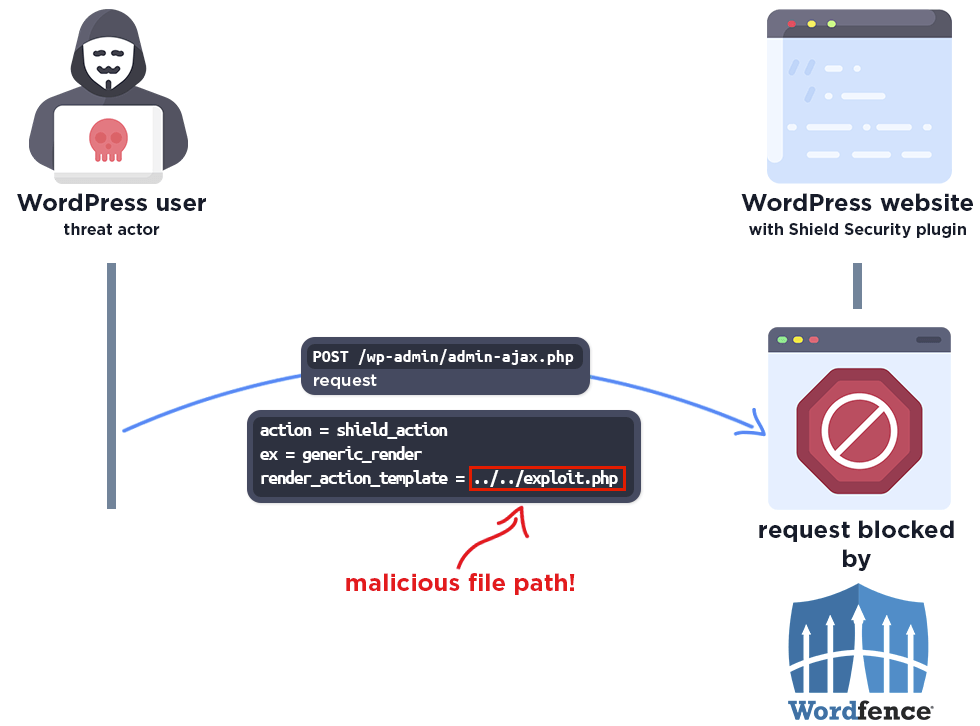
Ruchi Tandon
August 25, 2022
Looking to rapidly migrate to the cloud? Scale cost-effectively and strengthen disaster recovery? You’re not alone. Here’s how organizations are unlocking the power of hybrid cloud with VMware Cloud on AWS.
As we welcome back customers, partners, colleagues, and friends of VMware in person once again at VMware Explore 2022, one thing is unchanged – the impact that VMware Cloud on AWS has had on our customers’ cloud migration journeys.
In this blog, I want to highlight some of the recent customer stories and share our customers’ experiences with VMware Cloud on AWS. Also, check out Part 1, Part 2, Part 3, Part 4, Part 5, and Part 6 of this blog series for more customer stories across various use cases.
Schibsted Media Group
Schibsted Moves to the Cloud to Support Rapid Expansion and Gain Competitive Advantage
Schibsted Media Group, or Schibsted, a leading media corporation in Scandinavia, wanted to create a unified digital platform for its 55+ brands portfolio, allowing each company to scale operations easily. To support their rapid growth, Schibsted’s team also knew that having a cloud strategy in place would be beneficial when acquiring new companies. It would also significantly reduce time and resources otherwise spent managing multiple vendors and local data centers.
With VMware Cloud on AWS, the team at Schibsted was able to shut down 350 on-premises servers and migrate traditional workloads and legacy software to the cloud faster than expected. Their enterprise systems running apps such as Newspilot, SAP, HR systems, and a variety of advertising platforms now all run on VMware Cloud on AWS. Working with VMware, Schibsted has achieved considerable cost savings compared to on-premises data centers and hopes to save more on operating costs with every new acquisition in the future.
Here is what Schibsted has to say about their experience of using the service:
“We have a public cloud strategy, and traditional workloads are now running on VMware Cloud on AWS. It is a scalable platform that we are taking full advantage of to become cloud-native. We were one of the first customers in the Nordics who started using it.”
– Ken Sivertsen, Cloud Infrastructure Architect, Schibsted Enterprise Technology
Check out the case study to learn more about their experience of using VMware Cloud on AWS.
Lotte
Lotte Moves to the Cloud for Future-Readiness
When several divisions of Lotte merged into a single corporate entity in 2018—the year of its 70th anniversary—they decided to embark on digital transformation (DX) journey to enhance synergies and encourage business growth. After merging, Lotte found it challenging to ensure smooth business operations and employee experience due to silos between the merged departments. This had the potential to impact business development. Moreover, Lotte had been operating an on-premises VDI environment on Windows 7. When Windows 7 support ended, there was an urgent need to move to Windows 10 to strengthen the Lotte VDI resources and improve their system more broadly.
Lotte decided to use VMware Cloud on AWS because it offered the agility and flexibility of the cloud with a proven track record and made migration easy. With the help of VMware and partnering with DXC Technology Japan, and AWS Japan, Lotte has now migrated 4,000 VDI units to VMware Cloud on AWS. Doing so has improved employee experience and maximized business profitability. It has also positioned them well for future expansion and helped them reduce the time needed for infrastructure maintenance and operations.
Here is what Lotte has to say about their experience of using the product:
“We’re currently running VMware Cloud on AWS VDI environment alongside our on-premises environment and there is no difference between them. The user experience is virtually unchanged and everyone finds it easy to use.”
– Mr. Hisaaki Ogata, Senior Manager of ICT Strategic Division, Lotte Corporation
Read their customer story here in detail.
KDDI Corporation
KDDI Corporation Innovates from Modern Applications.
Keeping its agile mindset front and center, KDDI Corporation needed a go-to-market strategy to deploy its applications and deliver new services more rapidly than before. Their developers wanted the ability to concentrate on app development above all things. They also wanted monitoring, log collection, and security features integrated into the platform. In addition, the IT team at KDDI expected their environments to become more and more complex as KDDI deployed applications at the edge and in the cloud.
Solutions like VMware Cloud on AWS and Project Pacific helped KDDI achieve consistent control over such complex environments with a single portal.
Here is what KDDI Corporation has to say about their experience of using the product:
“Going forward, our environments will become more and more complex as we deploy applications at the edge and in the cloud. So, we are looking to VMware Cloud on AWS and Project Pacific to help us achieve consistent control over such complex environments with a single portal.”
– Takeshi Maehara, General Manager, KDDI Corporation
Learn more about KDDI’s story here.
State of Louisiana
State of Louisiana Unifies IT Service Delivery, Improves Medicare Enrollment, and Rapidly Responds to Disasters with VMware Cloud on AWS
Reforming government is a constant process requiring continuous innovation, creativity, and vigilance, including the technology on which government operates. For the State of Louisiana, that meant embarking on a statewide initiative to transform security and modernize data center operations. The goal: Take IT from legacy mainframes to cloud-based, mobile-ready application delivery. Louisiana decided to partner with VMware to modernize its data centers, transform digital workspaces for users, and move toward a common operating model that spans both private and public clouds.
To extend its on-premises data centers and easily migrate application workloads to the public cloud, the state decided to use VMware Cloud on AWS. With VMware SDDC software running on the AWS cloud, the state can seamlessly integrate with the public cloud and scale easily while leveraging existing VMware skill sets. It can also use familiar tools, such as vRealize Suite and NSX, to extend intelligent operations and micro-segmentation to the public cloud, helping keep its environment manageable and secure. As Louisiana adopts a public cloud-first strategy to reduce costs further, it will use VMware Cloud on AWS to evolve into DevOps methodologies and become an even more efficient broker of IT services.
Here is what the State of Louisiana has to say about their experience of using the product:
“VMware Cloud on AWS will help us take advantage of the elasticity of public cloud, giving us workload portability, a platform for next-gen apps, and easy access to AWS services.”
– Michael Allison, CTO, State of Louisiana
Learn more about State of Louisiana’s experience of using VMware Cloud on AWS in this case study
GuideOne
VMware Cloud on AWS Enables Cloud-Native Capabilities Without Increasing IT Budget For GuideOne
GuideOne, an insurance firm in the United States with over 600 employees and more than $500 million in annual revenue, maintains an environment of 16 ESXi hosts and 800 virtual machines (VMs).
The organization faced several challenges that prompted its investment in VMware Cloud on AWS. They supported workloads with on-premises hardware but wanted to move to the cloud to avoid the headaches and costs associated with managing its on-premises deployment. The organization also wanted the cost and capability benefits of cloud computing, but it wanted to minimize the likelihood of outages, delays, and cost overruns that could occur when migrating legacy workloads to the public cloud.
The move to VMware Cloud on AWS produced some great results:
- Eliminated 40% of its data center footprint and reduced power costs
- Reallocated resources to strategic IT initiatives
- Invested in its own employees and avoided costs of recruiting cloud-native skills
- Avoided hardware expansion and refresh costs
- Avoided costly application rearchitecture
- Flattened IT budget while providing business with new capabilities
- Enabled a more responsive and compliant security environment
Here is what GuideOne has to say about their experience of using the product:
“[VMware Cloud on AWS] is a quick way of getting into the cloud. You don’t have to do as much QA when it comes to switching over the workloads because you are doing it at the hypervisor level, and you’re really only worried about performance and latency.”
– IT Director, GuideOne
Read more about their experience here.
A Global Financial Firm
VMware Cloud on AWS Provides Frictionless Path to Capital and Operational Cost Savings to a global financial services firm
A global financial services firm headquartered in the United States with over 10,000 employees and more than $3 billion in annual revenue, now maintains three software-defined data centers (SDDCs), with a total of 42 hosts and roughly 800 virtual machines (VMs).
Prior to investing in VMware Cloud on AWS, the organization relied on outsource vendors to maintain its data centers. When the contract was up, the organization could not easily switch providers and did not want to reinvest in building a new data center. In an on-premises environment, the organization was also limited to inefficient disaster recovery processes, which hindered development teams. Additionally, a portfolio of 150 applications, many of which were legacy applications, meant unnecessary maintenance and operations costs. The organization was struggling to modernize its application portfolio due to the speed of service of the vendors managing its on-premises environment.
The business decision-makers were vary of upcoming data center deadlines
The move to VMware Cloud on AWS produced some great results:
- Retired on-premises data center and reduced annual operating costs by 59%
- Avoided costly infrastructure refreshes, saving ~$10M
- Reduced downtime
- Improved IT agility
- Modernized application portfolio, saving $200K in annual spend
- Improved business resilience across 35 offices during the pandemic by being in the cloud
Here is what this Financial Services organization has to say about their experience of using the product:
“Modern applications require modern infrastructure. So today we’re upscaling, we’re new-skilling, and we’re reskilling. I’ve been trying to retire apps my whole time here and was not able to until we moved to the cloud [with VMware Cloud on AWS]”
– Associate Director of Cloud Infrastructure, Financial Services organization
Read more about their experience here.
So don’t wait any further. Start your cloud migration and application modernization journey with VMware Cloud on AWS. If you are interested in finding out how much you could save, try the VMware Cloud on AWS TCO Calculator. To learn more about VMware Cloud on AWS, here are some learning resources. Or, you can get started now with VMware Cloud on AWS by purchasing the service online.
Resources for VMware Cloud on AWS
- Learn more about VMware Cloud on AWS on our website or by viewing the VMware Cloud on AWS: Overview.
- Obtain the VMware Cloud on AWS Solution Brief and VMware Cloud on AWS TCO 1-pager.
- Visit the VMware Cloud on AWS Tech Zone for technical articles, guides, videos and more.
- Listen to the latest episodes of the VMware Cloud on AWS Unplugged Podcast.
- Try the VMware Cloud on AWS Lightning Lab for a first-hand immersive experience.
- Follow us on Twitter @vmwarecloudaws and give us a shout with #VMWonAWS.
- Read our latest VMware Cloud on AWS blogs.
- Follow the VMware Cloud on AWS release notes on continuing updates.
- Watch informative demos, overview videos, webinars and hear from our customers on the VMware Cloud on AWS on YouTube channel.

Ruchi Tandon
Ruchi is a Senior Product Marketing Manager for VMware Cloud on AWS at VMware Inc. With 14+ years of strong technology, data, and marketing background, Ruchi brings deep experience in…