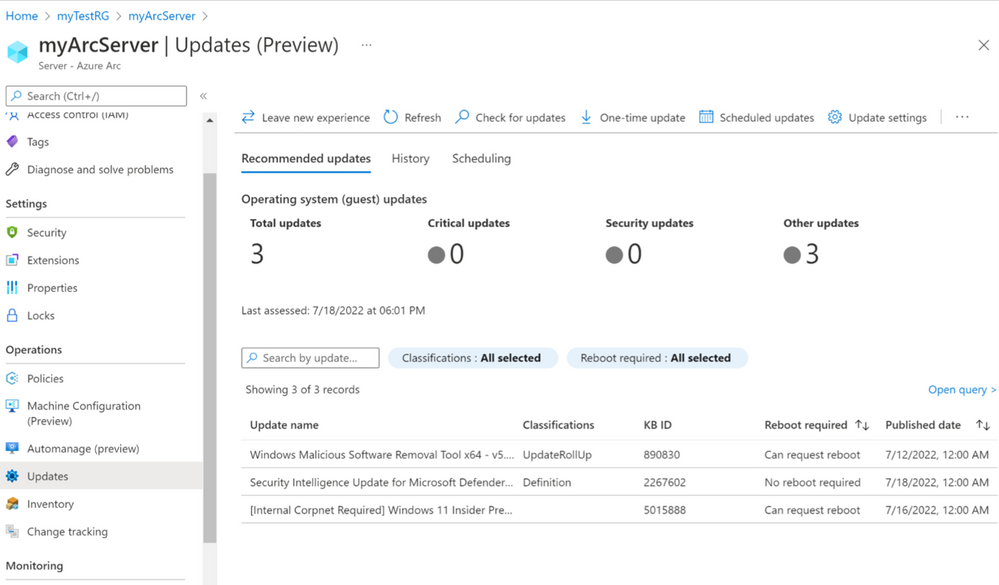
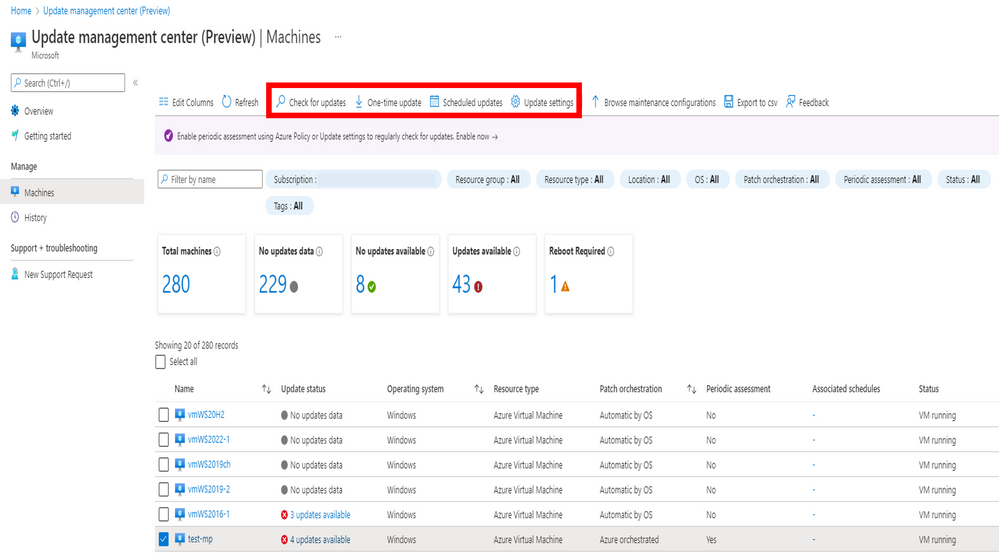
Insufficiently protected open ports can put your IT environment at serious risk. Threat actors often seek to exploit open ports and their applications through spoofing, credential sniffing and other techniques. For example, in 2017, cybercriminals spread WannaCry ransomware by exploiting an SMB vulnerability on port 445. Other examples include the ongoing campaigns targeting Microsoft’s Remote Desktop Protocol (RDP) service running on port 3389.
Handpicked related content:
Read on to learn more about the security risks linked to ports, vulnerable ports that need your attention and ways to enhance the security of open ports.
A Refresher on Ports
Ports are logical constructs that identify a specific type of network service. Each port is linked to a specific protocol, program or service, and has a port number for identification purposes. For instance, secured Hypertext Transfer Protocol (HTTPS) messages always go to port 443 on the server side, while port 1194 is exclusively for OpenVPN.
The most common transport protocols that have port numbers are Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). TCP is a connection-oriented protocol with built-in re-transmission and error recovery. UDP is a connectionless protocol that doesn’t recover or correct errors in messages; it’s faster and has less network overhead traffic than TCP. Both TCP and UDP sit at the transport layer of the TCP/IP stack and use the IP protocol to address and route data on the internet. Software and services are designed to use TCP or UDP, depending on their requirements.
TCP and UDP ports are in one of these three states:
- Open — The port responds to connection requests.
- Closed — The port is unreachable, indicating that there is no corresponding service running.
- Filtered — The firewall is monitoring traffic and blocking certain connection requests to the port.
Security Risks Linked to Ports
Numerous incidents have demonstrated that open ports are most vulnerable to attack when the services listening to them are unpatched or insufficiently protected or misconfigured, which can lead to compromised systems and networks. In these cases, threat actors can use open ports to perform various cyberattacks that exploit the lack of authentication mechanisms in the TCP and UDP protocols. One common example is spoofing, where a malicious actor impersonates a system or a service and sends malicious packets, often in combination with IP spoofing and man-in-the-middle-attacks. The campaign against RDP Pipe Plumbing is one of the latest to employ such a tactic. In addition, ports that have been opened on purpose (for instance, on a web server) can be attacked via that port using application-layer attacks such as SQL injection, cross-site request forgery and directory traversal.
Another common technique is the denial of service (DoS) attack, most frequently used in the form of distributed denial of service (DDoS), where attackers send massive numbers of connection requests from various machine to the service on the target in order to deplete its resources.
Vulnerable Ports that Need Your Attention
Any port can be targeted by threat actors, but some are more likely to fall prey to cyberattacks because they commonly have serious shortcomings, such as application vulnerabilities, lack of two-factor authentication and weak credentials.
Here are the most vulnerable ports regularly used in attacks:
Ports 20 and 21 (FTP)
Port 20 and (mainly) port 21 are File Transfer Protocol (FTP) ports that let users send and receive files from servers.
FTP is known for being outdated and insecure. As such, attackers frequently exploit it through:
- Brute-forcing passwords
- Anonymous authentication (it’s possible to log into the FTP port with “anonymous” as the username and password)
- Cross-site scripting
- Directory traversal attacks
Port 22 (SSH)
Port 22 is for Secure Shell (SSH). It’s a TCP port for ensuring secure access to servers. Hackers can exploit port 22 by using leaked SSH keys or brute-forcing credentials.
Port 23 (Telnet)
Port 23 is a TCP protocol that connects users to remote computers. For the most part, Telnet has been superseded by SSH, but it’s still used by some websites. Since it’s outdated and insecure, it’s vulnerable to many attacks, including credential brute-forcing, spoofing and credential sniffing.
Port 25 (SMTP)
Port 25 is a Simple Mail Transfer Protocol (SMTP) port for receiving and sending emails. Without proper configuration and protection, this TCP port is vulnerable to spoofing and spamming.
Port 53 (DNS)
Port 53 is for Domain Name System (DNS). It’s a UDP and TCP port for queries and transfers, respectively. This port is particularly vulnerable to DDoS attacks.
Ports 137 and 139 (NetBIOS over TCP) and 445 (SMB)
Server Message Block (SMB) uses port 445 directly and ports 137 and 139 indirectly. Cybercriminals can exploit these ports through:
- Using the EternalBlue exploit, which takes advantage of SMBv1 vulnerabilities in older versions of Microsoft computers (hackers used EternalBlue on the SMB port to spread WannaCry ransomware in 2017)
- Capturing NTLM hashes
- Brute-forcing SMB login credentials
Ports 80, 443, 8080 and 8443 (HTTP and HTTPS)
HTTP and HTTPS are the hottest protocols on the internet, so they’re often targeted by attackers. They’re especially vulnerable to cross-site scripting, SQL injections, cross-site request forgeries and DDoS attacks.
Ports 1433,1434 and 3306 (Used by Databases)
These are the default ports for SQL Server and MySQL. They are used to distribute malware or are directly attacked in DDoS scenarios. Quite often, attackers probe these ports to find unprotected database with exploitable default configurations.
Port 3389 (Remote Desktop)
This port is used in conjunction with various vulnerabilities in remote desktop protocols and to probe for leaked or weak user authentication. Remote desktop vulnerabilities are currently the most-used attack type; one example is the BlueKeep vulnerability.
Tips for Strengthening the Security of Open Ports
Luckily, there are ways to enhance the security of open ports. We highly recommend the following six strategies:
1. Patch firewalls regularly.
Your firewall is the gatekeeper to all the other systems and services in your network. Patching keeps your firewalls up to date and repairs vulnerabilities and flaws in your firewall system that cybercriminals could use to gain full access to your systems and data.
2. Check ports regularly.
You should also regularly scan and check your ports. There are three main ways to do this:
- Command-line tools — If you have the time to scan and check ports manually, use command-line tools to spot and scan open ports. Examples include Netstat and Network Mapper, both of which can be installed on a wide range of operating systems, including Windows and Linux.
- Port scanners — If you want faster results, consider using a port scanner. It’s a computer program that checks if ports are open, closed or filtered. The process is simple: The scanner transmits a network request to connect to a specific port and captures the response.
- Vulnerability scanning tools — Solutions of this type can also be used to discover ports that are open or configured with default passwords.
- Track service configuration changes.
Many services on your network connect to various ports, so it is important to monitor the running states of installed services and continuously track changes to service configuration settings. Services can be vulnerable when they are unpatched or misconfigured.
Using Netwrix Change Tracker, you can harden your systems by tracking unauthorized changes and other suspicious activities. In particular, it provides the following functionality:
- Actionable alerting about configuration changes
- Automatic recording, analyzing, validating and verifying of every change
- Real-time change monitoring
- Constant application vulnerability monitoring
4. Use IDP and IPS tools.
Intrusion detection systems (IDS) and intrusion prevention systems (IPS) can help you prevent attackers from exploiting your ports. They monitor your network, spot possible cybersecurity incidents, log information about them and report the incidents to security administrators. IPS complements your firewalls by identifying suspicious incoming traffic and logging and blocking the attack.
5. Use SSH Keys.
Another option is to use SSH keys. These access credentials are more secure than passwords because decrypting SSH is very difficult, if not impossible. There are two types of SSH keys:
- Private or identity keys, which identify users and give them access
- Public or authorized keys, which determine who can access your system
You can use public-key cryptographic algorithms and key generation tools to create SSH keys.
6. Conduct penetration tests and vulnerability assessments.
Consider conducting penetration tests and vulnerability assessments to protect your ports. Although both of these techniques are used to spot vulnerabilities in IT infrastructure, they are quite different. Vulnerability scans only identify and report vulnerabilities, while penetration tests exploit security gaps to determine how attackers can gain unauthorized access to your system.
FAQs
What is an open port vulnerability?
An open port vulnerability is a security gap caused by an open port. Without proper configuration and protection, attackers can use open ports to access your systems and data.
Which ports are most vulnerable?
Certain ports and their applications are more likely to be targeted because they often have weaker credentials and defenses. Common vulnerable ports include:
- FTP (20, 21)
- SSH (22)
- Telnet (23)
- SMTP (25)
- DNS (53)
- NetBIOS over TCP (137, 139)
- SMB (445)
- HTTP and HTTPS (80, 443, 8080, 8443)
- Ports 1433, 1434 and 3306
- Remote desktop (3389)
Is port 80 a security risk?
Port 80 isn’t inherently a security risk. However, if you leave it open and don’t have the proper configurations in place, attackers can easily use it to access your systems and data. Unlike port 443 (HTTPS), port 80 is unencrypted, making it easy for cybercriminals to access, leak and tamper with sensitive data.
Source :
https://blog.netwrix.com/2022/08/04/open-port-vulnerabilities-list/