Malicious actors taking advantage of important events is not a new trend. For example, a large number of tax-related scams pops up every tax season in the US, with threats ranging from simple phishing emails to the use of scare tactics that lead to ransomware. More recently, Covid-19 has led to a surge in pandemic-related malicious campaigns, mostly arriving via email.
For many people, major online shopping events such as the annual Amazon Prime day — which falls on June 21 this year — presents a unique opportunity to purchase goods at heavily discounted prices. However, shoppers are not the only ones looking to benefit — cybercriminals are also looking to prey on unsuspecting victims via social engineering and other kinds of scams. Amazon Prime has experienced tremendous growth over the past two years. According to estimates, there were 150 million Prime members at the end of the fourth quarter of 2019, a number which grew to 200 million by the first quarter of 2021 — with around 105 million users in the US alone. This makes Amazon Prime customers a particularly lucrative target for malicious actors.
As Amazon Prime day approaches, we’d like to build awareness among the shopping public by showing some of the related scams we’ve observed over the past few months.
Amazon Prime Scams
In 2020, Amazon Prime day, which is usually held in June or July, was postponed to October due to Covid-19. That same month, the Australian Communications and Media Authority (ACMA) issued an alert warning the public that they had been receiving reports of scammers — impersonating Amazon Prime staff — calling their targets, claiming that they owed money to Amazon. They also warned the victim that funds would be taken from their bank account if they did not act immediately. Often, the goal of these scammers is to retrieve Amazon account details and personal data from their victims by asking them to go online and enter the relevant information.
A variation of this scam involves swindlers calling their targets and presenting them with a recorded message, allegedly from Amazon, notifying call recipients of an issue with their order — such as a lost package or an unfulfilled order. The victims would then be invited to either press the number “1” button on their phone or provided a number that they would need to call. As with the first scam, the goals are the same: gaining personal information.
Aside from phone call scams, malicious actors also use tried-and-tested email-based phishing tactics. One method uses fake order invoices with corresponding phony order numbers and even a bogus hotline number, which, once called, will prompt the recipient to enter their personal details.
Another technique involves the scammer notifying an Amazon Prime user of problems with their account: For example, a Twitter post from user VZ NRW – Phishing shows fake Amazon Prime message warning the recipient that their Prime benefits have allegedly been suspended due to a problem with the payment. The message also contains a fake phishing link that the user would have to click to resolve the issue.
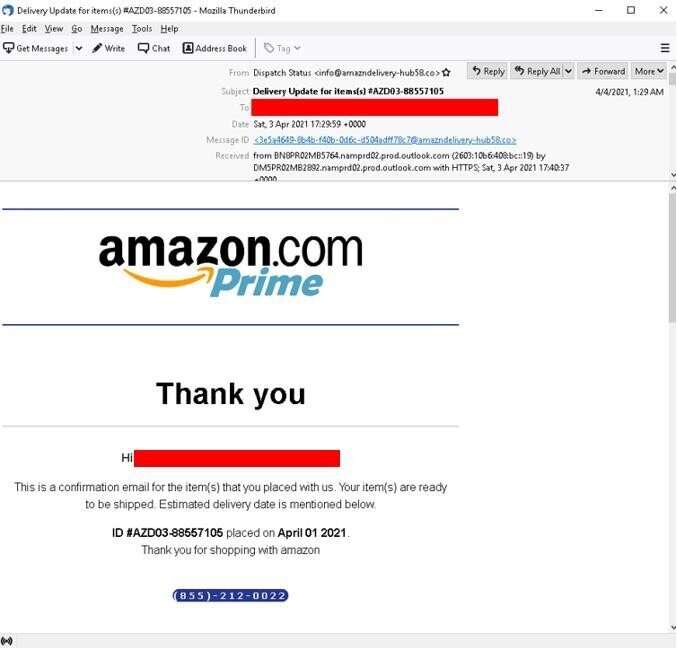
hotline number. Note the suspicious email address used by the sender containing a misspelled “Amazon.”
Malicious actors will also make use of fake websites and online forms — many of which are painstakingly crafted to match the official sites as much as possible. One phishing website asks users to confirm payment details by filling out certain information. However, despite looking authentic, the page contains plenty of red flags — for example, none of the outbound links actually work, and the forms used in the page requests more data than usual, including personal information that companies typically never ask users to provide.
A precursory search in VirusTotal using the strings “Amazon” and “Prime” reveal over a hundred PDF files, many of which contain movie names (membership in Amazon Prime also makes users eligible for Prime Video). These PDF files are hosted on various cloud services, with the link to these files typically distributed via malicious emails.
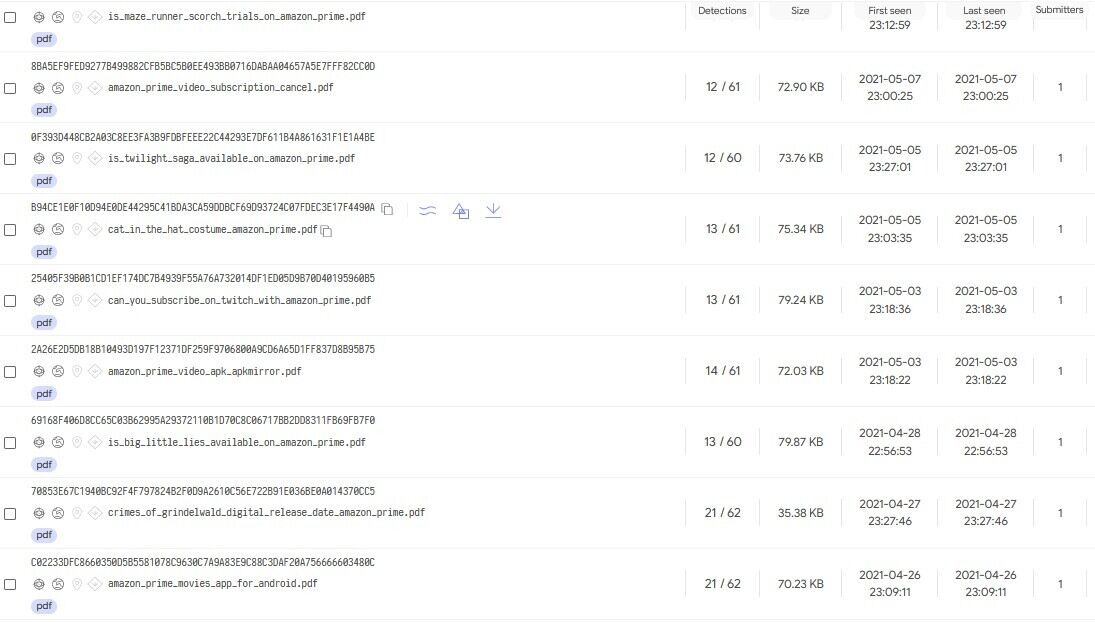
Upon opening some of these files, a Captcha button appears, which will activate a malicious redirection chain when clicked.
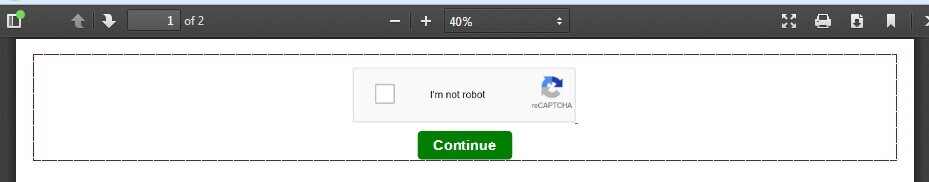
While it’s easy to assume that most of these scammers are single individuals or small groups looking for a quick buck, there are certain threat actor groups that use sophisticated social engineering techniques for their campaigns, which includes Amazon users as a primary target.
The Heatstroke phishing campaign
We first encountered the phishing campaign known as Heatstroke back in 2019, noting that the group behind the campaign utilized complex techniques for both researching about and luring in their victims, which were primarily Amazon and Paypal users.
For example, compared to the webpage from the previous section, Heatstroke makes use of a phishing website with multiple working screens and subpages to try and mimic a legitimate website as much as possible. In addition, Heatstroke implements various obfuscation techniques such as forwarding the phishing kit content from another location or changing the landing page to bypass content filters.
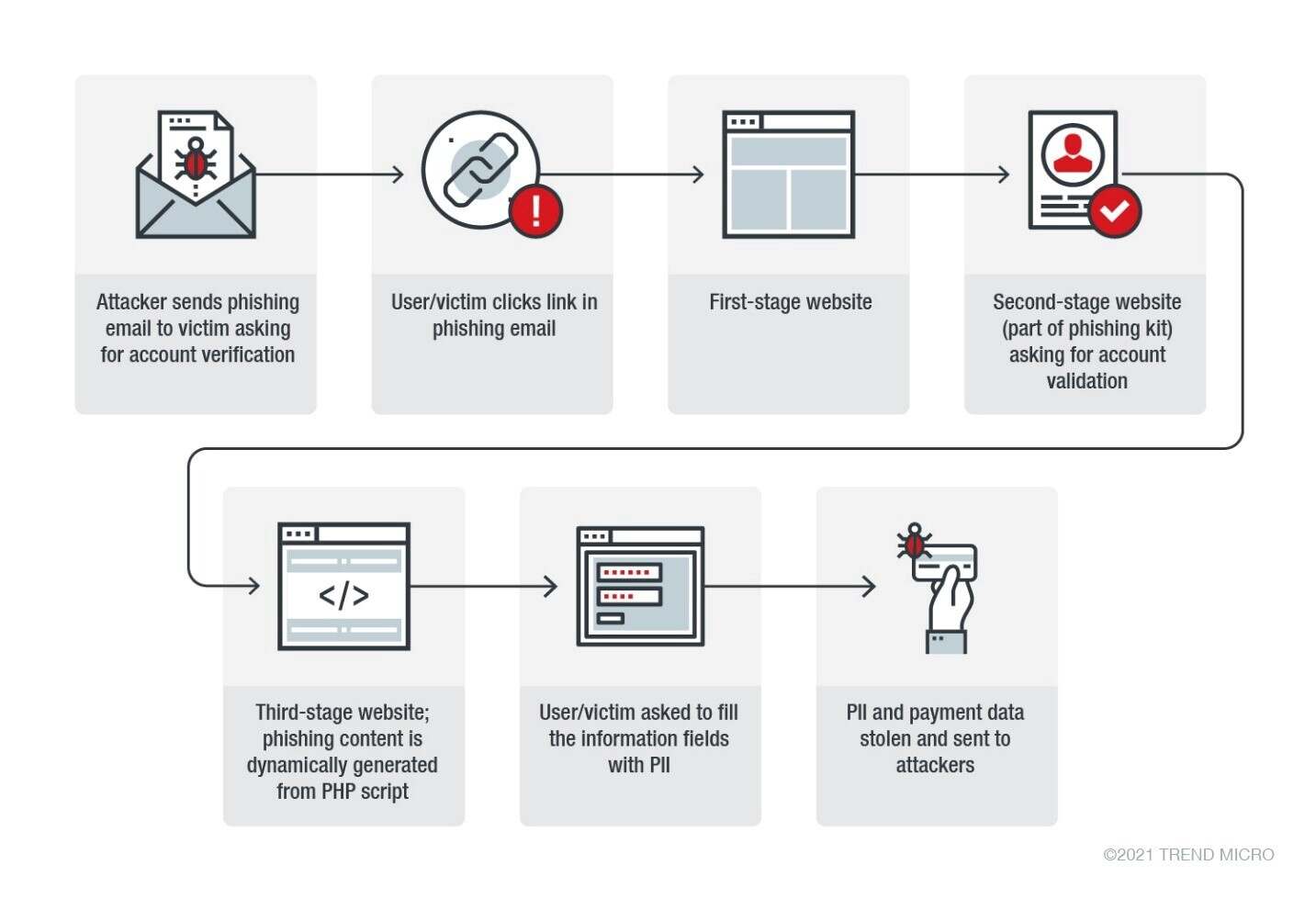
The threat actor has implemented some improvements over the past two years — such as expanded IP ranges and improvements to user agents and the kit’s “self-defense” mechanisms (coverage of scams, anti-bot, and IP protection services), as well as the addition of an API and kill date, after which the kit won’t work anymore.
Heatstroke remains active with a well-maintained infrastructure in 2021. The threat actor largely uses the same techniques from the past. However, it might be a case of not fixing what isn’t broken, given how effective the previous campaigns proved to be.
Defending against scams
As exciting as Amazon Prime Day (and other similar shopping extravaganzas like Black Friday and Cyber Monday) is, the public should remain vigilant against potential scams, as cybercriminals are looking to capitalize on these types of events.
The following best practices and recommendations can help individuals avoid these kinds of scams:
- Most reputable organizations will never ask for sensitive financial information over the phone. If a caller allegedly coming from Amazon or another company asks for strangely specific information such as credit card or bank account numbers, this is an automatic red flag.
- Be wary of out-of-context emails. If you receive an email referencing an item you did not purchase, then it is highly likely that the email is a phishing attempt. Refrain from downloading attachments or clicking links in suspicious emails, as these can lead to malware infections.
- Scan emails for typographical or grammatical mistakes. Legitimate emails will always be thoroughly checked and edited before being sent, therefore even small errors are possible signs of a malicious email.
- Always double check the URL of a website to see if it matches up with the real one. For example, Amazon websites and subpages will always have a dot before “amazon.com” (for example, “support.amazon.com” versus “support-amazon.com”), therefore, even if a website copies the design of the legitimate one, a sketchy URL will often give it away as being malicious. In the same vein, email addresses should be scrutinized to see if they look suspicious or have any unusual elements.
- Organizations are also encouraged to regularly check the awareness of employees on the latest cyberthreats via Trend Micro Phish Insight, a cloud-based security awareness service that is designed to empower employees to protect themselves and their organization from social engineering-based attacks.
Source :
https://www.trendmicro.com/en_us/research/21/f/amazon-prime-day-big-sales–big-scams.html