‘Add User’ button.

Next, you need to provide the user’s valid Google account email address and select permission to grant them.
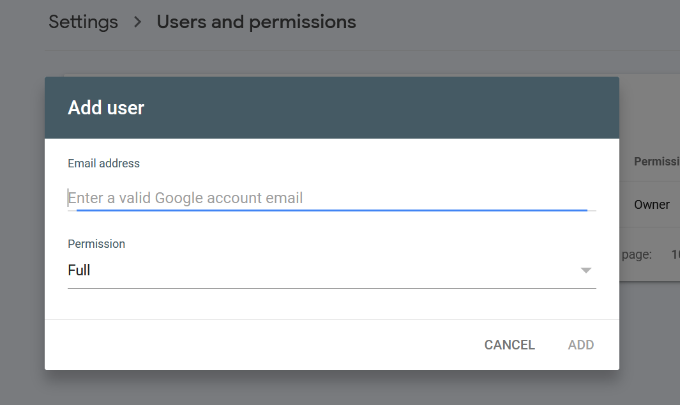
There are two types of permission levels. The full permission level will give them access to everything, including the ability to add new users. Restricted permissions will allow them to view the data but not add new users.
After choosing a permission level, click on the ‘Add’ button to save your changes.
The user you added will now receive an email notification, so they can login and view Google Search Console data for your website.
Helpful Resources
Following helpful resources on WPBeginner will help you further improve your website’s performance in search engines.
- Ultimate WordPress SEO Guide – Our complete step by step WordPress SEO guide will walk you through complete WordPress SEO setup like a pro.
- WordPress Performance Guide – Step by step guide to improve your WordPress speed and performance for higher search rankings and better user experience.
- WordPress Security Guide – Keep your WordPress site secure with this complete WordPress security guide for beginners.
- Tracking User Engagement – This guide helps you learn how to track user activity on your website and use it to plan your growth strategy.
- Convert visitors into Customers – If you run an online store, then this guide will show you how to convert search traffic into paying customers.
We hope this article gave you some good tips on using Google Search Console more effectively to grow your site. You may also want to see our guide on the best managed WordPress hosting and how to move WordPress from HTTP to HTTPS.
If you liked this article, then please subscribe to our YouTube Channel for WordPress video tutorials. You can also find us on Twitter and Facebook.
Source :
https://www.wpbeginner.com/beginners-guide/google-search-console-ultimate-guide/












.jpg)