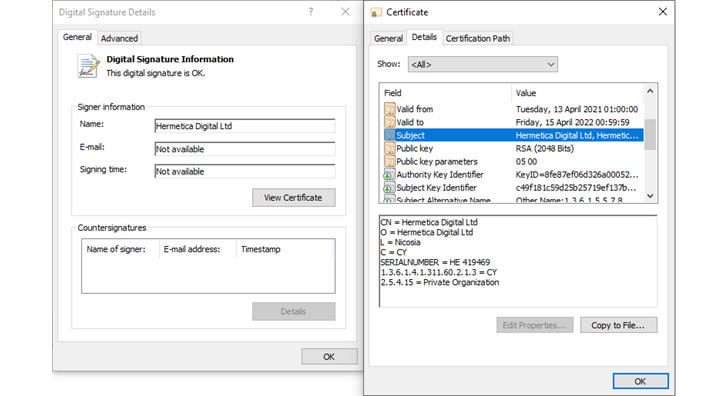
It is commonly believed that Macs are immune to viruses. However, although they are less vulnerable than Windows computers, the reality is that MacBooks, iMacs, and Mac minis are still susceptible to malware and other security vulnerabilities — and there are some worrying ones out there, too.
Below are the top 5 macOS malware programs, security flaws, and vulnerabilities that you need to be aware of!
Silver Sparrow
Disclosed by Red Canary researchers, Silver Sparrow is a unique macOS malware program that was created to target Apple’s new M1 processors.
Silver Sparrow is a PUA (potentially unwanted application) that can serve as a delivery mechanism for malware. Once your device is infected it will contact a server every hour. It is still currently unknown how much of a threat Silver Sparrow truly poses, but in theory, it could act as a catalyst for significant attacks.
Apple quickly released an update to macOS that stopped Silver Sparrow from being able to be installed. Therefore, if you have a fully updated version of macOS, you are safe from Silver Sparrow.
XLoader
It was all but guaranteed that one of the most common pieces of Windows malware would make its way to macOS. Initially reported by Check Point security researchers in July 2021, it was confirmed that a Mac version of the XLoader malware had actually been around for some time.
XLoader is a new variant of the infamous Formbook, a program used to steal login credentials, record keystrokes, and download and execute files.
Once a device is infected with XLoader, it transfers a hidden application bundle containing a copy of itself to the user’s home folder, and what is particularly dangerous about it is the fact that it can run completely undetected by macOS.
XCSSET
Initially reported by Trend Micro in August 2020, XCSSET primarily targets macOS users in Asia. Many experts believe that XCSSET mainly targets Chinese gambling sites and their users.
XCSSET replaces users’ web browser icons with fake versions that launch malware whenever opened. XCSSET can bypass macOS’s privacy protections by hijacking the privileges of legitimate apps, allowing it to take screen captures.
XCSSET seeks to access information via the Safari browser, including login details for various Apple, Google, PayPal, and Yandex services. Other types of information it can collect include notes and messages sent via Skype, Telegram, QQ, and WeChat.
macOS Big Sur IOMobileFrameBuffer
This vulnerability can allow attackers to take over an affected system. It is a critical memory corruption issue found in internal component extensions in macOS. This security flaw allows the installation of malicious applications and enables them to execute commands with system administrator privileges — bypassing macOS’s built-in security measures.
The issue was addressed immediately by Apple, with a fix released in the macOS Big Sur 11.5.1 July 26, 2021 update.
Log4Shell
Log4Shell is a vulnerability in the widely used Java library Apache Log4j — software used by an innumerable number of large companies including Google, Apple, Netflix, Twitter, and many more. It enables attackers to perform remote code execution and gain control over affected servers.
Log4j is an open-source logging tool used by a huge number of websites and apps. Because it is so widely used, the number of services at risk of exploitation is incredibly concerning.
Although macOS is not directly affected by Log4Shell, according to security researchers, the vulnerability has been found to affect Apple’s iCloud platform. Luckily, Apple was quick to patch the vulnerability — releasing a fix shortly after it was discovered.
It was estimated that around 850,000 attacks were attempted within just 72 hours of the initial outbreak. It is not clear if Apple’s iCloud was among the services targeted.
Apache has already released an update fixing the vulnerability, although because of Log4j’s widespread worldwide use, the prospect of all the apps that use it receiving the fix is simply not realistic.
However, even if you use one of the compromised apps, your Mac will not be at risk. When exploited, the bug affects the server running Log4j, not the computer itself. Although in theory the exploit could be used to plant a malicious app on a server that then affects connected machines.
Stay protected at all times
Malware creators will always seek out undiscovered vulnerabilities that they can exploit, and Macs are certainly not immune. Fortunately, security researchers are often exceptionally quick at discovering these vulnerabilities, and fixes are almost always released timely.
However, it is best practice to always use a trusted antivirus app to ensure you are as protected as possible against all types of threats.
Trend Micro’s Antivirus One — the best option for complete peace of mind
Antivirus One can protect your Mac from viruses, malware, and adware, block potential web threats and safeguard against vulnerabilities.
Some key features include:
- Fast Thorough Scans — Scan your Mac for hidden threats in less than a minute.
- Web Threat Protection — Avoid online fraud, malicious software embedded in websites, and other threats lurking on the web.
- Data Privacy Sweeps — Clear personal information out of Safari, Google Chrome, and Mozilla Firefox before it leaks online.
Source :
https://news.trendmicro.com/2022/02/21/top-mac-malware-and-security-vulnerabilities/